Workflow and Case Management
Native workflow case management shortens response times by streamlining processes, prioritizing work, and enabling collaboration.
Streamline Operations and Reduce Response Times
Transform expertise into reusable templates, run automation alongside manual inputs, and improve response times. Enhance collaboration and prioritize events for effective security operations.
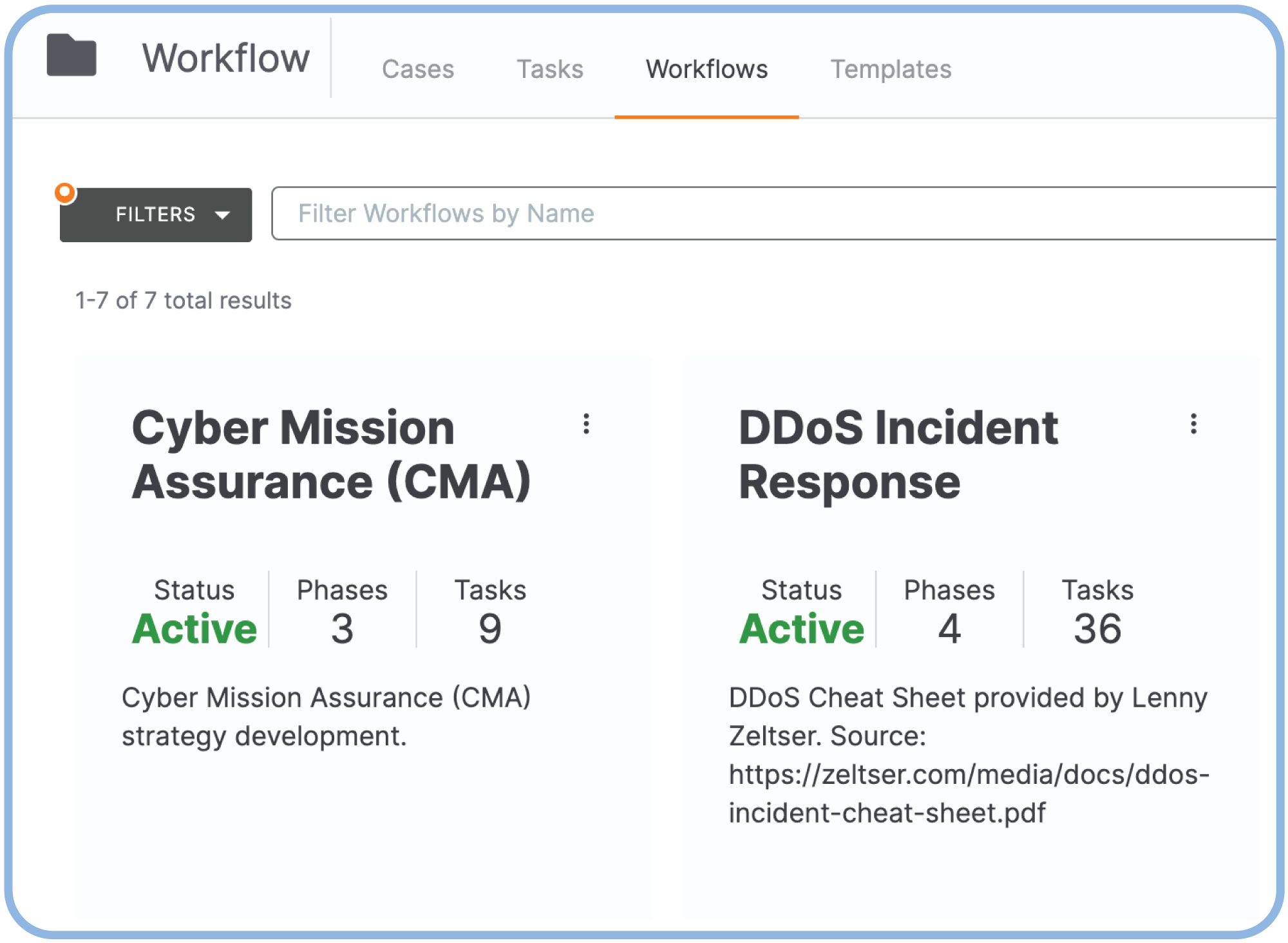
Flexible Workflow Automation
Workflows can be fully manual, semi-automated, or fully automated. Build automation into your workflows with tasks and playbooks. Analysts can leverage a structured and centralized approach to investigate, track, and collaborate on threats and incidents by automating tasks triggered by workflow events.
