Posted
At ThreatConnect, we enable teams to achieve maximum impact on their security program by improving insights, efficiency, and collaboration. We are continuously building and iterating on our Platform based on feedback from our customers to simplify processes, speed up security tasks, and deliver a seamless user experience.
The ThreatConnect 6.7 release delivers a more streamlined and intuitive experience for users to achieve their greater security goals. This release innovates on existing capabilities like Intelligence Anywhere, Threat Graph, and Case Management. The updates include:
- More comprehensive threat data with cross-owner associations
- Better insights with Intelligence Everywhere v3
- Faster investigations by viewing cases in Threat Graph
Cross-Owner Associations
When you’re compiling knowledge on a topic, like an Indicator, the last thing you want to do is search in multiple places to link information together. Not only is it time-consuming, but searching through different sources can lead to duplicative and/or missing information.
Security teams want to view everything they know about a topic in one place so Cyber Threat Intelligence (CTI) analysts can build out a comprehensive threat library, and Security Operations Center (SOC) analysts can view the context they need for faster investigation and response.
ThreatConnect 6.7 solves this problem with our first iteration of cross-owner associations. This feature lets you filter by Owners in your ThreatConnect instance to link information from across your sources, communities, and organizations. This provides an easy way to build out your threat library in a more comprehensive way and view everything your organization knows about an Indicator or Group in one place.
