Posted
Over a decade ago, Forrester Research introduced the concept of zero trust. Today, zero trust is considered one of the leading frameworks to guide information and security architects in the design of robust and resilient information security architectures. This is a very important aspect of zero trust – it’s a framework that influences security architectures and not a singular technology that you buy.
Zero trust starts out with some very different principles to help you architect your defenses. The legacy concept of a trusted internal network zone, and an untrusted external network zone, are no longer adequate. Zero trust essentially posits that no data traffic or user can be trusted just because of their position within the network. It is now assumed that at any time, any portion of the network can and will be compromised. Users, therefore, must go through re-authentication and validation at every step of the experience.
Zero trust architectures have shown to bring compelling value. They are a best practice way for government and private enterprises to add the layers of necessary security to manage and protect sensitive information while rapidly taking advantage of and supporting digital transformation initiatives and the value that those bring.
There are a few key best practices that guide users in building out their own zero trust architectures.
- To begin, data is the core element that must be continually protected. Any access to this data will require authentication and revalidation.
- Understanding the flow of data is critical to designing the micro-networks in which that data moves. Access to these micro-networks is to be similarly protected.
- Finally, in order to build a robust and scalable zero trust architecture, you must have deep visibility of activity, be able to monitor and log this activity, and then analyze this data to understand if malicious activity is ongoing.
In order to get the speed of execution and scale, the technologies implemented for a zero trust approach must be able to integrate and be orchestrated.
The Role of Threat Intelligence in a Zero Trust Architecture
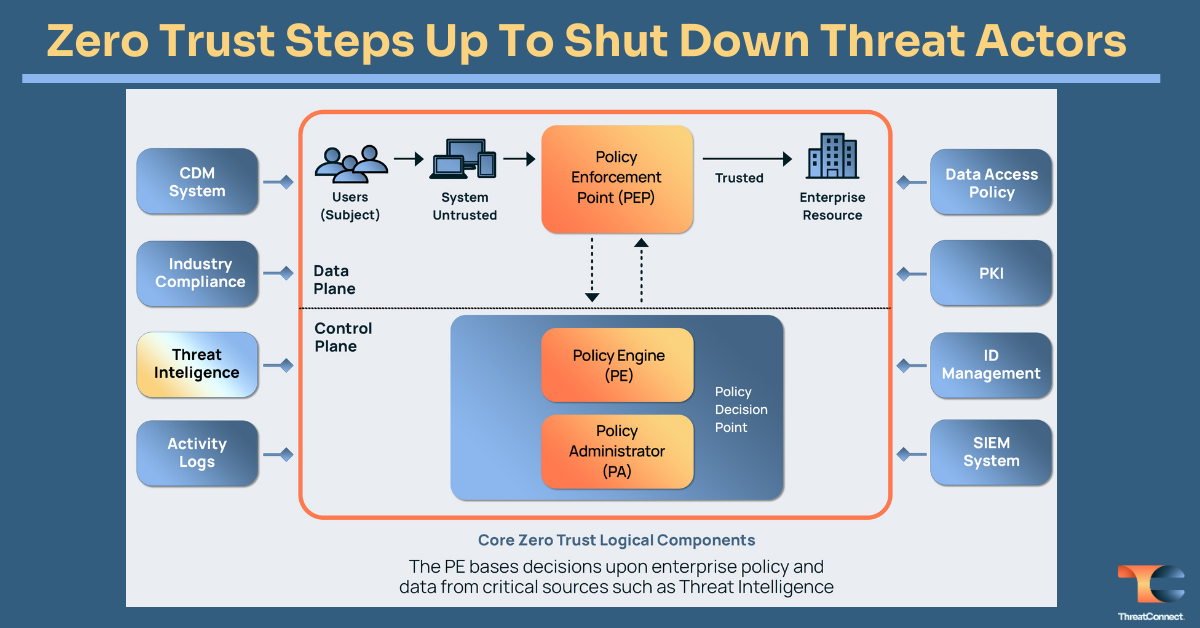
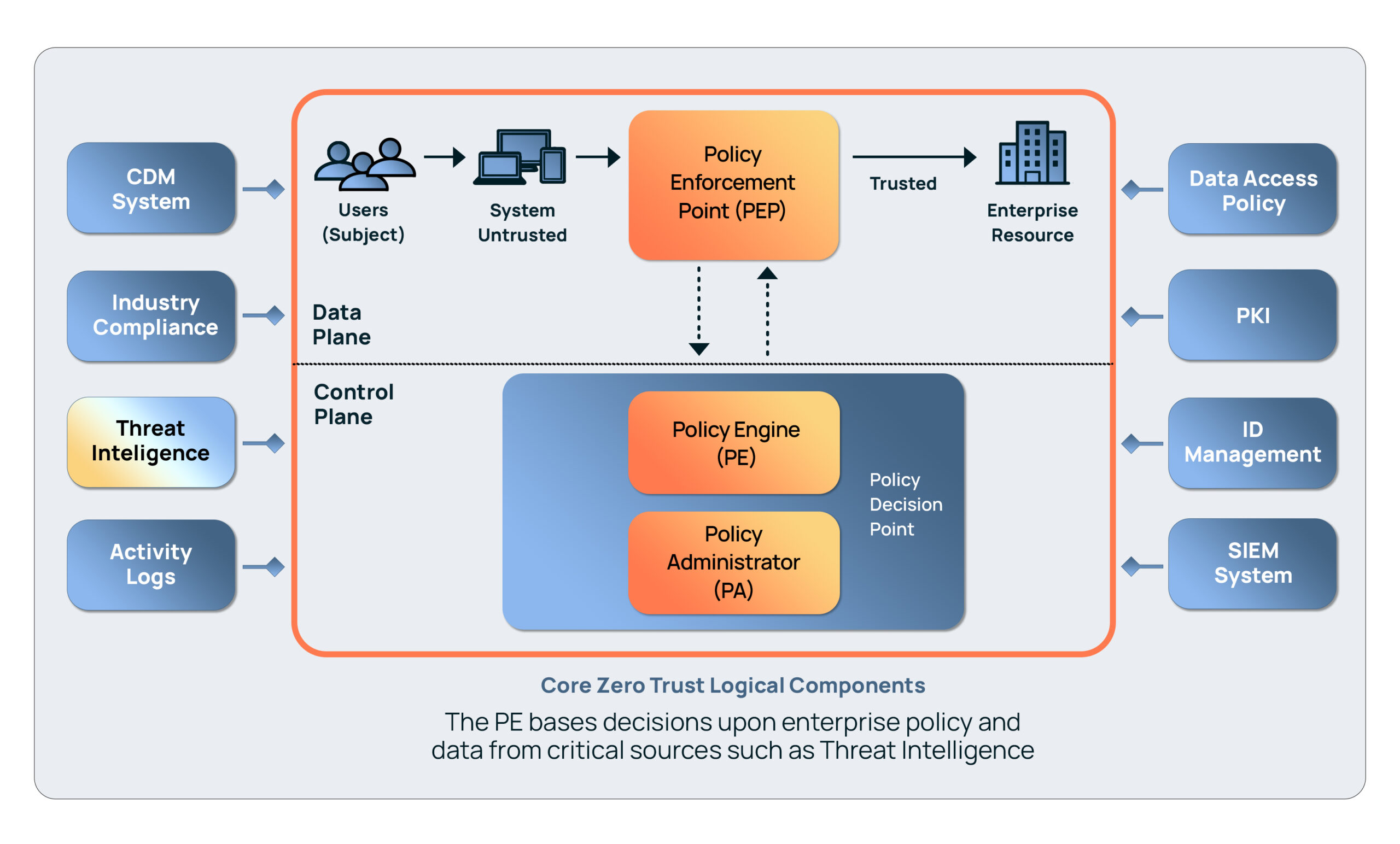
Zero trust implementations require context. Why? NIST800-207 explains it well. Access to each enterprise resource, like applications and data, is granted on a per-session basis. Access to resources is determined by A dynamic policy. The enterprise monitors the state of the security posture of all assets. Resource authentication and approval are dynamic and strictly enforced prior to allowing access.
