Posted
A dedicated threat intelligence team and function has been treated as a luxury for far too long, and if there is one, demonstrating its value is a persistent struggle.
However, security leaders know that the modernization and digitization of the enterprise, an expanding attack surface, and evolving adversaries are stressing their teams and capacity. In order for organizations to be more resilient to threats, they need to be more proactive in their response to the most relevant adversaries while working to minimize exposures that can be used in attacks.
Getting ahead of adversaries by operationalizing threat intelligence is the way to do this.
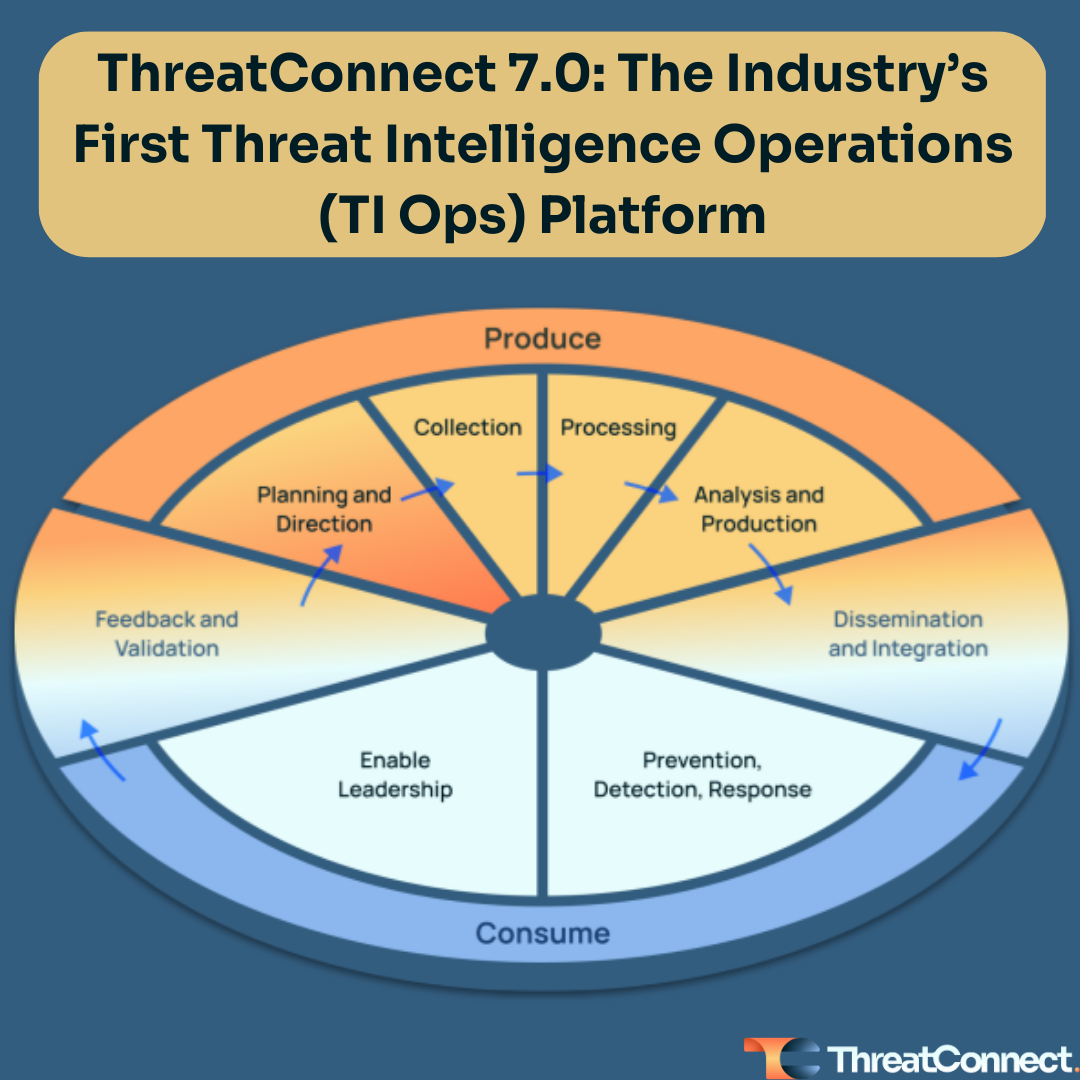
We believe that a new approach to threat intelligence across people, processes, and technology is required.
