No Results Match Your Search
Please try again or contact marketing@threatconnect.com for more information on our resources.
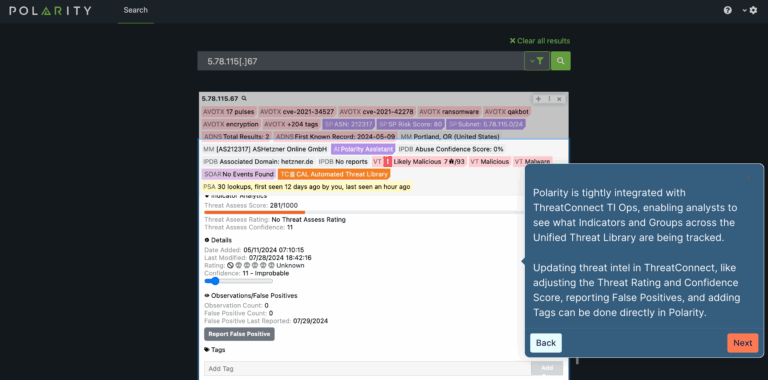
Polarity Tour
Explore an interactive tour of Polarity to see how it integrates into analysts’ workflows across apps and browsers. It automates search, aggregation, and correlation of contextual data in real-time from hundreds of federated data and knowledge sources into a unified display.
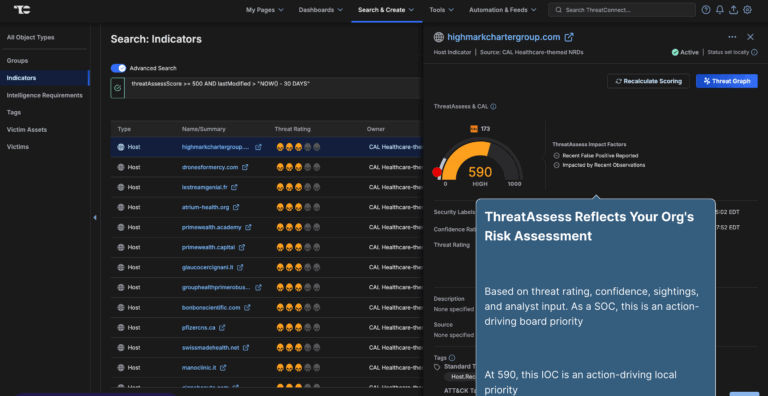
ThreatConnect Platform Tour
Explore the ThreatConnect Platform with this interactive tour. You can navigate through our platform overview plus dive into our capabilities, including Intelligence Requirements, ATT&CK Visualizer, Threat Graph, Playbook Automation, Built-in Reporting, CAL™ Feeds and Automated Threat Library, and Workflows, Tasks, and Cases.

Polarity Intel Edition: Real-Time Threat Intelligence for Your Security Operations Webinar
Watch this insightful on-demand webinar as we dive into the newly launched Polarity Intel Edition (PIE) and explore how it makes it easier for teams to disseminate and use threat intelligence. In this session, Dan Cole, VP of Product Marketing, and Joe Miller, Director of Product, will walk you through the key capabilities of PIE, showcasing how it integrates with ThreatConnect’s TI Ops platform to deliver real-time, contextual intelligence across your security tools.
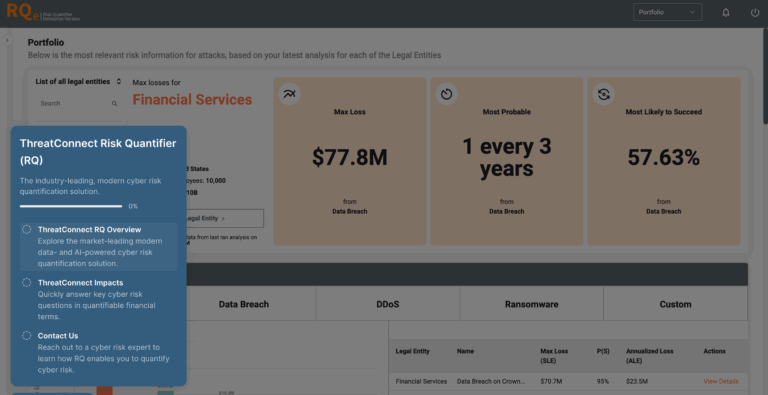
ThreatConnect Risk Quantifier Tour
Explore our cyber risk quantification tour to prioritize security investments and defensive actions by focusing on the greatest risks to your business.

Maximizing Internal Intelligence for Defense Enablement Webinar
Watch this on-demand webinar with Paul Battista, CEO and co-founder of Polarity.io to learn how to harness internal intelligence more effectively, analyze threat intel faster, and increase team efficiency without additional resources.

Polarity Intel Edition by ThreatConnect
Streamline threat intel workflows and provide real-time contextual information for SecOps and CTI teams.

ThreatConnect TI Ops and Polarity Solution Brief
ThreatConnect and Polarity offer an integrated solution for real-time access to aggregated and correlated threat intel and context, enhancing the efficiency and decision-making confidence of security operations and threat intel teams.

ThreatConnect + Polarity A Better Together Story Webinar
Discover how ThreatConnect and Polarity revolutionize threat intel and SOC analysis, offering real-time insights and a unified view for teams. Watch our webinar for in-depth discussions on enhancing your cybersecurity strategy.

Customer Story: Wyndham Improves Threat Detection and Response While Scaling Security Operations
Discover how Wyndham’s security teams enhanced their threat detection and response with ThreatConnect TI Ops and Polarity, streamlining operations and improving efficiency.
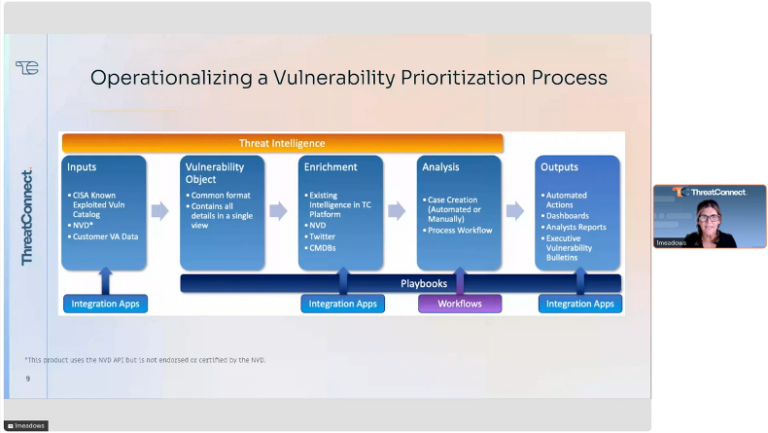
Explore Vulnerability Prioritization with Lara Meadows
Once you find yourself drowning in a sea of vulnerabilities flagged by countless scans, the pressing task at hand becomes which deficiency to fix first. This complex concern transforms into a far less daunting task when you master the concept of vulnerability prioritization with the utilization of threat intelligence operations. Lara Meadows, VP of Sales […]
Cyber Risk: A Fireside Conversation
Watch this fireside chat for a lively and practical discussion on ways to manage, mitigate, and prioritize cyber risk for your business.
Enhance Insights with AI Summaries
Revolutionize cybersecurity with ThreatConnect and Polarity’s AI integration. Gain actionable insights, streamline analysis, and enhance defenses with AI-driven tools.



