Posted
Many organizations struggle to demonstrate value for threat intel and their threat intelligence teams. The intel team is trying to do the right thing though. They are collecting threat intelligence, managing it into usable shape, making it available for use, and then struggling to find consumers who need, or want, to use it.
Security operations is a well-used and accepted term. It’s an action-oriented term. Security teams have people, processes, and tools that support activities like vulnerability management, and threat detection and response. Threat intelligence teams are called the cyber threat intel or “the CTI team”. There is zero implication that there is any operational aspect, or action, to the function. We know that’s not the truth. This may appear simplistic, but I believe it’s a foundational issue with threat intel – how it’s perceived by leaders and peers in cybersecurity operations and cyber risk management.
This is the reason why I believe the perceptions of cyber threat intel have to change. But that change requires assessing the what, how, and why of threat intelligence. A new approach is needed. This is the reason why CTI teams need to evolve into Threat Intel Operations, or TI Ops as we call it. And it’s definitely more than just a name change.
In the Dawn of Threat Intelligence Operations paper, seven tenets of TI Ops are defined. This blog is the first in a series where I’m going to dive deep into these and the reason why their adoption will help transform CTI teams into TI Ops. Here I’ll touch on the tenets at a high level, with more blogs focusing on specific tenets coming in the near future.
The Seven Tenets of TI Ops
I observe many CTI teams being relegated to a function within the SOC. This makes sense as threat intel is a crucial element of threat monitoring, detection, and incident response, but it also limits the value that threat intel can provide across cybersecurity operations and cyber risk management. By elevating TI Ops to a top-level role within security operations, threat intel can become the core of how to transform SecOps into what we call Intelligence-Powered Security Operations.
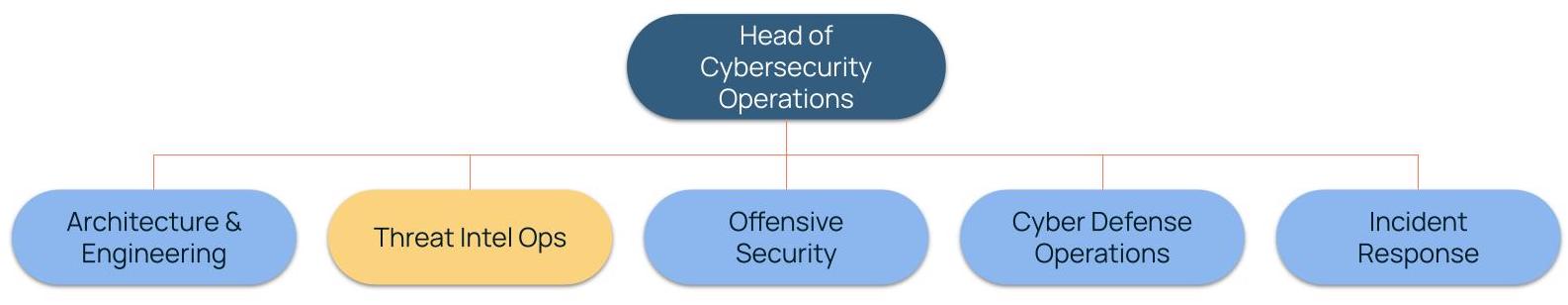
A Sample CyberSecurity Operations Org Chart
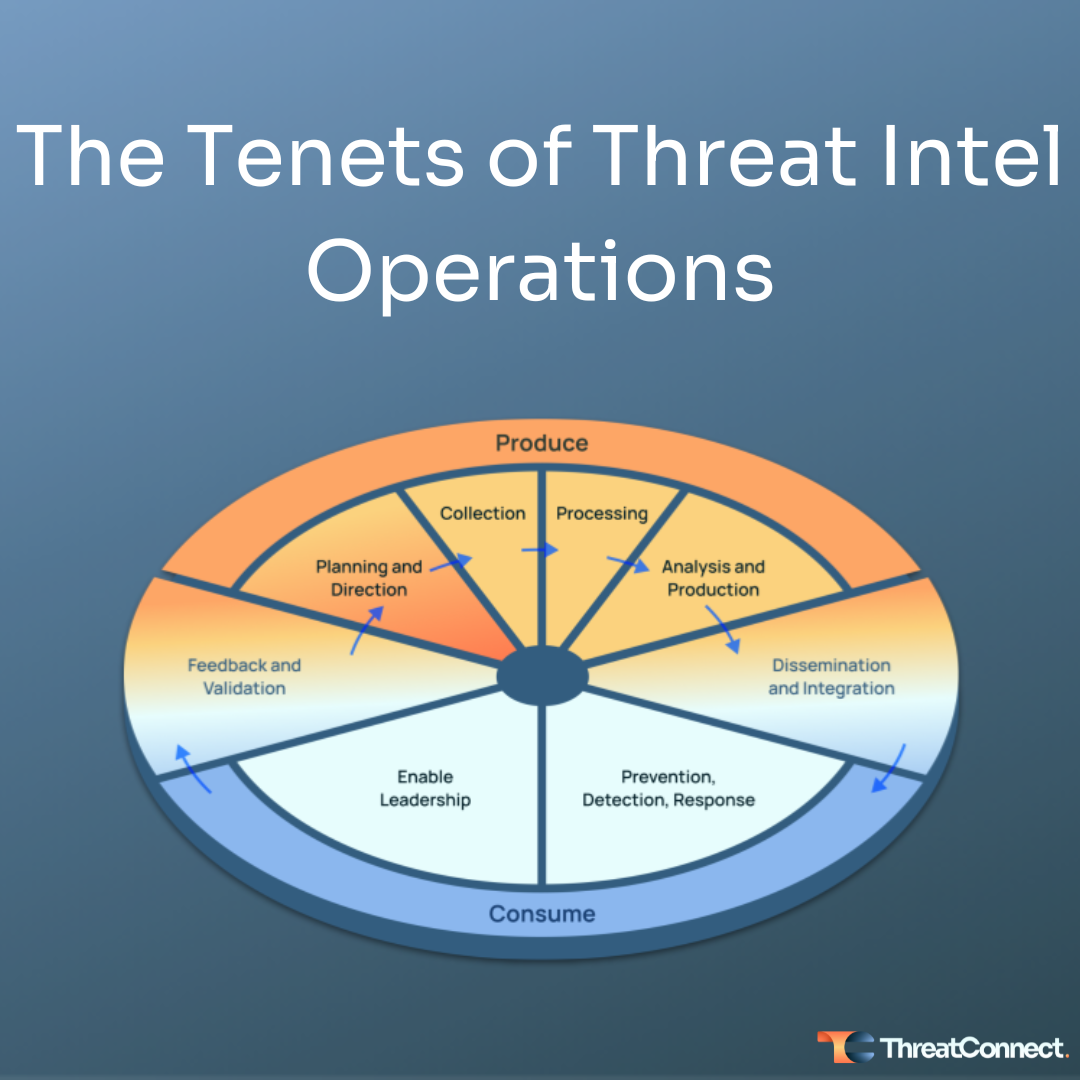
I’m a fan of processes in tradecraft, and the CTI lifecycle has done an admirable job of aligning CTI teams around a common process, but it’s showing its age. It really focuses on the production of CTI, not the consumer or customer of intel, and the importance of the feedback to make it a virtuous cycle. This is why we believe an Evolved Threat Intel Lifecycle is required for TI OPs.
