Posted
In the first blog of this series, I took a 30,000-foot view of the 7 Tenets of TI Ops defined in the Dawn of Threat Intelligence Operations paper. In this edition, I’m going to dig into Tenet #1 – Elevates threat intelligence to a mandatory, critical security operations role – in more detail.
In the various roles I’ve had over the years, I have observed CTI teams primarily being a function within the SOC. This makes sense as threat intel is a crucial element of threat monitoring, detection, and incident response, but it also limits the value that threat intel can provide across cybersecurity operations and cyber risk management. By elevating TI Ops to a peer-level role within security operations, threat intel becomes the core of how to transform SecOps into what we call Intelligence-Powered Security Operations.
Why is this elevation important? A failure of every team in an organization operating from and contributing to a common body of threat intelligence gives adversaries the advantage. An Intelligence-Powered Security Operations approach takes this advantage away by:
- Enhancing Prevention and Detection capabilities – Correlate data from your security tools with threat intelligence for more accurate alerting, blocking, and threat response
- Improving Response Time –The more knowledge you have about a particular threat, the faster you can respond to it
- Inform Security Policy and Controls – Ensure that your organization has the appropriate and optimized defenses in place for adversaries relevant to your organization
The formation of the concept of fusion centers after the 9/11 attacks in the U.S. is an apt reference point, especially as it established the foundations of cyber fusion centers and operations. There is a lot written already about intelligence sharing failures as one of the root causes for why terrorists were able to carry out successful attacks (see the 9/11 Commission Final Report ). The outcomes from the analyses highlighted how intelligence existed, but it was collected and leveraged in siloes, not widely shared with applicable stakeholders, and could not be operationalized. This sounds very much like how cyber threat intelligence exists for many organizations these days.
The recommendations to form fusion centers gave direction to state and federal government agencies to elevate their intelligence collection and sharing capabilities. I love the call to action for leadership from the Fusion Center Guidelines Developing and Sharing Information and Intelligence in a New Era, which is equally applicable to cybersecurity.
“In developing our country’s response to the threat of terrorism, law enforcement, public safety, and private sector leaders have recognized the need to improve the sharing of information and intelligence across agency borders. Every official involved in information and intelligence sharing has a stake in this initiative. Leaders must move forward with a new paradigm on the exchange of information and intelligence, one that includes the integration of law enforcement, public safety, and the private sector.”
However, it was not something that occurred overnight. It took years to see progress, and this is another important point in the journey to elevate threat intelligence – it’s a marathon, not a sprint, and more like a 100 miler in reality since technology, threats, and adversaries will all change and evolve, and therefore you won’t be able to just stop after 26.2 miles). Some of this progress is evident in the improvements within the cybersecurity community of sharing intelligence between organizations, such as ISACs and ISAOs. There are 27 ISACs that are part of the National Council of ISACs across a broad spectrum of industries.
Making some organization reporting changes can be seen as the “easy” path – elevate the CTI team to being a direct report of the CISO, and the problem is solved, right? Not at all. Building and sustaining a high-performant, value-delivering function requires more than changing an org chart. It requires:
- Getting leadership buy-in on a target operating model for the TI Ops function and securing a commitment to the required funding for multiple years (one year is not enough!)
- Identifying and engaging the right stakeholders to understand, document, agree, and prioritize their requirements and get sustained support.
- Hiring, developing, and maintaining TI Ops talent is a challenge. It’s estimated that millions of cybersecurity jobs are unfilled. Experience with cyber threat intelligence is a very specific class of talent that can be hard to find, and if you can find it, affording that talent might not be feasible. It’s possible to develop that talent, but that takes time too.
