Posted
Playbook Fridays: How To Control The Cloud With Playbooks
Interacting with SNS from ThreatConnect Playbooks
ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. You can also communicate with third-party services to trigger events outside of ThreatConnect.
Why Was the Playbook Created?
Threat intelligence is far reaching in today’s highly diverse and global infrastructure, we wanted a way to set the wheels of AWS in motion based on certain criteria in TC. With AWS SNS you can have a single, reliable point of entry to start AWS services and send user notifications, here are a few examples.
- SMS
- Mobile Push Notifications
- Lambda Functions
- SQS
We also released the SNS TC Playbook app open source to give you a starting point for the simple code required to extend the best TIP into the world’s largest cloud provider.
What are some use cases?
- Send alerts to your IR team using multiple methods
- Add an item to a worker queue for later processing such as checking your user database for newly discovered spam accounts
- Run a lambda function to take a snapshot of a URL at the time the indicator is added to TC and associate a PDF back to that URL Indicator
How It Works
We have included a sample PlayBook in the GitHub repo called “AWS-SNS-Integration-PlayBook.pbx” that you can import directly into your ThreatConnect instance.
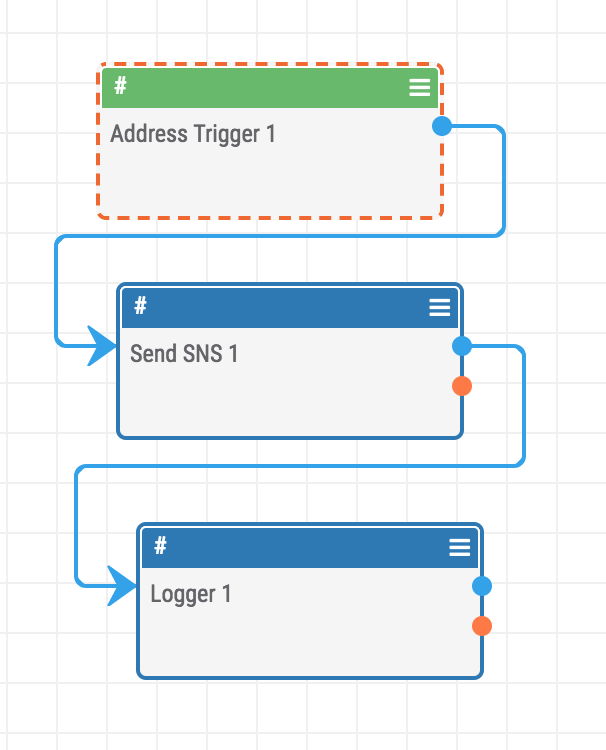
In this example we use an Indicator Trigger to start the playbook when an Address Indicator is created. We could have used any indicator type or any action on those indicators such as Email Address deleted or when a tag is applied to a Host.
So whenever a new Address indicator is created in TC this PlayBook will start executing the Send SNS app.
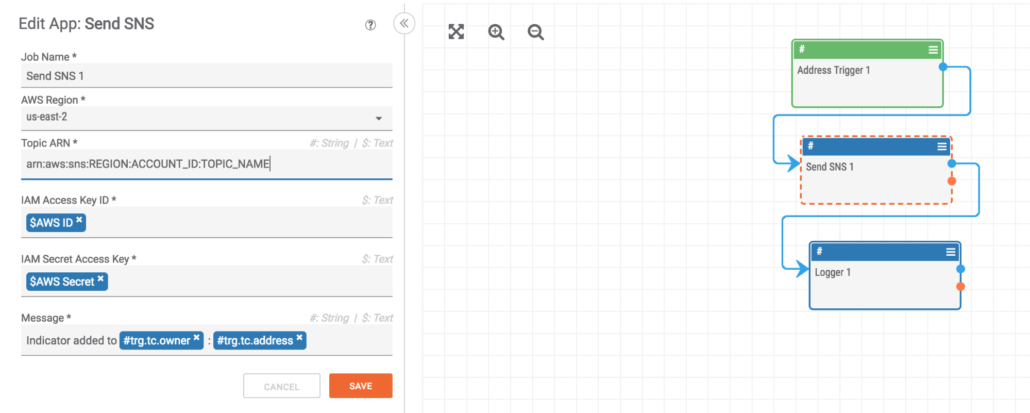
Here we have access to various attributes of the Address such as the address itself, the owner, the ThreatAssess score, confidence rating and a link back to the ThreatConnect details page.
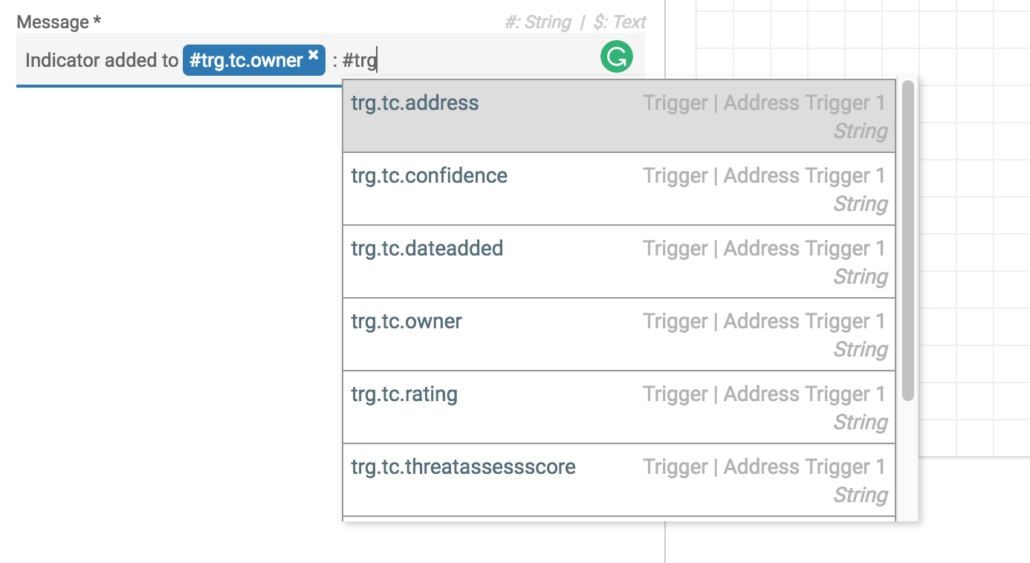
This information is passed up to SNS in the message parameter for later use in your AWS workflow. We also log an “sns.debug” string variable that will provide either the SNS MessageID or debugging information if the SNS call failed.
For this demo I used an SNS topic that sends me an email with with the Address and the ThreatConnect Owner.
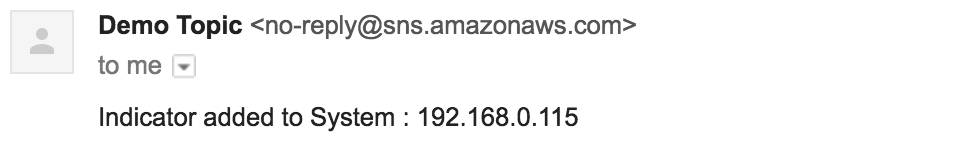
We hope this gives you inspiration to write your own PlayBooks and integrations, you can find more information on this project’s GitHub page or by looking at the ThreatConnect Developer Documentation.
Happy Protecting Your Network!
Read the rest of the Playbook Fridays blog series: