Speed Response Time with Alert Triage
Eliminate false positives across your security tools and enable security operations center (SOC) analysts to quickly and easily prioritize the alerts that matter.
Remove False Positives that Cost your SOC Time and Money
You need high-fidelity intel across your threat detection tools to minimize false-positive alerts. Threat scoring removes noisy indicators that consume valuable analyst time.
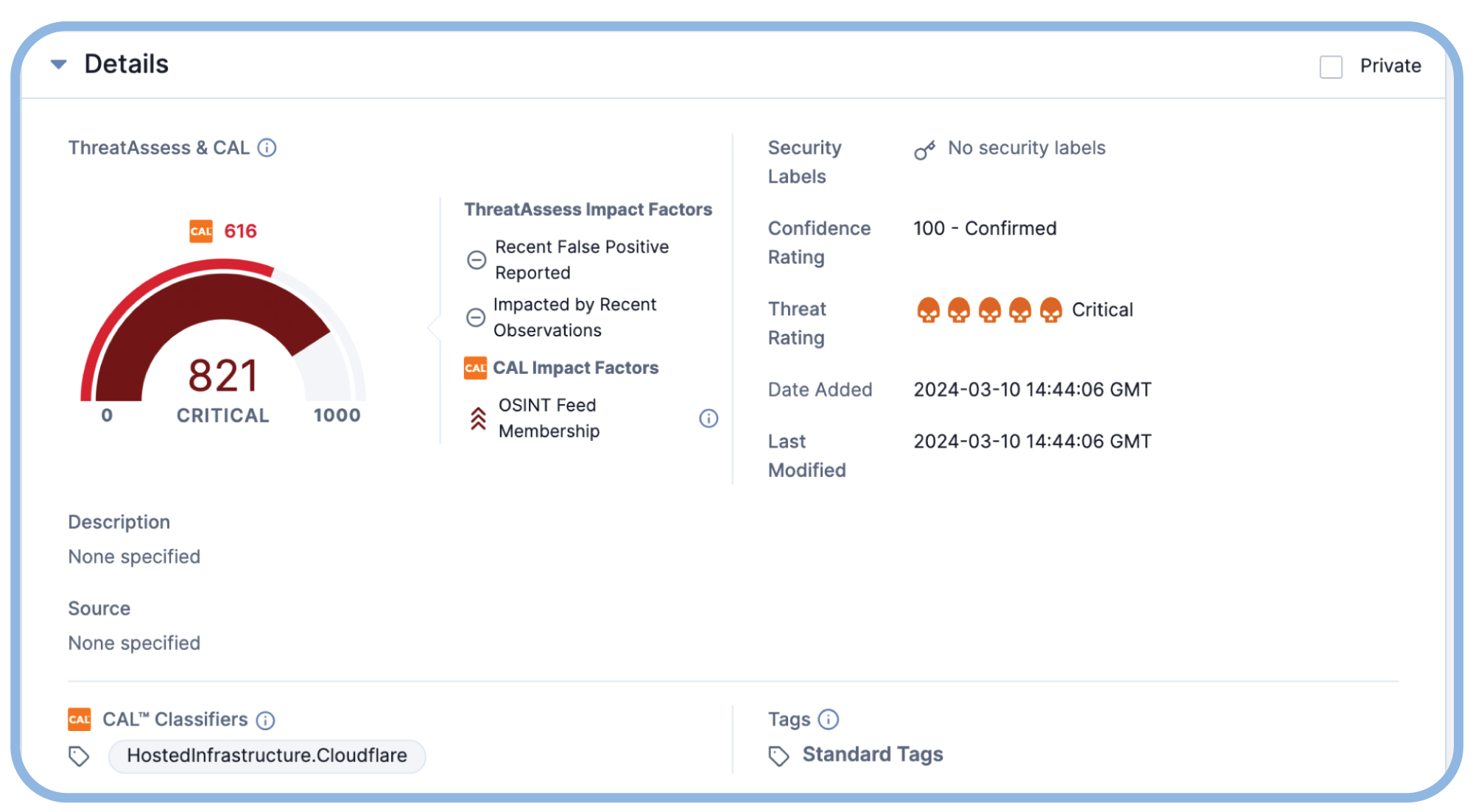
Triage and Prioritize the Most Critical Alerts
Minutes matter when there is an active threat. Stop drowning analysts in alerts and give them the context they need to quickly assess an alert and decide what action is required.

Achieve Faster Threat Detection and Response with Automation
The longer an attacker is in your environment, the more significant the financial impact. Respond in seconds and limit the damage with playbook and task automation.

Defend your Organization from Attacks
Intelligence-Powered Security Operations
Put threat intelligence at the center of security operations
ThreatConnect for Security Operations
Learn how the ThreatConnect Platform can be a force multiplier for security operations teams.
Triage Alerts Quickly and Confidently
See the ThreatConnect TI Operations Platform in action