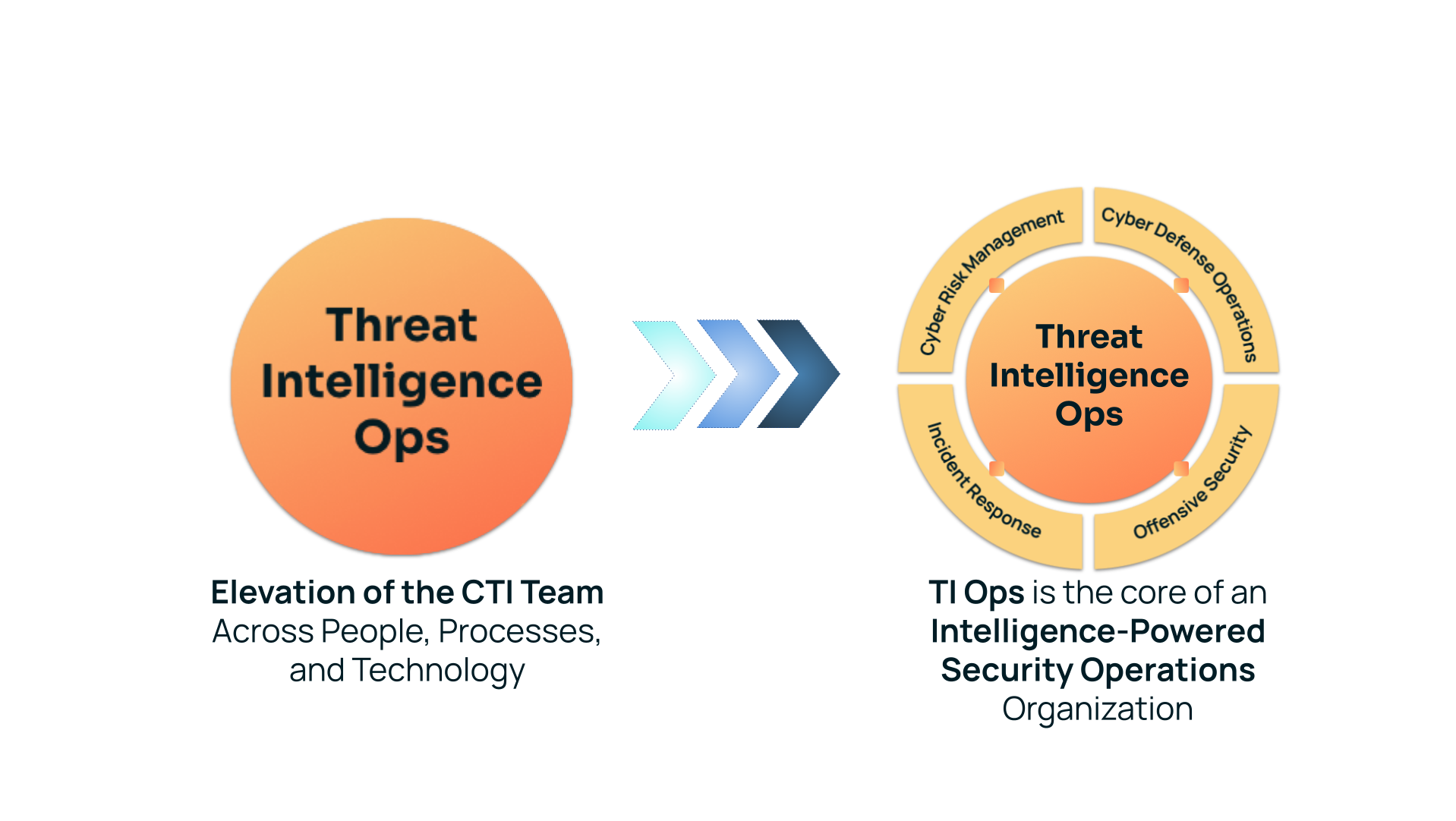
So by now, you’re probably thinking, “Too hard, too much work, etc. There is no way I’m getting a TI Ops function, and it’s going to be that important to my organization.” Don’t despair! I’ve seen both large, global, and very well-funded enterprises implement a TI Ops capability, but I’ve also seen midsize enterprises embrace the power of having threat intelligence be a core capability for their security and risk management operations. Sure, they didn’t have dozens of CTI or TI Ops analysts, but they didn’t need that. They did great with a couple of analysts. They invested in TI Ops because they recognized the payback to the overall security function was significant and the effort worthwhile.
The Bottom Line
TI Ops must be the future of CTI teams and functions in order to remain relevant to an organization’s cyber security and risk management program. By adopting the 7 Tenets of TI Ops, CISOs and SecOps leaders are going to gain an advantage over the adversaries, and any upper hand they get to make their organizations more defensible and resilient to attacks is a win.
Take the Next Step
Check out our next blog in this series: The 7 Tenets of Threat Intelligence Operations – Tenet #2: Requires an Evolved Threat Intelligence Lifecycle.
To learn more about our thoughts on the future of CTI teams, read the Dawn of TI Ops paper and be sure to subscribe to get notified of the latest blogs from ThreatConnect.
