
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.
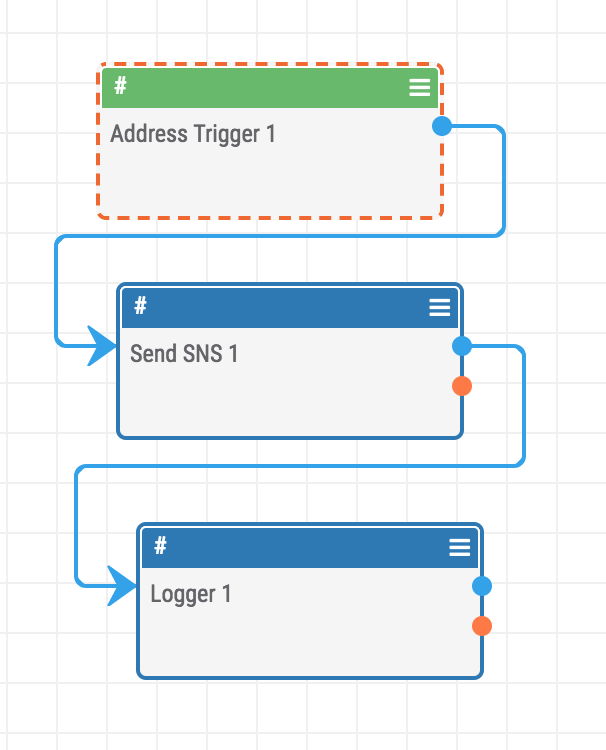
Playbook Fridays: How to Control the Cloud with Playbooks
Playbook Fridays: How To Control The Cloud With Playbooks Interacting with SNS from ThreatConnect Playbooks ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. You can also communicate with third-party services to trigger events outside of ThreatConnect. Why Was the Playbook […]

Track to the Future
How to use historical intelligence to get back to the future and defend your organization We need to talk about something. In the history of this blog, we’ve never discussed Back to the Future. It’s crazy to think that that’s the case as arguably the second-greatest sci-fi trilogy is rife with quotable lines and meme-able […]
Casting a Light on BlackEnergy
A look into BlackEnergy malware and using ThreatConnect to aggregate and memorialize the identified intelligence. As workers prepared to head home on December 23, 2015, an attack against Ukraine’s energy sector left 230,000 without electricity (or heat) for six hours. The attackers demonstrated a variety of capabilities, including spearphishing emails and variants of the BlackEnergy […]
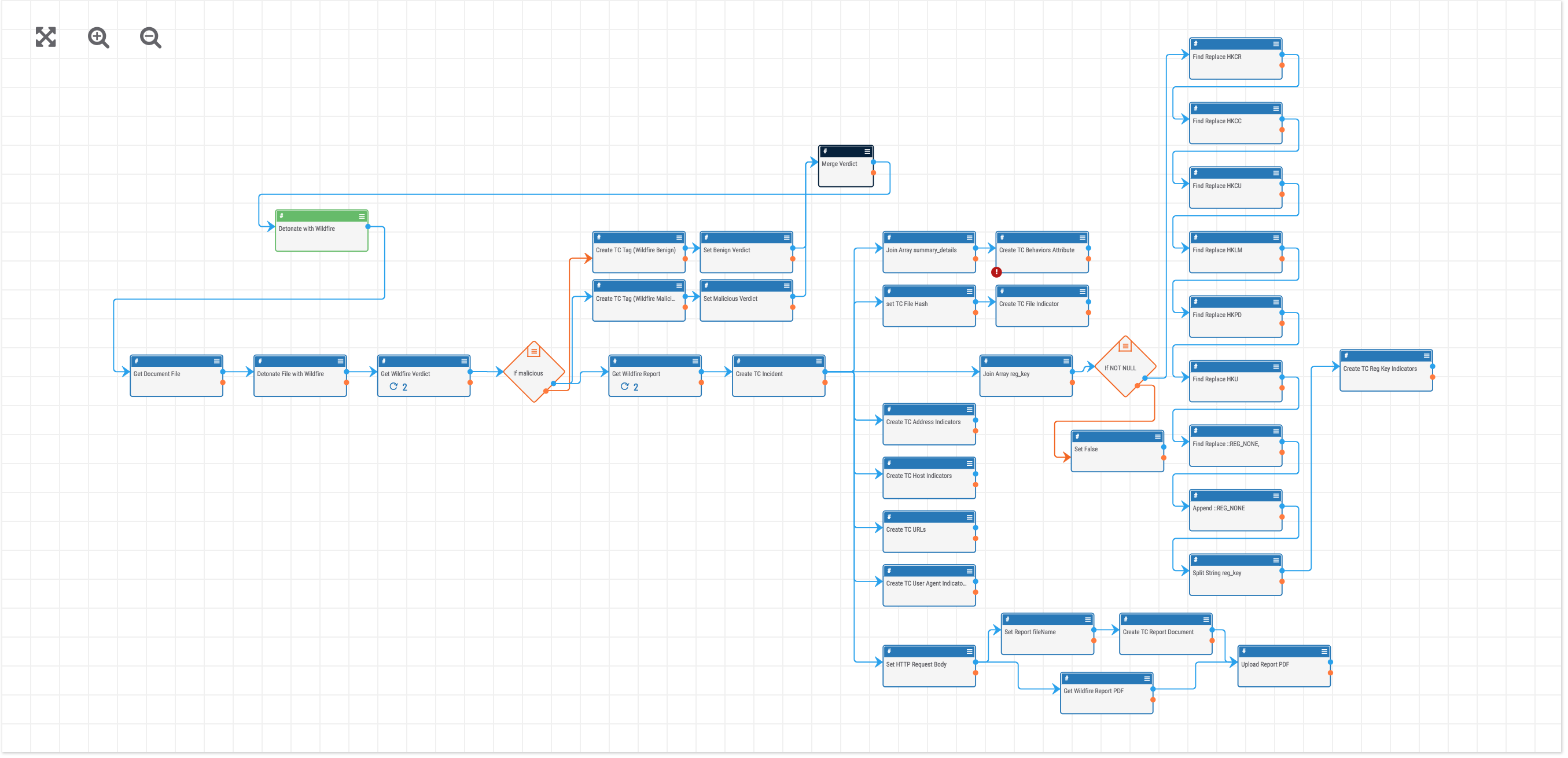
