
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.
Playbook Fridays: Query Hashes via Email Submission
We were asked by a customer to extend the analysis functionality of ThreatConnect to other SOC personnel that didn’t have direct access to the Platform. So we did. This Playbook creates a new process in which non-ThreatConnect users can get on-the-fly analysis and context into potential hash IOCs they’ve encountered, and simplifies the process of […]

Security Teams Can Spend Less Time Querying & More Time Analyzing with Polarity’s Updated Splunk Integration
We’re excited to announce our updated integration with Splunk, a platform that empowers teams from Security to IoT to Business Analysis with data. These updates will enable Polarity users to retrieve a more in-depth analysis from different Splunk queries even more seamlessly than before. Now, instead of running the same Splunk query over and over to get […]
Playbook Fridays: Generate Intelligence Reports, Part 2
As promised, below is how to customize this app to change the disclaimer, and contact information. However, I encourage you to stick around as I dig in for a deeper dive, explaining in detail all of the code within this app. With that said, let’s go! Replace everything after the = on Lines 32-34 and […]

Polarity – urlscan Integration
Ever gotten an email with a link and wondered what that link is and if you should click on it? Ever seen a random url in your logs and wondered what it is? Well, with Polarity’s latest integration with urlscan, you will always know if that url or domain is malicious or not! What is […]
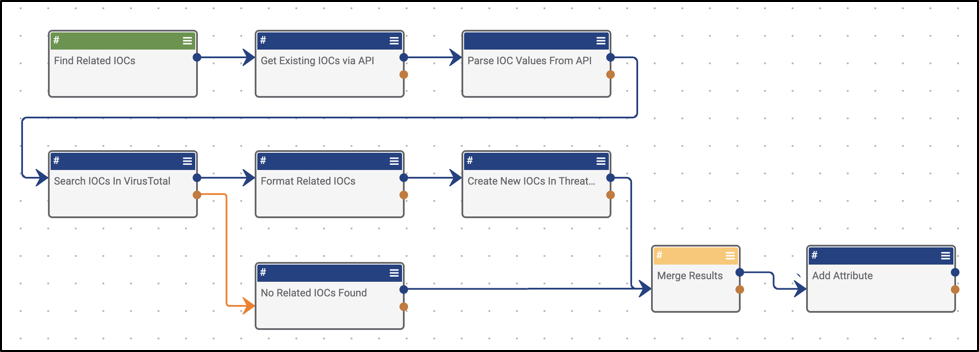
Best Practices for Writing Playbooks, Part 2
This is Part 2 of the Best Practices for Writing Playbooks in ThreatConnect blog post series. This time, I wanted to get into the weeds on some best practices for development and testing. If you haven’t already read it, I highly recommend taking a minute and reading Part 1, here. To Playbook or not to […]
Playbook Fridays: Generate Intelligence Reports
John Locke, a wise man, once said, “No man’s knowledge here can go beyond his experience.” The same is true with the latest release of ThreatConnect that includes quite a few new features. The feature that has me excited the most is the AppBuilder functionality. The primary reason is that I can see the full […]
The Secret to our (Customer) Success
I recently sat down with Jody Caldwell, the Senior Director of Customer Success at ThreatConnect, to pick his brain and understand the specifics of how we help a customer from initial deployment throughout the entire span of their relationship with ThreatConnect. Will you describe your role at ThreatConnect? What does a day look like for […]
Playbook Fridays: Component IOC All Data Pull
For all of the other applications that ThreatConnect does not have an integration for, API is the best way to go. With the repeating of calling IOC data, the use of the Component allows you to have all of that data in a format to map it as needed The reason for the PlayBook came […]

Leveraging LDAP with Polarity
Our latest integration is with Lightweight Directory Access Protocol (LDAP). The Polarity – LDAP integration automatically searches LDAP for usernames and emails and returns associated accounts. What is LDAP? Lightweight Directory Access Protocol or otherwise known as LDAP is a software protocol for enabling anyone to locate organizations, individuals, and other resources such as files […]
Operationalizing Threat Intel: On the Importance of “Boring” Dashboards
This blog post is for boots-on-the-ground security analysts. Managers, turn back now! By the end, you’ll be able to create a tailor-made dashboard in ThreatConnect to help inform your day-to-day activities. “Flash! Ah-ah! Savior of the universe!” -Queen I cringe a little bit whenever I hear someone say that dashboards are just to show “pretty […]
Best Practices for Writing Playbooks in ThreatConnect, Part 1
Proper naming conventions, using Descriptions and Labels, and more! This is the first of a multi-part series of posts on Playbooks best practices. There’s a lot of material to cover, and it would be too much for a single post. In Part 1, I’m sticking to the basics – how to use proper naming conventions […]
Playbook Fridays: Reporting Through Email Attachment
This Playbook streamlines a process for reporting to a threat intel team without asking the reporting party to rework any existing infrastructure, or go too far out of their way to make findings accessible. This also works regardless of who the reporting party is; whether that is a SOC, customer, or industry partner. The most […]