Additionally, you can leverage the new “CAL Aliases” button in the Platform to query across your ThreatConnect instance for the Group you are viewing and identify known aliases of the Group so you can find and associate related information faster.
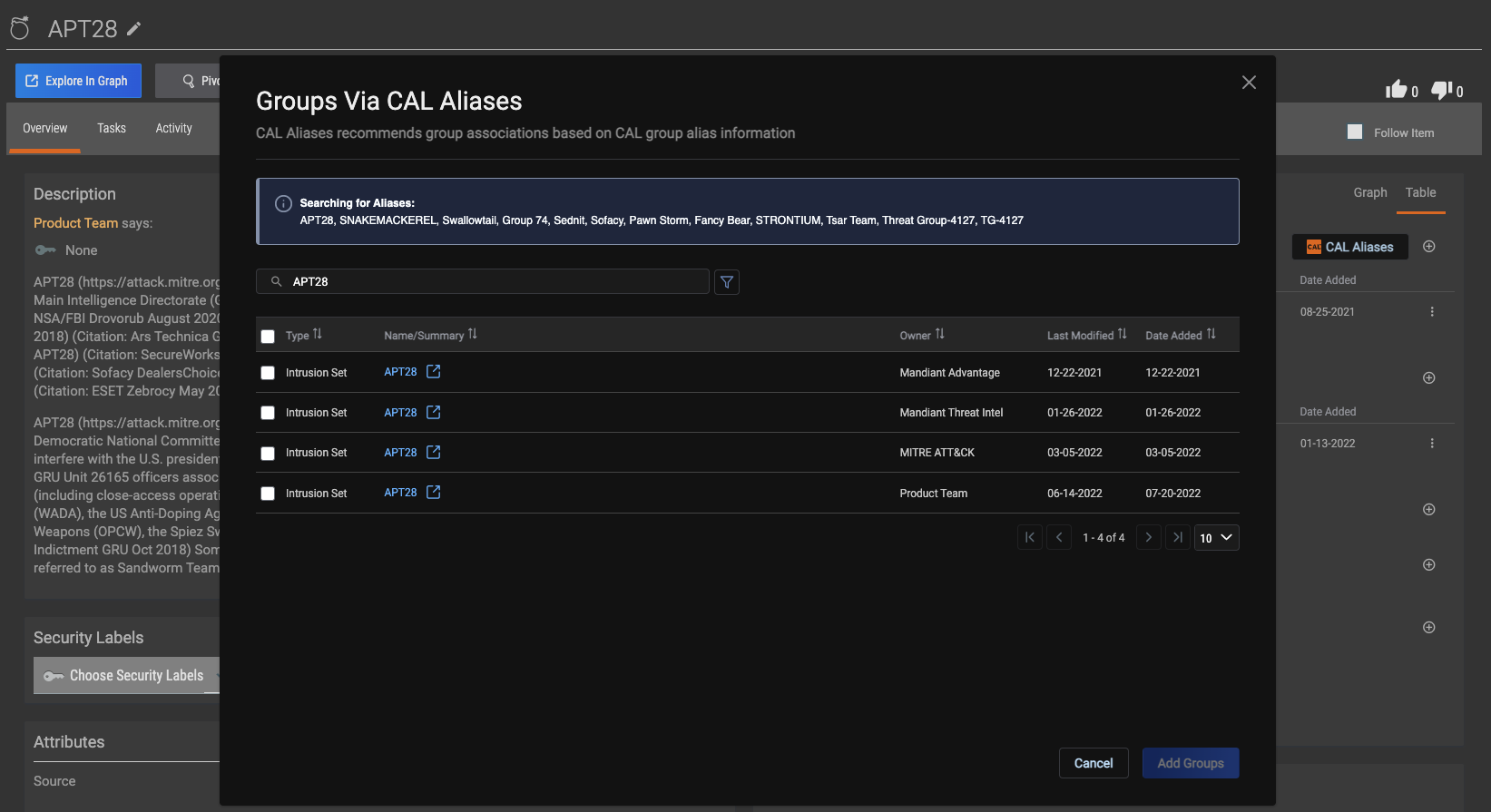
Use the CAL Aliases button to quickly identify other Groups that are likely to be related to the one being viewed
Intelligence Anywhere v3
For CTI analysts, researching new Indicators across multiple sources is part of the job. However, ensuring the findings are collected and saved to an accessible repository is often a manual task, and leads to spreading information across different spreadsheets. With Intelligence Anywhere, users simply click a button to instantly scan and identify relevant pieces of information from any web-based resource to add to your Threat Library.
Intelligence Anywhere v3 builds on these capabilities with the addition of CAL natural language processing (NLP) that enables you to scan a web page and query the CAL NLP engine for matches on MITRE® ATT&CK® techniques. NLP looks for language that is indicative of MITRE ATT&CK techniques rather than looking for an exact match. When a technique is identified, you can hover over the text for additional insights on that technique and add relevant indicator information to your threat library for future investigations.
