Posted
This Bit.ly URL decoder Playbook automatically lengthens potentially malicious bit.ly urls.
ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can occur consistently and in real time, without human intervention.
As analysts, we should never spend our time on mundane and monotonous tasks when dealing with the cyber antics of adversaries. Playbooks have provided such powerful and flexible capabilities that no adversary should take comfort in thinking that the good guys are getting stuck in the weeds when dealing with these feeble attempts of masquerading.
One common example of such techniques implemented by adversaries is using Bit.ly services to mask malicious URLs and hosts. Sure, as analysts we can manually reverse this process to reveal the dangerous sites, but with Playbooks this is now a trivial matter that requires no effort from us!
Enter the Bit.ly URL decoder, a very simple Playbook that automatically lengthens potentially malicious bit.ly urls.
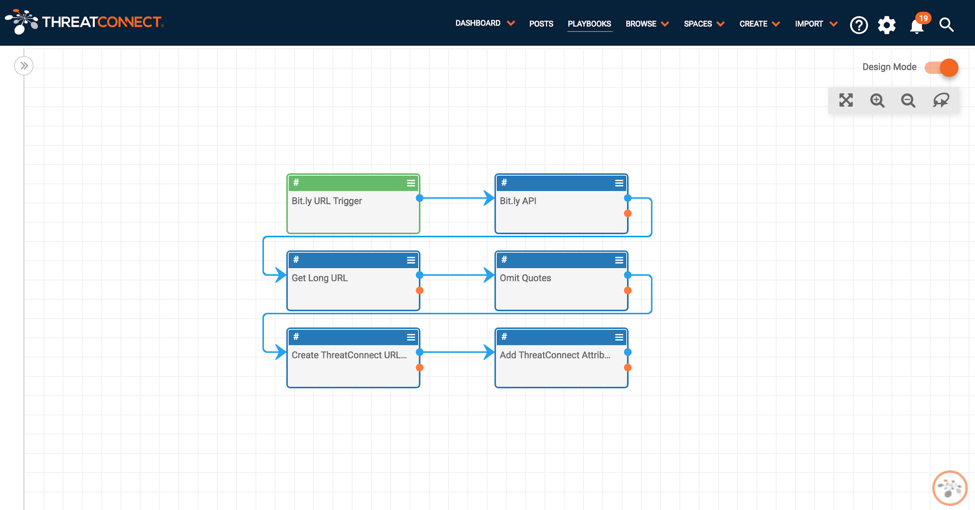
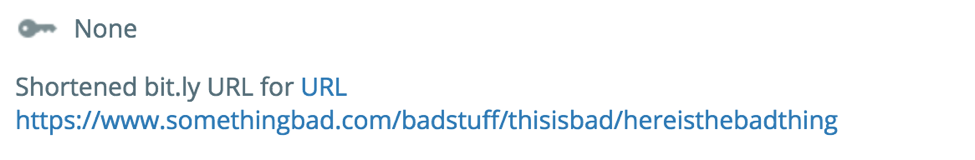
Upon creation of any Bit.ly URL in the Platform, the Playbook is kicked off automatically (thanks to the URL trigger with text filtering) and leverages the bit.ly API to retrieve the lengthened version of the link, kindly adding it as a URL in the Platform with a link to it in the description.
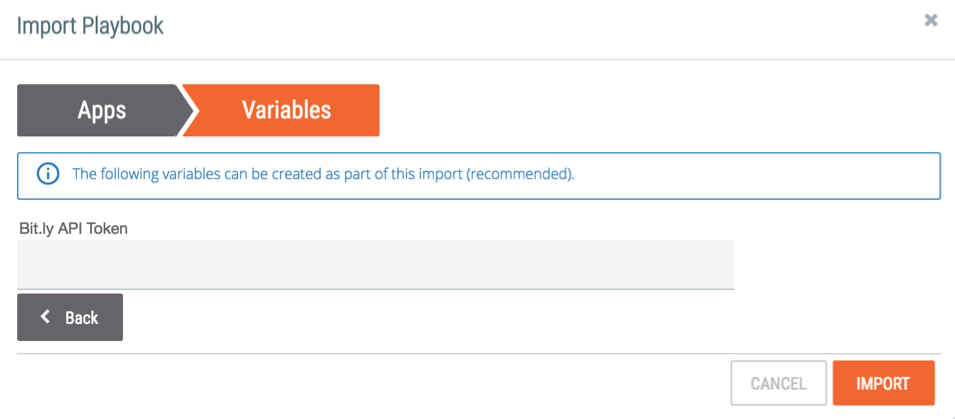
To set up this Playbook in your org., download the .pbx file from the ThreatConnect PlayBook repo, import it, and configure the variable for the bit.ly API key when prompted.
You also need to make sure the Trigger has the correct owner configured as well as the Create TC URL app. Then you’re all set!