TI Ops: An Evolved Threat Intelligence Platform
Move beyond a legacy threat intelligence platform
(TIP) to threat intelligence operations (TI Ops).
Operationalize all your intel for faster, more precise
detection and response.
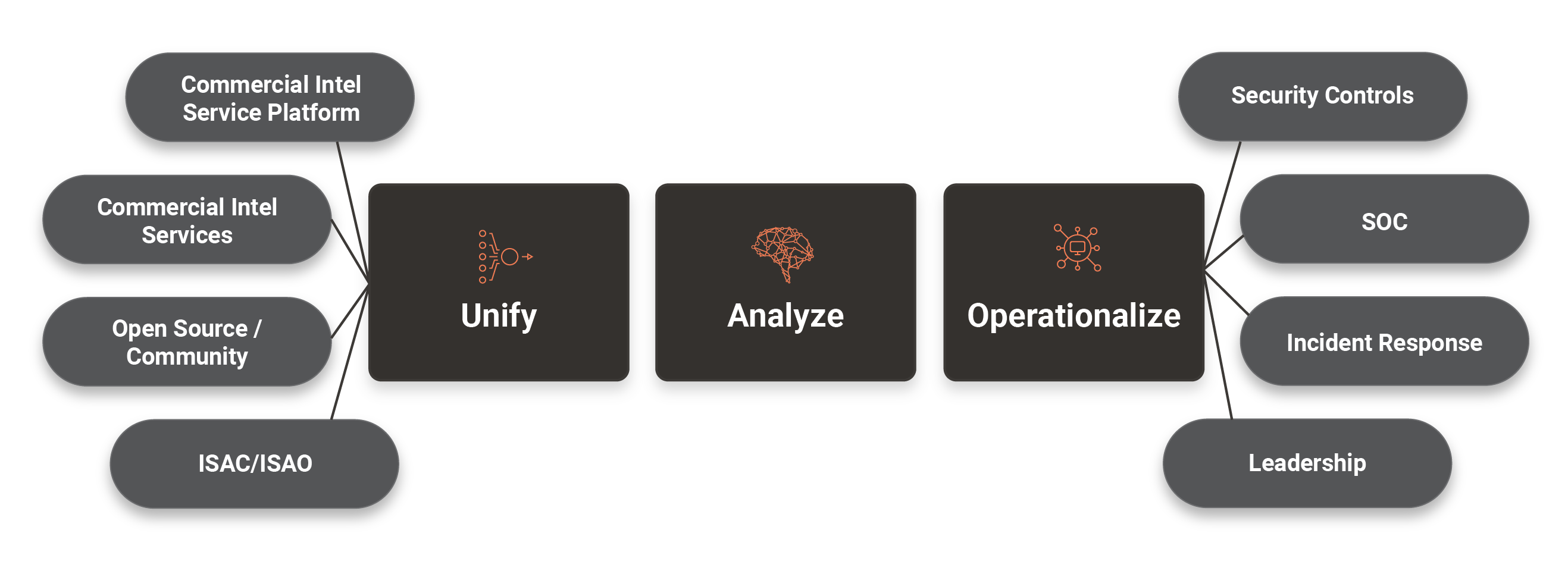
Harness the power of AI and automation to aggregate, enrich, and analyze all your intelligence in a single threat intel platform, enabling prioritization and action on the most critical threats.
Key Capabilities of the TI Ops Platform
Covering Your Most Critical Use Cases
Whether you’re an analyst responsible for synthesizing and producing intel, or a customer consuming the operational, tactical, and strategic intel from the CTI team, the ThreatConnect TI Ops Platform covers a wide-variety of your critical use cases.
