Posted
Cyber Intel Analysis is a growing concern for organizations of all sizes. Staying ahead of evolving digital threats can seem like an impossible task. That’s where ThreatConnect’s TI Ops Platform comes in, offering a powerful solution to guide your CTI efforts through ThreatConnect Intelligence Requirements. The best part? Creating and managing your Intelligence Requirements (IRs) and finding objects in ThreatConnect that may be relevant to your IRs is now simpler than ever!
Let’s explore how easy it is to use Intelligence Requirements to set up your IRs. This new, streamlined capability in the TI Ops Platform can be completed in three easy steps: “Fill in the Details,” “Track Keywords,” and “View Results and Save.”
Step 1: Fill in the Details
To get started, simply log into your ThreatConnect account. On the top navigation bar, select Create and then Intelligence Requirement (IR). This step is where you provide key details about your IR:
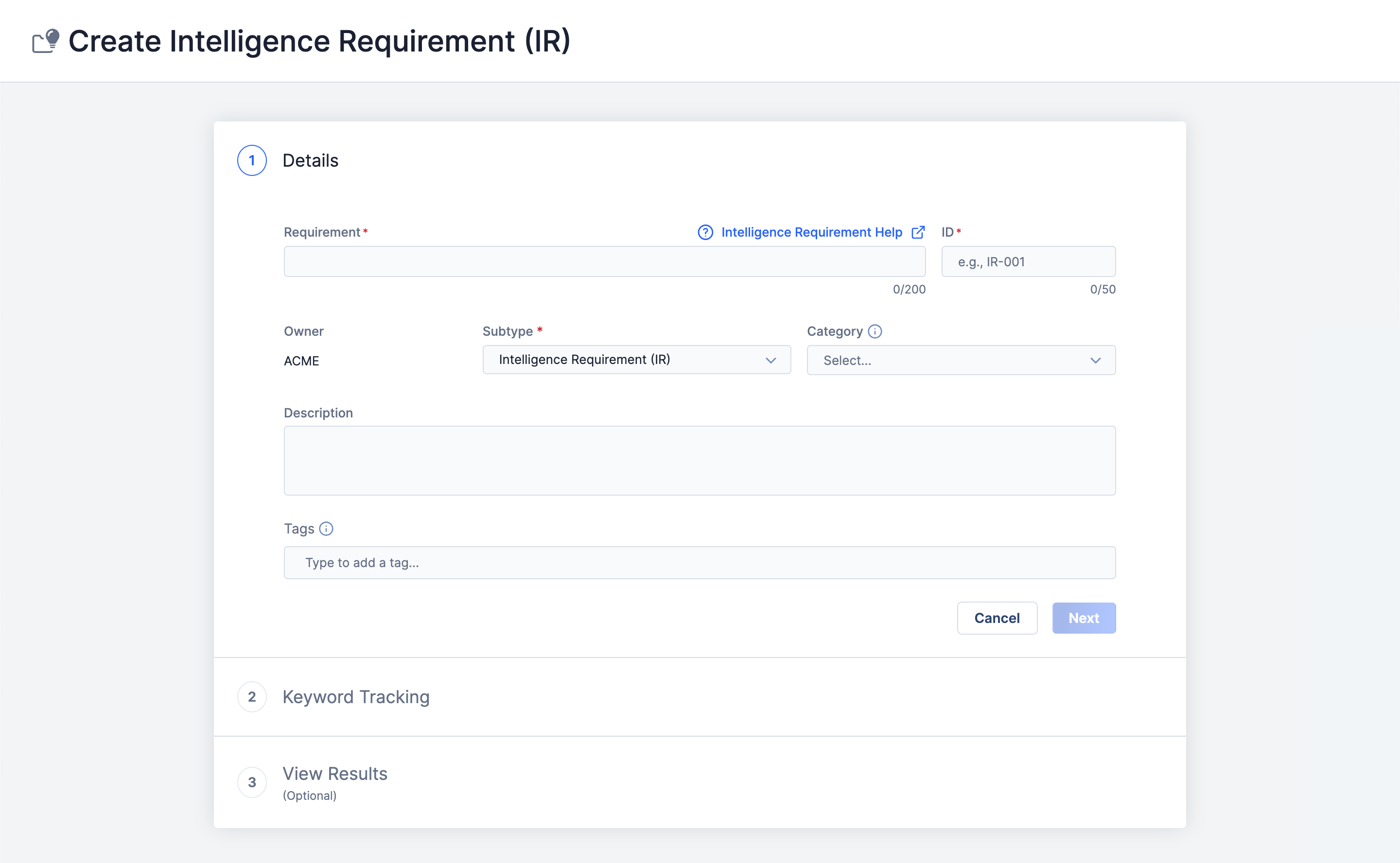
Fill in the following details for your IR:
Requirement: The central question, topic, or statement your IR focuses on. Click here to learn more about what goes into writing a robust IR for further insights.
ID: A unique identifier to distinguish your IR from others.
Owner: The organization your IR belongs to.
Subtype: This is where you choose the subtype for your IR. Options include”Intelligence Requirement (IR), Priority Intelligence Requirement (PIR), Specific Intelligence Requirement (SIR), Request for Information (RFI), and Research Requirement (RR). Choose what fits your needs.
Category: Select an existing category or None. Your System Administrator sets up categories.
Description: Brief context for your IR.
Tags: One or more Tags to organize and find your IR easily.
Click Next to move on to keywords.
Step 2: Track Keywords
The next step is to define a keyword query for your IR:
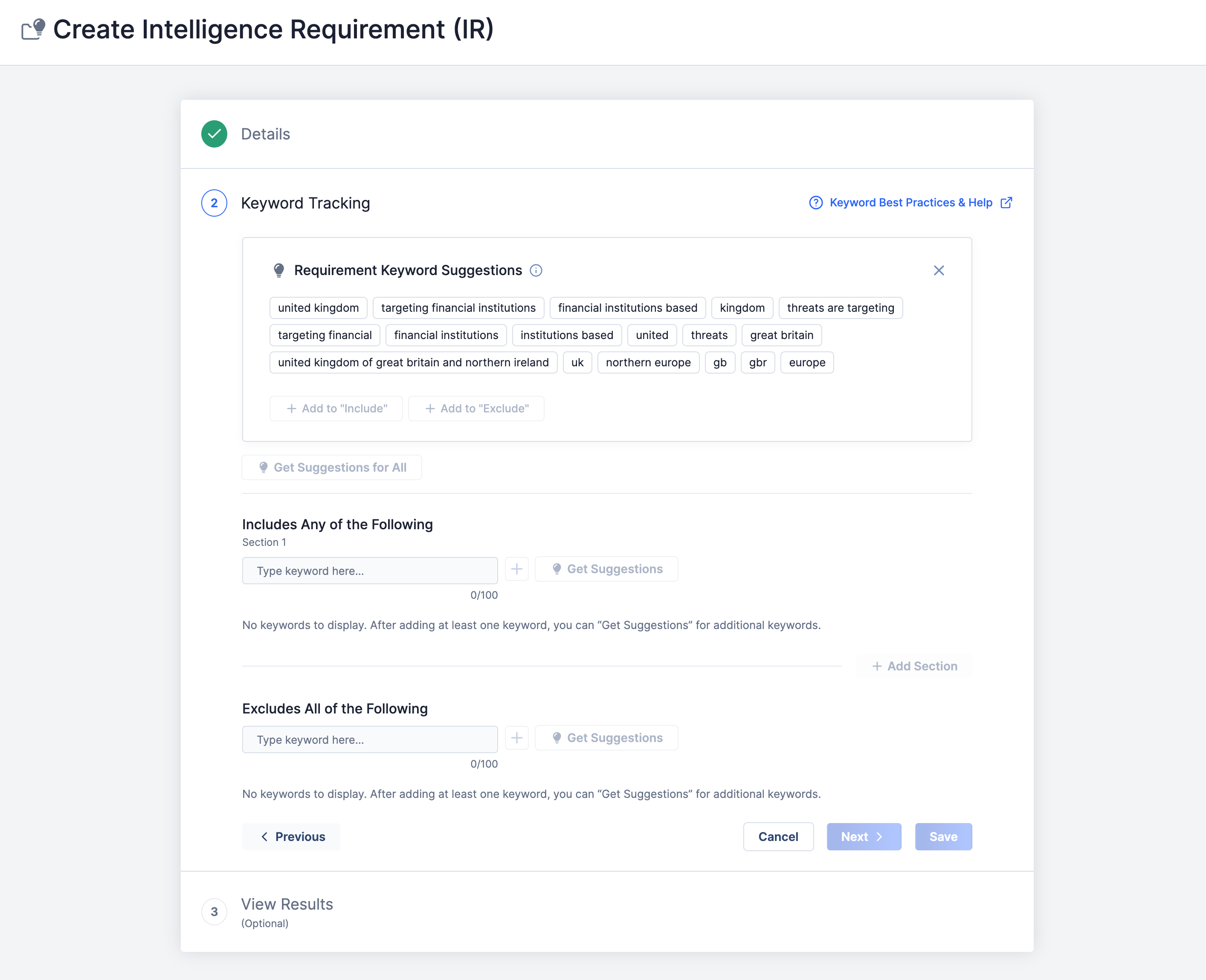
Requirement Keyword Suggestions: The system suggests keywords based on what you entered in the Requirement field. You can use these keywords to tell the system what kind of information you want it to return about your IR. Select keywords that you want the results to include, and then click the + Add to “Include” button. Select keywords that you want the results to exclude, and then click the “Add to Exclude” button.
Includes Any of the Following: This section lists all the keywords you selected to be included as search terms for your IR’s results. The system will use “OR” logic between them when searching for results.
Excludes All of the Following: This section lists all the keywords you selected to be excluded as search terms for your IR’s results. The system uses “AND NOT” logic between them when searching for results.
Click Save to move on to the results.
Step 3: View Results and Save
