Posted
Security teams need to move at the speed of the business. Teams don’t want to be slowed down by burdensome tasks like manually digging through threat intel or manually triaging alerts. They want to make fast, easy decisions to identify and protect against the most relevant threats. We’ve got you covered! In the 6.6 release of the ThreatConnect Platform we have added exciting new features to maximize the impact of your security team:
- Even more capabilities in Graph View that will have you quickly linking datasets you’ve only dreamed of.
- Adding more context for faster and easier alert triage
- And a few other updates in the Platform, like dashboard export and import.
Graph View Improvements
For CTI teams and threat hunters, having an elegant, easy way to visualize associations between intel sources is essential for crafting a data-driven story around the risks and threats to the business.
ThreatConnect 6.6 continues to improve on the Graph View capabilities. Where previously users could explore in the Collective Analytics Layer (CAL™) and pivot from indicator to indicator, with this release, users can also pivot between Groups both within their ThreatConnect dataset as well as in the CAL dataset to perform link analysis.
CAL provides anonymized, crowdsourced intel about threats and indicators. It leverages the collective insight of the thousands of analysts who use ThreatConnect around the globe to provide teams with even more context regarding indicators and threats to their business.
With the ability to pivot on Groups in CAL, analysts can visually explore the associations between Intrusion Sets and MITRE ATT&CK® techniques, malware, and tools they leverage. Users can access the Group alias information available in CAL. This feature, effectively a Rosetta Stone for threat actors groups, aggregates the different aliases given to these threat actors. . The ability to cluster groups with associated aliases makes an analyst’s job less burdensome in that they no longer have to keep track of this information on their own. This is a critical capability when it comes to quickly understanding the severity of a threat and allows users to add relevant indicators to their threat library for future analysis and investigation efforts.
Additionally, users can save the Graphs they create, enabling them to work on or view the Graph at a later time and/or collaborate with colleagues.
These updates to the Graph View better enables cyber threat intelligence teams to visualize the threat landscape in their environment. Linking associations helps CTI teams determine where to focus their attention, ultimately powering the security operations team with intel to better prioritize, so they don’t waste their time on meaningless alerts like false-positives.
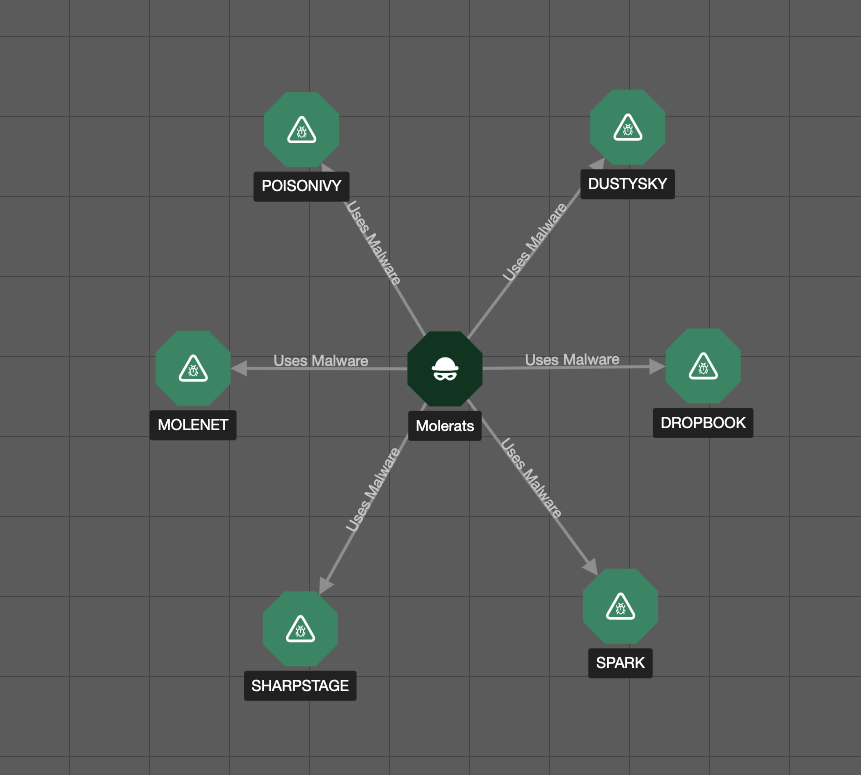
View Group relationships in CAL
With the updates to the Graph View, you can perform investigations faster and easier by:
- Visualizing relationships between indicators and Groups
- Identifying Group relationships in CAL and leveraging known associated aliases
- Saving Graphs for later use and sharing
Alert Triage Enhancements
If you’re in security operations, you know there’s no shortage of security tools which, consequently, come with an abundance of alerts. Quickly triaging and identifying which alerts to prioritize can be difficult when you’re digging through the piles of alerts filled with false-positives and low severity events. To make matters worse, alerts can be duplicative, with dozens of alerts related to a single event.
