Posted
Monitor a website’s content and get alerts if it changes
ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can occur consistently and in real time, without human intervention.
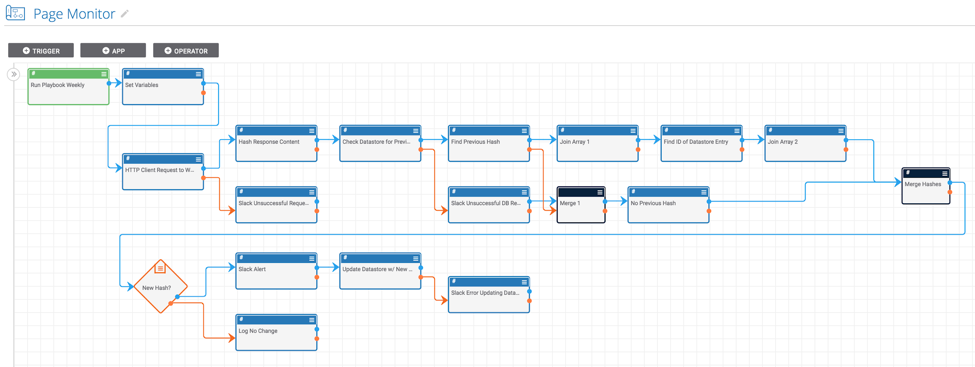
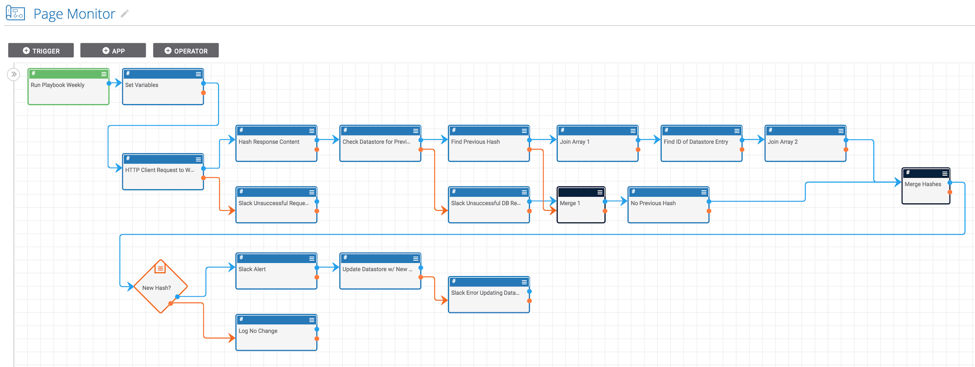
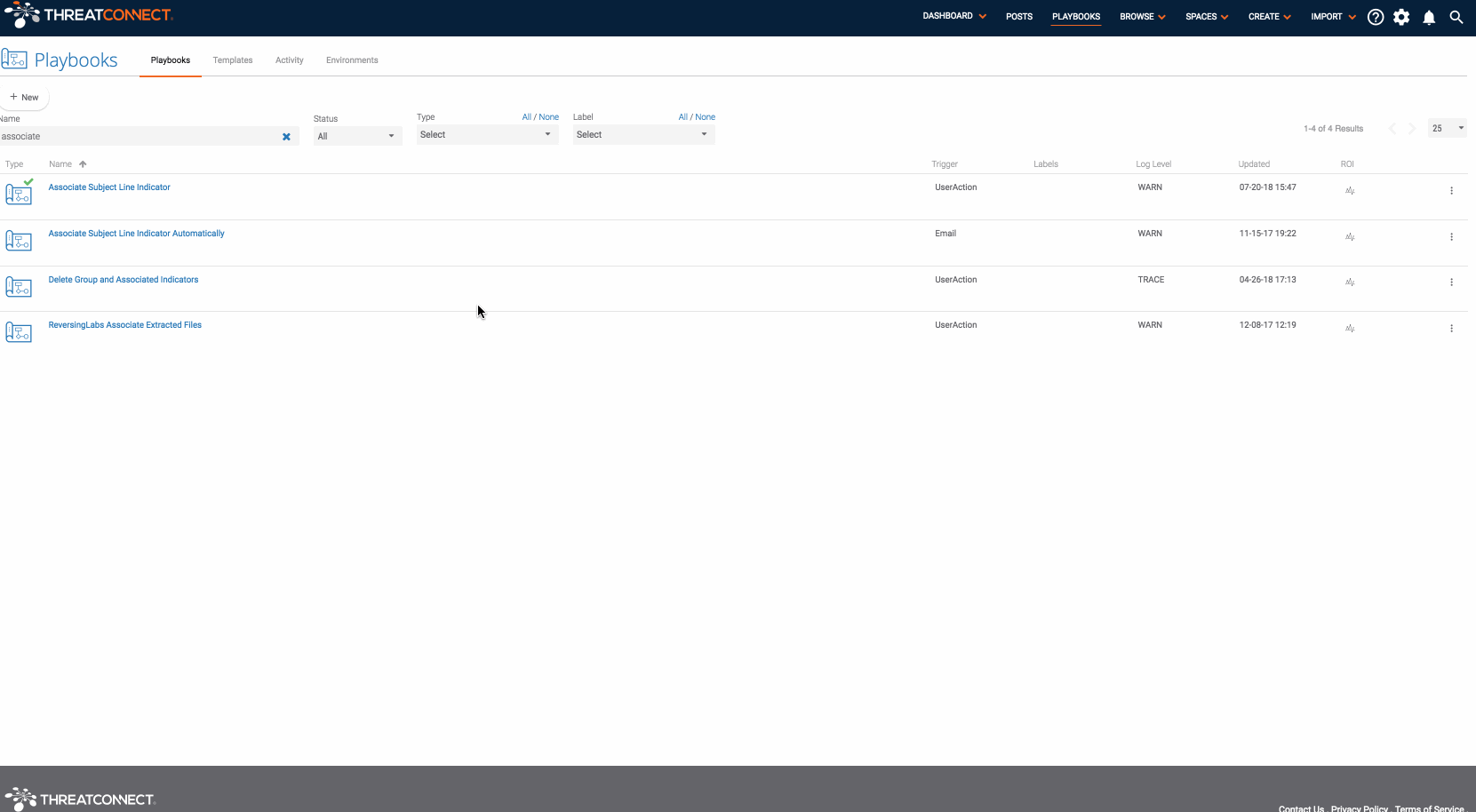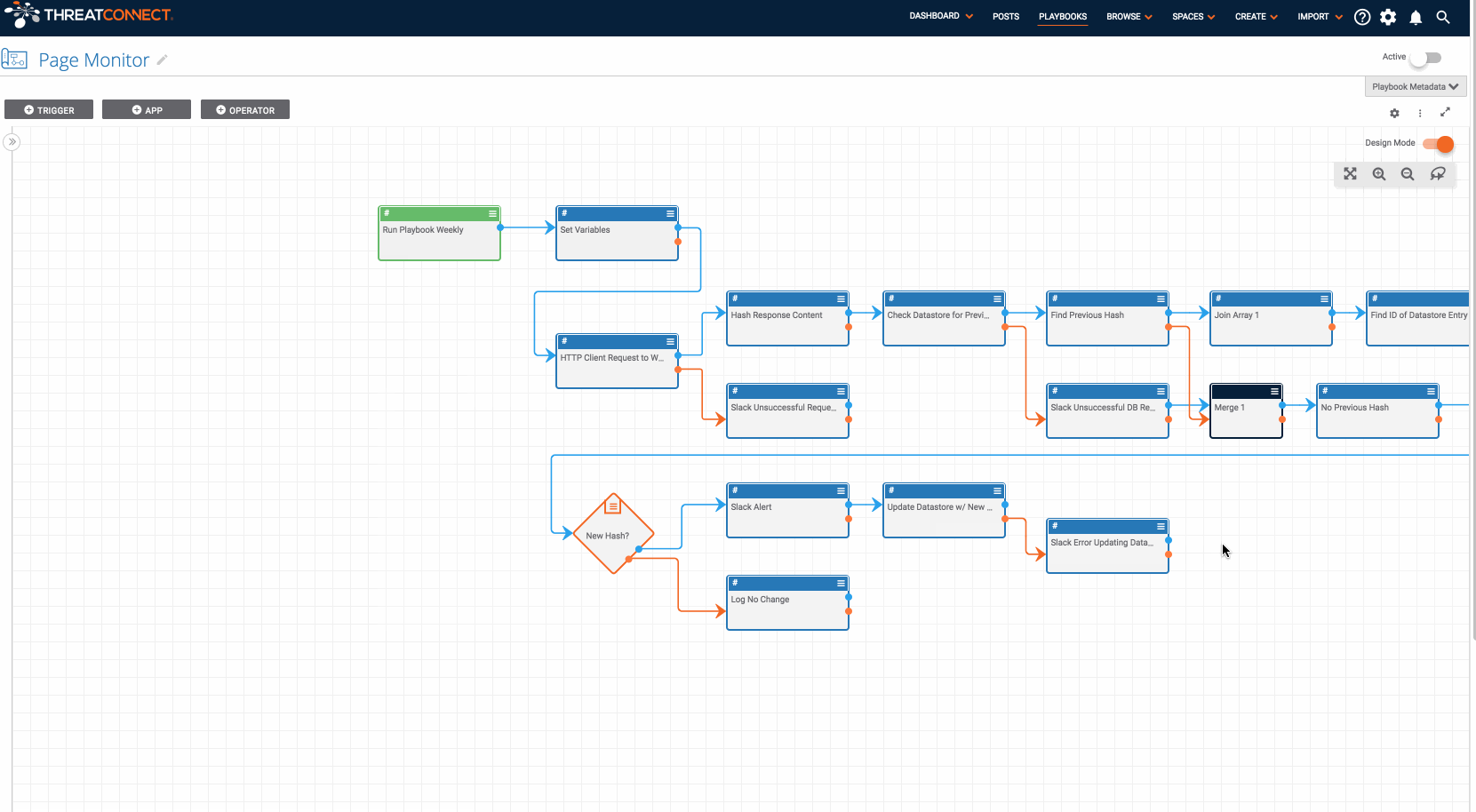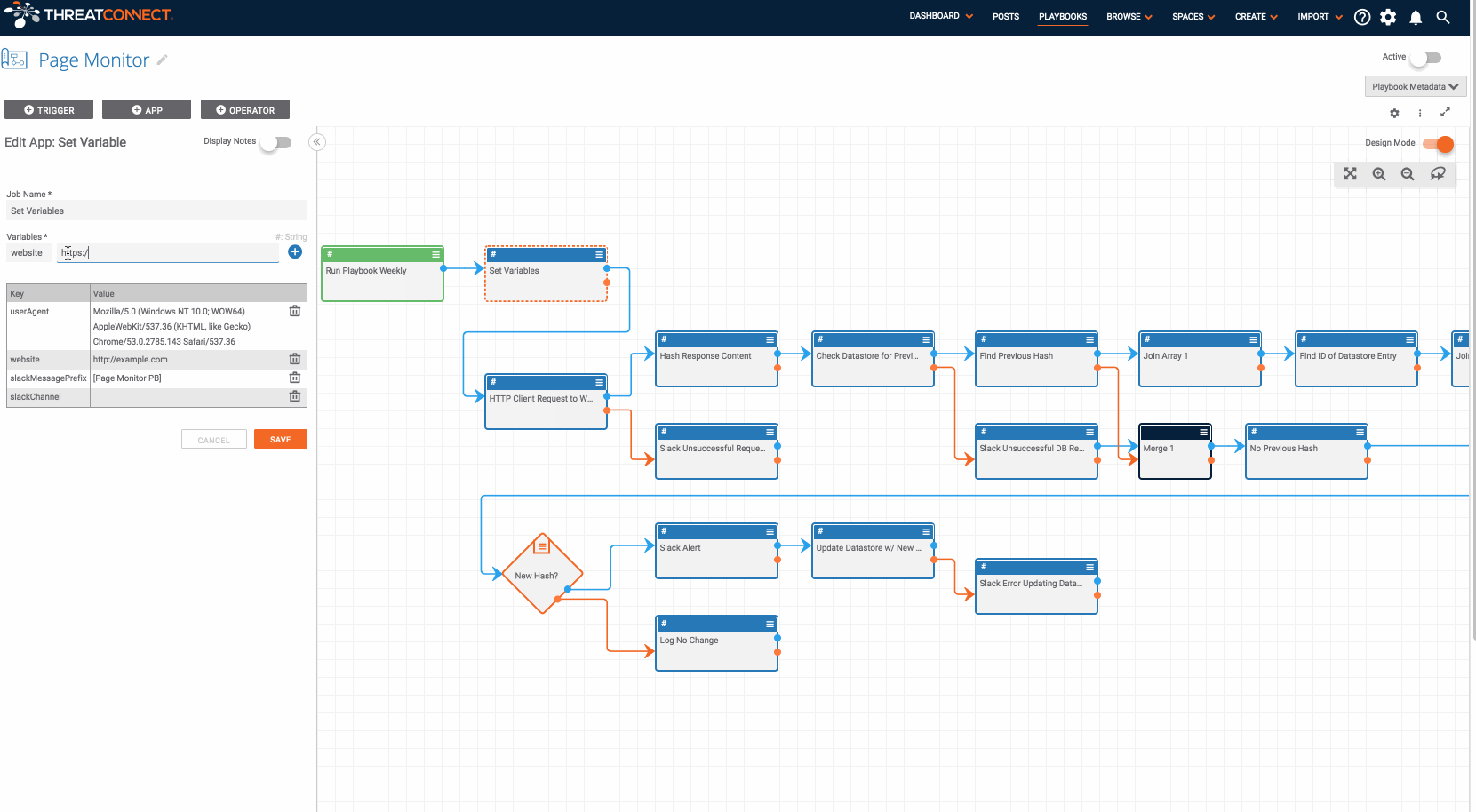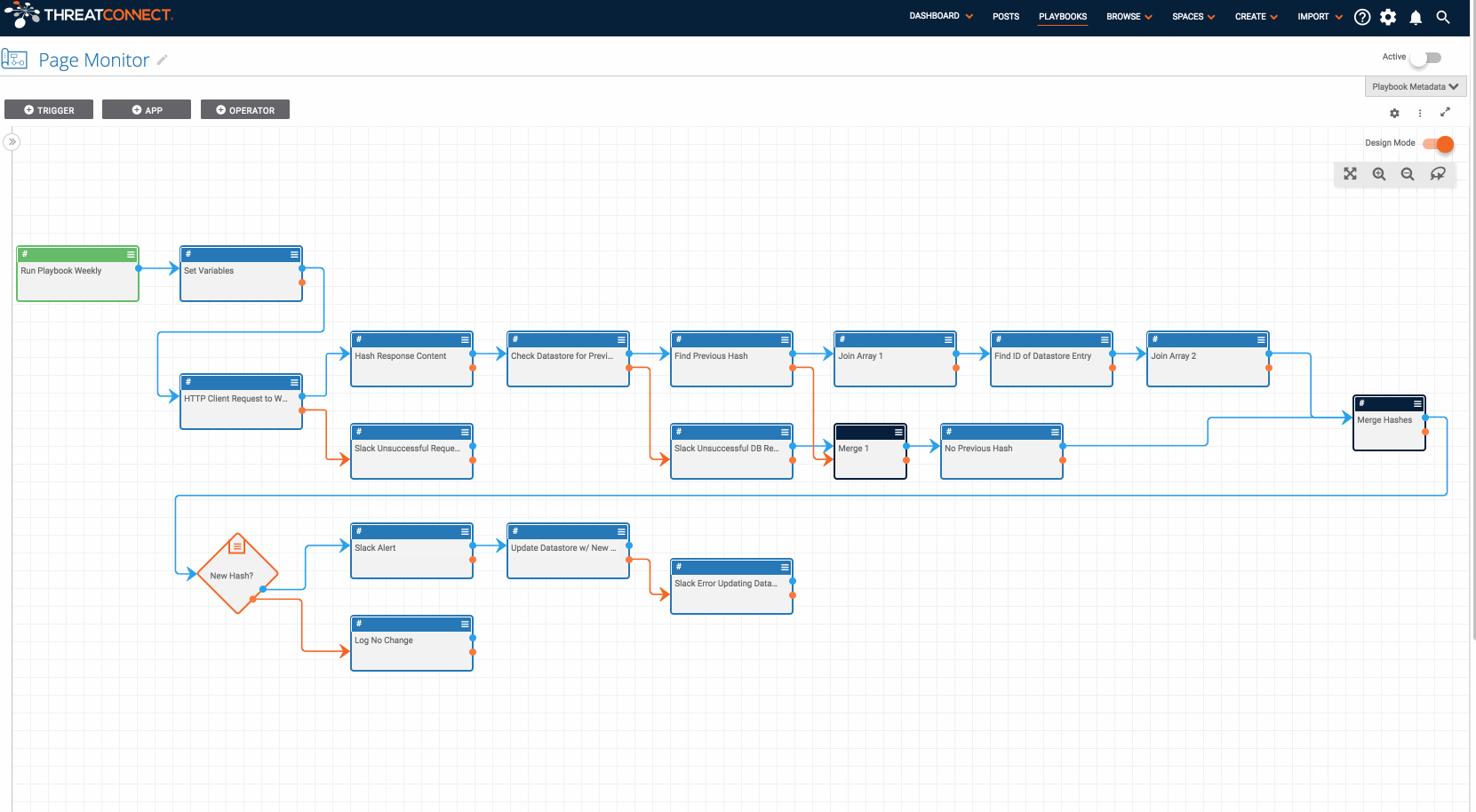
Monitoring websites for changes in content is an important procedure for both offensive and defensive teams. This Playbook allows