Posted
 Chief Information Security Officers (CISOs) have more data on emerging cyber threats and vulnerabilities than ever before. In fact, the majority of CISOs at Fortune 1,000 companies will tell you they are drowning in data and alerts. Despite having all of this information, most security leaders struggle to explain to their fellow C-Suite executives and board of directors how at risk their organizations actually are from cyber events. They can’t translate threats and vulnerabilities into the real picture they need to provide – a financial view into cyber risk.
Chief Information Security Officers (CISOs) have more data on emerging cyber threats and vulnerabilities than ever before. In fact, the majority of CISOs at Fortune 1,000 companies will tell you they are drowning in data and alerts. Despite having all of this information, most security leaders struggle to explain to their fellow C-Suite executives and board of directors how at risk their organizations actually are from cyber events. They can’t translate threats and vulnerabilities into the real picture they need to provide – a financial view into cyber risk.
This inability to understand the core mission of cybersecurity at a business level is one of the most critical challenges facing CISOs today. Our role as cybersecurity professionals is not solely about defending IT systems, it’s about risk mitigation and protecting the business from harm. But to do this effectively requires security professionals to come to grips with how to quantify risk and communicate risk in both cyber and financial terms. Once translated into this view, security and business are on the same page. Risk mitigation then becomes the north star focus, and the struggle of resource prioritization finally dissipates as it becomes crystal clear what scenarios matter most. CISOs and Security Leadership will also know exactly what scenarios to protect against, threat teams where to focus their attention, and SOC teams how to prioritize their response.
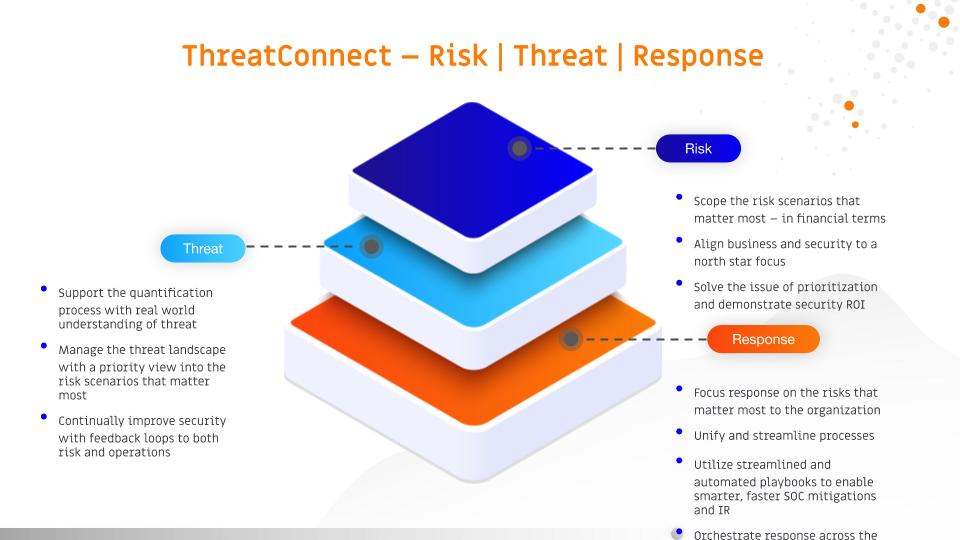
At ThreatConnect, we call this the risk, threat, response paradigm. It is a truly revolutionary approach that is improving security outcomes by marrying cyber risk quantification (CRQ), threat intelligence platform (TIP), and SOAR capabilities.
Interested in learning more about our Risk, Threat, Response approach?
Request a Demo!
Intelligence-Driven SOAR: Driving a Threat Oriented View
Making Security Really Good
ThreatConnect has long been known as a leader in the TIP market. We understood the need to enable large enterprises to aggregate all available threat data – both internal and external, structured and unstructured – analyze it rapidly, distill it down to understand the most critical threats, automate action, and then produce tactical, operational, and strategic threat intelligence all in one place. We also believe that a TIP should allow secure crowdsourcing to surface more intelligence than you could on your own – that’s why we built CAL (Collective Analytics Layer) to harness the work of thousands of threat analysts around the globe. But that wasn’t enough. We recognized the need to make this intelligence work with your other systems to automate action based on workflows you establish.