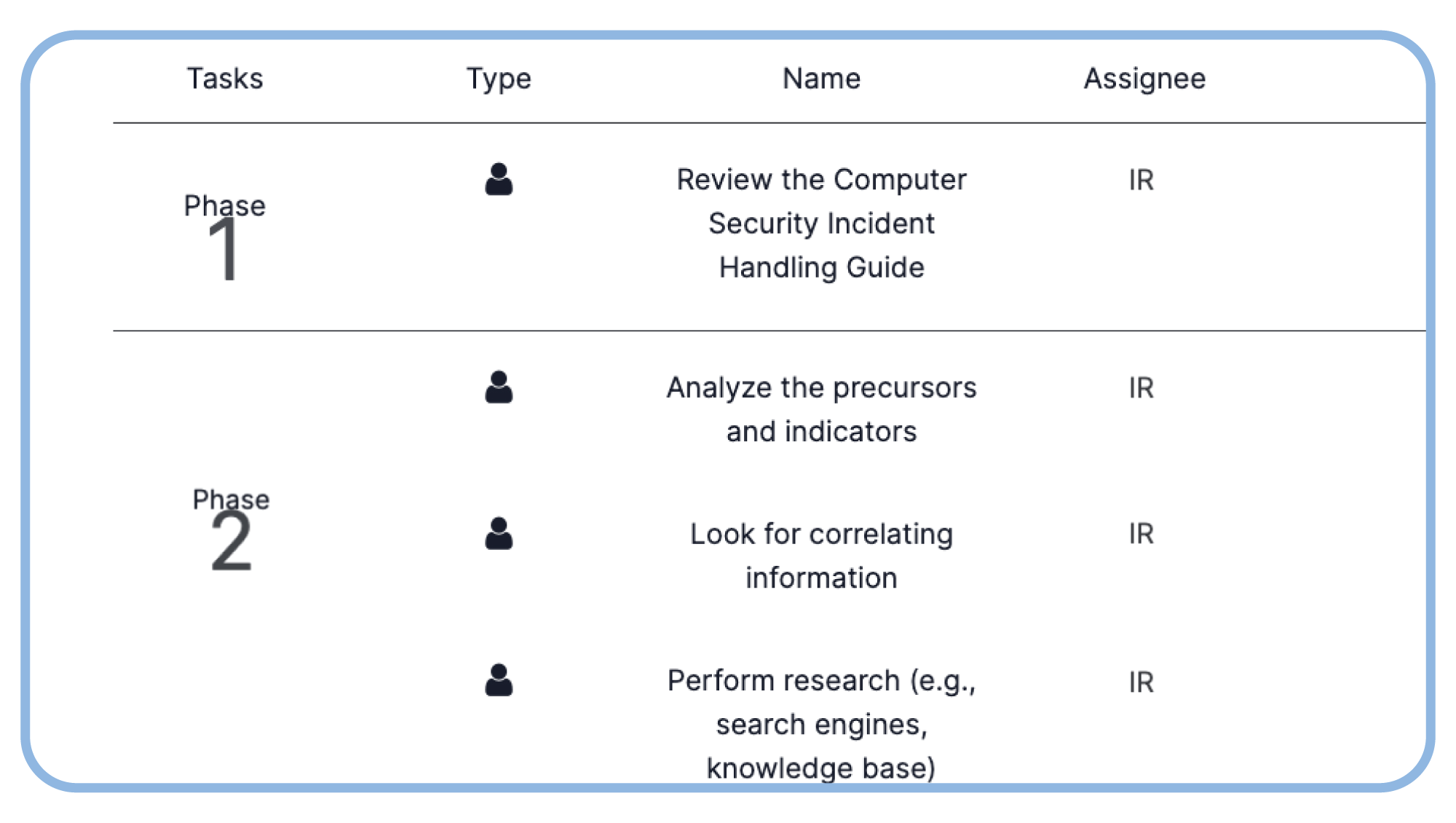
Centrally Capture Threat Intel Knowledge for Future Use
CTI, incident response, and threat hunting teams can record their work and centrally capture new findings and knowledge. With a central repository of threat intelligence activities teams can ensure new threat insights and intel, like IOCs, are memorialized for future use.
