Posted
In the first blog of this series, I took a 30,000 foot view of the seven tenets of TI Ops defined in the Dawn of Threat Intelligence Operations paper. In this blog, I’m diving deeper into Tenet 5 – Automate TI Ops Work
Automate the work of the TI Ops team
Automation has permeated our daily lives. We can tell assistants to take automated actions via voice commands. You likely interact with robotic process automation on a daily basis through websites and phone systems. Automation makes specific types of work easier, faster, and cheaper. The use of automation in cybersecurity is growing too, whether you notice it or not. What do I mean by this? First, let’s get a common understanding of automation. Merriam-Webster has three definitions for automation:
- The technique of making an apparatus, a process, or a system operate automatically
- The state of being operated automatically
- Automatically controlled operation of an apparatus, process, or system by mechanical or electronic devices that take the place of human labor”
This is pretty straightforward. Manual work is done automatically via some means, whether through a device or, in our situation, code.
The next question is, “How is automation done?” This is important because automation permeates our tools, so we might not even notice some work or activity being automated. In cybersecurity, we tend to think of automation as something like security orchestration, automation, and response, aka SOAR, where processes are defined via a user interface, creating code in the background executed according to a specific trigger. However, automation is increasingly becoming embedded into tools. Hence, we have increasingly powerful abilities to leverage automation to help us do our work better, faster, easier, and more effectively.
Cyber threat intelligence is a function where automation has not yet been adequately adopted and leveraged, creating an untapped opportunity for CTI teams. A survey of ThreatConnect customers in 2022 asked users, “What’s your biggest waste of time during the day?” Data gathering/manipulation was number one, followed by manual tasks in second place. This indicates that the work to collect and process intel is a time sink, as well as the variety of other manual tasks that CTI analysts have to do (e.g., enriching intel, creating reports, etc.). When asked about the most time-consuming phases of the threat intel lifecycle, users who responded with “Collection” and “Processing” indicated that manual tasks were one of the key reasons why they spent so much time on that phase. A modern approach is needed.
A key aspect when embracing Threat Intelligence Operations is to also embrace automation. And when I say embrace, there are multiple dimensions to using automation.
- Getting past the perception that automation will remove the need for skilled analysts. Quite the opposite. It allows skilled analysts to do what they do best: analysis, not data collection, processing, manipulation, etc. It allows them to do more analysis. Allowing the machine to perform routine, low-value tasks is advantageous. And when the machine can perform those tasks in parallel rather than sequentially and consistently, it allows analysts to go faster with less effort. A basic but powerful form of automation that is built into the ThreatConnect Platform, is the aggregating and processing of intel, like ingesting data from a variety of sources, deduplicating indicators, or extracting indicators and ATT&CK tactics and techniques from unstructured intel sources, like PDF reports or web pages, using natural language processing, a common type of AI. This isn’t a “process” that needs to be automated through a playbook, it’s automation built directly into the Platform. Enrichment is another example. Indicators are indicators. Enriching them with context from 3rd party sources lends itself to built-in automation.
- Using the appropriate type of automation for the task or process at the right time. Per the above point, there are routine tasks consistent across organizations that lend themselves to being automated “behind the scenes.”
On the other hand, workflows and processes are going to be more unique to each organization. The ability to define the specific tasks in a workflow, determining whether it should be automated or done manually, and then having an automation (aka playbook) that incorporates the specific steps and integrated tools is what is generally considered orchestration and automation in cybersecurity.
The ThreatConnect TI Ops Platform leverages this combination of built-in automation, as well as a drag-and-drop, low-code automation capability to reduce the burden on analysts. Common activities are automated directly in the Platform, but for enterprise-specific workflows and processes, the Platform easily supports those via our Workflows and Playbooks. This approach to automation allows analysts to focus on high-value and interesting work, like intel analysis. This also reduces the stress on analysts and makes them happier, which is a win.