That’s why we added security orchestration, automation, and response capabilities to our platform. This provided security leaders with critical intelligence-driven SOAR capabilities that broke down silos and helped unify the actions of the entire security team with a true threat oriented view — a major leap forward for security at the time.
Most automation and orchestration solutions have their limits when it comes to enabling speed and effectiveness at the same time. While automation can speed up a repetitive process and orchestration can direct the broader security ecosystem, without intelligence they’re often only doing mundane tasks.
Intelligence-driven SOAR improves your ability to manage the threat landscape with a priority view of the threats that matter most. And in so doing, this bi-directional feedback loop continuously improves both threat management and operations.
Risk Quantification: Driving a Risk Oriented View and
Moving Cybersecurity From Really Good to Great
Cyber Risk Quantification is the critical third leg of the cybersecurity stool that will fundamentally alter the way security works and how it is communicated to the business. CRQ technology enables businesses to create a financial view into cyber risk, allowing for proactive cyber defense and data-driven decision making across the board. It creates the north star for all of security — leveraging the advancements we’ve made in creating a threat oriented view to enable a risk oriented view.
Our September 2020 release of ThreatConnect Risk Quantifier™ (RQ – formerly Nehemiah Risk Quantifier) created the market’s only portfolio of products that unifies the actions of the security team around the most critical risks, supports their response with streamlined and automated workflows and strengthens the entire security ecosystem through powerful technology integrations.
By quantifying risk, based on possible losses from business interruption and response, exposure can be directly linked to the business services that are affected. This is the missing link in the ability of CISOs to communicate the risks facing their companies.
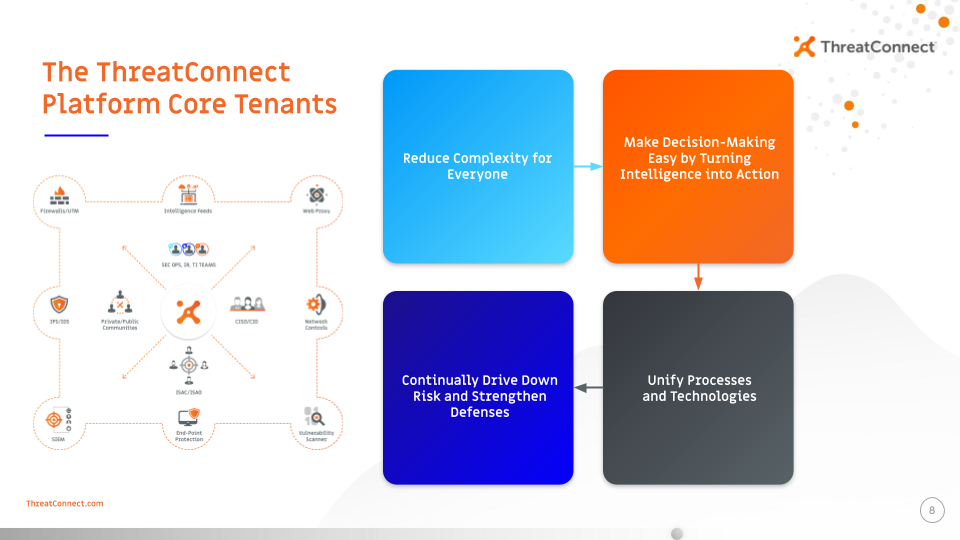
The combination of RQ, TIP, and SOAR, is how organizations can move their cybersecurity programs from good to great. While each capability is a necessity for any modern cybersecurity program, their combination reduces complexity to help make decision making easy, unites processes and technology, and continually drives down risk to help you strengthen your defenses.