ThreatConnect 6.6 includes alert triage enhancements to make alert triage easier and faster. Users will be able to:
- Perform more accurate investigations with more context from similar alerts,
- Identify and triage similar alerts at the same time using bulk operations, and
- Respond to real threats faster by using CAL-powered Case prioritization.
ThreatConnect now enables analysts to perform more accurate investigations by providing more context around potential Case associations for a given Case. When alerts come in from security tools like your SIEM, a case is created, and analysts triage the case to identify and prioritize based on the severity of the risk to the business.
When viewing a case, analysts will be able to view related cases and the artifact(s) associated with those cases for users to better understand the relationship. Grouping cases linked by the same Indicator of Compromise (IOC) adds more context for analysts for quick triage.
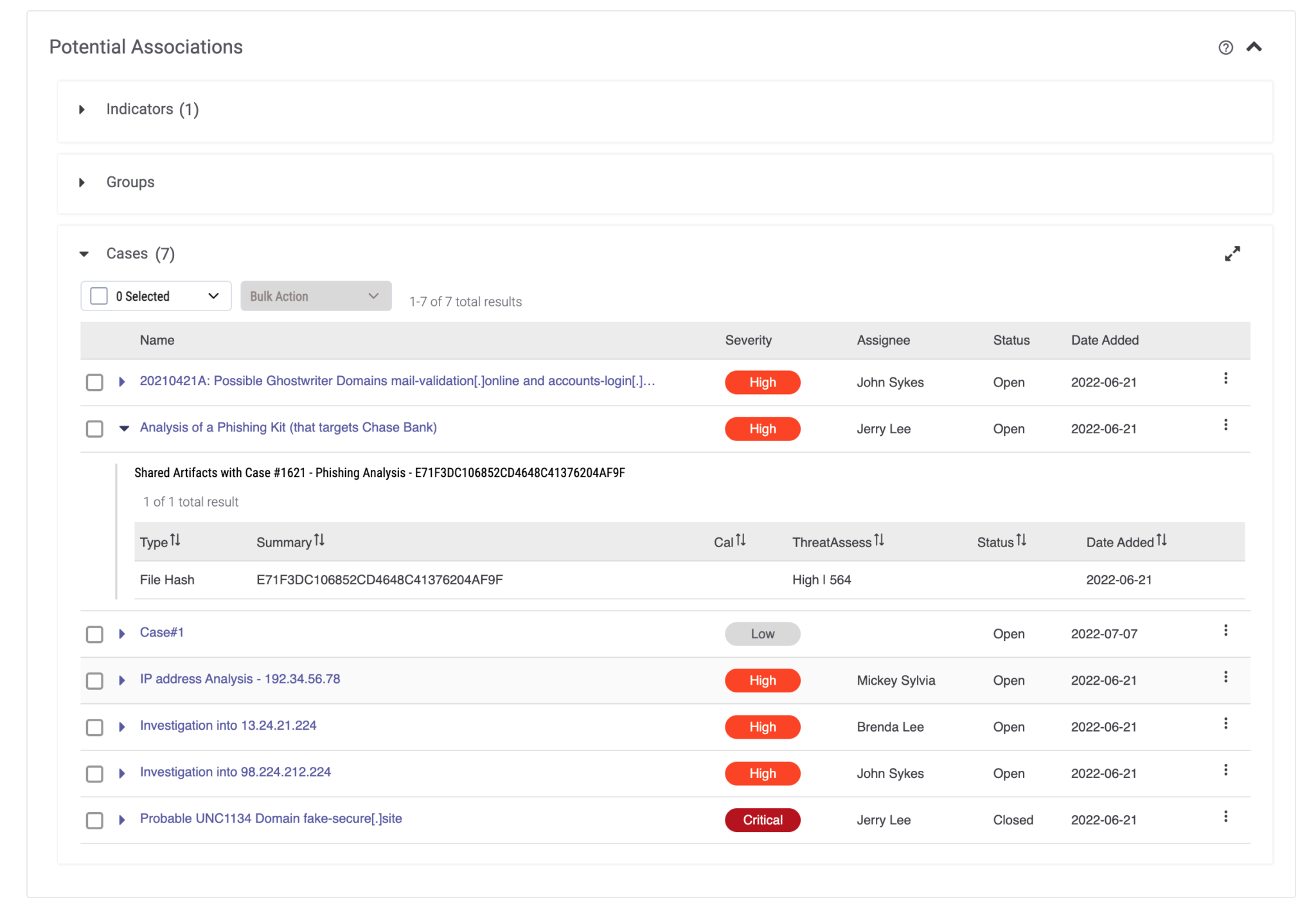