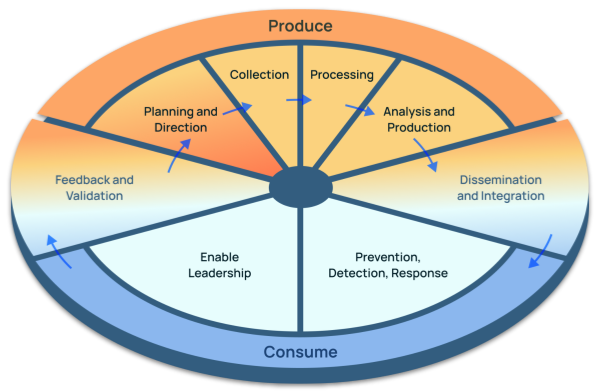
The Evolved Threat Intel Lifecycle
The Evolved Threat Intel Lifecycle’s emphasis on the threat intel consumers reinforces the importance of defined intel requirements (e.g. PIRs), which according to SANS’ 2022 Cyber Threat Intelligence Survey don’t exist in almost ⅔ of the organizations they surveyed. Like other functions that rely on technology to enable the people and processes, the lack of defined requirements makes it difficult to determine if the function is operating efficiently, meeting customer requirements, and technologies employed are fit-for-purpose. If threat intel requirements don’t exist or are not aligned to the organizational risks, there is a high likelihood the CTI function will ultimately fail. Cybersecurity teams can’t afford these failures.
The days of threat intel focused only on indicators of compromise are numbered, but many CTI teams are still stuck here because it serves a valuable use case – threat detection and prevention – but it’s just one of the many areas a CTI team can inject value into. I’ve heard from many leading-edge companies that are expanding the focus of their CTI teams into monitoring the motives, methods and tradecraft, and infrastructure used by adversaries. The adoption and use of MITRE ATT&CK within threat intel reflects this interest. TI Ops goes beyond just managing intel and focusing on IOCs and expands to include all the other valuable intel that provides context to consumers, enabling not just the operational use of intel, but informing and influencing cybersecurity and risk management strategies.
Automation is critical. It’s becoming ubiquitous and accepted within the technology across our daily lives, and CTI is no different. Automation is one of the critical advantages that helps CTI teams pivot to being operationally focused, and it needs to be applied to as many stages of the Evolved Threat Intel Lifecycle as feasible. Leveraging automation allows the CTI team to address the big data challenges they are facing these days, e.g., the volume, variety, and velocity of intel, and to scale operations by being more efficient and effective.
Security operations teams are still too siloed in many organizations. The SOC does its thing by detecting and responding to threats. The vulnerability management team is trying to reduce exposures to the organization’s attack surface. The identity and access management and governance teams are trying to keep identities and accounts current with the right level of security. The infrastructure security team is trying to keep the adversaries out while enabling employees and partners to get their work done with as little friction as possible. Cyber risk management is trying to identify and quantify the greatest risks to the organization. And finally, Leadership is responsible for the strategic direction of the cybersecurity and cyber risk management functions. What is a common thread across all of them? Threat intelligence. They are all important customers of threat intel, whether it be strategic, operational, or tactical intel.
CTI functions struggle to demonstrate their value, and that falls back on the lack of agreed and documented requirements, and being able to measure the team’s performance against those requirements and demonstrate how the intel they produced led to wins. Evolving into a TI Ops function requires putting in place measures, and then using those measures to communicate with stakeholders, both the good and the bad. This allows TI Ops team to implement a virtuous improvement cycle, and more importantly to demonstrate the value, like ROI, of the TI Ops team and insulating it against the perennial question from leadership – “what value is the CTI function providing for the money I’m spending on it, and should I expand or reduce that budget”?
The Bottom Line
TI Ops must be the future of CTI teams and functions in order to remain relevant to an organization’s cyber security and risk management program. By adopting the 7 tenets of TI Ops, CISOs and SecOps leaders are going to gain an advantage over the adversaries, and any upper hand they get to make their organizations more defensible and resilient to attacks is a win.
To Learn More
Subscribe to ThreatConnect emails for event invites, tips, and industry trends and read the Dawn of TI Ops paper.