
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.
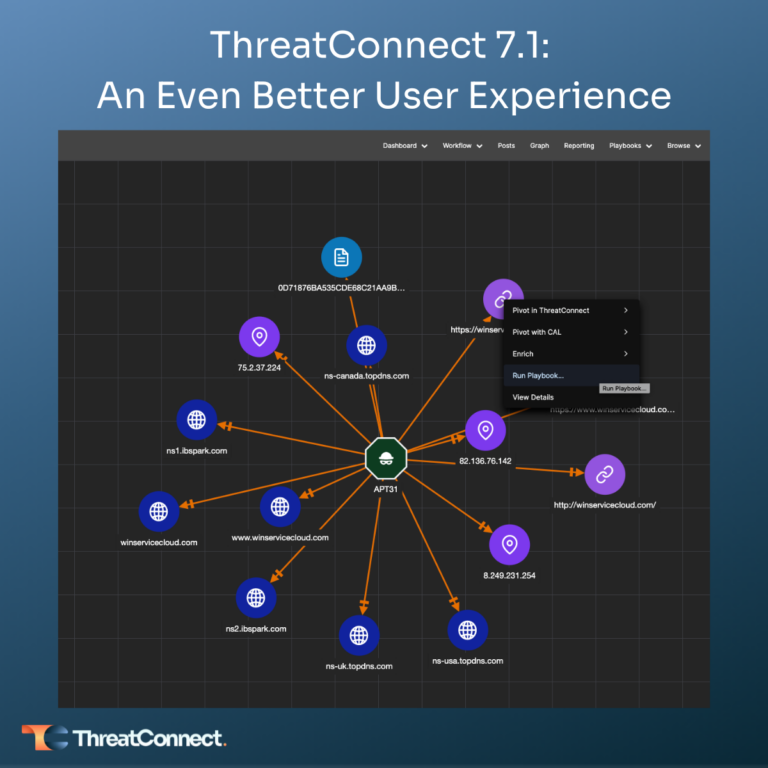
ThreatConnect 7.1: An Even Better User Experience
ThreatConnect’s 7.1 release delivers an even better ThreatConnect user experience. ThreatConnect 7.1 strengthens capabilities introduced in 7.0, including Enrichment and Reporting, providing more flexibility and customization while also refining the Platform for a more streamlined user experience so security teams can be more efficient and effective. Built-in Enrichment v2 When investigating an indicator, knowledge is […]

ThreatConnect, Inc Achieves SOC 2 Type 2 Compliance
In partnership with one of the most well-respected independent auditors, Schellman & Company, ThreatConnect has achieved SOC 2 Type 2 compliance with our Dedicated Cloud and Risk Quantifier products for the second year in a row. Over the last few years, ThreatConnect has demonstrated our commitment to protecting our customer’s data by aligning our security […]

The 7 Tenets of Threat Intel Operations – Tenet #1: Elevating Threat Intelligence
In the first blog of this series, I took a 30,000-foot view of the 7 Tenets of TI Ops defined in the Dawn of Threat Intelligence Operations paper. In this edition, I’m going to dig into Tenet #1 – Elevates threat intelligence to a mandatory, critical security operations role – in more detail. In the […]

Why Every Team Needs Federated Search
Data, information, and knowledge exists in too many different places to ask employees to search them all manually. New employees don’t know where data is and senior employees waste time searching systems that may not even contain the information they are looking for. Searching through all of this siloed information is not only inefficient, but […]