Threat intelligence provides critical context to address these tenets of zero trust. In NIST 800-207, Figure 2: Core Zero Trust Logical Components specifically addresses threat intelligence as a logical input into a zero trust control plane. NIST800-207 states, “The [Policy Engine] PE uses enterprise policy as well as input from external sources (e.g., CDM systems, threat intelligence services described below) as input to a trust algorithm … to grant, deny, or revoke access to the resource.”
Without a single source of high-fidelity threat intel, there can be potential challenges in integrating threat intel into your zero trust control plane.
- Intel sources – If you have multiple threat intel data sources and feeds, you have to make sure the data is optimized to be ingested by your policy engine. Will all your intel sources integrate with your policy engine? How well will a policy engine handle duplicative intel? Will that create a resource constraint on that engine?
- Connectivity overhead – You may have a lot of overhead making sure multiple integrations stay working and up-to-date in the event of any events, e.g. changes to APIs.
- Intel reliability – Relying on intel that hasn’t been refined can lead to false positives without ensuring it is of sufficient quality. Without this assurance, end users may have a negative experience if they are unable to access critical resources in a timely manner due to low-fidelity threat intel.
So how do you avoid these potential challenges? Here’s how the ThreatConnect Platform helps you avoid these challenges and provides high-quality and reliable context in a zero trust architecture.
- Threat Library – Your organization’s single source of threat intelligence. The Threat Library leverages an industry-leading data model to normalize, optimize, and make available any type of intel data and knowledge.
- CAL™ Global Intelligence – using AI and ML-powered insights into threats and indicators and the industry’s largest ground-truth threat telemetry from the global ThreatConnect user community. CAL’s™ Automated Threat Library, CAL™ Feeds, ThreatAssess intel scoring, and Feed Cards ensure highly relevant, accurate, and reliable intel is supporting your zero trust technologies.
- Easy Connectivity – Out-of-the-box integrations via Apps, and a flexible API for any custom integrations.
- Flexible automation, from no-code to custom code, makes your daily management and operationalization of threat intelligence easier and faster.
Just having a single source of threat intelligence is not enough to achieve a successful zero-trust architecture. Having robust, performant, and reliable intelligence feeding the decision-making elements in your zero trust architecture is vital to ensure that the security tools are protecting and defending your organization, not impeding and causing unnecessary disruptions.
Learn More
Want to learn how ThreatConnect fills a critical need in your zero trust architecture? Reach out today to speak to one of our experts to learn more or to request a demo of the ThreatConnect Platform.
Read Next: