
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.
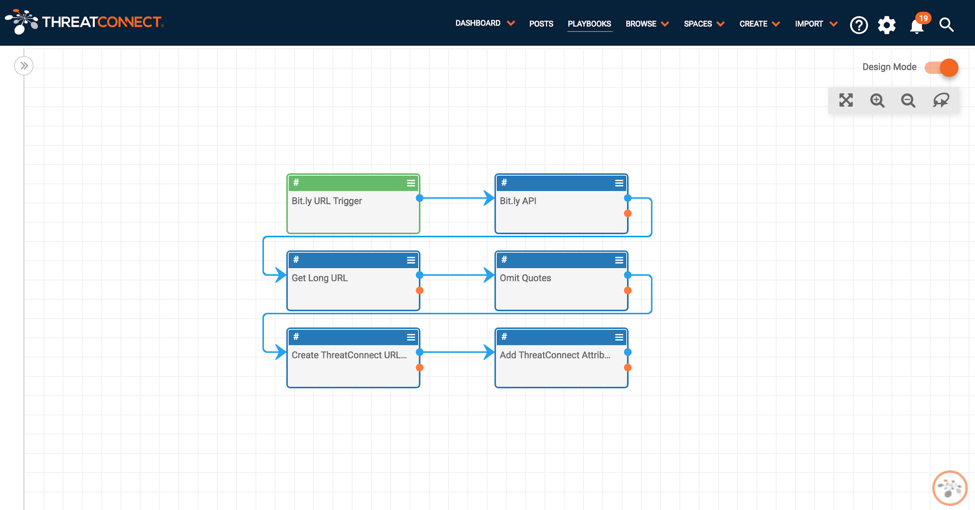
Playbook Fridays: Bit.ly URL Decoder
This Bit.ly URL decoder Playbook automatically lengthens potentially malicious bit.ly urls. ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can occur consistently and in real time, without human intervention. As analysts, […]
Playbook Fridays: How to Create a Playbook for the Non-Programmer
Playbooks for the Non-Programmer using what else, Star Wars ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can occur consistently and in real time, without human intervention. We’ve written lots of […]
5 Reasons to Mark a False Positive in ThreatConnect
By taking an intelligence-driven approach, we can start to connect the dots in a more interesting fashion ThreatConnect allows you to curate almost every facet of your intelligence — including indicator reputation. One of the best ways you can help keep a tidy shop is to flag an indicator as a False Positive (FP) when […]