Users will also benefit from an updated Intelligence Anywhere interface for a more intuitive experience. Updates include ranking Indicators based on ThreatAssess score, a settings menu alphabetized by source, and the ability to filter between Groups and Indicators. With Intelligence Anywhere v3, you’ll maximize insights on MITRE ATT&CK techniques without having to track your findings in a spreadsheet.
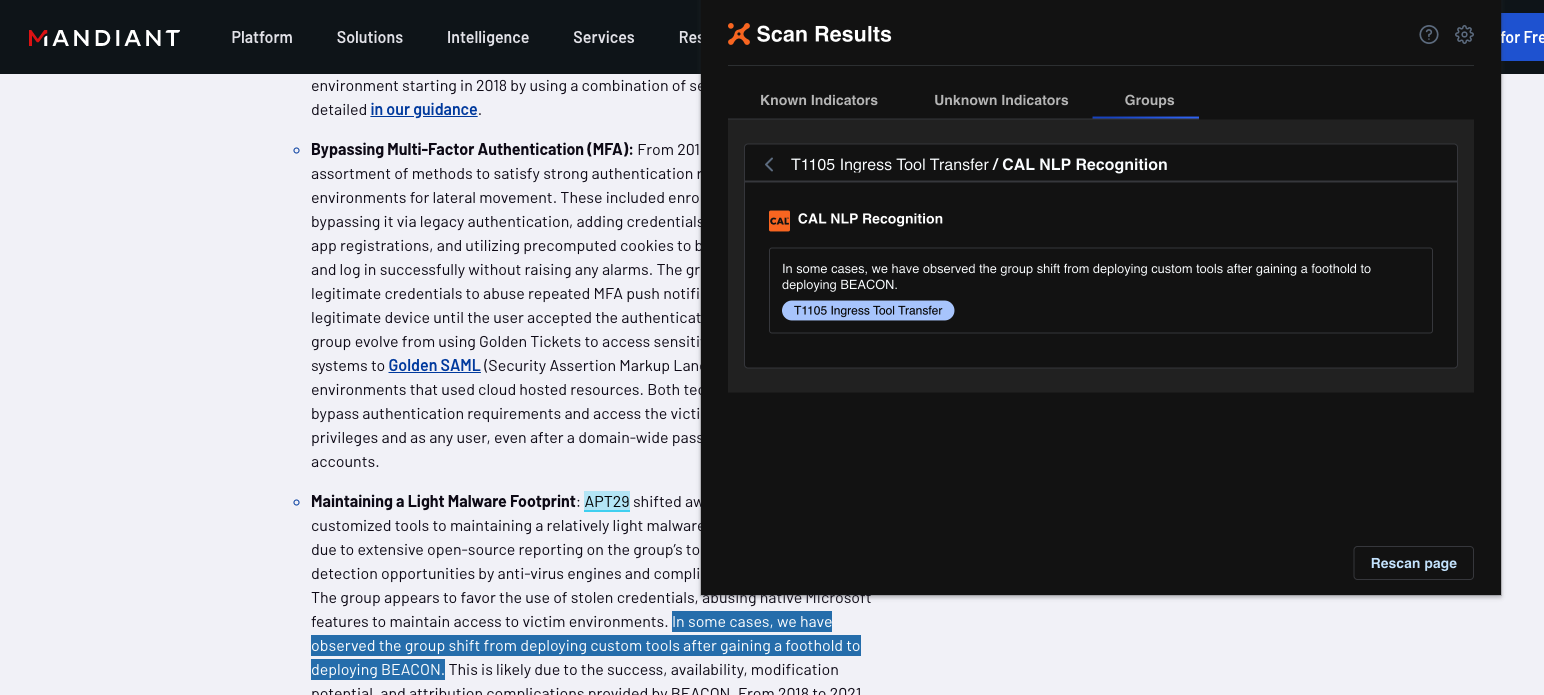
Leverage CAL’s NLP to identify ATT&CK techniques not explicitly mentioned in the text of a web page
Visualize Cases in Threat Graph
The threat landscape is constantly evolving, making it difficult for analysts to keep up and respond to threats in a timely manner. Zooming out on the landscape to have a holistic view of the threats and how they relate to each other is ideal to decrease the time spent on investigations.
With ThreatConnect 6.7, SOC and IR teams can visualize cases in Threat Graph. Threat Graph is a tool for analysts to easily visualize the relationships between Groups, Indicators, and Cases in an interactive UI.
By using Threat Graph, analysts can leverage high-fidelity threat intelligence from the CTI team to investigate Cases faster and identify similar cases that share the same Indicators and Groups. Drawing these associations allows you to use the same action you’d take on the Case you’re investigating with other similar cases, reducing mean-time-to-respond.
Threat Graph lets you save Graphs for future use, delete items from a Graph, and combine Group nodes by alias to view similarities, such as specific Indicators related to multiple groups or threat actors leveraging similar TTPs. With Threat Graph, you’ll maximize efficiency with a view of your organization’s entire threat landscape.
