Posted
This Playbook is designed to automate the monitoring and alerting of Github activity for a given user
ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can occur consistently and in real time, without human intervention.
Many malicious actors, from unsophisticated defacers to sophisticated actors, use Github to develop and/or serve malicious content. This is largely because Github offers version control and Github Pages for automatically deploying content.
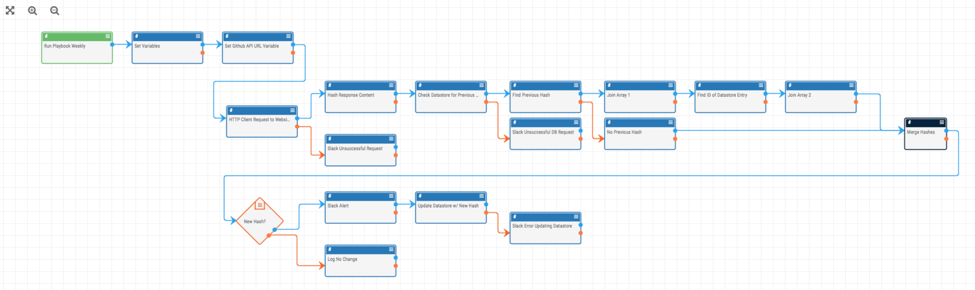
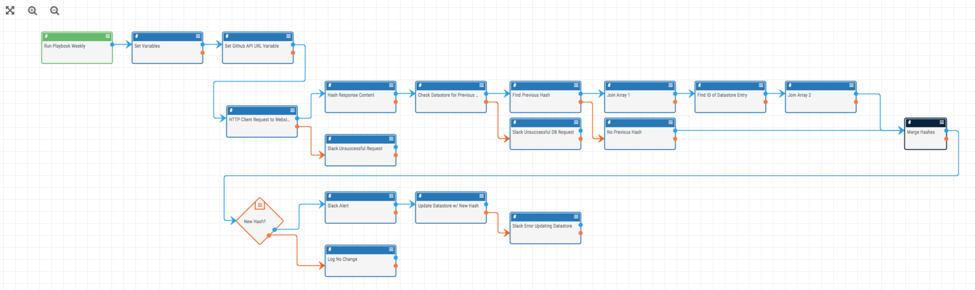
With so much diverse, malicious activity on Github, it is important to be able to track the changes on a malicious code repository. This Playbook is designed to automate the monitoring and alerting of Github activity for a given user. In this way, you can get alerts whenever a github user does a public action.
This Playbook is based on the Page Monitor.pbx Playbook described here: /blog/web-page-monitoring/ . It is designed to be run once a week and uses Github’s