Posted
ThreatConnect Risk Quantifier was recently named a leader in The Forrester Wave™ for Cyber Risk Quantification (CRQ), Q3 2023 and we couldn’t be more excited for the recognition. We’ve grown over the years from a small team trying to solve a hard problem to one leveraging the best of AI and ML as a leader in the CRQ space. To see Forrester rate us with the top score in the current offering category and the highest possible marks in the user experience, integrations, and methodology criteria (to name a few) is something to celebrate.
The Forrester report made a very astute observation in their report about our approach and strategy. They said that “ThreatConnect sets the standard for a threat-driven approach to CRQ”. That’s a great statement, and we couldn’t agree more.
We initially created RQ to be able to help organizations understand their cyber risk in financial terms, to identify where (and how much) they could transfer to cyber insurance, and – arguably most importantly – prioritize mitigations based on financial risk reduction. That last piece – the financial risk reductions – is core to RQ as we see security as a business function, not just a technical function. Just showing that a risk exists isn’t enough – CRQ needs to provide actionable, tactical options for how to mitigate and potentially remove that risk.
We spend a significant amount of time looking at loss data and attack data, and our analysis shows that there is a direct correlation between the financial loss caused by a cyber attack and the technical characteristics of the attack in question. In fact, the correlation is so clear we put it into the product (an example screenshot is shown below)
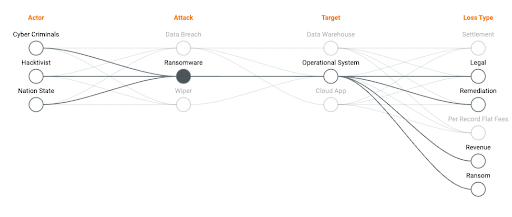
The data shows that a loss is incurred when an actor launches an attack on technical assets (e.g. endpoints) and beats the surrounding defenses. Loss and attack type are correlated – they are not independent. You will have a different loss posture to a data breach attack than you will to a ransomware attack. The controls that help prevent the attack from succeeding vary in effectiveness against different attacks (and MITRE TTP’s) too.
That’s why we’re committed to not only “setting the standard” for a threat-based approach to CRQ but to making sure we can trace results from the executive level to the security and business leaders, and into the Security Operations Center (SOC). This actionable traceability is how CRQ becomes part of a continuous monitoring effort.
Today most organizations run CRQ on an ad-hoc or scenario basis. The challenge here is that you can miss the forest for the trees. Threats change regularly, and most ad-hoc scenario building doesn’t adapt at that speed. By tying threat analytics with risk quantification using AI and Machine Learning, we can better measure when your risk exceeds your acceptable limit and – most importantly – help you mitigate the technical risk before it gets realized.
What sometimes gets lost in the CRQ conversation is the fact that what you mitigate is technical or threat-focused. You transfer financial loss (to insurance or a partner), but to prevent it from happening requires an understanding of the attack surface and how attacks materialize against defenses. That’s why we’re in complete agreement that ThreatConnect sets the standard for a threat-driven approach to CRQ.
Our goal is to continue to empower CRQ decision-making at multiple levels, including the executive, operational and tactical levels. After all, if you can prevent a threat from becoming a loss event by fixing a deficiency in the system, why wouldn’t you?
You can learn more about ThreatConnect RQ here. You can read your complimentary version of the Forrester Wave ™ for Cyber Risk Quantification, Q3 2023 here.
