Posted
In the first blog of this series, I took a 30,000 foot view of the seven tenets of TI Ops defined in the Dawn of Threat Intelligence Operations paper. In this blog, I’m diving deeper into Tenet #4 – Focus is not solely on indicators of compromise, but expands to cover the motivations, tactics, techniques, trends, tools, and infrastructure patterns of threat actors.
Indicators of compromise are where the action is at for most CTI teams. They are plentiful, whether from commercial, open source, or community feeds, useful for threat detection, and consumable in machine-readable format by a wide variety of security tools. They have their place and aren’t going away any time soon. However, the variability in the fidelity of indicators is challenging. The feedback from our customers is that they are prone to false positives, and this has an effect on teams responsible for threat monitoring and triage, and incident response. The more false positives, the more challenging it is to assess and prioritize events and alerts. It even impacts threat hunters, who may think they are going to pull the thread with an indicator only to be taken down a rabbit hole that doesn’t lead to anything fruitful.
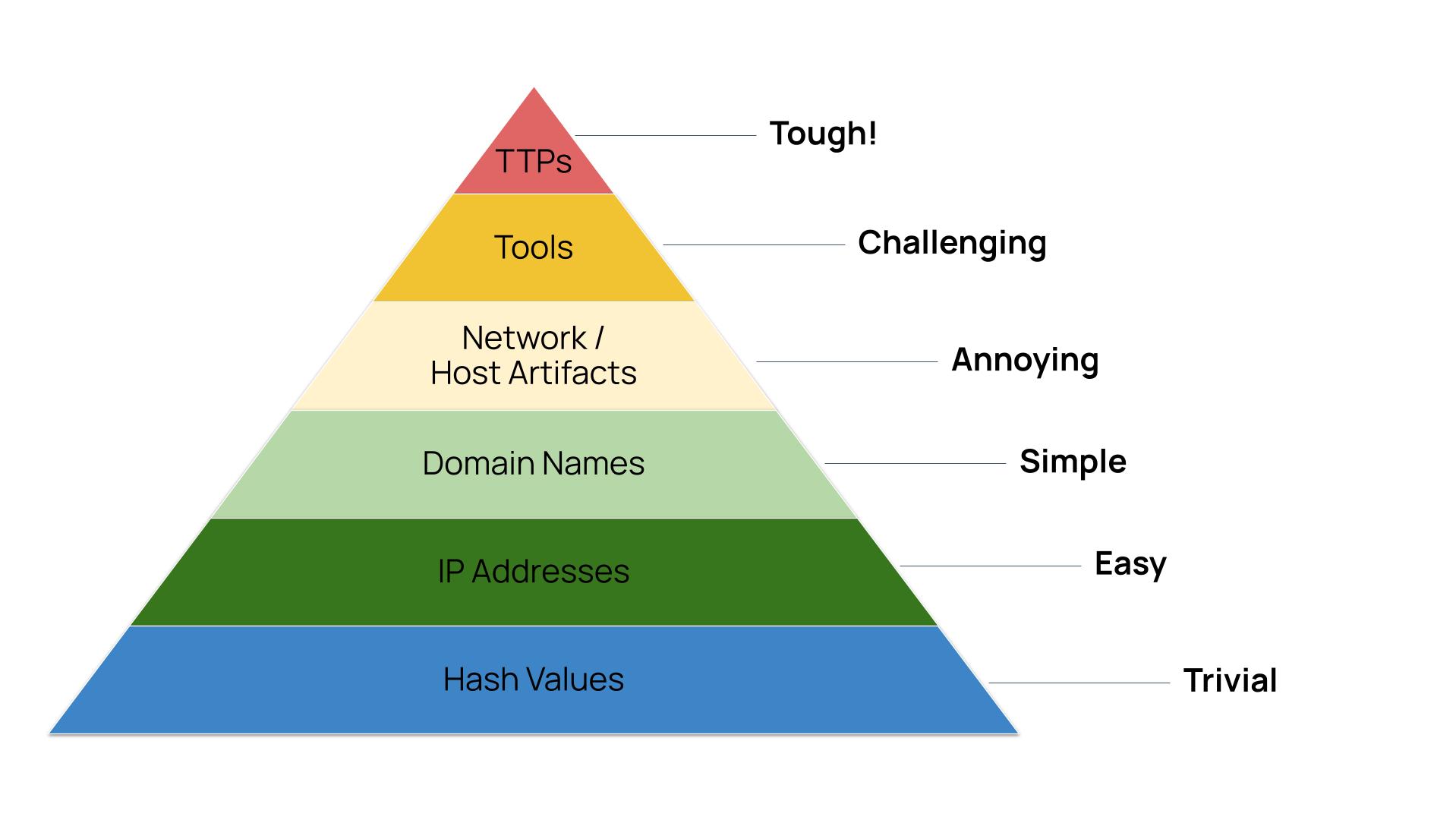
There is also the impact on the adversary. It’s important to keep in mind the role of David Bianco’s Pyramid of Pain. David explains it best, but the tl:dr is that defenders inflict low amounts of pain on adversaries when focusing on indicators to detect and block, and the most pain when they focus on their tactics, technical, and procedures (TTPs).