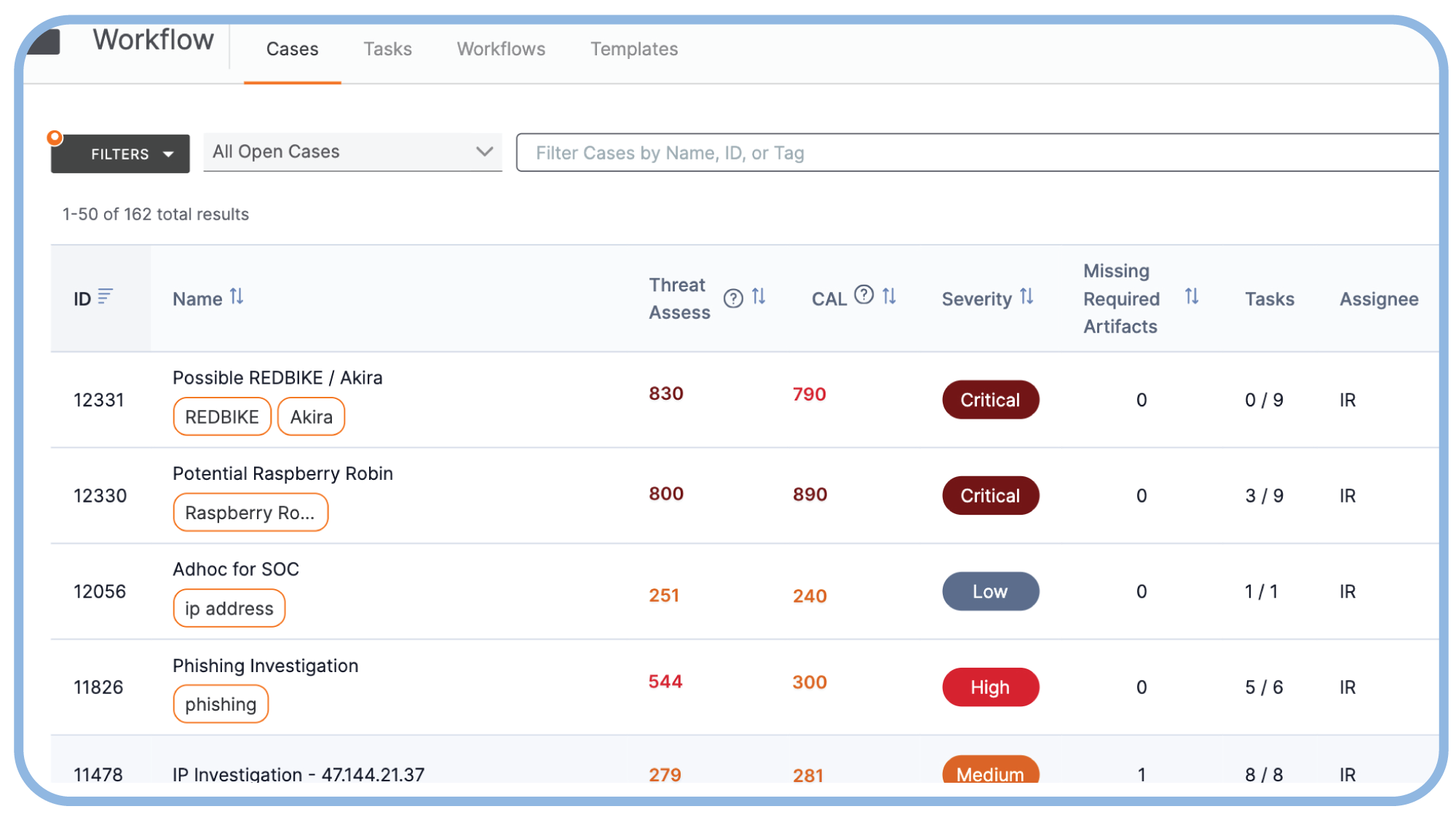
Ensure operational effectiveness and consistency
TI Ops Buyer’s Guide
This guide will help you evaluate the threat intelligence vendor landscape and determine the best fit for your cybersecurity program’s needs.
Workflows for SOC and IR Teams
Learn how workflows streamline CTI and security operations teams and help them achieve breakthrough effectiveness.
8 Questions to Ask a Threat Intelligence Platform Vendor
The threat intelligence platform (TIP) landscape can be confusing. To help you choose the right platform, we’ve compiled eight questions to ask your vendor.