Posted
In the first blog of this series, I took a 30,000-foot view of the seven tenets of TI Ops defined in the Dawn of Threat Intelligence Operations paper. In this blog, I’m diving deeper into Tenet #3 – Threat intel is aligned and focused on the most critical risks to the business through a living set of requirements
Threat intelligence is a critical function for cybersecurity and risk, however, it hasn’t been widely adopted and applied in a way where it is core to how security operations and cyber risk management are performed. Why? One crucial element is the lack of defined requirements with stakeholders. Threat intel is treated like a check-box exercise, e.g., check the box in security technology X and then check the box off the list of must-have controls. That approach will not suffice these days. CTI is a powerful tool against threat actors and adversaries, but many organizations don’t use it to effect. There are multiple data points that highlight the lack of requirements for threat intelligence, and this has a massive knock-on effect on a threat intel function and how they contribute to the organization’s risk management.
SANS’ 2023 CTI Survey indicates that 59% of organizations have defined requirements, also known as priority intelligence requirements (PIRs for short). It was getting worse for several years, but there was a significant increase from 2022 to 2023 (see the figures below from the survey). This is great news, but it also suggests there is still significant room for improvement.
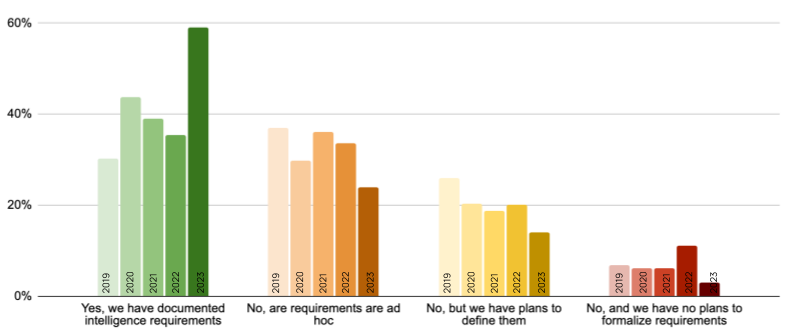
Another data point is from a recent survey on cyber threat intelligence by ESG that found “Twenty-three percent of security professionals believe that a mature CTI program must include well-defined goals, objectives, and metrics in pursuit of continuous program improvement.”
Houston! We have a problem.
Without requirements, how are CTI teams going to align their activities with the most critical risks to their organizations? Guessing and assuming are not the correct answers to this question. Building and managing requirements with the cyber risk team should follow a standard process:
- Identify the relevant cyber risk management stakeholders
- Educate those stakeholders on what CTI is (and isn’t), what intel data can be collected, and the types available outputs
- Agree and document the PIRs with stakeholders
- Produce and deliver relevant intel
- Incorporate feedback from stakeholders and refine PIRs as needed
The steps above come from the Evolved Threat Intel Lifecycle, which I covered in my previous blog discussing Tenet #2, put into practice. If you’d like to learn more about what makes a great PIR, my colleague Dan discusses The 7 Critical Elements of a Robust PIR in this blog.
The Role of Strategic Intel
As a brief reminder, there are commonly three types of CTI – operational, tactical, and strategic.
- Operational intel is primarily interested in Indicators like IP addresses, URLs, file hashes, etc.
- Tactical intel is interested in the TTPs of an attacker to inform proactive defenses measures, and aid threat hunts and offensive security activities.
- Strategic intel is the big picture intel that is used by leaders to understand the threat landscape in context of their organization (like trends), help make strategic decisions (e.g., where to invest resources to defend the organization), influence policies, etc.
Tactical and strategic intel are really important here, although operational intel will play a role in some scenarios. Some examples of how strategic and tactical intel are leveraged by stakeholders includes:
- Understanding which threat actors are targeting an organization’s industry, their standard operating procedures (SOPs) and their impacts (e.g., how much revenue was lost due to a ransomware attack).
- Emerging trends by threat actors that could increase the risk to critical assets and business processes, requiring investments to ensure risk levels remain within agreed tolerances.
- The threats against suppliers and 3rd parties providing services and technologies to the organization to ensure the risk from suppliers is managed and the organization is resilient to attacks and disruptions to their supply chains.
- Knowing the vulnerabilities being actively exploited in the wild, by which threat actors, and for what purposes.
So now that we understand how threat intel drives cyber risk management, let’s look at the benefits of a threat intel-informed cyber risk management approach.
- The ability to prioritize the remediation of exposures in your attack surface, e.g., which vulnerabilities do I remediate first, which applications do I prioritize?
- Which controls should be prioritized, whether that’s updating configurations, expanding coverage, upgrading, or implementing new controls to address coverage gaps?
Being able to answer these questions makes response activities laser-focused, which drives faster risk mitigation while minimizing the impact to resource-constrained teams.
Other benefits include:
- Improving the accuracy of risk assessments. This is an important benefit as risks assessments, whether cyber, physical, or digital suffer when they are overly qualitative. Applying relevant threat intelligence enhances the fidelity of the assessment. For example, you can apply specific knowledge about which threat actors may be attacking an application that a business unit wants to bring into the organization. This context can influence the required security controls and how they are applied.
- Supporting supply chain and 3rd party risk management. The risks with suppliers have grown in importance as adversaries focus on alternative attack vectors, e.g., infiltrating software vendors. I covered this in more depth in a previous blog (https://threatconnect.com/blog/why-threat-intel-is-critical-for-supply-chain-security/).
- Providing context to digital business risks (e.g., brand). Threat actors aren’t just targeting endpoints and VPNs. They will also go after an organization’s digital assets, like domains and marketing websites. These can be effectively abused to make ransomware and BEC attacks look more legitimate, for example standing up fake websites under a sub-domain in order to steal account details and create more realistic phishing emails. It also creates brand reputation risks when these types of attacks are successful.
The Bottom Line
High-fidelity threat intelligence is not only for security operations. It has a significant role to play in cyber risk management as well. By adopting the 7 Tenets of TI Ops, CTI teams, SecOps teams, and cyber risk teams all benefit in their goal of protecting their organization from attacks and adversaries and helping the organization stay within their risk tolerance zones.
Take the Next Step
While waiting for the next part of this series, read the Dawn of TI Ops paper, and keep an eye out on your favorite social media channels for the next post where I address Tenet 4 – Focus is not solely on indicators of compromise but expands to cover the motivations, tactics, techniques, trends, tools, and infrastructure patterns of threat actors.