The answer to this challenge is to enhance the use of indicators to track attacker behavior through their TTPs. Indicators are still needed as they provide utility in filtering potentially malicious traffic and content, and generating events that can provide context to potential incidents. As CTI teams mature, this is one of the indicators (pardon the pun) of that maturity: moving beyond just indicator-driven CTI and incorporating adversary knowledge.
The excellent SANS 2023 CTI Survey reinforces this point – “This finding shows that even with the rise of tracking tactics, techniques, and procedures (TTPs), including with MITRE ATT&CK®, CTI personnel still find value in indicators as a key source. This is likely in part due to the ease of applying indicators in tools. Although indicators can play a role in CTI, organizations should consider, as their CTI function matures, how they can produce or consume beyond feeds of IOCs.” (p.9). This insight is what I see across the ThreatConnect community. More mature organizations have embraced the power of “and” – indicators and infrastructure and behaviors.
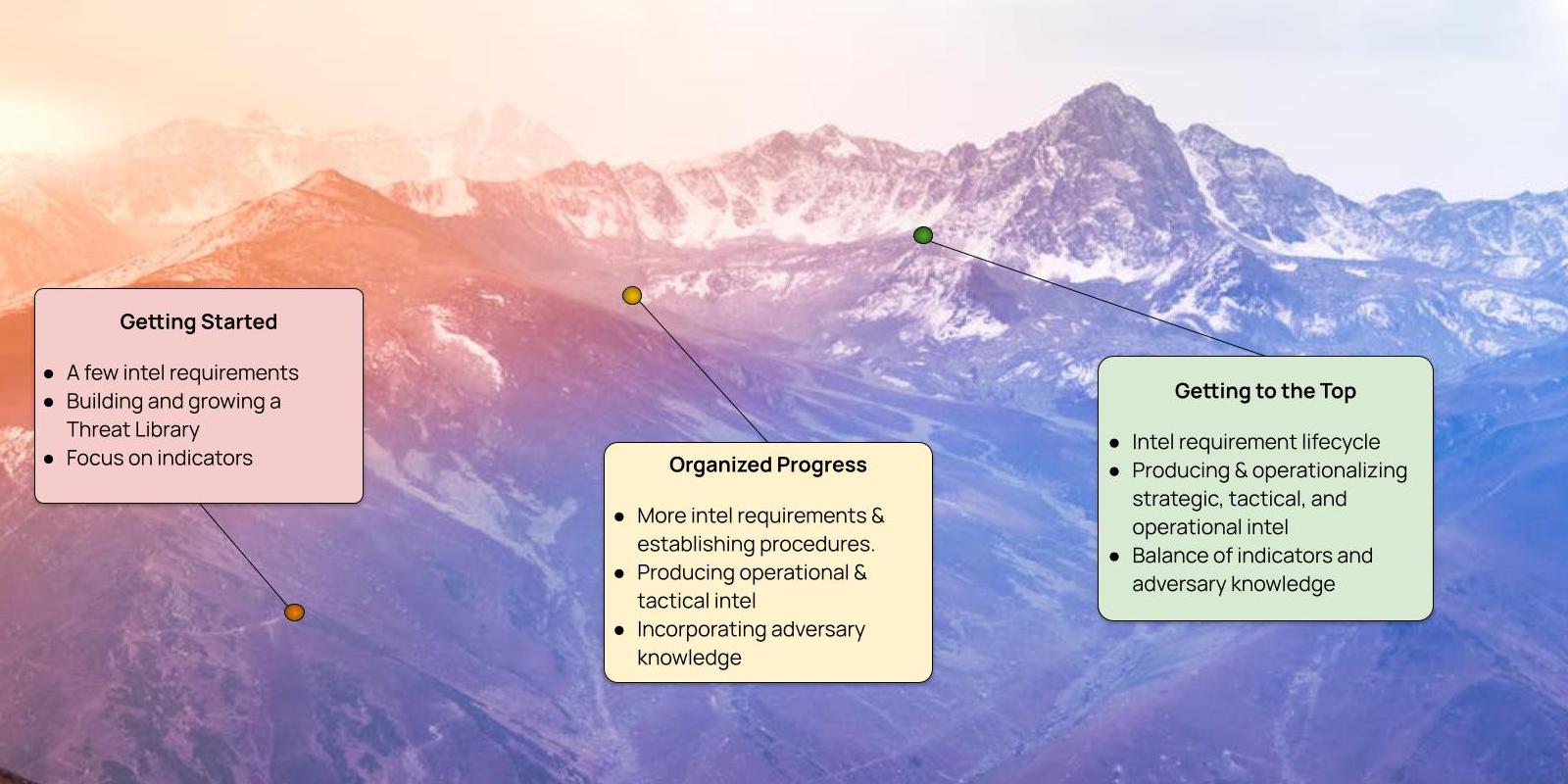
The organizations that are establishing and growing their CTI functions are primarily focused on operational intel. As they mature, they start to expand into tactical and strategic intel (although many get pulled into producing strategic intel through RFIs on the latest threats from other functions, like the SOC, architecture/engineering, and leadership). This is a natural and healthy progression. Someone getting into running isn’t going to go out and run a marathon after just a few days. Likewise, CTI teams have to start with a manageable number of intel requirements and deliverables that balance their current capabilities across people, processes, and tools. As analysts gain more skills and confidence, processes are established and refined, and tools move from spreadsheets to a dedicated platform, so does the maturity of the CTI team with a reasonable goal of being able to manage an increasing number of priority intel requirements (PIRs), RFI, etc. and collecting, analyzing, and disseminating the right type of intel for the stakeholder.