Playbook Fridays: How to Build a Playbook in ThreatConnect
This week: Palo Alto Wildfire Malware Triage Playbook ThreatConnect is beginning a NEW blog post series. We will continually publish posts featuring Playbooks that can be built in the Platform. ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in […]
ThreatConnect Training: Save Time and Act Faster with Playbooks
Automate almost any cybersecurity process – no coding needed Ingesting threat data, malware analysis, and data enrichment can all be time consuming tasks. To learn how to automate these things (along with almost any cybersecurity task) using an easy drag-and-drop interface, watch the video, Save Time and Act Faster with Playbooks. It’s presented by Dan […]
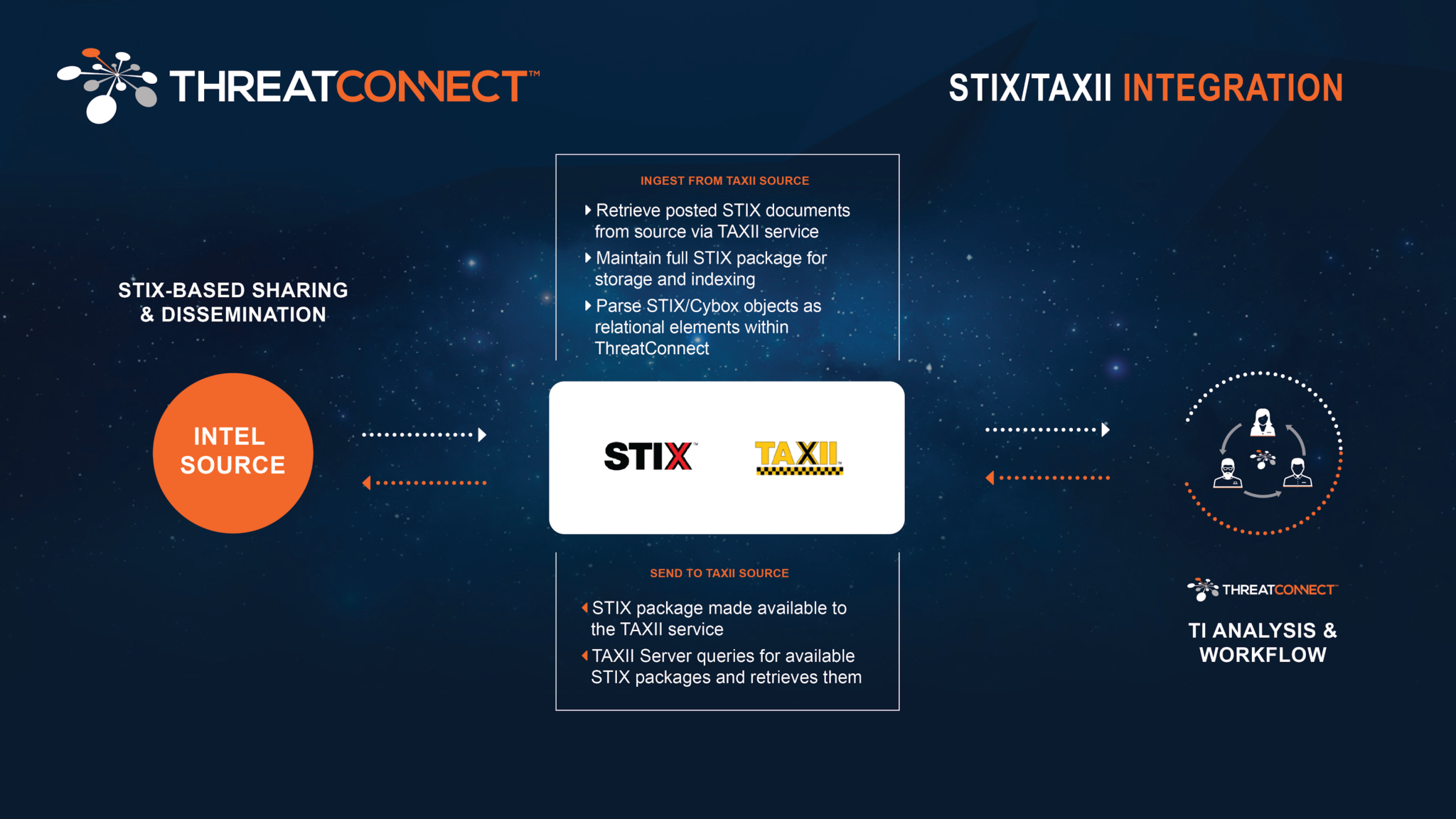
Sharing Threat Intelligence Using STIX-TAXII
STIX-TAXII | Learn how to Collect and Send STIX Threat Intelligence in ThreatConnect Sharing threat intelligence and collaborating with your peers, vendors and partners, is not optional to protect your network. ThreatConnect® supports STIX-TAXII. STIX (Structured Threat Information Expression™) and TAXII (Trusted Automated eXchange of Indicator Information™) standards in our Platform to enable effective sharing […]
