Posted
ThreatConnect has partnered with Check Point and built a Playbook App for our joint customers to leverage. With the addition of this new Playbook App, immediate actions can be taken to investigate, stop, and remediate potential threats at the endpoint based on external threat intelligence.
Check Point’s Unified Security Management gives you unified management control across all networks and cloud environments. This allows you to increase operational efficiency and lower the complexity of managing your security.
This new Playbook App automates adding and removing known malicious IOCs in Check Point Security Management. These actions may take place as part of an Incident Response workflow, Phishing Email Triage workflow, or enriching/processing intelligence from OSINT or Premium Intelligence feeds.
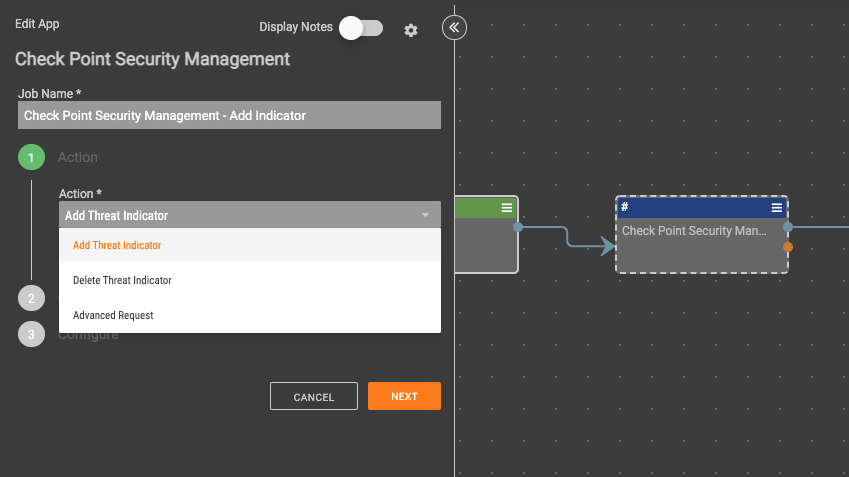
Check Point Security Management Playbook App
The following actions are available:
- Add Threat Indicator
- Delete Threat Indicator
- Advanced Request
By automating this process, you ensure that high fidelity intelligence is being sent between the two solutions and that you and your team have all the information needed to make informed decisions.
Together, ThreatConnect and Check Point provide a complete solution for security teams that enables them to detect threats and perform remediation quickly and precisely by utilizing tools that communicate with each other.
If you’re a ThreatConnect customer, please reach out to your dedicated Customer Success Team for more information on utilizing the Check Point Playbook Apps. If you’re not yet a customer and are interested in ThreatConnect, contact sales@threatconnect.com.