public API to check if there is any new activity. If there is new content, it sends an alert (in this case via slack).
Installing the Playbook
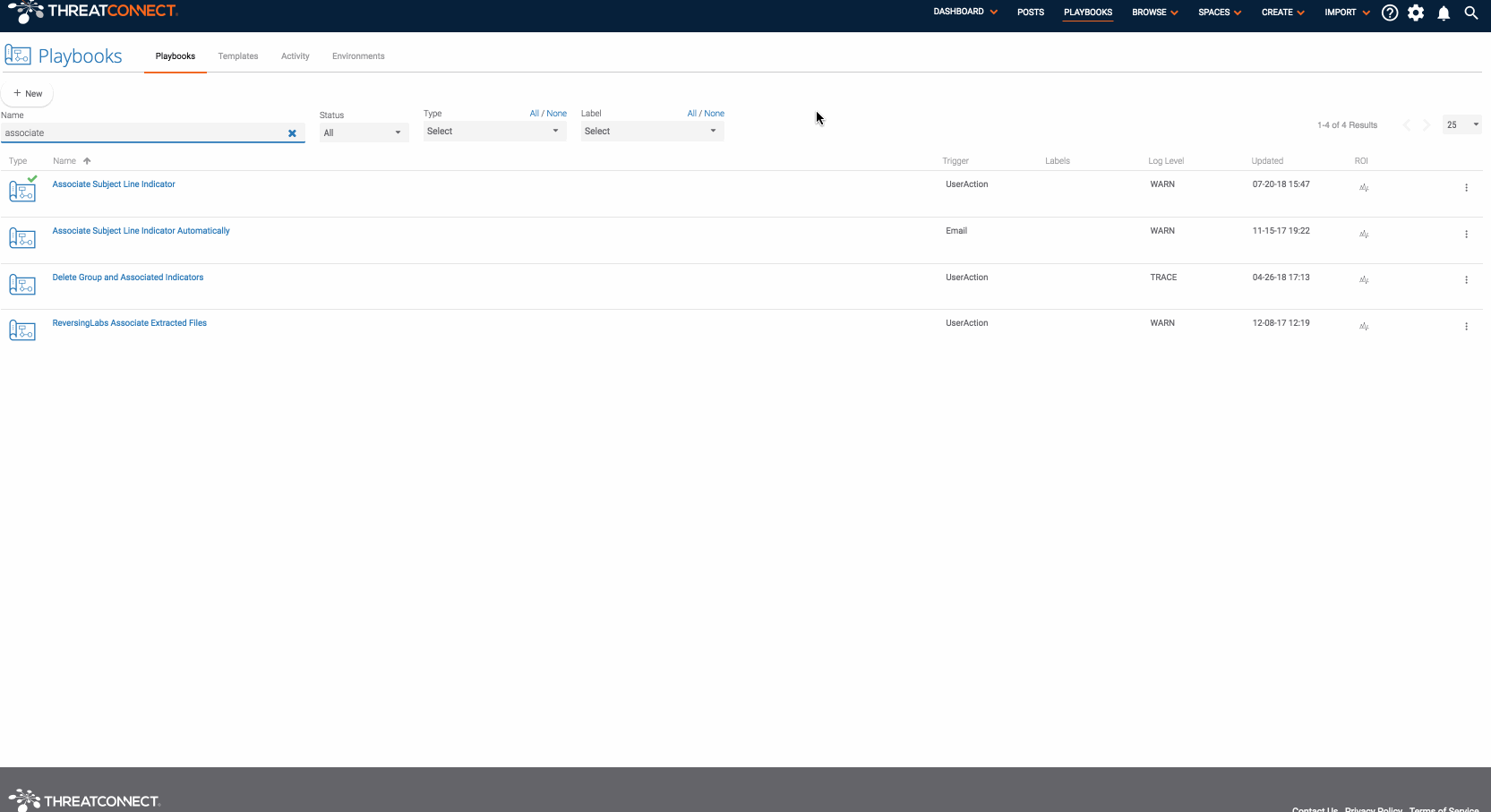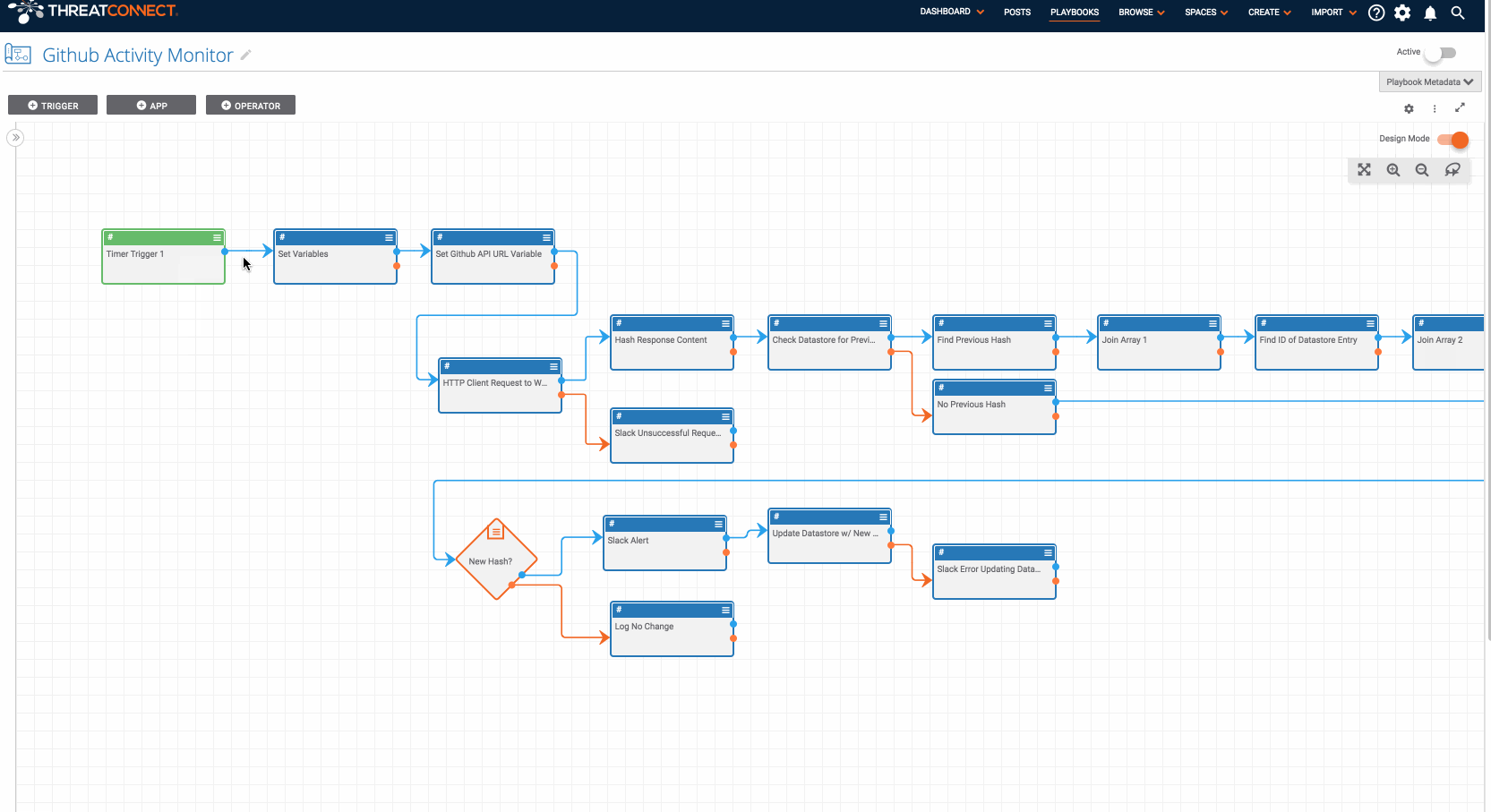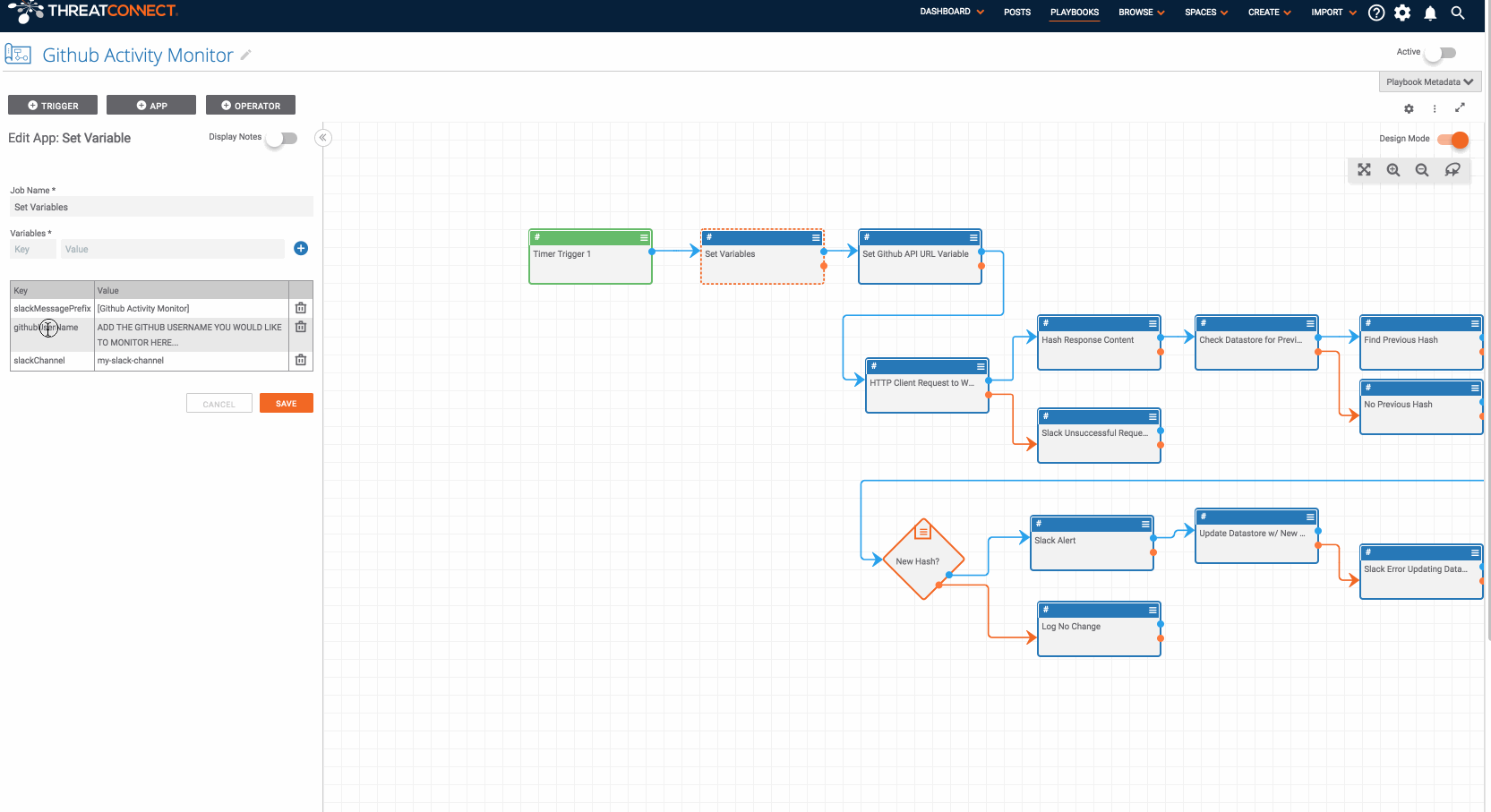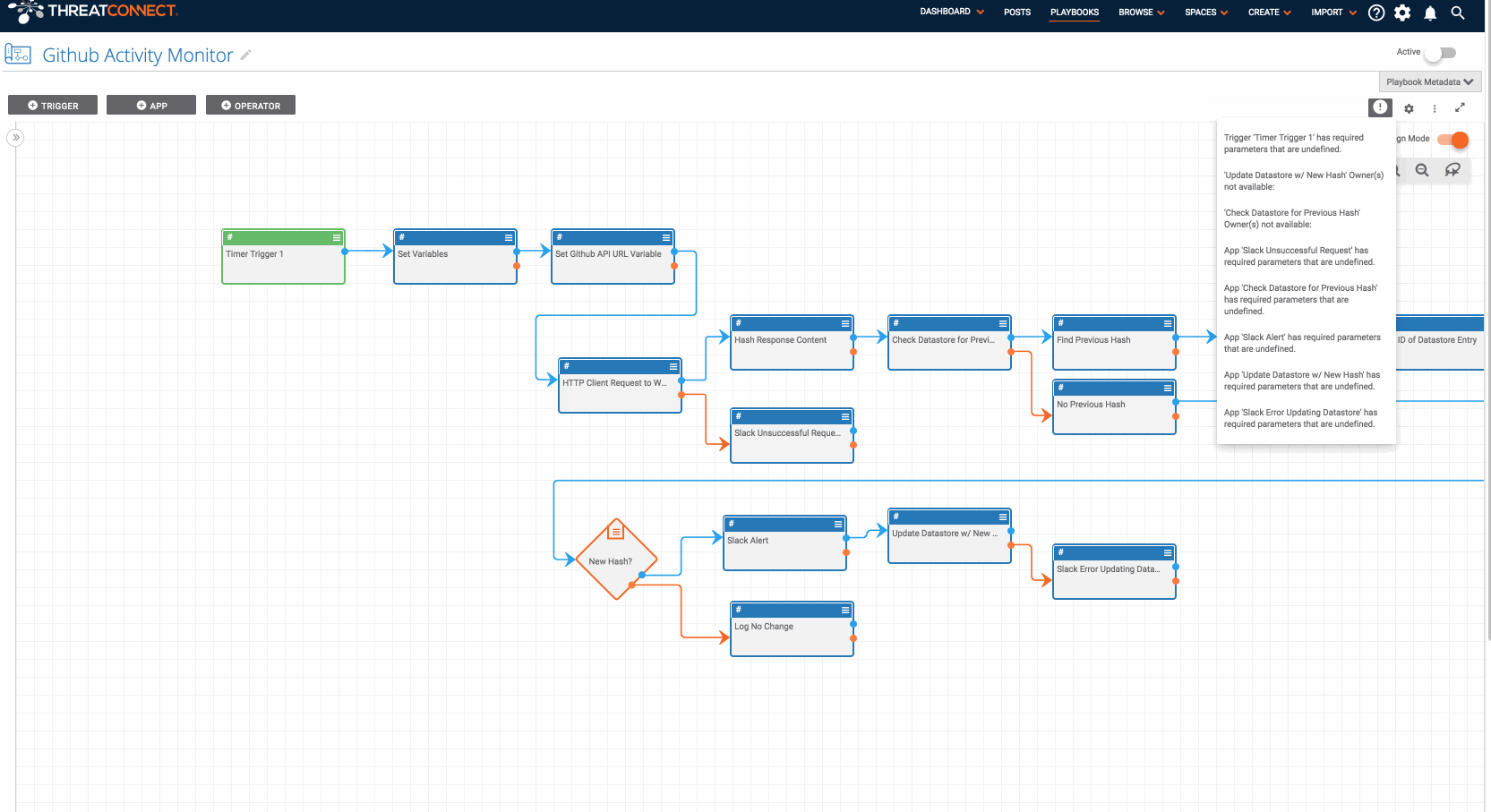
To install the Playbook, download the Github Activity Monitor.pbx Playbook and install it in ThreatConnect from the Playbooks page. Once it is installed, start by editing the “Set Variables” app (the Playbook app right after the trigger). You will need to provide the “slackChannel” variable to which messages will be sent and the “githubUserName” variable you would like to monitor. Now, there are a few other apps which need some credentials and other information. The best way to find which apps still need updated is to try to turn the Playbook on which will provide you a list of apps that still need modified. Among the apps that need edited are the slack apps and the datastore apps.
But what if you don’t use Slack? Easy: the Slack apps can be replaced with an app to send an email, create a task in ThreatConnect, or create a Jira issue (among other options). If you have any questions or run into any problems with anything mentioned in this blog, please raise an issue in Github! If you would like to have your app or playbook featured in a Playbook Friday blog post, submit it to our Playbook repository (there are instructions here: https://github.com/ThreatConnect-Inc/threatconnect-playbooks/wiki/Contributions-Workflow).