
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.
ThreatConnect and Tanium: Improved Incident Response with Intel Packages
ThreatConnect and Tanium’s partnership just got stronger. Recently, we released 3 Apps for Tanium Threat Response as well as developed a brand new Playbook App for Tanium Platform. With these Playbook Apps, you can take immediate action to investigate, stop, and remediate potential threats at the endpoint based on external threat intelligence. Let’s dive in! […]
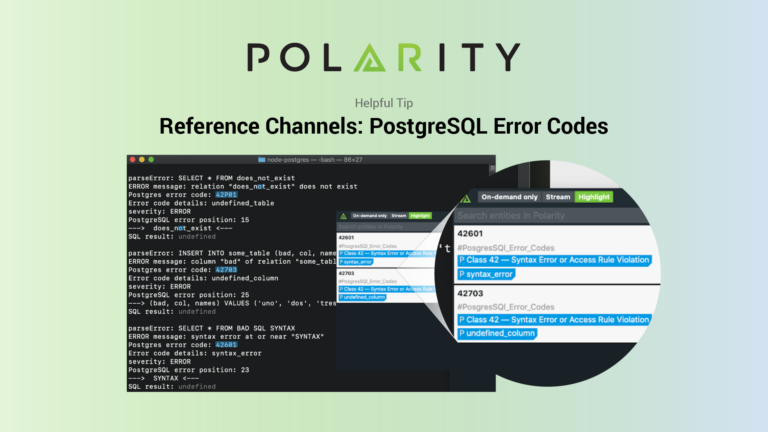
Polarity Reference Channels: PostgreSQL Error Codes
Today’s post continues an ongoing series on Polarity User Tips. Data tells a story, Polarity helps you see it with Augmented Reality overlaying contextual information as you work, giving you the right data at the right time to make informed decisions and take action with speed (no glasses or goggles required). This guide explains how […]
Playbook Fridays: Converting your IOCs to CSVs
Welcome to ThreatConnect’s Playbook Fridays! We will continually publish posts featuring Playbooks (and sometimes Dashboards!) that can be built in the Platform. ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can […]
ThreatConnect Research Roundup: More Kimsuky “AutoUpdate” Malware
Howdy, and welcome to the ThreatConnect Research Roundup, a collection of recent findings by our Research Team and items from open source publications that have resulted in Observations of related indicators across ThreatConnect’s CAL™ (Collective Analytics Layer). Note: Viewing the pages linked in this blog post requires a ThreatConnect account. In this edition, we cover: […]
ThreatConnect Research Roundup: Kimsuky “AutoUpdate” Malware
June 19 2020 Edition Howdy, and welcome to the ThreatConnect Research Roundup, a collection of recent findings by our Research Team and items from open source publications that have resulted in Observations of related indicators across ThreatConnect’s CAL™ (Collective Analytics Layer). Note: Viewing the pages linked in this blog post requires a ThreatConnect account. In […]
Polarity for Phishing Email Analysis
Today’s post continues an ongoing series on Polarity Use Cases. Data tells a story, Polarity helps you see it with Augmented Reality overlaying contextual information as you work, giving you the right data at the right time to make informed decisions and take action with speed. No glasses or goggles required, Polarity is software that […]
Orchestration With and Without Intelligence: What’s the Difference?
Orchestration informed by security intelligence from within your environment, and threat intelligence from a variety of external sources, is more effective, resilient, and adaptive. An intelligence-led approach will inform your strategy for orchestration in two key ways: Intelligence on an adversary’s capabilities, attack patterns, and intent will inform how you build and configure orchestration capabilities […]

Get Even Better Data Awareness & Recall with the Updated Polarity-ThreatQuotient Integration
Today’s post continues an ongoing series on Polarity Integrations. Data tells a story, Polarity helps you see it with Augmented Reality overlaying contextual information from the applications you use every day, no glasses or goggles required. With over 100 powerful integrations, Polarity’s open-source Integrations Library arms you with the right data at the right time […]

Empowering Teams with Data Awareness
Polarity Gives you Superhuman Data Awareness & Recall Polarity is software-based Augmented Reality for your data. That means superior Data Awareness and Recall for your team. In this post, we break down what we mean by “Data Awareness”. Empowering Teams with Data Awareness Having the right data to make an informed decision is Data Awareness. It’s about […]

Enabling Teams with Data Recall
Polarity Gives you Superhuman Data Awareness & Recall Polarity is software-based Augmented Reality for your data. That means superior Data Awareness and Recall for your team. In this post, we break down what we mean by “Data Recall”. Enabling Teams with Data Recall Perfect Data Awareness doesn’t matter much if it isn’t there exactly when you need it. Getting […]
ThreatConnect Research Roundup: Probable Sandworm Infrastructure
June 12 2020 Edition Howdy, and welcome to the ThreatConnect Research Roundup, a collection of recent findings by our Research Team and items from open source publications that have resulted in Observations of related indicators across ThreatConnect’s CAL™ (Collective Analytics Layer). Note: Viewing the pages linked in this blog post requires a ThreatConnect account. In […]

Announcing the Polarity Community Contributor of the Quarter, June 2020
We would like to congratulate Michael Francess and the Wyndham team as the Polarity Community Contributor of the quarter! Michael and the Wyndham team’s contributions have greatly helped Polarity build its product roadmap and understand how to improve the Polarity experience for everyone. We encourage all of our Polarity Community members to look at opportunities […]