Productivity: Part I
Happy New Year! Whether you are a customer or fan, thank you for joining us on this ride to enable teams to perform above their limits through augmentation with technology. Studies show the most common New Year’s resolutions are often giving something up such as smoking, or a weight-loss-driven goal such as diet and exercise(1). […]
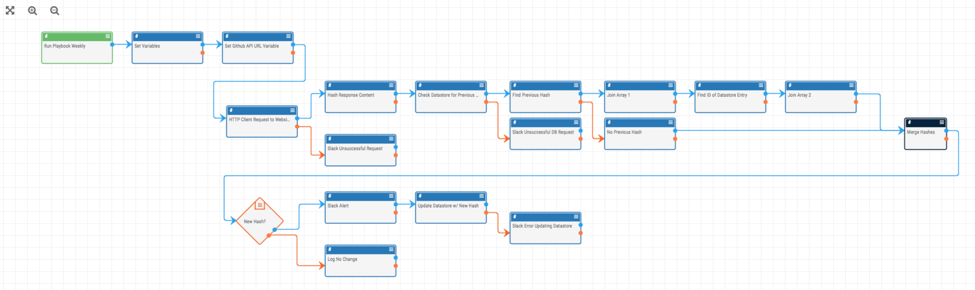
Playbook Fridays: Github Activity Monitor
This Playbook is designed to automate the monitoring and alerting of Github activity for a given user ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can occur consistently and in real […]
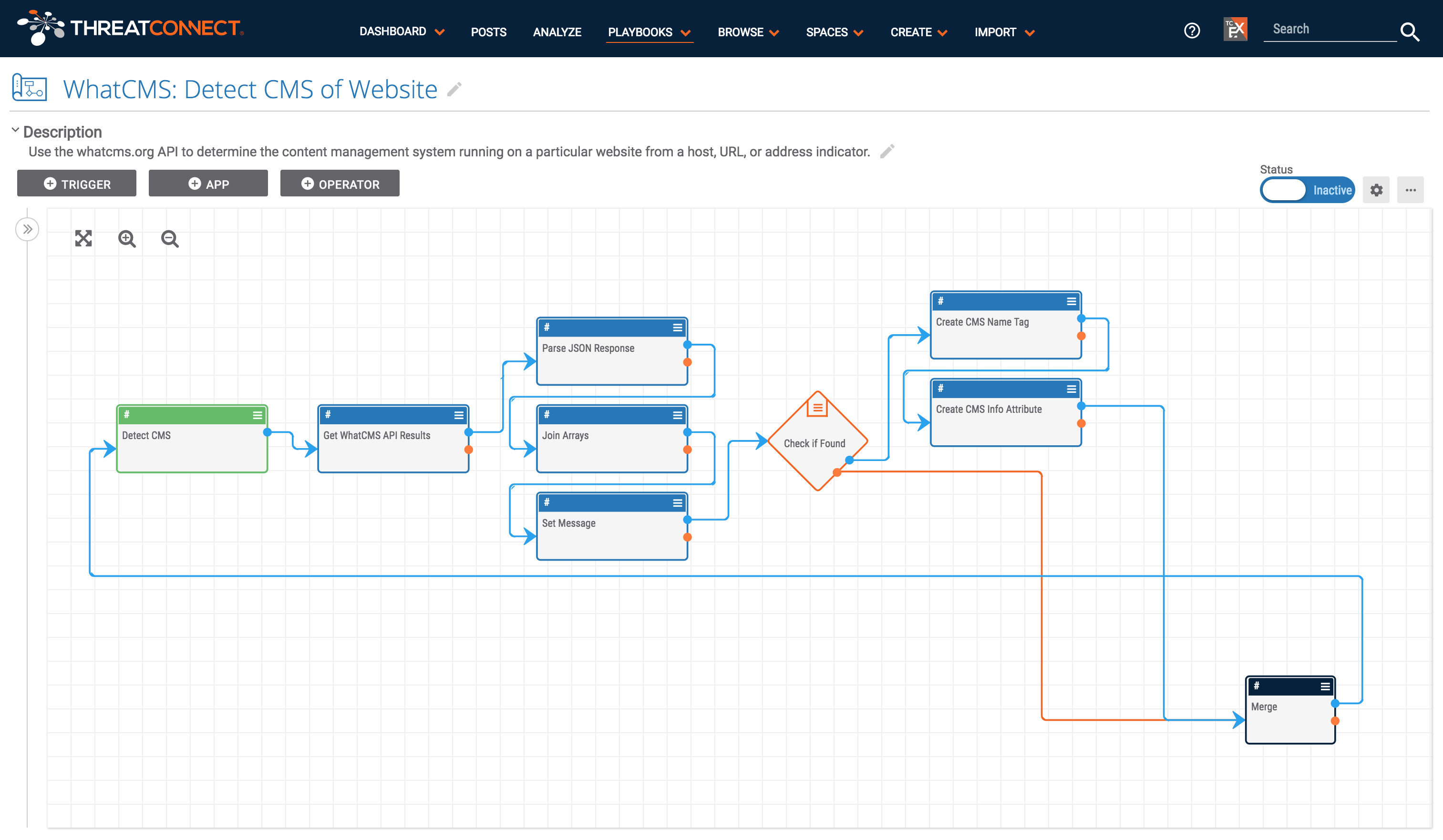
Playbook Fridays: WhatCMS API Playbook
Detect a website’s content management system (CMS) ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can occur consistently and in real time, without human intervention. Determining the CMS (Content Management System) […]