Balancing the Benefits and Challenges of FAIR – A Practitioner’s View
If you have been a FAIR practitioner for years, like me, or maybe you are just starting out, you may have noticed (or will notice) that FAIR is great for understanding your financial risk exposure, however, it has its challenges. I’m not here to highlight everything, but the good does FAR outweigh the bad. No […]
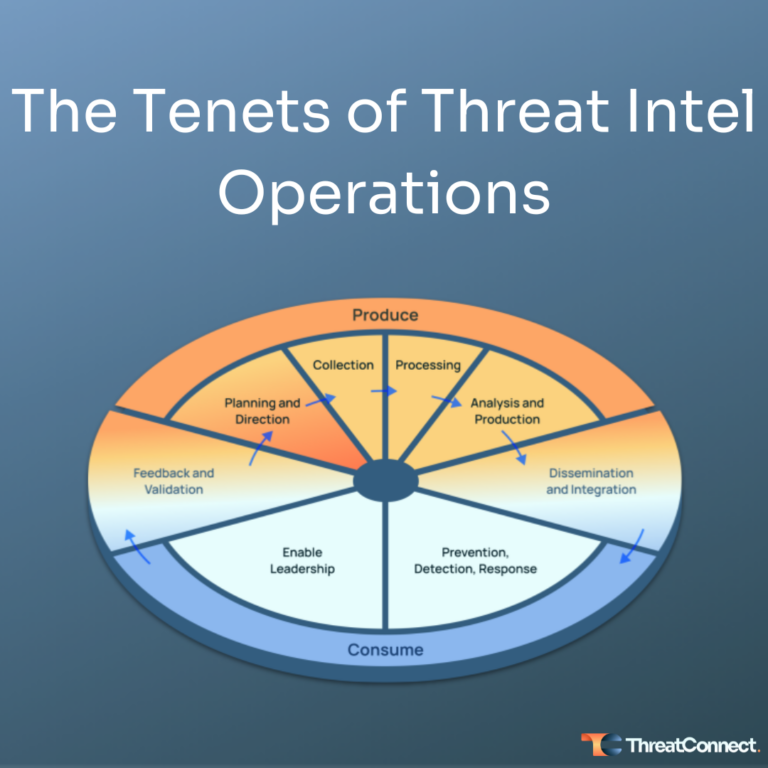
The Tenets of Threat Intel Operations
Many organizations struggle to demonstrate value for threat intel and their threat intelligence teams. The intel team is trying to do the right thing though. They are collecting threat intelligence, managing it into usable shape, making it available for use, and then struggling to find consumers who need, or want, to use it. Security operations […]
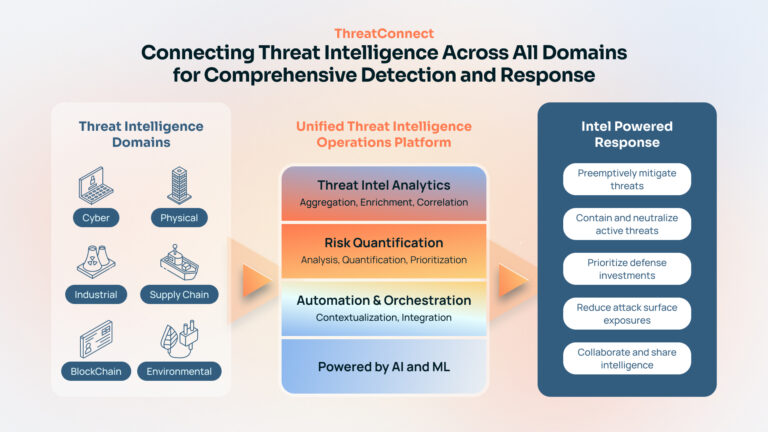
Uniting the Threat and Risk Intelligence Across ALL Domains
Blog authored by Dave DeWalt, Founder and Managing Director, NightDragon. Read it on the Night Dragon’s website here We live in a true golden age of data and information. Organizations have more threat intelligence, whether it be cyber, physical, etc, at their fingertips than ever before, from vulnerabilities to adversary profiles and more. Inside these […]

The Need for an Evolved Threat Intel Lifecycle
If you’ve seen our blog, “Luke in the Sky with Diamonds,” or have read Adam Shostack’s excellent book: “Threats: What Every Engineer Should Learn From Star Wars,” you know that Star Wars is really just a series of cybersecurity parables. In this blog, we’re going to examine how the lead-up to the Battle of Hoth […]
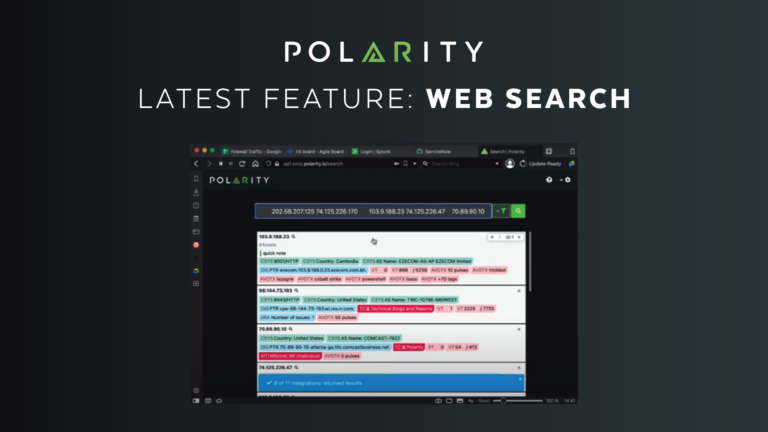
Introducing Polarity Web Search
We are thrilled to announce our release of Polarity Web Search, a new feature that enables users to get immediate value from their integrations and annotations with more ease and speed than ever. Any Polarity user can now log in through a browser and use just one search to find relevant information across all of […]