So how does a CTI team incorporate threat actor behaviors into their intel collection, analysis, and dissemination? The MITRE ATT&CK Framework is the most common answer to this question. If you’re not familiar with ATT&CK, it’s worth taking a few minutes to understand what it is and why it’s powerful. ATT&CK is one of those elements that has changed the game for cyber defenders by offering a common taxonomy and language to ensure security teams are all speaking the same language, much what the VERIS Frameworks did for incidents and breaches and the Cyber Kill Chain did for applying an intel-driven approach to analyzing how adversaries attacked their targets.
Applying ATT&CK allows intel teams and operational teams to map specific tactics and techniques used by a threat actor, and describe their procedures, and understand their tooling and behaviors. Once this level of understanding is achieved, then there are multiple benefits:
- Detections can be engineered that have a longer lifetime with fewer false positives, compared to detections that leverage indicators and are useful for an increasingly shorter amount of time, and are more prone to false positives.
- TTPs can be overlaid against the technical defenses of the organization to determine if there are gaps or over-investments in coverage.
- Defenders are now inflicting pain on the adversary and making it harder to compromise the organization
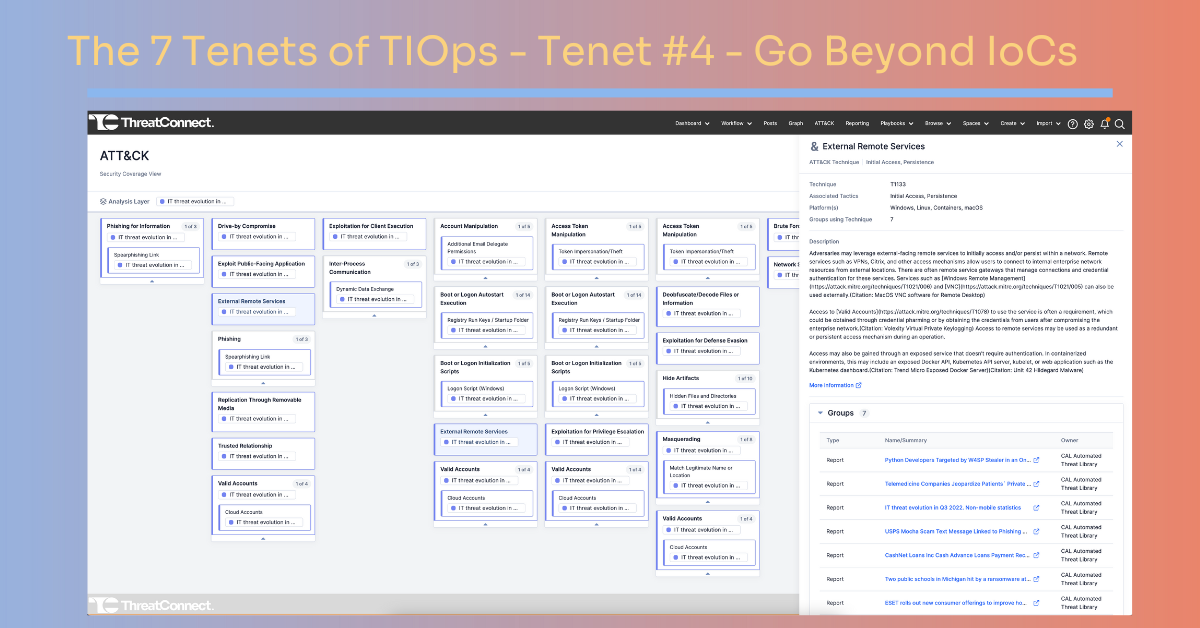
We recently introduced the ATT&CK Visualizer in the ThreatConnect Platform. This expands our existing support for the ATT&CK Framework by giving users a Navigator-like view, but our ATT&CK Visualizer goes well beyond just being yet-another-navigator. It allows you to “see” the TTPs captured in your own threat intel, analyze them, and take action.