Polarity – Pulsedive Integration
Polarity’s integration framework can connect to your existing third-party data sources ensuring you have contextual awareness of data from across your organization. Our latest integration is with Pulsedive, a free threat intelligence platform that provides real-time threat data on IOCs including IPs, domains, and URLs. What is Pulsedive? Pulsedive is a new analyst-centric threat intelligence […]
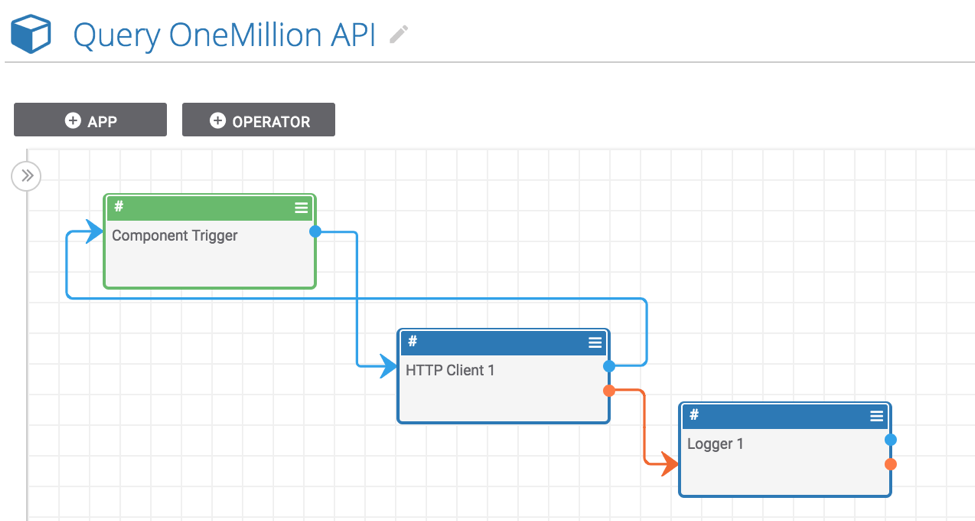
Playbook Fridays: OneMillion API Component
Using this Playbook Component, incident responders and analysts can check if a given domain exists on any lists of the most frequently visited hostnames ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis […]
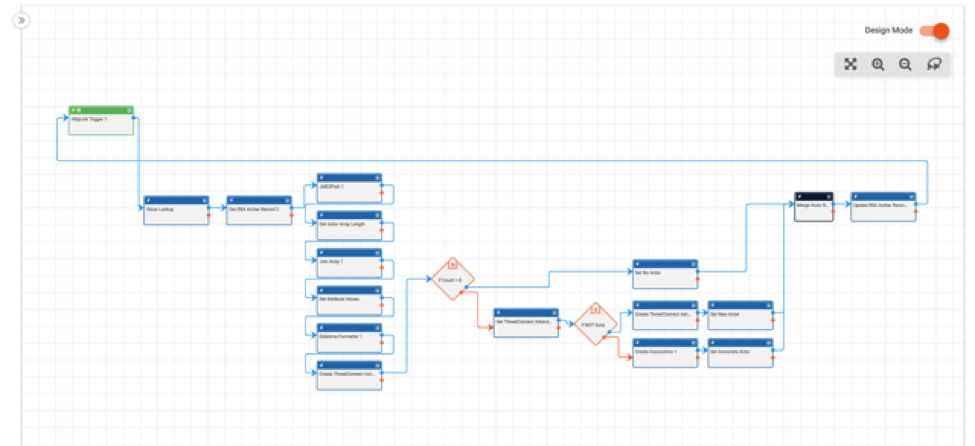
ThreatConnect’s RSA Archer Integration, Playbooks, and Apps (oh my!)
