Posted
In the first blog of this series, I took a 30,000-foot view of the seven tenets of TI Ops defined in the Dawn of Threat Intelligence Operations paper. In this edition we are going to dig into Tenet #2 – Requires an Evolved Threat Intelligence Lifecycle, one that emphasizes the planning and requirements and the use of threat intel by the consumers
My colleague Dan Cole, VP of Product Management, who conceived the Evolved Threat Intel Lifecycle, agreed to answer my questions and provide his insights, like an AMA, about why an evolution of the current threat intel lifecycle and why it’s needed now, and how it helps both TI Ops and SecOps teams. First, a brief background on the current Cyber Threat Intel Lifecycle.
The current lifecycle consists of 5, or 6, phases depending on the version:
- Planning and Direction (aka Requirements)
- Collection
- Processing
- Analysis (and Production)
- Dissemination, and
- Feedback (sometimes combined with Dissemination as a single phase, hence the variations).
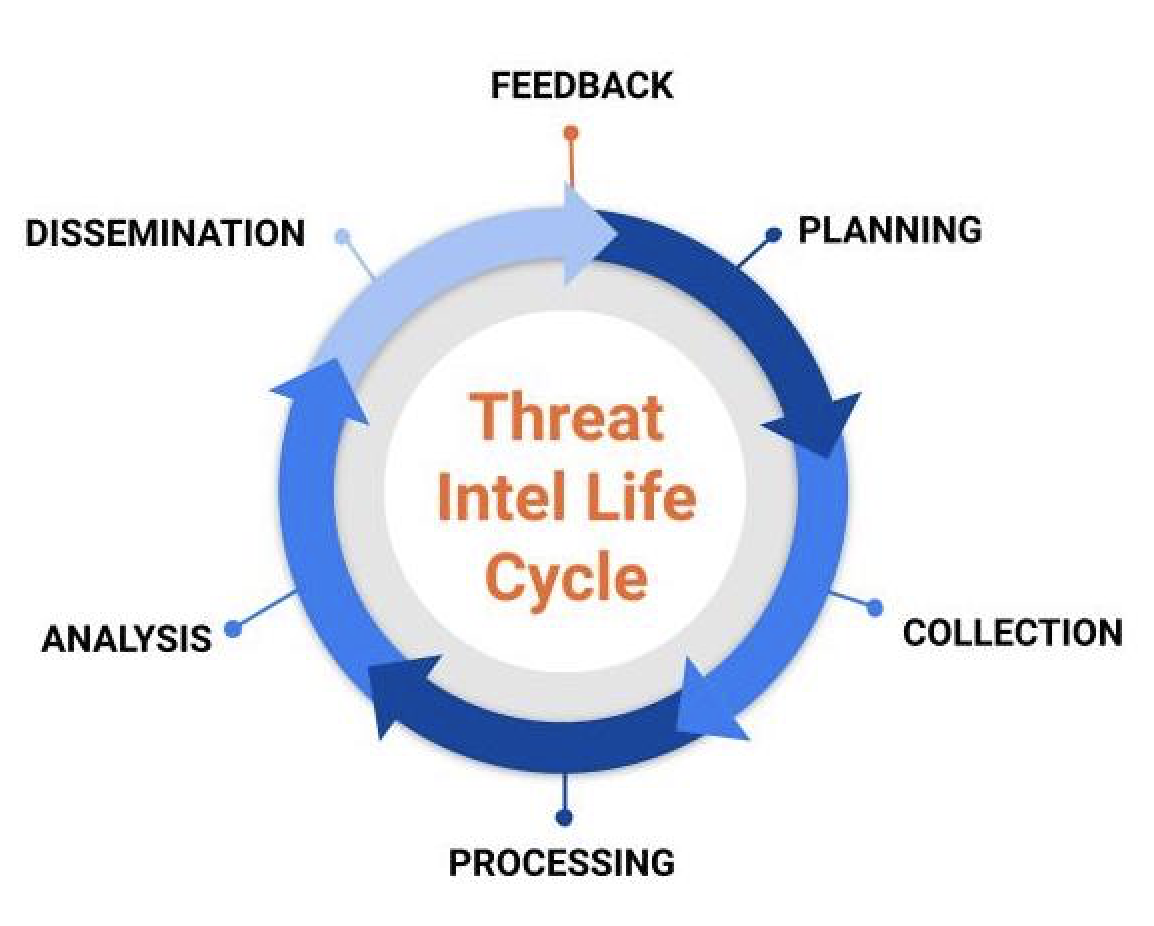
Current Threat Intel Lifecycle
The lifecycle forms the foundation of most cyber threat intel programs. However, there are challenges with implementing and operationalizing the lifecycle. For example, planning, direction, and requirements are the first phase in a lifecycle that logically flows from one phase to the next, yet organizations struggle with this phase. The 2022 SANS Cyber Threat Intel Survey shows that almost two-thirds of cybersecurity organizations lack defined intel requirements, and looking over the 4 years of data summarized in the report, it’s not improving.