you to monitor a website’s content and get alerts if it changes. It simplifies the process of monitoring website content and alerting when there are changes. At the outset, we need to be clear that this Playbook is NOT designed to monitor malicious websites. Please do not use it for that purpose!
The mechanics of the Playbook are pretty simple. It contains a timer trigger which means the Playbook can be executed on a desired interval (daily, weekly, or monthly). When the Playbook runs, it requests the website’s content, computes the hash of the website’s content, and compares the hash against the previous hash in the datastore. If the hash of the website’s content is different on one of the Playbook executions it will send a slack message to the given channel (although you can modify this to get notified however you prefer). As the Playbook is currently designed, if the website’s contents have not changed, no notification will be sent.
Getting Started
- Download the appropriate version for your instance of ThreatConnect. If you are running ThreatConnect version 5.6 or newer, you can use the Page Monitor.pbx. If you are using an older version on ThreatConnect, you should use Page Monitor < 5.6.pbx.
- Go to the “Playbooks” tab in ThreatConnect and click “New” > “Import” (on ThreatConnect versions before 5.7, you can just click the “Import” button). Then import the page monitor Playbook file you downloaded in step 1. Now, we need to setup the Playbook.
- To setup the Playbook, find all of the apps with a red error messages and fix the problem. For some of the apps, you may only need to open the app and re-save it.
- Once you are all setup, you can configure the timer trigger so that the Playbook runs when you would like it to run. From there, you’re good to go! Again, please do NOT use this Playbook to monitor malicious infrastructure.
As always, if this Playbook does not fit your use-case exactly, feel free to redesign it and create the process you would like to see, or raise an issue describing your idea and one of the security developers from the community may be able to make the update for you. If you have any questions or run into any problems with this Playbook, please raise an issue in Github.