Now you get to see initial results based on your IR’s keyword query. You can view both local results and global results.
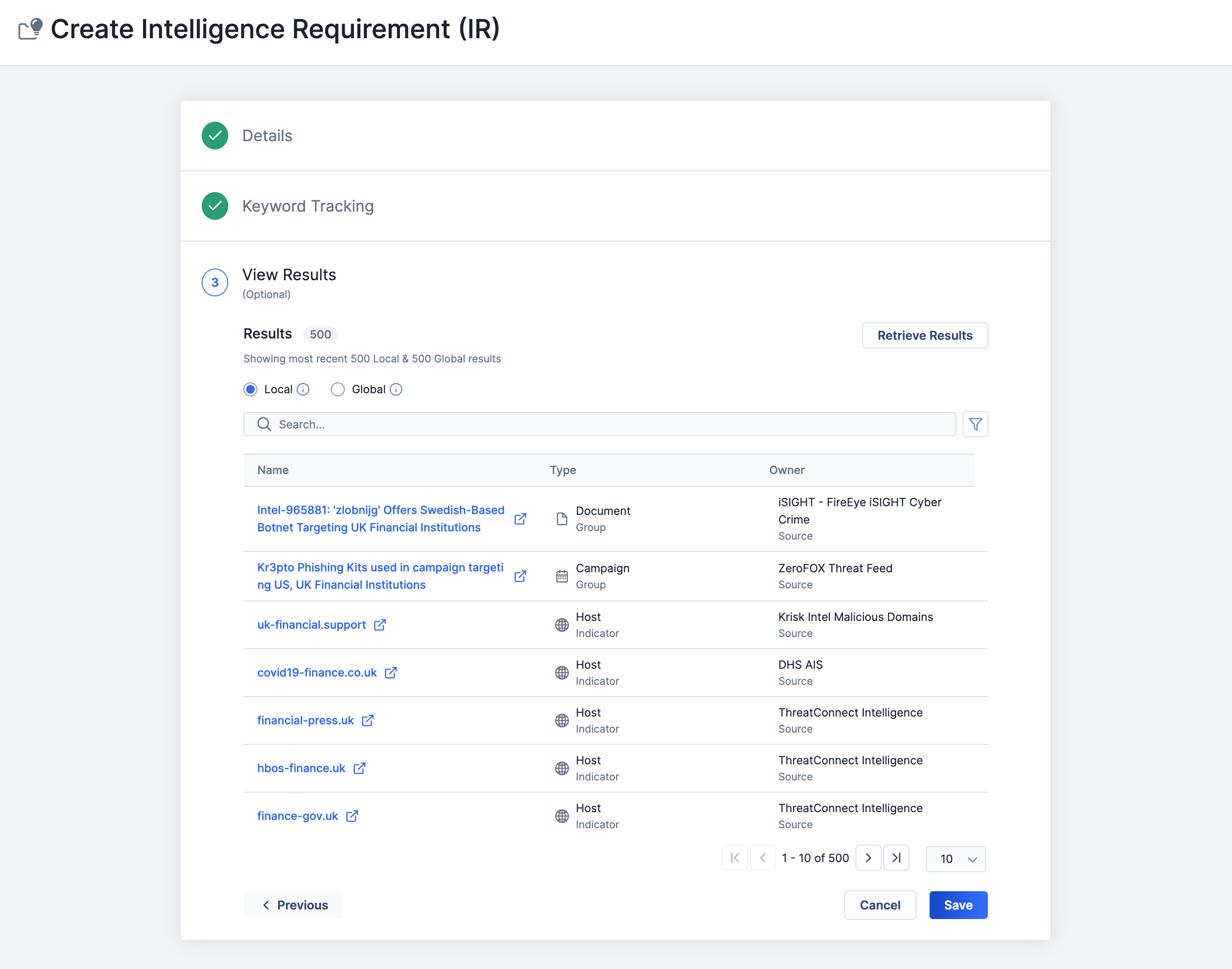
Local Results: These results are objects in your ThreatConnect owners (Organization, Communities, and Sources) that match to the keyword query you set up in the previous step. You can filter by owner or type, or search by name. Click each result to view its Details screen.
Global Results: These results are objects in the ThreatConnect Global Intelligence Dataset that match to the keyword query you set up in the previous step. Filter by type, or search by name. If you can access the CAL Automated Threat Library Source, you can click a result in this Source to view its Details screen.
Click Save to create your IR. You’re done!
Prepare Your Intel Requirements
Now you’ve seen how easy it is to get your IRs set up in ThreatConnect’s TI Ops Platform. You may be thinking, “Hey, I don’t even know what my org’s IRs are or if we even have any.” No problem…
It’s ok if you feel like you’re behind and we can even help! Discover the art of building a cohesive ecosystem of intelligence requirements so you can build a robust and effective threat intelligence function. Immerse yourself in the realm of intelligence requirements through ThreatConnect’s “Operationalizing Intelligence Requirements: A Comprehensive Guide.”
In this guide, you’ll explore a spectrum of intelligence requirements, ranging from Geographic to Industry and Technology considerations. Delve into the nuances of Priority Intelligence Requirements, Special Intelligence Requirements, and more, while learning how to craft effective requirements that elevate your threat intelligence program.
Amplify Your Threat Intelligence with TI Ops Platform
In addition to helping you create and manage IRs, ThreatConnect offers a variety of other features to empower your cybersecurity efforts. These features include threat intelligence sharing, data enrichment, and automation capabilities. Organizations can stay ahead of digital threats by utilizing these tools with Intelligence Requirements and minimizing their risk exposure.
Another benefit of using Intelligence Requirements is that they enable you to collaborate with multiple teams and organizations. This allows for a more comprehensive approach to threat intelligence, with various perspectives and expertises coming together to address potential risks.
Beyond Intelligence Requirements, ThreatConnect’s TI Ops Platform offers customizable dashboards and reports, providing organizations with valuable insights into the threat landscape. By accurately tracking and monitoring IRs and other key metrics, organizations can make data-driven decisions to improve their security strategies continuously.
ThreatConnect offers a comprehensive solution for creating and managing IRs and a variety of other features to strengthen your cybersecurity efforts. Don’t wait any longer – empower your cybersecurity with ThreatConnect today!
To read more about this, check out our Operationalizing Intelligence Requirements: A Comprehensive Guide
Authored By:
- Abbie Baker – Senior Technical Write
- Mark O’Black – Technical Writer
- Dan McCorriston – Senior Product Marketing Manager