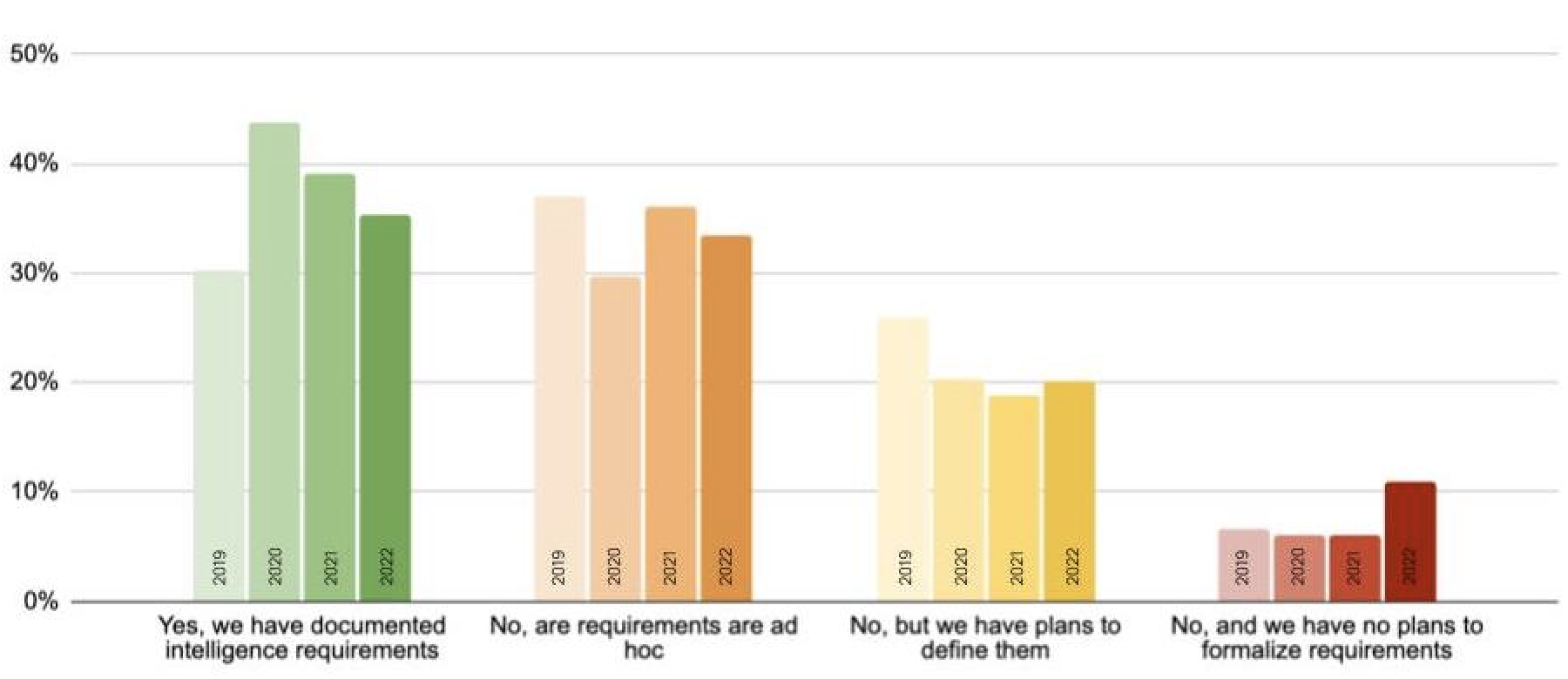
Source: SANS 2022 Cyber Threat Intelligence Survey
We hear the same thing from organizations that struggle in the dissemination and feedback stages. This seems obvious if there are no requirements or ad-hoc requirements with stakeholders. CTI teams can be great at producing the most high-fidelity intelligence, but if there aren’t any customers for the intel, then the value of the CTI program isn’t realized, and unfortunately, its relevance is challenged, particularly in these times of economic uncertainty.