View context around potential Case associations
Additionally, analysts can perform Bulk Case Operations. Rather than spending endless hours sifting through alerts one-by-one, users can identify and triage alerts with the same IOCs to make changes including the severity, status, assignee, and resolution. This means users can bulk close out a slew of false-positives in just a few quick clicks or assign groups of alerts to the same analyst, rather than having multiple analysts siloed and working on similar alerts.
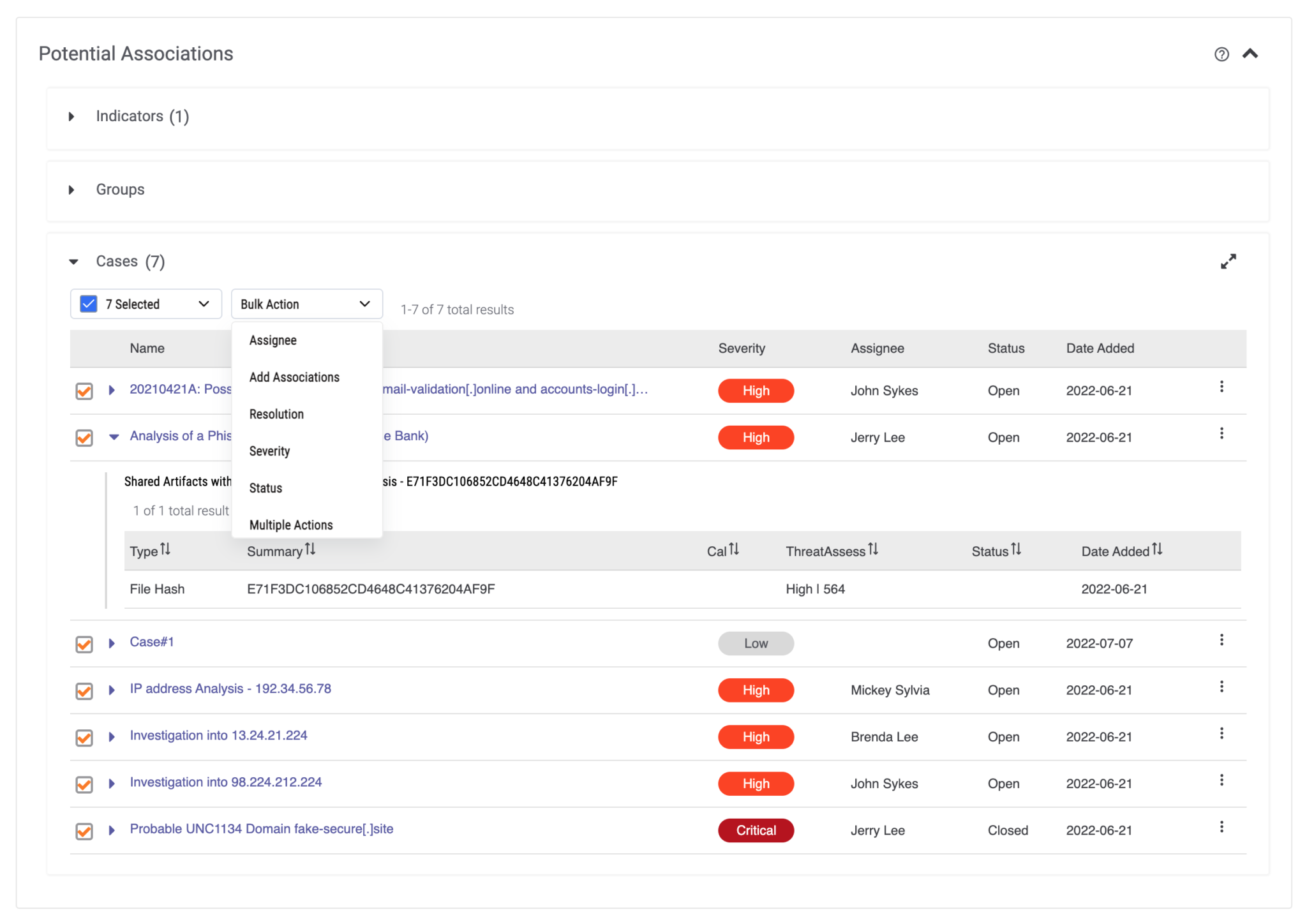
Perform bulk actions on Cases
Users will reduce time spent on alert volume by performing bulk actions on related Cases including:
- Severity
- Status
- Assignee
- Resolution
- Association of cases in potential association
ThreatConnect Alert Triage Enhancements comes with a native CAL Powered Case Prioritization enabling analysts to respond to real threats, fast. Analysts can use CAL and ThreatAssess scores to prioritize alerts and focus on Cases that need immediate attention. When an analyst knows which alerts to prioritize, dwell time of threats is reduced, speeding up the time to resolutions while reducing alert fatigue.
Other Super Cool Updates
We have added some other super cool updates in the 6.6 release to improve the user experience for analysts and leaders.
- Dashboard Export and Import
- System Wide Deprecation Rules
- Analyst Workload Cases Metric
Dashboard Export and Import
Users are now able to export dashboards from one ThreatConnect instance and import them into another. The new Export Dashboard option makes it easy to save dashboard configuration files to uploaded and imported.
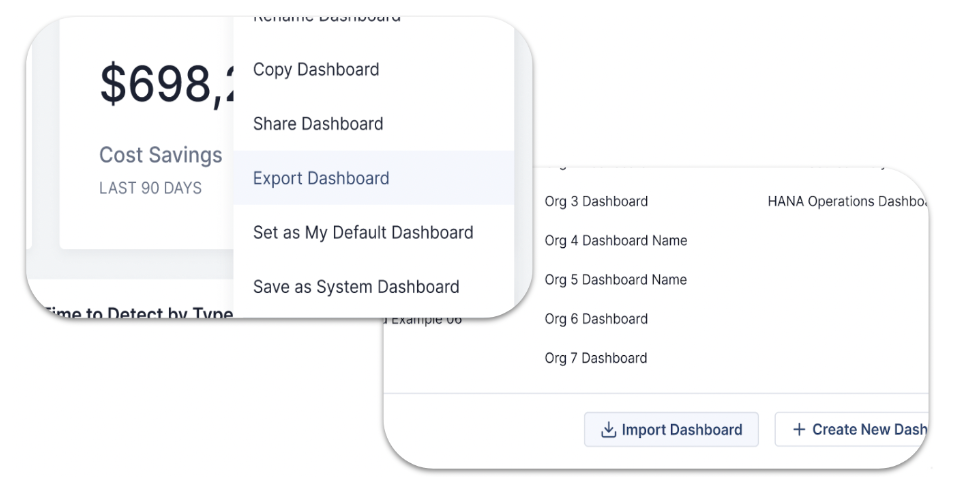
Export and import dashboards
For more information on these new capabilities and how ThreatConnect can help your organization super-charge your threat intelligence and security teams, please reach out to sales@threatconnect.com or /request-a-demo/