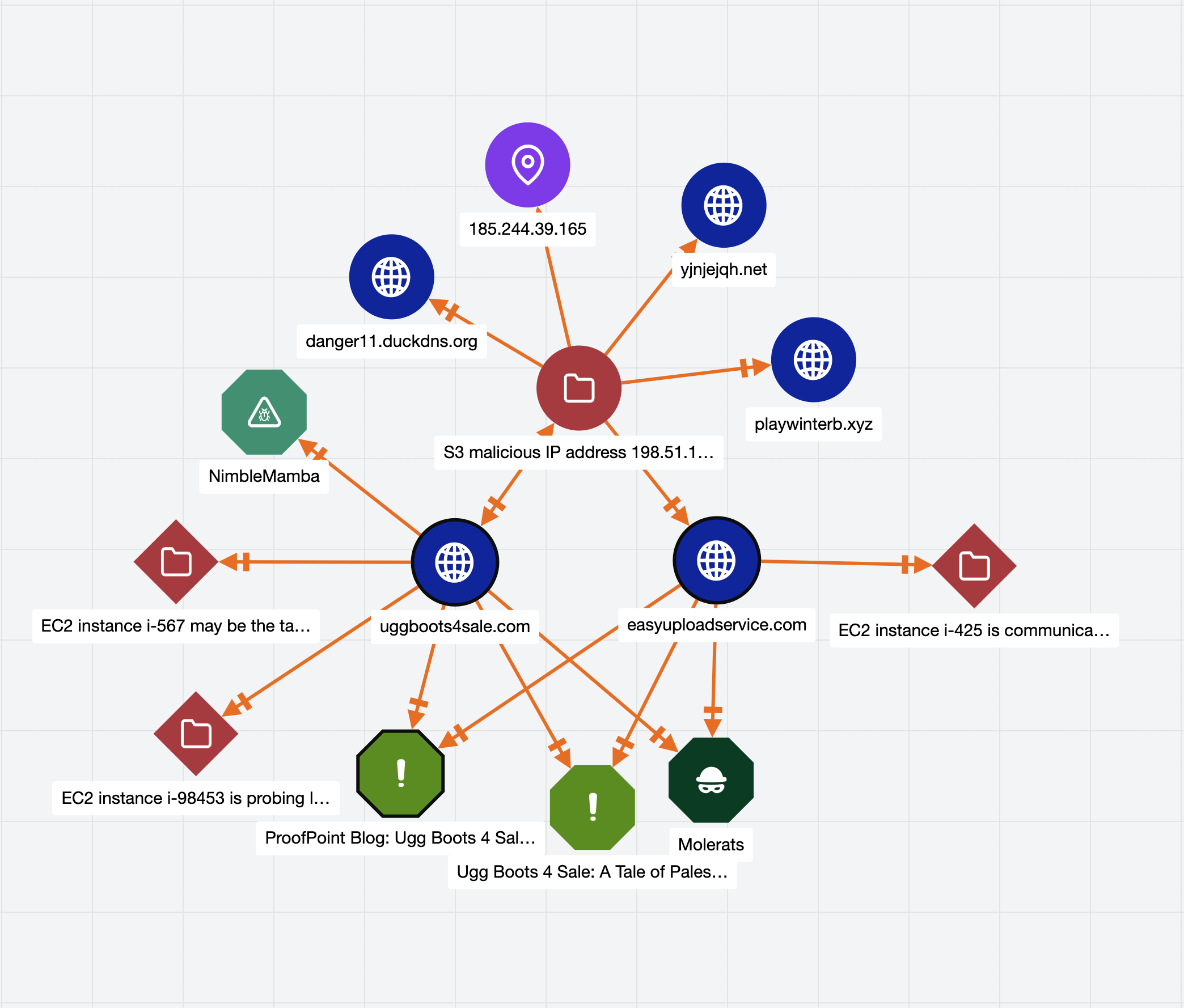
Holistic view of Cases and shared Indicators and Groups
More Features with 6.7
We’ve included even more great improvements and bug fixes to the Platform as part of the 6.7 release to boost the user experience.
Intel-Powered Case Associations – Users can bring in relevant potential associations from external sources to add more context, like matching Indicators and their related Groups to the Cases in Workflow.
Add Indicators to the Exclusion List – System Administrators and Organization Administrators will have the option to add an Indicator to their Organization’s Exclusion List directly from the Indicator’s Details screen.
User Management API v1 – An update to our existing v3 endpoint allows API Users with Organization Administrators role to retrieve all users of an Organization, retrieve a single user by user ID, create a user, update a user, and delete a user.
For more information on these new capabilities and how ThreatConnect can help your organization maximize the impact of your security program, please reach out to sales@threatconnect.com or /request-a-demo/