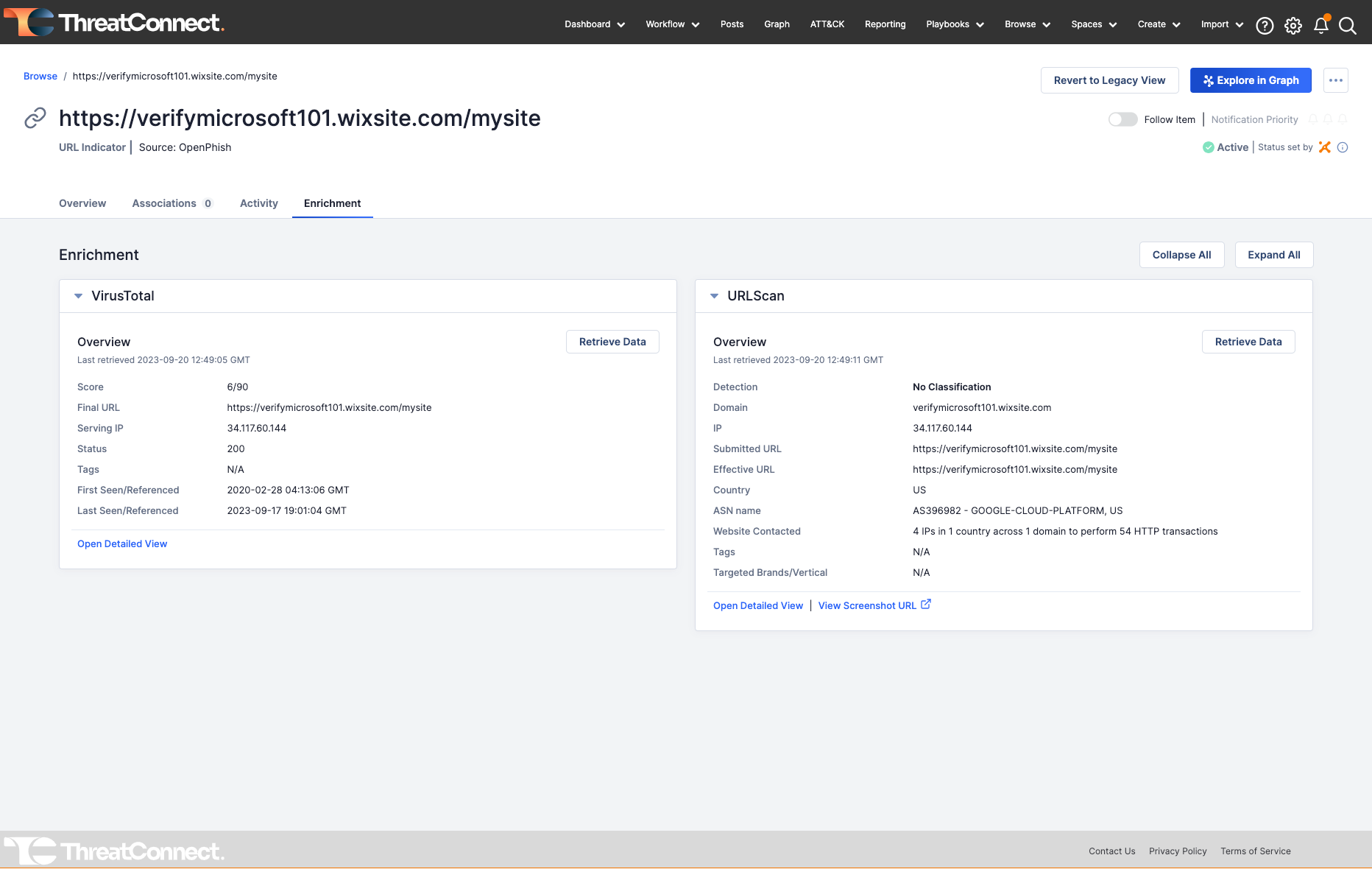
Automated Indicator Enrichment in the ThreatConnect Platform
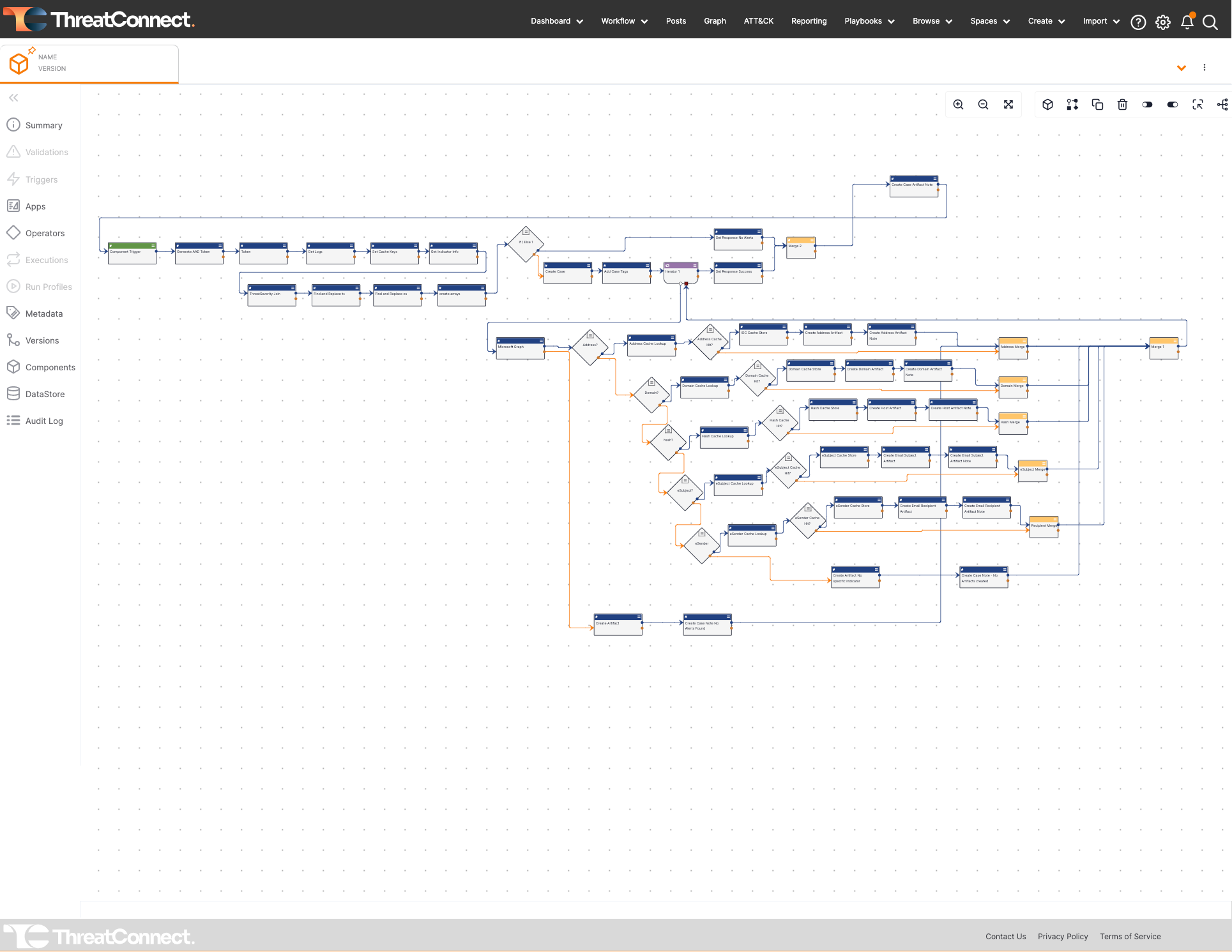
Example of a Playbook Built Using Low-Code Automation in the ThreatConnect Platform
Take the next step
While waiting for the next part of this series, read the Dawn of TI Ops paper, and keep an eye out on your favorite social media channels for the next post where I address Tenet 6 – Integrates and automates threat intel into every aspect of security and cyber risk management.
If you’d like to learn more about the ThreatConnect Platform, reach out to speak to one of our experts. If you want a custom demo of the Platform, just ask, we can do that, too!