Posted
This week: Palo Alto Wildfire Malware Triage Playbook
ThreatConnect is beginning a NEW blog post series. We will continually publish posts featuring Playbooks that can be built in the Platform.
ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can occur consistently and in real time, without human intervention.
Why was the Playbook created?
The Palo Alto Wildfire (a cloud-based service that provides malware sandboxing) Malware Triage Playbook was created to make the malware analysis process more effective by speeding up reaction time, eliminating time consuming repetitive tasks, and deliver the results to the analyst in a way they can quickly make decisions and take action.
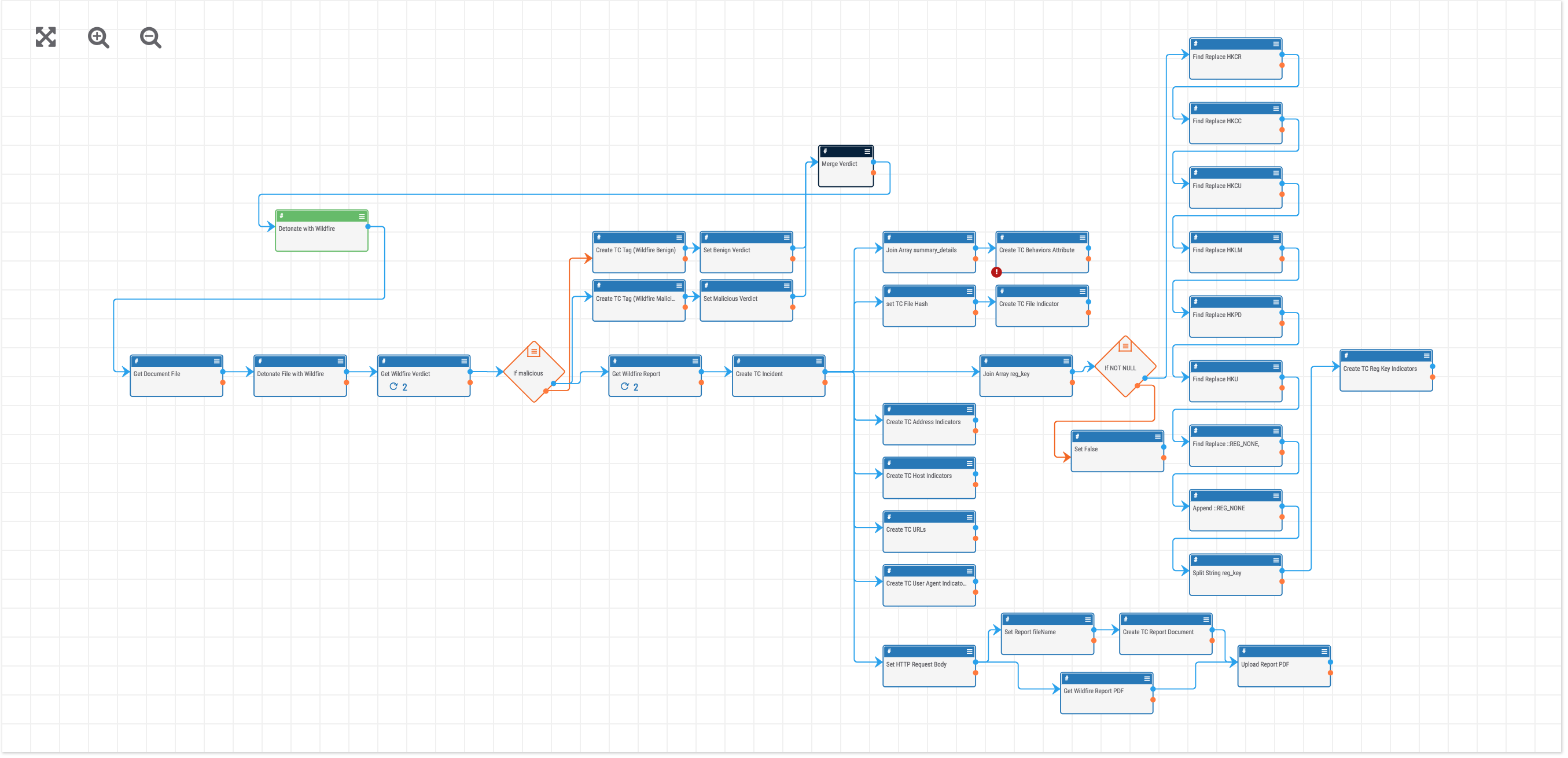
Though this Playbook can be triggered in a variety of ways, most commonly it would use an email, HTTP, or user action trigger and solves the following:
- The submission of suspicious binary files to Palo Alto Wildfire for analysis.
- The retrieval and parsing of report results.
- The creation of report results, including behavior details and associated indicators in ThreatConnect for easy correlation across other malware reports and intelligence sources.
- The assignment of a task for an analyst to review the results and take action.
How it works:
- When the playbook is triggered, the binary is first detonated with Wildfire.
- Next, the Wildfire Verdict is retrieved and used to determine the path the Playbook takes.
- The binary in ThreatConnect is tagged with the Wildfire verdict and a response is sent back to the user letting them know the outcome.
- If the Verdict was malicious, the Playbook will get and parse the Wildfire report results.
- An incident is created in ThreatConnect to store the report details.
- The Wildfire behavior details are saved as an attribute on the incident.
- File, Registry Key, Address, Host, URL and User Agent indicators that were parsed from the report are created in ThreatConnect and associate with the Incident.
- The HTML version of the Wildfire report is downloaded and saved as a ThreatConnect document and associated with the Incident.
- Finally, we want to be sure that the incident is reviewed so a Task is created in ThreatConnect and assigned to an analyst for review.
How to Build It:
- Templates are found in the Templates section of the Playbooks dashboard. Import the Palo Alto Wildfire Malware Triage template to get started..
- Enter the requested variable information during the import step to speed up configuration.
- Review the configuration of the trigger and apps to ensure they are accurate for your organization.
- Activate the Playbook.
- If using the default User Action trigger you can trigger the Playbook by pressing the “Detonate with Wildfire” user action on a ThreatConnect document containing a suspicious binary.
Learn more about Playbooks here. Questions about this Playbook or have a Playbook you’d like to contribute? Please contact: support@threatconnect.com.