One of our top integration requests has been Playbooks for RSA Archer. Good News: we now have numerous out-of-the-box integration capabilities for connecting RSA Archer and ThreatConnect! These apps and playbooks templates allow you to perform a variety of use cases with Archer, from saving users time by automatically assigning relevant threat intelligence to cases, […]
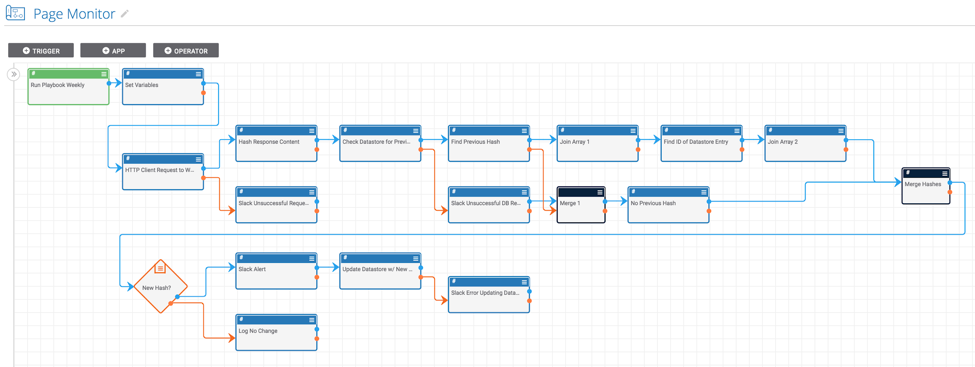
Playbook Fridays: Web Page Monitoring
Monitor a website’s content and get alerts if it changes ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can occur consistently and in real time, without human intervention. Monitoring websites for […]
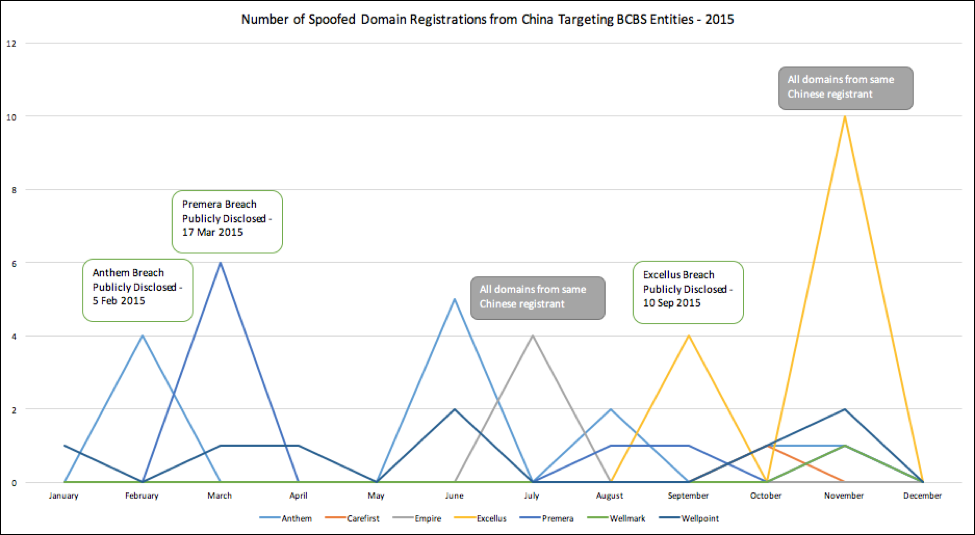
Playbook Fridays: Domain Spinning Workbench Spaces App
Gain insight into possible permutations of domain names to indicate suspicious activity and further analysis For this week’s Playbook Fridays post, we’re mixing things up a little. Instead of directing you on how to set-up a specific Playbook, we’re going to help you take advantage of an App we built which is set up on […]

Polarity – VulnDB Integration
Polarity was built to be as versatile as possible, not only enabling a real-time collective memory across teammates, but also extending to any 3rd-party datasource through our integration framework. This allows analysts to get any information they need whether from internal or external sources. Our newest integration is with Risk Based Security’s VulnDB. The Polarity […]