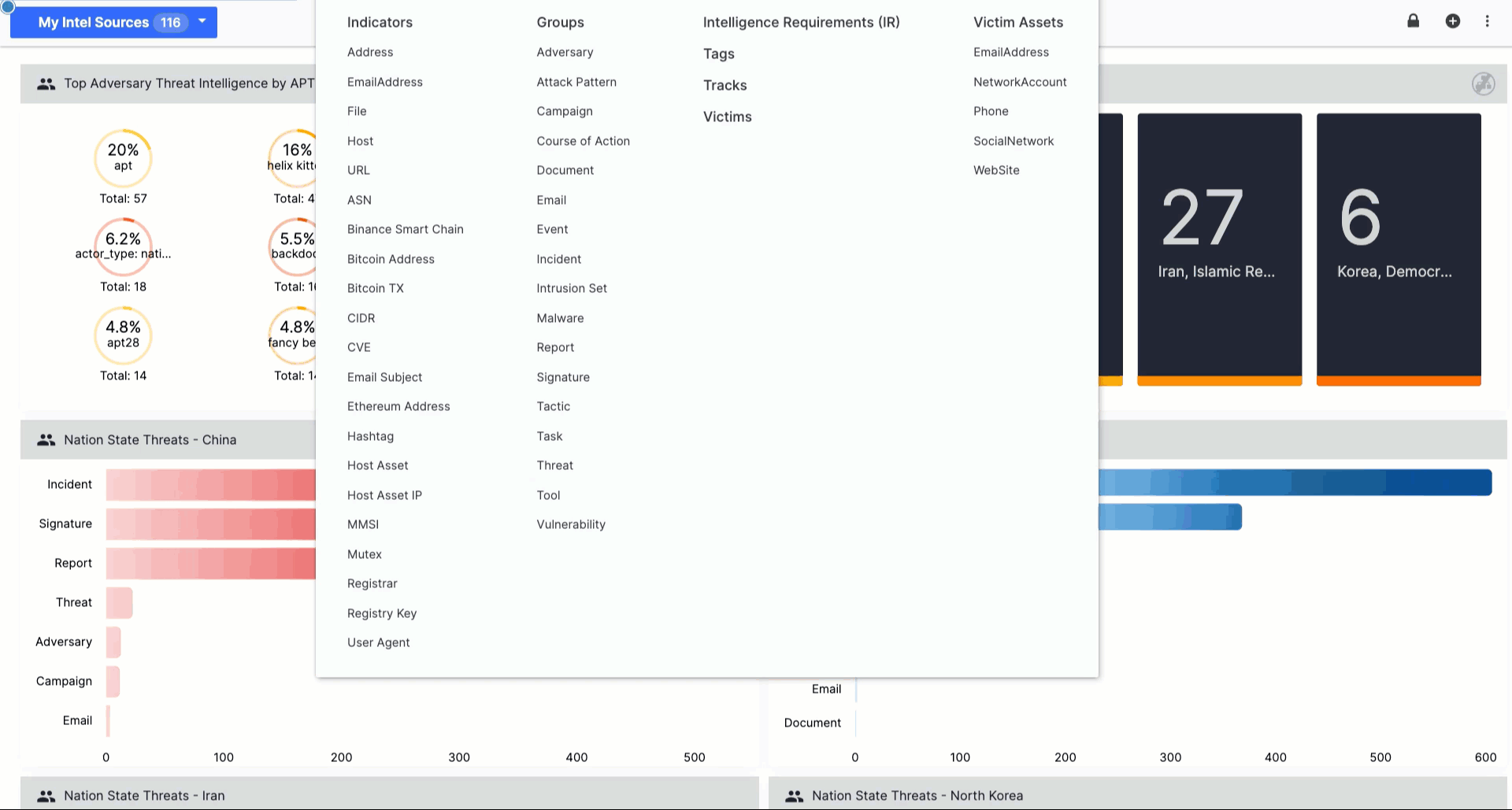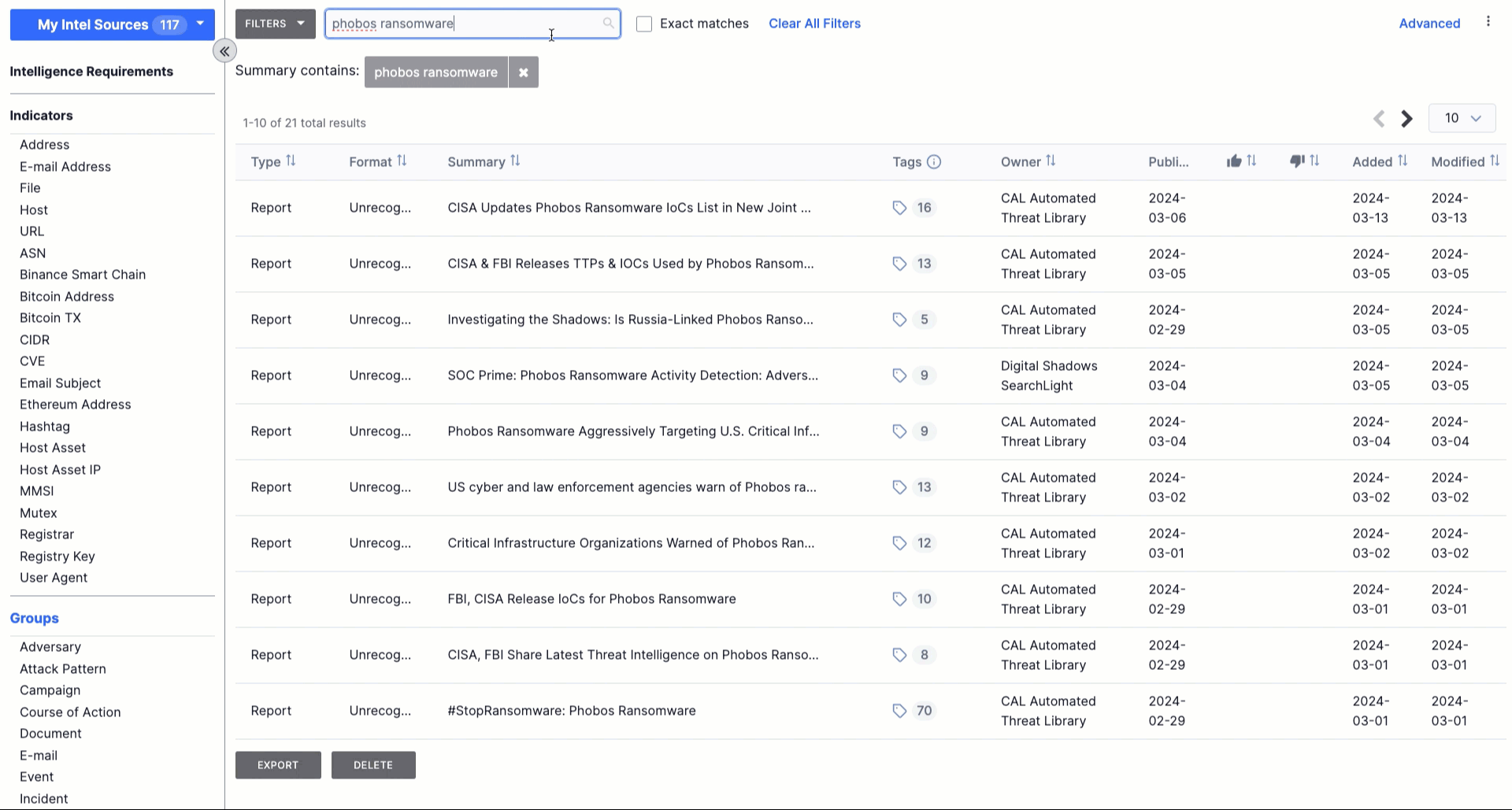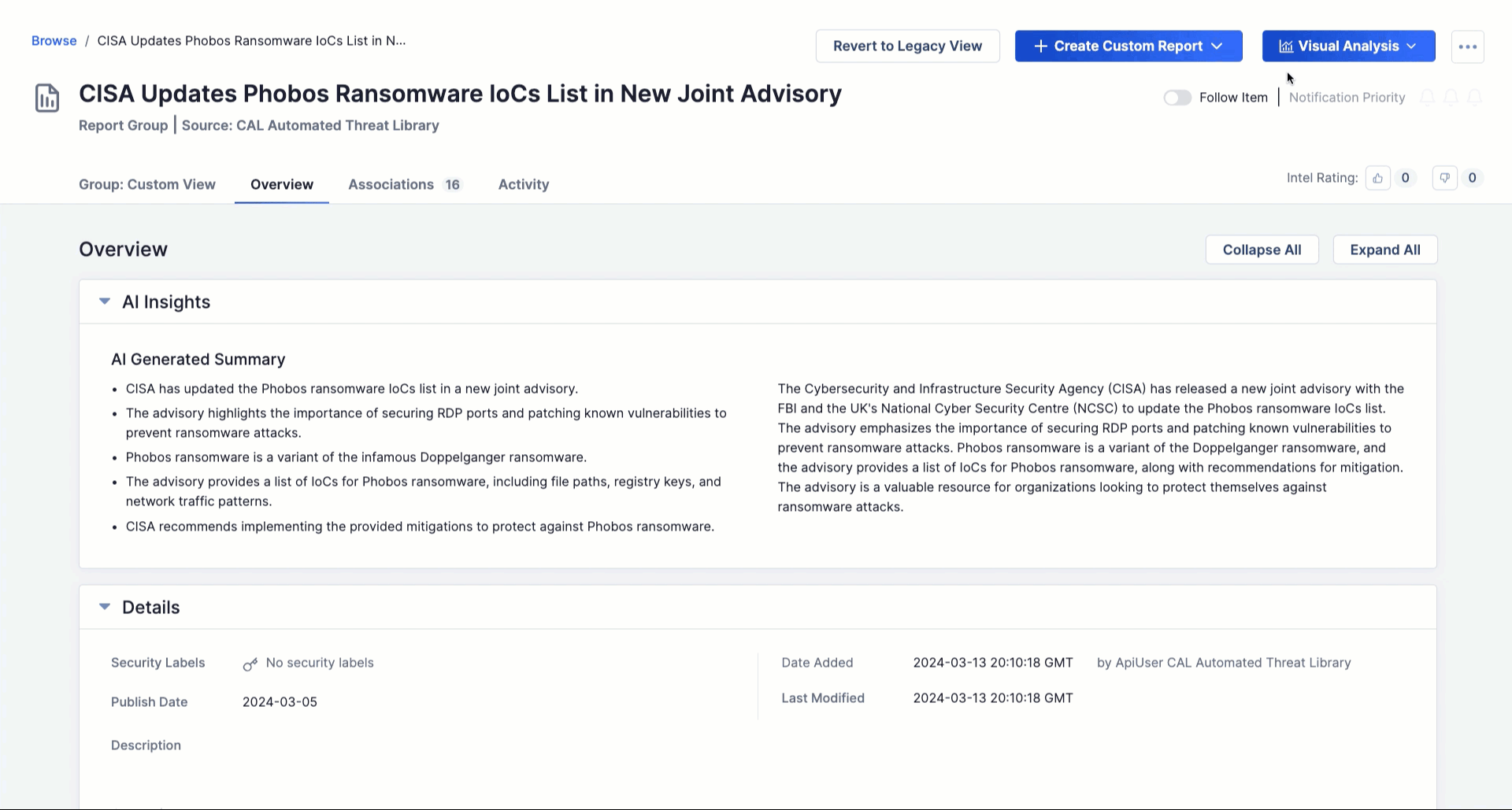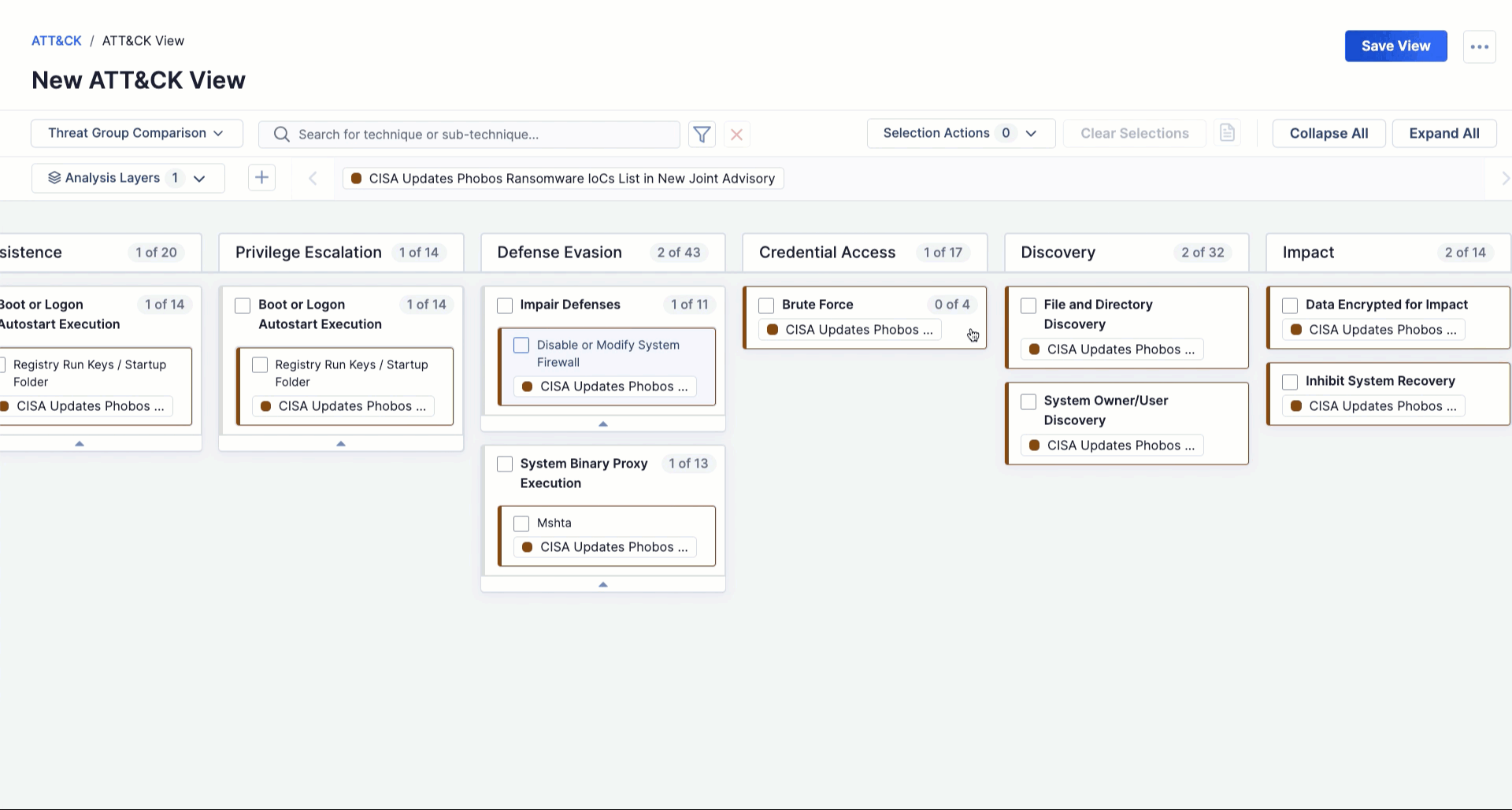
New: Polarity Intel Edition
Polarity Intel Edition is an add-on to our TI Ops platform that makes it easier for the entire cybersecurity organization (SOC, IR, threat hunting, etc.) to access intelligence when and where it’s needed – without even needing to leave their pane of glass!
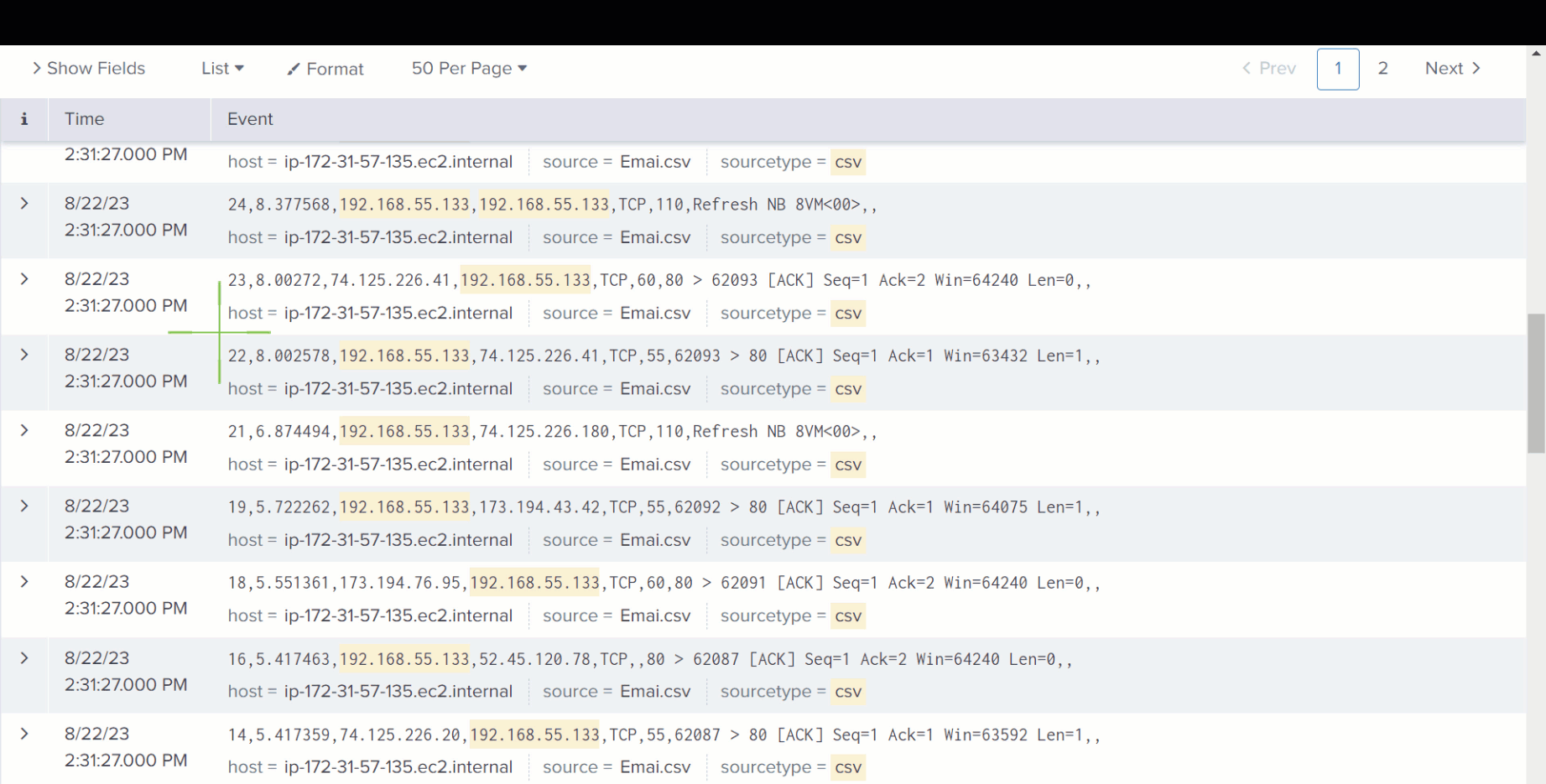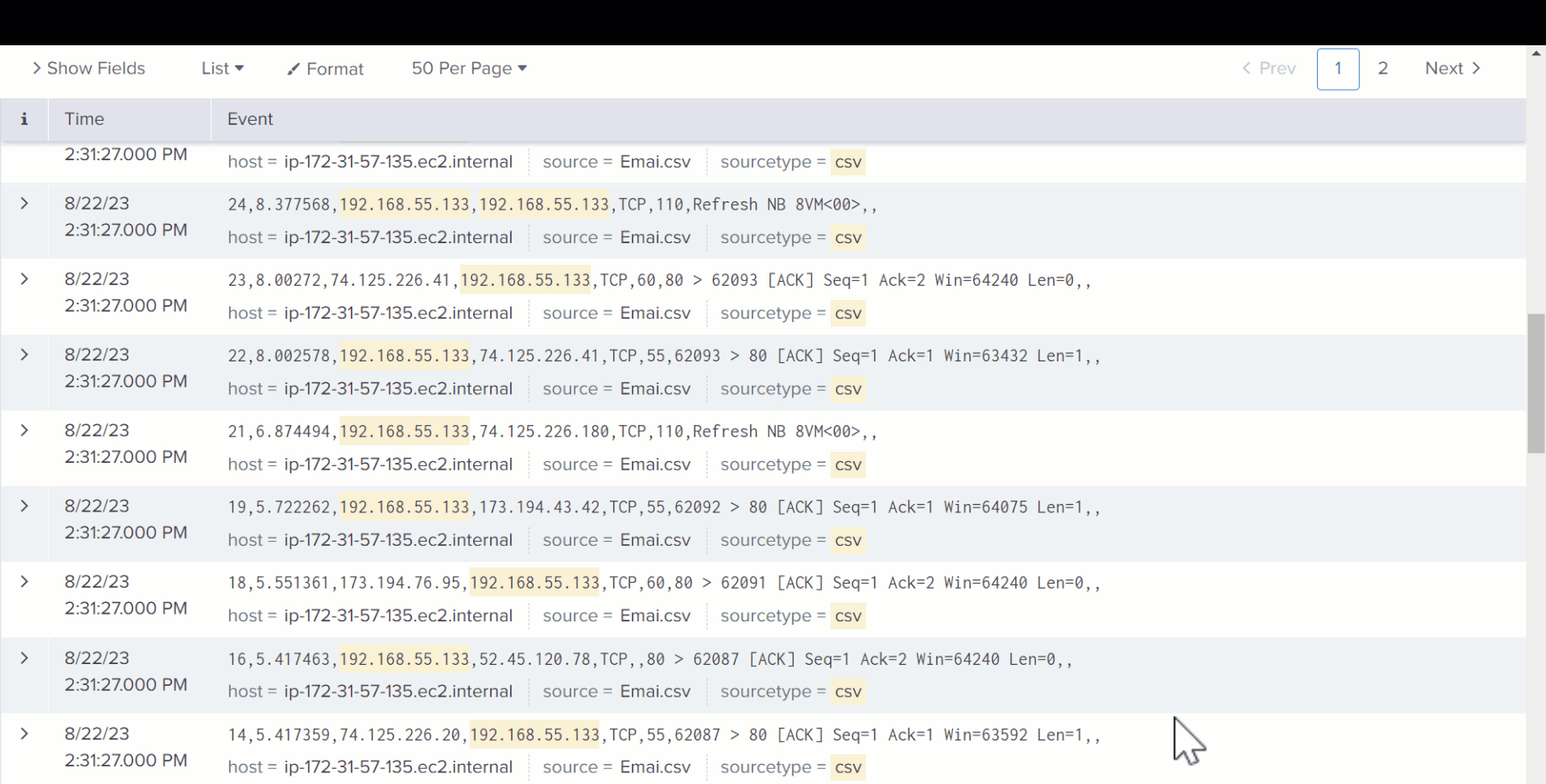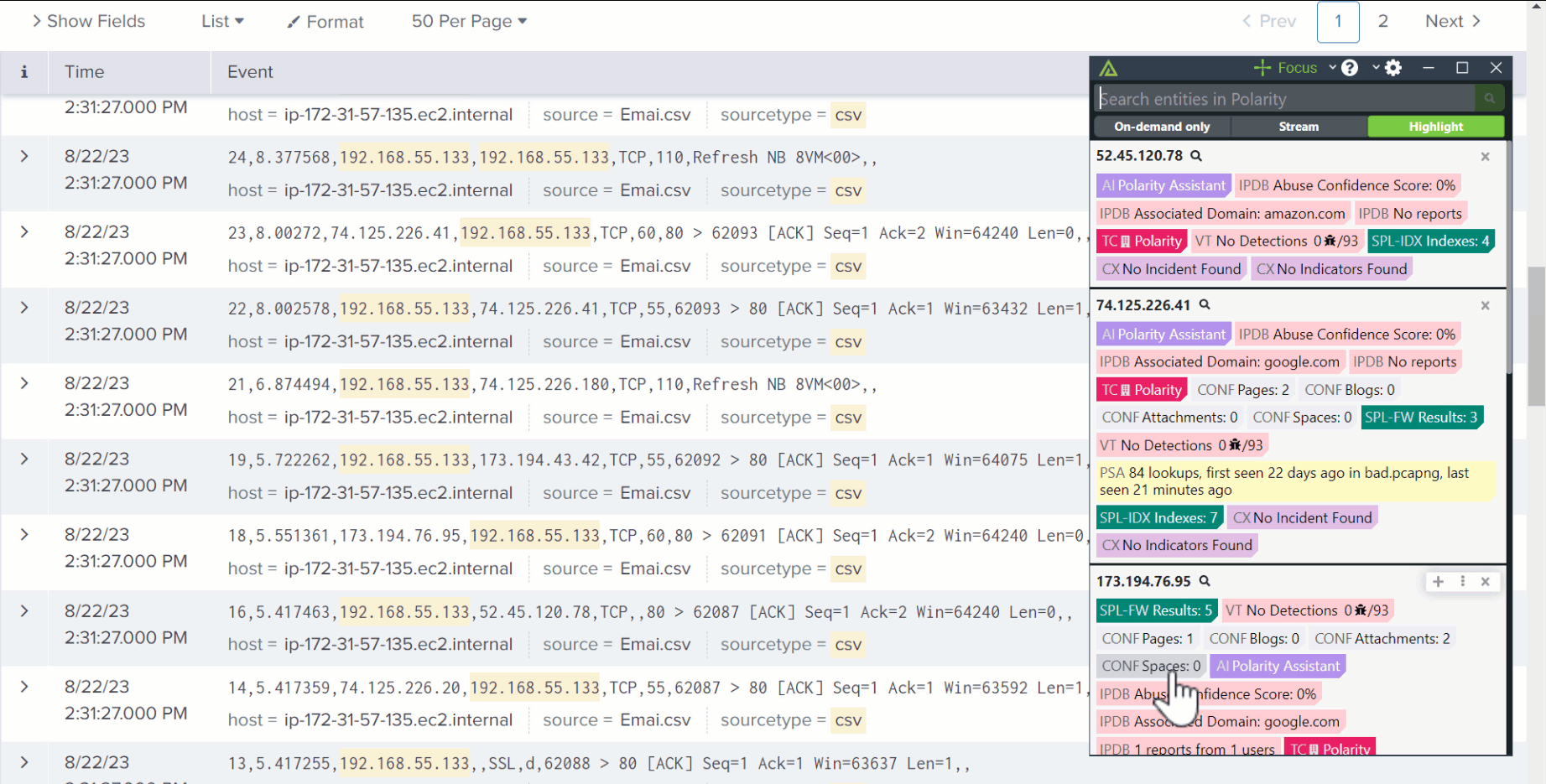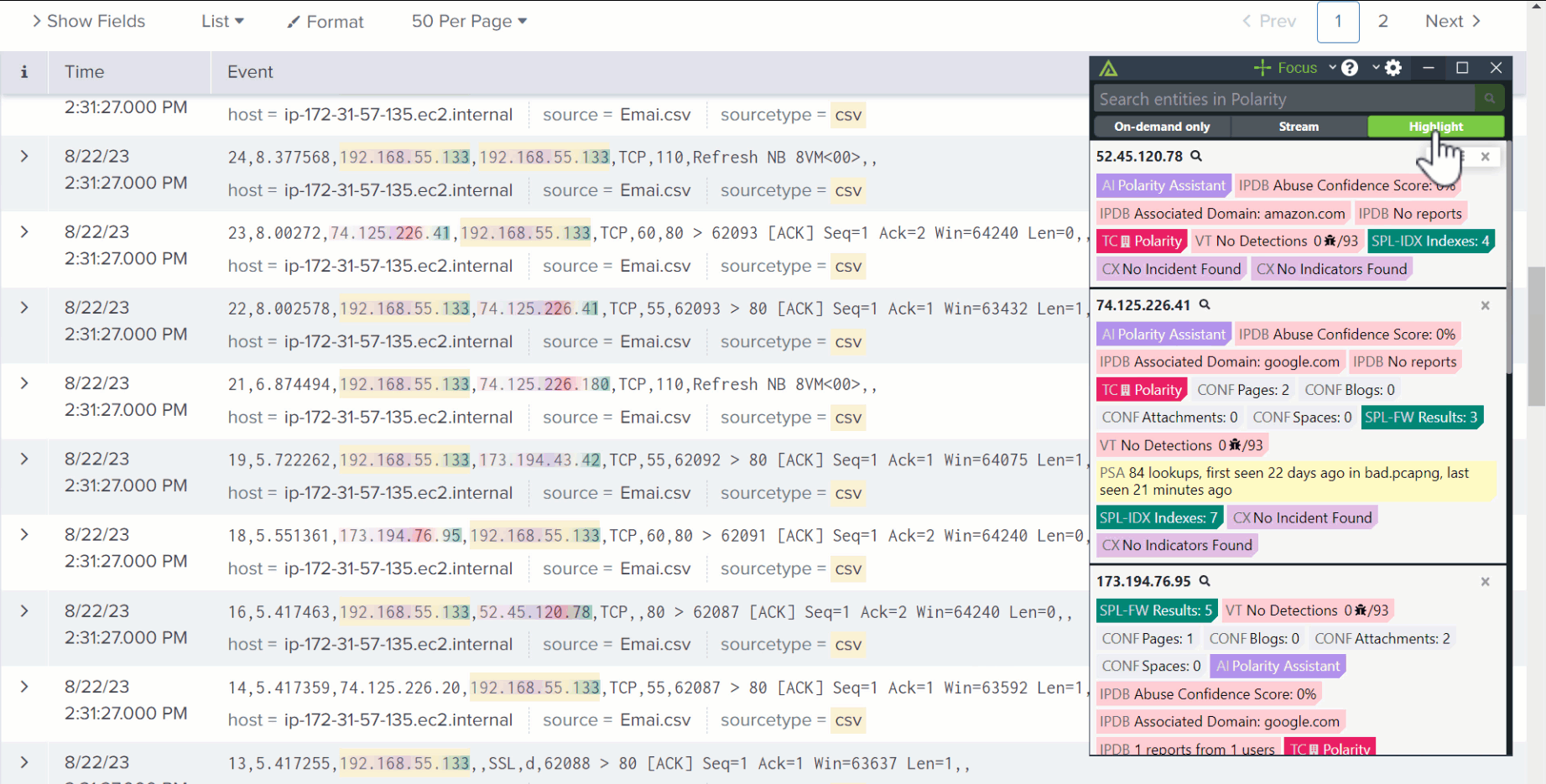
Focus on what matters to you
Intel Your Teams Will Love
See how the ThreatConnect platform can take you beyond a traditional threat intelligence platform.
Threat Intel Is Your Force Multiplier
See how the ThreatConnect Platform helps you find and respond to the most critical threats.
See how The ThreatConnect platform enables intelligence-driven incident response.
See how ThreatConnect can make your threat hunting faster and more effective.
Learn how ThreatConnect can take your vulnerability management program to the next level.
Increase Resilience, Reduce Stress
Learn how ThreatConnect enables Threat Intel Operations with an evolved Threat Intelligence Platform.
Learn how putting CTI at the core of your cybersecurity program is a game changer.
Trusted By Leading Companies
See how industry leaders are driving outcomes with the ThreatConnect platform.

Threat and Risk Intelligence Solutions
Elevate Your Threat Intelligence
Move your security operations teams from reactive to proactive by operationalizing your cyber threat intelligence beyond a legacy threat intelligence platform.
Buyer’s Guide for Threat Intelligence Operations
Threat intelligence platforms collect threat indicators and produce threat reports. Learn why you need a modern TI Ops platform to replace your threat intel platform.
Choosing the Right Threat Intelligence Platform
Evaluating TIP capabilities, threat intelligence sources, and threat intelligence management solutions? Find the best fit for your cybersecurity teams.