- One that elevates the threat intel function, which we call Threat Intelligence Operations (aka TI Ops), to a core team in security operations.
- It requires an Evolved Threat Intel Lifecycle that considers not just the production but the consumption of threat intel – which meets agreed needs and requirements, is delivered at the right time and place, is actionable, and has demonstrable value to the consumer.
- A modern Threat Intelligence Operations Platform that solves the challenges faced by teams relying on spreadsheets and legacy threat intel platforms.
ThreatConnect enables organizations to maximize the impact of TI Ops by utilizing a combination of human analysis, AI and machine learning, and automation. In our latest release, ThreatConnect 7.0 delivers new capabilities that radically increase the effectiveness and efficiency of threat intel operations analysts and security operations teams throughout the Evolved Threat Intel Lifecycle.
The ThreatConnect 7.0 features and capabilities include:
- Native Reporting
- Built-in Enrichment
- Improved User Experience
Native Reporting
Dissemination and Enabling Leadership are key stages in the Evolved Threat Intel Lifecycle, providing stakeholders the necessary information and insights to make strategic, tactical, and operational decisions. This is most easily achieved with reports but getting the right information in front of the right people at the right time is difficult when analysts are stuck exporting data using copy and paste across multiple spreadsheets and documents.
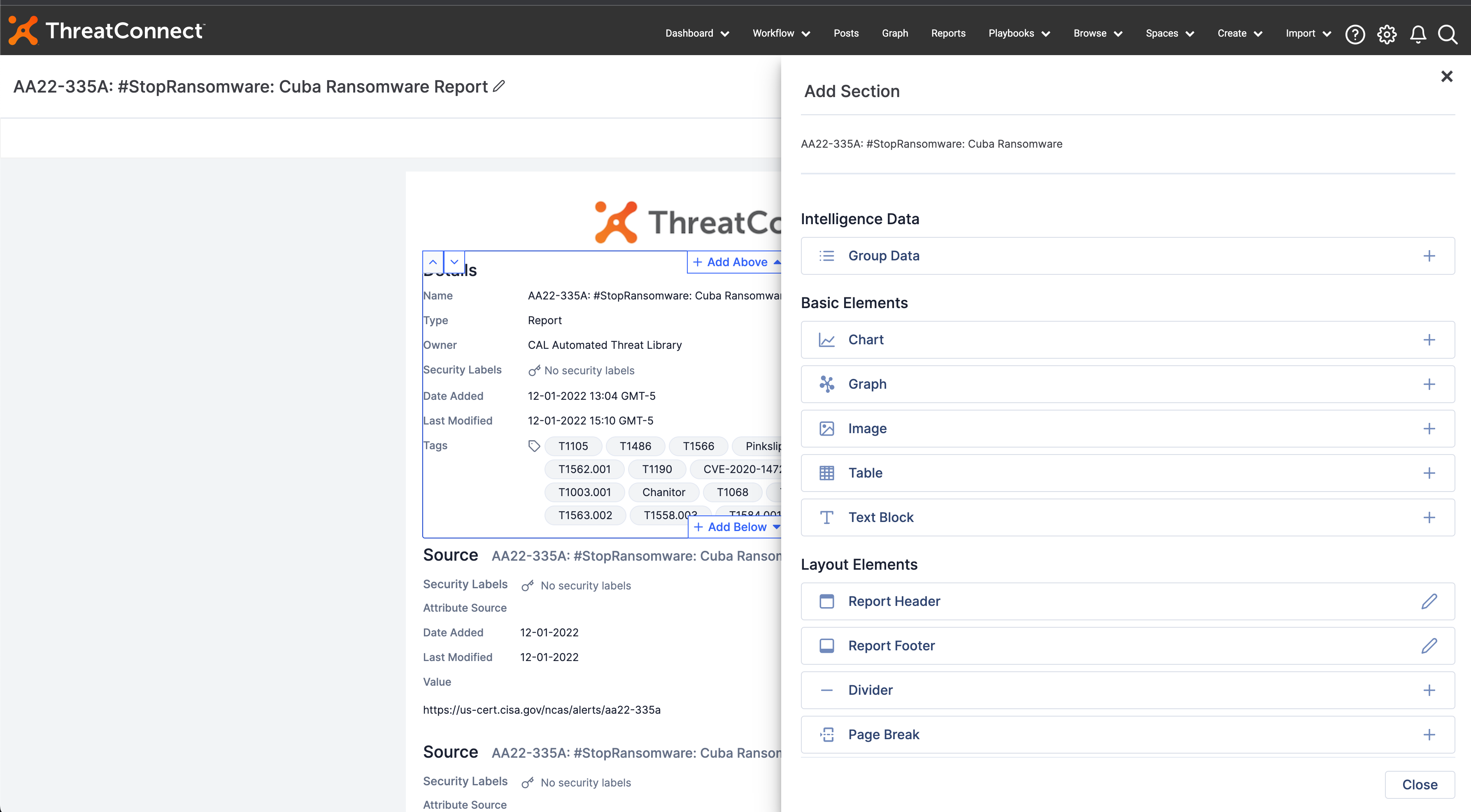
Analysts need an easy way to build custom reports within the ThreatConnect Platform to demonstrate the value of TI Ops to the organization. ThreatConnect 7.0 introduces the first version of in-Platform, native Reporting. ThreatConnect’s Reporting feature was built for ease of use based on real-life reports analysts use every day to ensure you can continue to provide the same type of content and formatting you’re used to, now in the same tool that produces the data and insights.