ThreatConnect Introduces its Multi-Environment Orchestration Capability
Providing flexibility and scalability to unite all of your security management processes Everyone is talking orchestration these days. Including us. But not one to sit back and let our Playbooks capability languish, we took it one step further. Now, Playbooks has the ability to run across multiple environments including cloud, office networks, or virtual. The […]
Finding Nemo(hosts)
How to identify potential malicious infrastructure using ThreatConnect, DomainTools, and more All that is bad is not known Individual indicators are often highly perishable, but understanding the patterns adversaries use to stand up infrastructure can give us a leg up by illuminating suspicious domains potentially prior to an attack. But where to start? How to […]
How to Use Threat Intelligence & Orchestration to Defeat Stranger Threats
Threat Intelligence and Orchestration can come together to defeat threats to your network, or D&D monsters…whichever you face. When watching Stranger Things it’s easy to notice many incidents throughout the show worthy of further investigation. Many of the characters in the show could actually benefit quite a bit from the processes and techniques security professionals […]
Getting Started with the ThreatConnect Query Language (TQL)
From Neanderthal to Ninja Users in ThreatConnect have a lot of data to go through, and a big part of our job is finding ways to empower them to find the right data faster. Our Browse Screen harbors an array of different filters you can apply and chain together, slicing and dicing the dataset to […]
Phantom of the Opaera: New KASPERAGENT Malware Campaign
KASPERAGENT Malware Campaign resurfaces in the run up to May Palestinian Authority Elections ThreatConnect has identified a KASPERAGENT malware campaign leveraging decoy Palestinian Authority documents. The samples date from April – May 2017, coinciding with the run up to the May 2017 Palestinian Authority elections. Although we do not know who is behind the campaign, […]
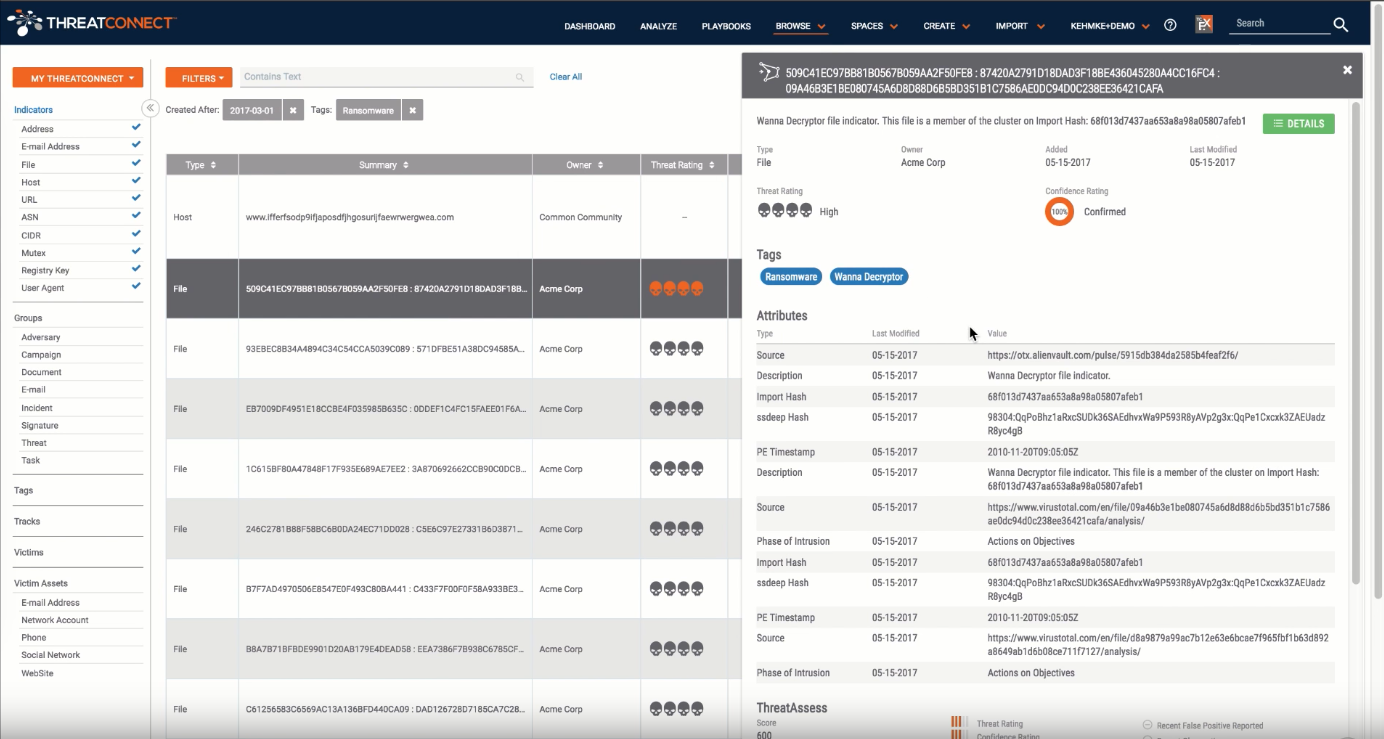
Get Started with Cyber Threat Analysis: How to Research Ransomware
Learn How to Research Ransomware in ThreatConnect We recently recorded a video to show what members of our Research Team do on a daily basis within the ThreatConnect platform to perform cyber threat analysis, research threats, conduct investigations, create new intelligence, and more. Our hope is that this video will help to educate viewers on the […]