It’s 2023, Automating Your Threat Intelligence Operations Doesn’t Have to be Hard
Threat intelligence activities, especially enrichment, analysis, and action, have traditionally required a lot of manual work. Threat Intel Operations analysts are not expected to be coders, spending their time in Python to automate their activities, and it’s not usually a “one and done” activity. Changing APIs and process improvements that require scripts to be updated […]
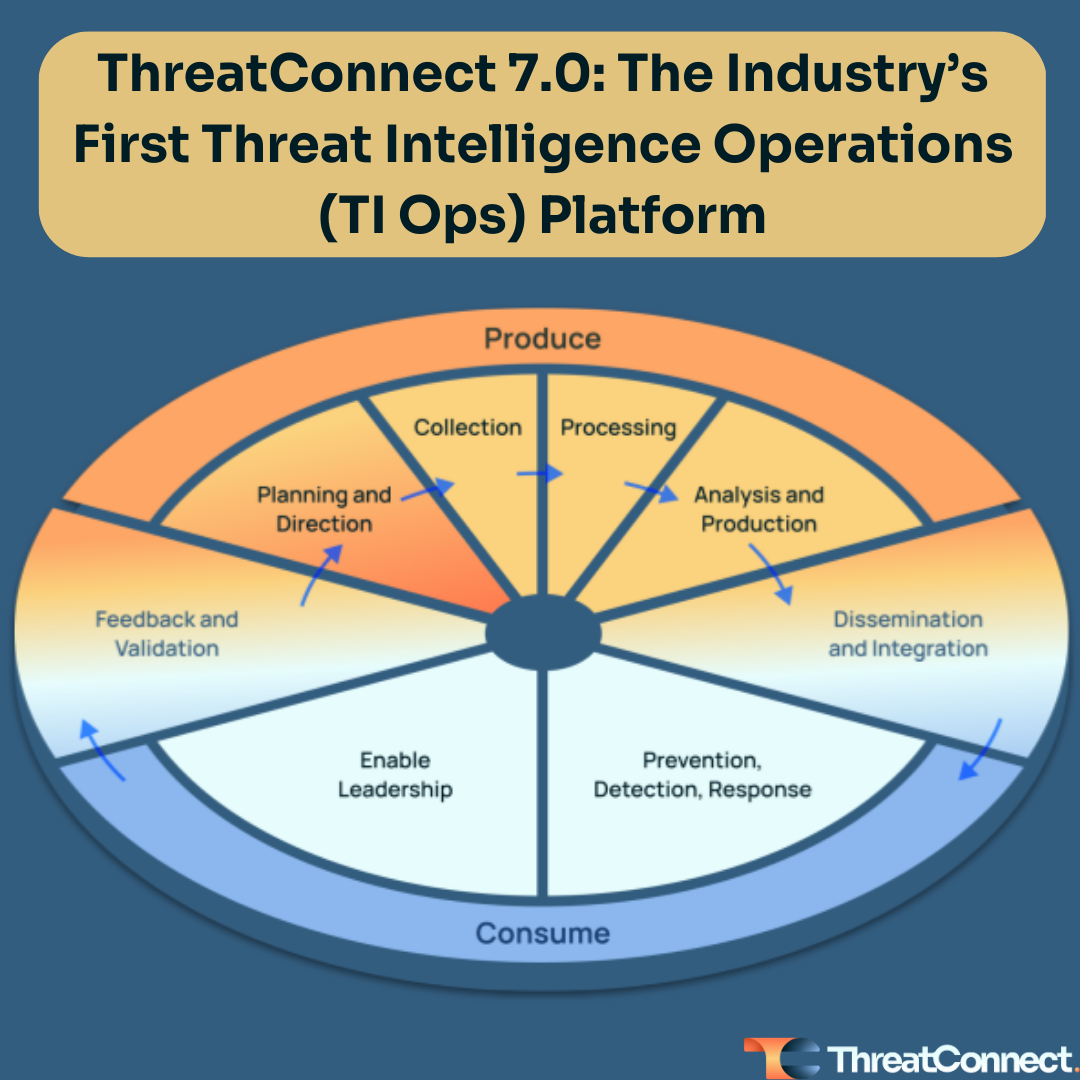
ThreatConnect 7.0: The Industry’s First Threat Intelligence Operations (TI Ops) Platform
A dedicated threat intelligence team and function has been treated as a luxury for far too long, and if there is one, demonstrating its value is a persistent struggle. However, security leaders know that the modernization and digitization of the enterprise, an expanding attack surface, and evolving adversaries are stressing their teams and capacity. In […]

Powering Cyber Fusion Operations with ThreatConnect
Cybersecurity technology, processes, and tradecraft are constantly evolving as the attack surface, and vectors expand. It’s no secret that threats are growing faster than defenders can combat them. Organizations often create specialized teams with a specific mandate, such as incident response and threat hunting, which become siloed. This impacts their ability to share valuable threat […]
