Posted
In the first blog of this series, I took a 30,000 foot view of the seven tenets of TI Ops defined in the Dawn of Threat Intelligence Operations paper. In this blog, I’m diving deeper into Tenet 6 – Integrates and automates threat intel into every aspect of security and cyber risk management.
Once you have a single source of high-fidelity threat intelligence, it needs to be put to use. Three kinds of threat intelligence are commonly produced to match the needs of the different stakeholders – operational, tactical, and strategic.
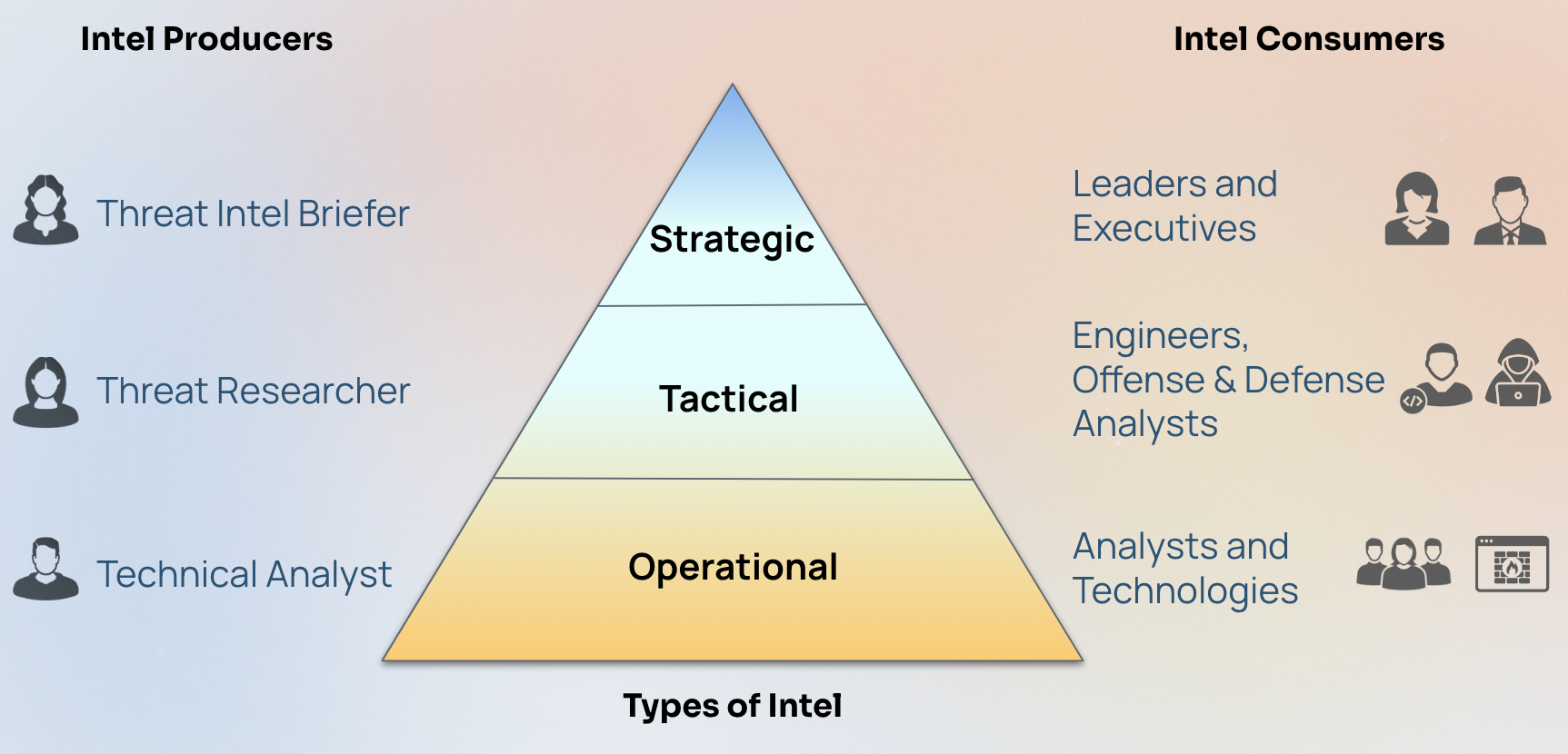
How each of these types of intel are disseminated will vary, but the common goal is to consistently and efficiently distribute high-fidelity intel:
- To the right stakeholder
- At the right time
- And in the right format
The challenge is around doing it “consistently and efficiently.” This is where TI Ops differentiates from traditional CTI functions that focus more on the management and production of intel, and less on the actionability.
To supply threat intel efficiently and reliably, it requires a few key ingredients. When dealing with “machine” intel consumers, e.g., systems and applications, then integrations are a critical ingredient. Automations are also a key ingredient. Putting these two together enables consistent, repeatable, fast, and reliable dissemination of cyber threat intel and other response actions as needed.
We’re in a much better time in cybersecurity than we were even five years ago. APIs are becoming ubiquitous in the technologies used in security, IT, and the myriad of business applications employed across an organization. APIs are a powerful tool that enable CTI to be consumed near real-time across a broad range of solutions. I consider this to be a bit of a golden age for cybersecurity.
The ability to integrate your TI Ops Platform into your threat detection and prevention tools, like EDR, SIEM, XDR, NDR, firewalls, SASE, etc. is crucial. It allows indicators to flow from a unified source of threat intelligence out to those controls in a consistent and efficient manner, enabling those controls to have the latest high-fidelity intel. This approach speeds up threat detection and blocking, and minimizes false positives, and where there are duplicative alerts, e.g., firewalls, NDR, and EDR tools all detect the same threat, it’s based on the same intel with its associated context, rather than dealing with what appears to be loosely related alerts that require a lot of analyst effort to confirm if they are related.
Automating work and actions related to intel dissemination is also crucial. Automation should support the aggregation, analysis, and distribution of intel. Automation should be applied where it will have the greatest impact. For example, enriching Indicators is a universal need and generally consistent across CTI teams, so it lends itself to being baked into a TI Ops Platform. When there are custom processes and procedures, then the ability to implement customized automations is needed. This is the potent combination of built-in and custom automation that flexes and scales to the needs of a TI Ops team. Automation was covered in depth in my blog covering Tenet #5 if you want to dig deeper.
The goal of the CTI team should be to find ways to automate and integrate the intel they are producing to as many stakeholders as possible, whether the SOC, vulnerability management, offensive security, or cyber risk management. This benefits both sides. The CTI team spends more time doing analysis and ensuring the intel being produced is high-quality, reliable, and valuable. Stakeholders benefit from getting relevant, actionable intel.
Take the next step
Read our paper on The Dawn of TI Ops and keep an eye out on your favorite social media channels for the next post where I address Tenet #7 – Creates measures of effectiveness and success for produced and consumed threat intel that are understandable and relevant to the business.
If you’d like to learn more about the ThreatConnect Platform, reach out to chat with one of our experts or request a customized demo.