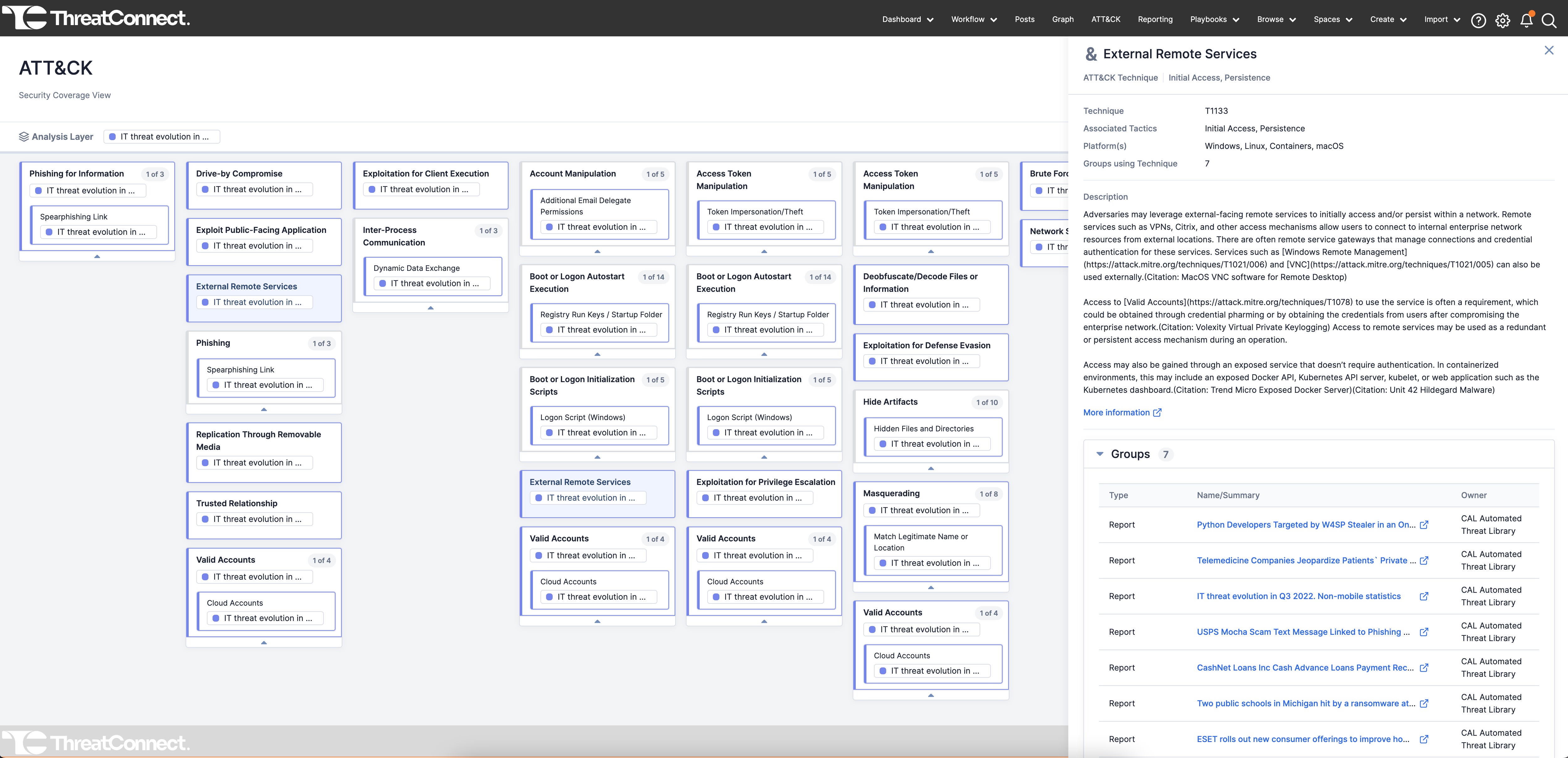
Click here to experience ThreatConnect’s ATT&CK Visualizer.
The Bottom Line
Focusing on indicators of compromise is necessary, but as threat actors adapt and evolve, so must CTI teams by learning more about their adversaries and putting that knowledge into action. The adversaries are learning everything about your organization, so you must learn everything you can about them!
Take the Next Step
While waiting for the next part of this series, read the Dawn of TI Ops paper, and keep an eye out on your favorite social media channels for the next post where I address Tenet 5 – Automates the work of the TI Ops team.