Building, customizing, and sharing reports within the Platform is nearly effortless with drag-and-drop functionality. Users have the flexibility to choose which sections to include and to format each section within the report as they see fit. Each report has customizable headers and footers so users can include their organization’s brand and have the ability to contextualize each report down to the individual data point. Add out-of-the-box charts and tables or build your own using our proprietary ThreatConnect Query Language (TQL) for valuable context in each report, as well as images, charts, and data from Threat Graph, our interactive visualization tool.
Reporting in the Platform not only saves analysts time but also enables them to easily share the most relevant threats and intel to better communicate the value of TI Ops and enable leadership from the CISO down to have the necessary information and insights to make strategic, tactical, and operational decisions.
In future releases, we’re introducing more features like Case Reports, API Support, Reporting Templates, Automated Scheduling, Playbook Integration, and more!
Built-in Enrichment
Security teams are buried in indicators, but not all indicators are relevant. The more an analyst knows about an indicator, the better they can assess its severity and relevance to their organization. Adding context to individual indicators is cumbersome, relying on manual processes or building and maintaining complex Playbooks for simple enrichment.
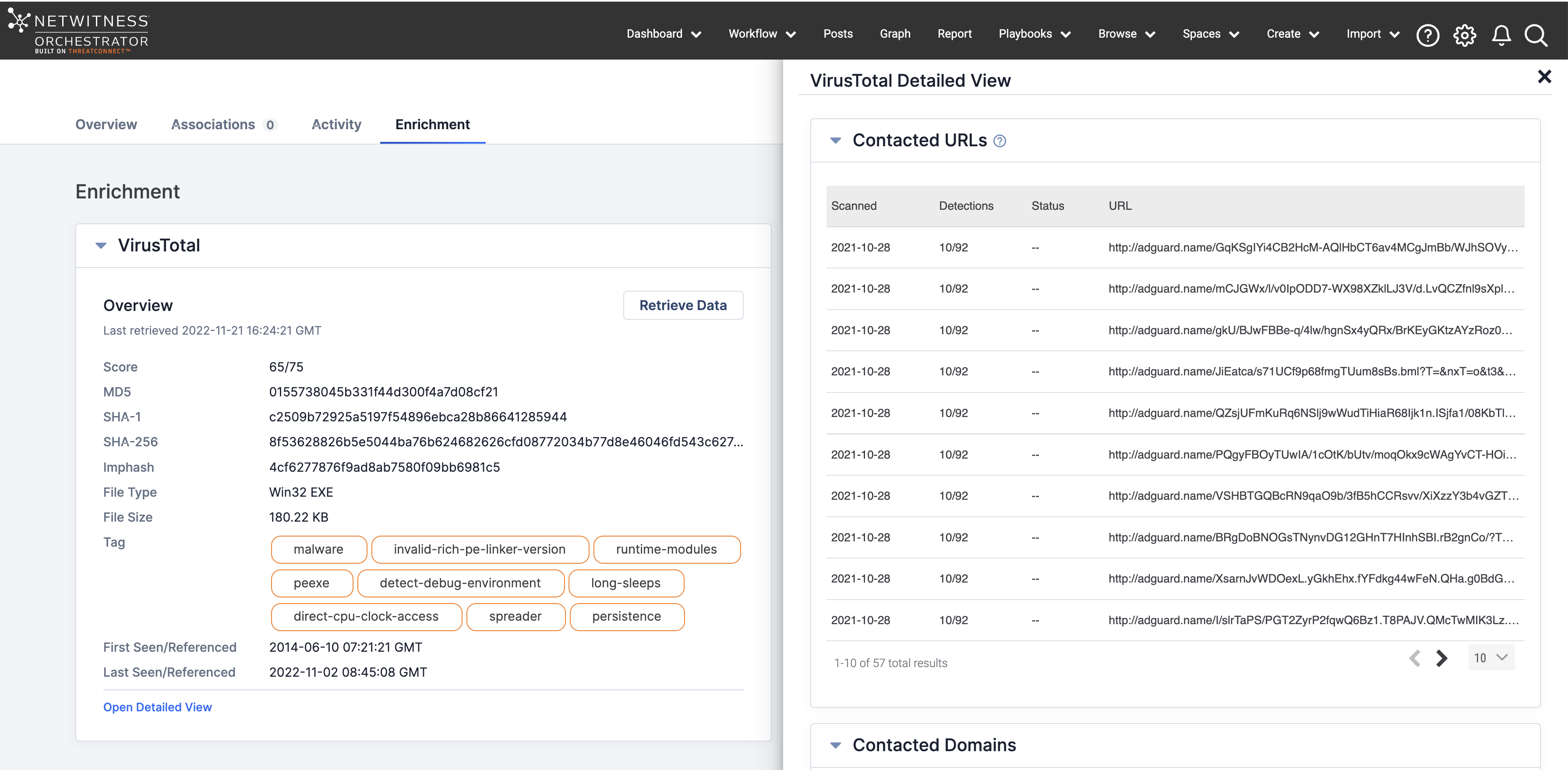
To help analysts perform more efficient and effective investigations, ThreatConnect added built-in, out-of-the-box Enrichment of threat intel, adding more context without impacting analyst time and effort. In this first iteration of Enrichment, users can easily configure VirusTotal in ThreatConnect to understand the maliciousness of an indicator and links and dependencies between indicators, with more partner integrations coming in the future.
Once VirusTotal is configured, Enrichment is as simple as one click. With a single click, users get basic information about an Indicator beyond just its score, including Tag, Domain, Country, First and Last seen, etc. A second click within the Platform provides more details about an indicator’s links and dependencies for additional context. VirusTotal scores are queryable via ThreatConnect Query Langue (TQL), adding relevant enrichment data to your threat library for future analysis during an investigation.
Additionally, users can leverage Threat Graph to conduct investigations and visualize and contextualize enrichment data to understand an indicator’s relationships and associations with other indicators, like if an IP has been part of a threat campaign.
With Enrichment, you’ll save time and resources processing and analyzing hundreds of thousands of indicators trying to determine which pose a threat and which are benign while expanding your threat library with relevant enrichment data. In later releases, we’re adding more enrichment sources like URLscan, Shodan, and more!
Improved User Experience
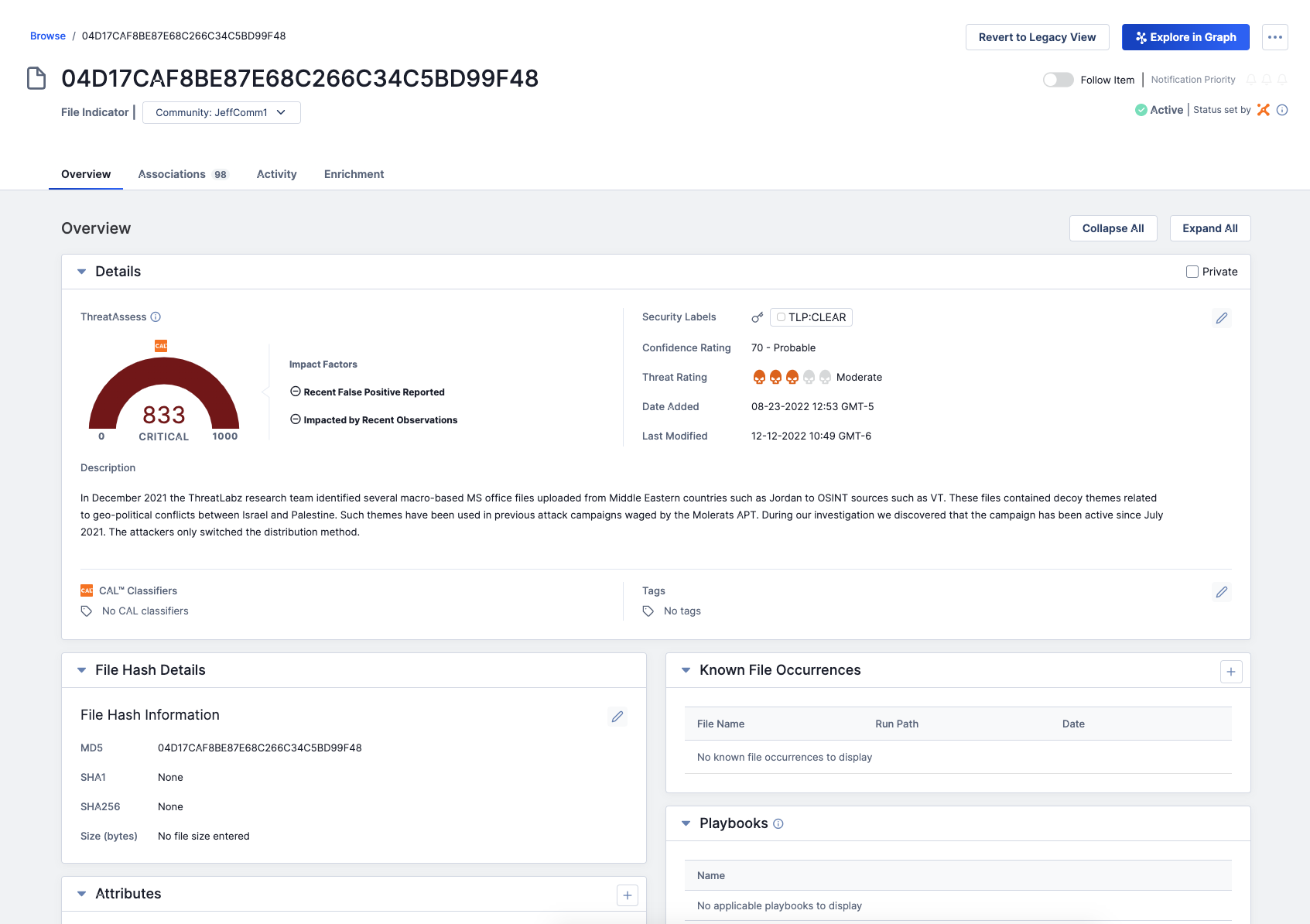
Security teams need to move fast and make important decisions to confidently take action on impending threats. In the ThreatConnect 6.7 release, we introduced Cross-Owner Associations (XOA), enabling users to link information across sources in their ThreatConnect instance for a fuller view of their organization’s threat landscape. In ThreatConnect 7.0, we revamped the Details screen, creating a more intuitive user experience.
The updated Details page is easier to use, elevating relevant information about Indicators and Groups in one place so analysts can quickly understand the threats to your organization and make fast decisions without having to dig around the Platform. Noteworthy updates to the Details page include:
- Insight from multiple sources – Leverage insights from a variety of sources, including local and global insights from CAL™, our ML-powered analytics engine.
- Pinned Attributes – Elevate the most important information to the top of the Details page so you can spend less time scrolling and make decisions even faster.
- Enrichment – Out-of-the-box enrichment of indicators adds contexts to understand the links and dependencies between indicators for more effective investigations without having to build out complex Playbooks.
This revamped Details page is the foundation of multiple enhancements planned for future releases, including Automated Associations via TQL, ATT&CK Navigator, and other features to form a single pane of glass in the ThreatConnect Platform.
Download ThreatConnect’s Dawn of TI Ops White Paper and the Evolved Threat Intel Lifecycle infographic to learn more about getting ahead of adversaries by operationalizing threat intelligence. You also don’t want to miss our webinar The Need for an Evolved Threat Intel Lifecycle, on February 17th, 2023.
For more information on these new capabilities and how ThreatConnect can help your organization operationalize threat intelligence, please reach out to sales@threatconnect.com or request a demo.