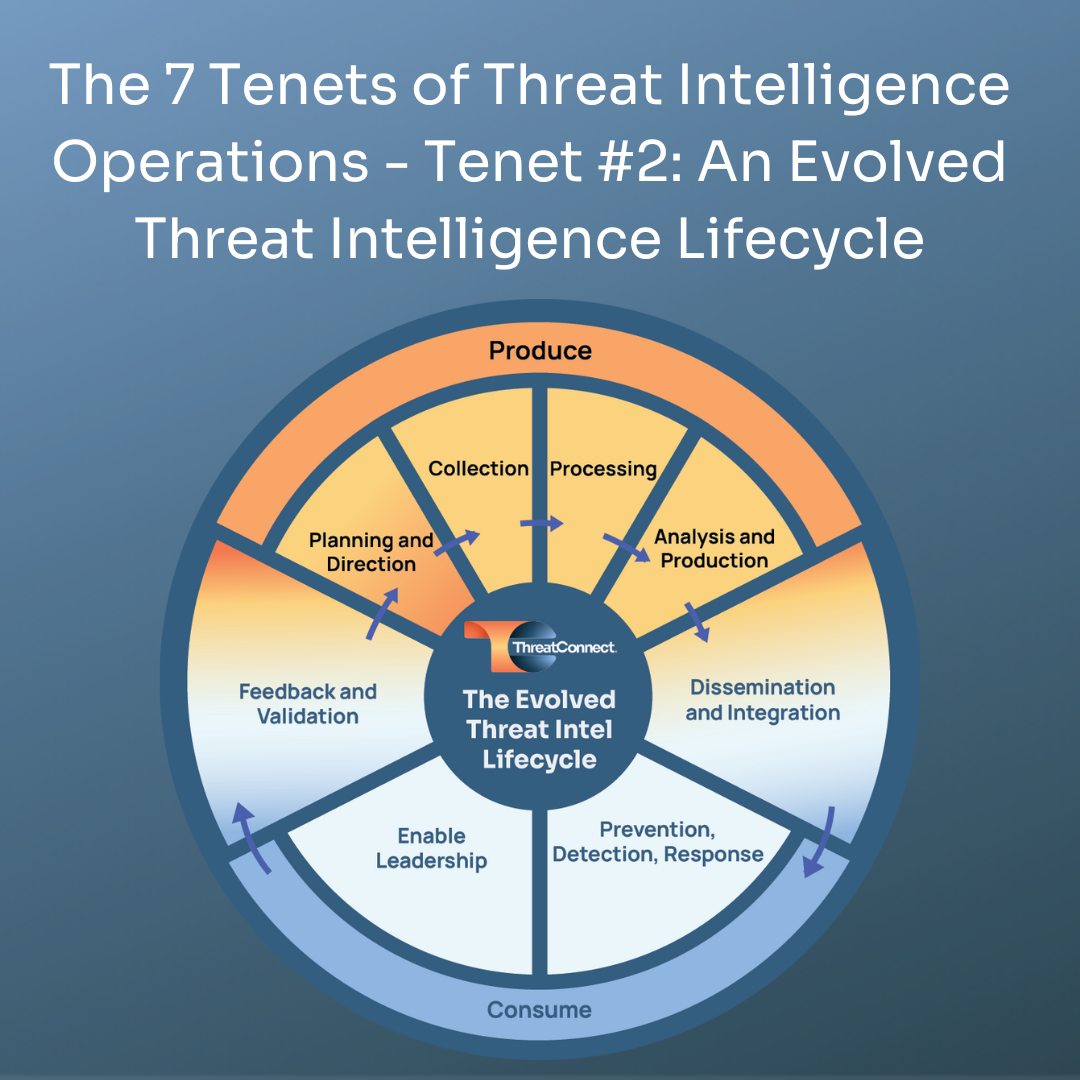
The Evolved Threat Intel Lifecycle expands on the current lifecycle making it more relevant to the needs of cybersecurity teams these days, e.g., it expands the focus on not just the management and production but the consumption of threat intelligence.
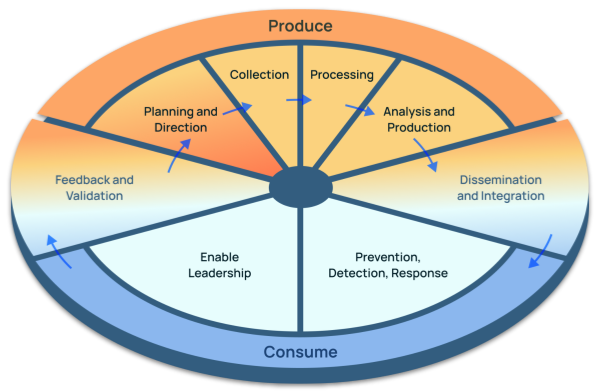
The Evolved Threat Intel Lifecycle
With this background, let’s get to the questions I asked Dan along with his insights.
Why do CTI teams need an evolution of the current threat intel lifecycle?
CTI teams need an evolution of the current threat intel lifecycle because the traditional lifecycle does not prioritize feedback and stakeholder involvement sufficiently. The drawbacks of the current lifecycle include:
- Insufficient focus on feedback and evaluation, hinders continuous improvement and the relevance of the intelligence gathered.
- Limited stakeholder involvement, can lead to a disconnect between the producers and consumers of intelligence and may result in under-utilization of the intelligence provided.
- The perception of CTI as a “nice-to-have” rather than an essential component of an organization’s security posture.
So why now?
The need for an evolved threat intel lifecycle is more urgent now due to several factors:
- The rapidly changing threat landscape and the increasing complexity of cyberattacks. Organizations face a myriad of threats from various sources, and staying ahead of these threats requires a more agile and collaborative approach to threat intelligence.
- The growing importance of collaboration and breaking down silos within security organizations. An evolved threat intel lifecycle fosters better communication between different teams, enabling a more unified and effective response to threats.
- The growing popularity of the fusion center model, which integrates various security functions and stakeholders to create a comprehensive and coordinated approach to threat management. The evolved threat intel lifecycle is well-aligned with this model, ensuring that threat intelligence is effectively integrated into broader security operations.
By adopting an evolved lifecycle, CTI teams can better address the challenges posed by sophisticated adversaries, help their organizations make more informed decisions to protect their assets and networks and contribute more effectively to the organization’s security posture.
How does the Evolved Threat Intel Lifecycle help CTI teams? What benefits should they expect by adopting this updated lifecycle?
The Evolved Threat Intel Lifecycle helps CTI teams by:
- Enhancing collaboration and communication between intelligence producers and consumers, ensuring that the intelligence gathered is effectively utilized by the relevant stakeholders.
- Fostering accountability and continuous improvement, with a strong focus on feedback and evaluation, to ensure the quality and relevance of the intelligence produced.
- Encouraging a more action-oriented approach to threat intelligence, moving beyond mere dissemination to actively informing decisions and driving effective responses to threats.
- Transforming CTI from a “nice-to-have” to a must-have: an essential part of security. This helps CTI teams demonstrate their value, build trust with their stakeholders, and contribute more effectively to the organization’s security posture.
By adopting this updated lifecycle, CTI teams can expect to see increased efficiency, improved decision-making, and better overall security posture for their organizations.
The Bottom Line
Embracing the Evolved Threat Intel Lifecycle is one of the important steps to achieving a TI Ops capability. It helps CTI teams become an integral part of Security Operations, demonstrating the power, and value, of threat intelligence.
Take the Next Step
If you’d like to learn more about the Evolved Threat Intel Lifecycle, check out Dan’s blog “The Need for an Evolved Threat Intel Lifecycle”. Reach out to one of our experts if you want to learn more about how the ThreatConnect Platform can help you operationalize the Evolved Threat Intel Lifecycle.
Check out our next blog in this series: