
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.

Looking Forward To Seeing You At SecTor 2023!
We’ll be at SecTor 2023, will you? ThreatConnect is excited to once again be attending SecTor in Toronto, Canada. We are looking forward to catching up with customers and friends, talking about threat intel operations and cyber risk quantification, and hearing about some exciting topics. SecTor 2022 was awesome, and we expect 2023 to be […]

The Tenets of Threat Intel Operations: Tenet #7 – Measure for Success
In the first blog of this series, I took a 30,000 foot view of the seven tenets of TI Ops defined in the Dawn of Threat Intelligence Operations paper. In this blog, the last in the series, I’m discussing Tenet 7 – Creates measures of effectiveness and success for produced and consumed threat intel that are […]
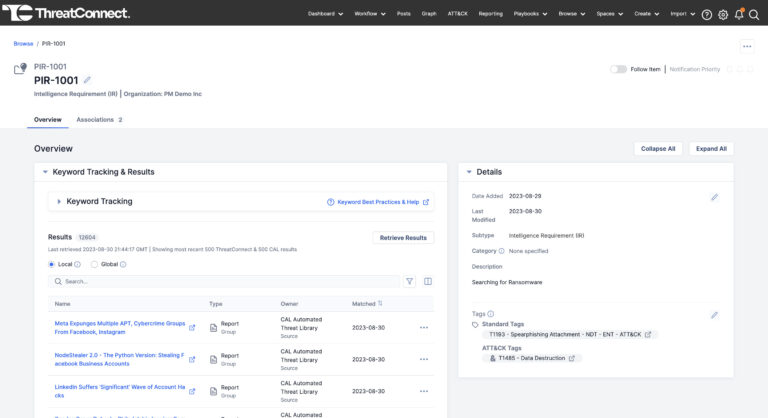
ThreatConnect 7.3: Leverage the power of Intelligence Requirements and ATT&CK Visualizer
Today, we’re launching version 7.3 of the ThreatConnect TI Ops Platform. This marks an exciting occasion as we roll out this update, delivering substantial enhancements to our customers through a range of new capabilities and improvements. Our latest updates include our new Intelligence Requirements capability, ATT&CK Visualizer v2, the latest update to ThreatConnect’s native ATT&CK […]
The 7 Tenets of Threat Intelligence Operations – Tenet #6: Integrates and Automates Threat Intel
In the first blog of this series, I took a 30,000 foot view of the seven tenets of TI Ops defined in the Dawn of Threat Intelligence Operations paper. In this blog, I’m diving deeper into Tenet 6 – Integrates and automates threat intel into every aspect of security and cyber risk management. Once you have […]

Cyber Risk Quantification and the SEC Rules on Cybersecurity
As the risk of cybersecurity incidents increases, the need to be more proactive and increase organizational resilience to cyber attacks is needed. The U.S. Securities and Exchange Commission (SEC) recently released guidelines that publicly traded companies must follow for proper cybersecurity risk management, strategy, governance, and incident disclosure. This blog discusses – essential aspects of […]

Introducing the ThreatConnect Threat Intelligence Operations Buyers Guide
I’m excited to announce the release of ThreatConnect’s Threat Intelligence Operations Buyers Guide. The need for this type of guide is critical as the adoption of cyber threat intel (CTI) grows, and cybersecurity teams starting this journey need an understanding of what is required to implement and grow a TI Ops function. I continue to […]

Top 3 User Group Takeaways from ThreatConnect Customers
ThreatConnect hosted four customer user groups in 2023, and we are grateful to our customers for providing invaluable insights. These insights will inform our product roadmap and our users’ shared strategies on how to get the most out of ThreatConnect. These events have served as a platform for sharing knowledge, exchanging ideas, and fostering collaborative […]

Intelligence-Powered Cybersecurity for State, Local, and Territorial Governments
State, local, and tribal (SLT) governments are responsible for numerous critical services like educating children, providing safe drinking water, delivering safety and emergency services, managing airports, and administering elections. Yet, the threat landscape for SLT governments is getting even more hostile. Ransomware gangs are increasingly indiscriminate regarding who they target and impact. Sophos’ “The State […]
The 7 Tenets of Threat Intelligence Operations – Tenet #5: Automate TI Ops Work
In the first blog of this series, I took a 30,000 foot view of the seven tenets of TI Ops defined in the Dawn of Threat Intelligence Operations paper. In this blog, I’m diving deeper into Tenet 5 – Automate TI Ops Work Automate the work of the TI Ops team Automation has permeated our […]

Create Intelligence Requirements in 5 Easy Steps
How to Understand Intelligence Requirements As threat landscapes morph, intelligence requirements have emerged as a vital tool for cyber threat research and analysis. These are topics or research questions centered on an organization’s cyber threat priorities. They guide the Security or Threat Intelligence Team’s research and analysis efforts, providing valuable insights into threats, vulnerabilities, and […]

Top 5 Use Cases for ATT&CK Visualizer
The cybersecurity landscape is complex and fraught with many threats and vulnerabilities. Understanding and navigating this space requires access to up-to-date information on the activities of threat actors, which you can get through ThreatConnect ATT&CK Visualizer. What is ATT&CK Visualizer? ThreatConnect ATT&CK Visualizer is our new interactive platform capability that visualizes the MITRE ATT&CK matrix […]
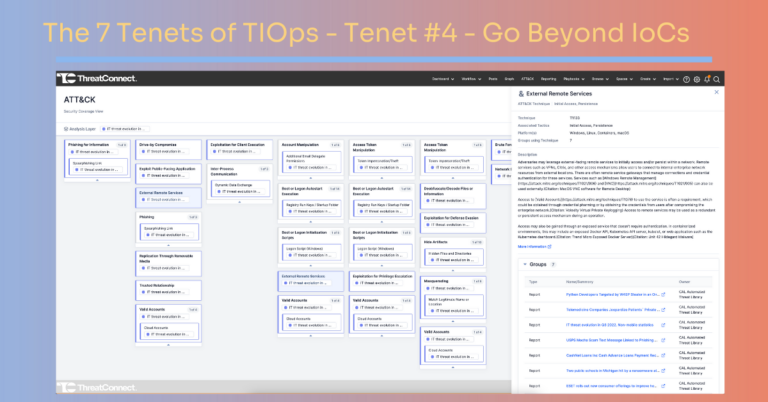
The 7 Tenets of Threat Intelligence Operations – Tenet #4 – Go Beyond IoCs
In the first blog of this series, I took a 30,000 foot view of the seven tenets of TI Ops defined in the Dawn of Threat Intelligence Operations paper. In this blog, I’m diving deeper into Tenet #4 – Focus is not solely on indicators of compromise, but expands to cover the motivations, tactics, techniques, […]
