Posted
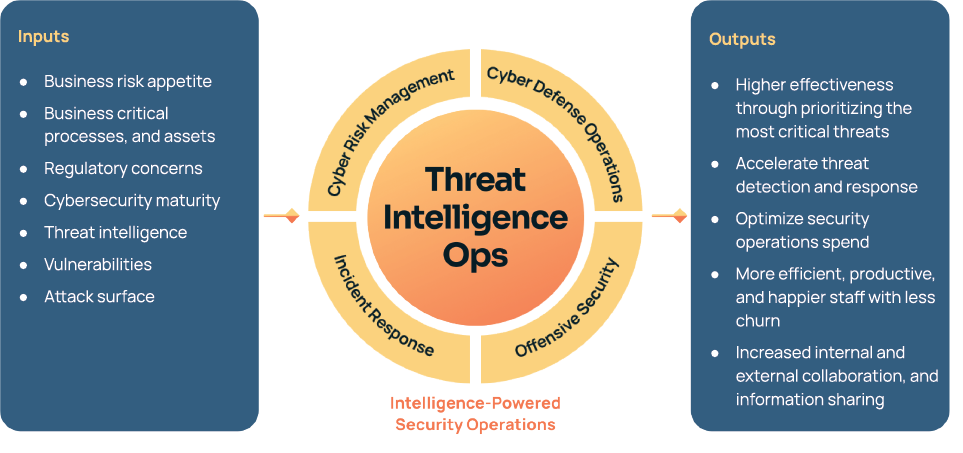
In the fast-paced, ever-changing cybersecurity landscape today, organizations recognize the need to transform their security operations to achieve greater effectiveness and deliver better protection while demonstrating a measurable return on investment. When threat intelligence operations (TI Ops) infuses cyber threat intelligence into everything a security team does, it results in better decision-making, greater efficiency, and stronger collaboration. This is the concept of Intelligence-Powered Security Operations (IPSO). IPSO makes it possible for organizations to apply their efforts where they’ll have the biggest impact against the most dangerous threats and most prevalent attack tactics.
Placing TI at the core of your security operations informs every aspect of your security program. Consider IPSO the next evolution in a transformation from traditional SecOps to a highly collaborative and flexible organization that spreads TI across functions to protect against, detect and respond to threats. By combining people, processes, and technology, IPSO can deliver on the promise of a stronger and more agile security organization.
The challenges facing security teams today are no secret:
- Teams struggle to collect, prioritize, and act-on high-fidelity threat intelligence with a consistent and centralized approach.
- Having enough skilled staff on hand to address the volume and speed at which vulnerabilities emerge has become one of the biggest challenges in the security industry.
- Alerts are overwhelming security teams to the point where some alerts may get missed completely.
Threat intelligence management is a starting point to address these problems. Building a centralized threat library can act as the system of record for relevant, documented threats and provide your organization with a holistic view of the threat landscape in one place, supporting faster decision-making and more efficient operations. From this, your defenders will have the information they need to better identify, detect and respond to attacks.
Using a Threat Intelligence Platform (TIP) as your threat library will bring additional capabilities to the table as it can offer access to real-time feeds, machine learning, and valuable analytics to help refine and improve your TI data. The ThreatConnect platform analyzes and makes intelligence actionable, which helps the TI Ops team be more agile and effective.
Infusing threat intelligence into an alert triage program empowers analysts to quickly cross-check alert data with current sources of threat intelligence to get the most current information and act quickly on the most meaningful threats. When using a single source of high-fidelity threat intelligence from a unified threat library to fuel the security technology stack, including firewalls, Endpoint Detection & Response (EDR), Security Access Service Edge/Security Service Edge (SASE/SSE), Security Information and Event Management (SIEM), etc., you get better detections, a reduction in false positives, the ability to link related alerts across tools into a single incident and better alert prioritization which makes organizations more effective and efficient.
Considering the unparalleled growth of vulnerabilities in recent years, it’s easy to see how threat and vulnerability intelligence could be leveraged to create a clear prioritization. Intelligence-powered security operations can evaluate which vulnerabilities are currently being employed by attackers and what’s up next by tracking cybercriminal chatter. Take this a step further and consider how cyber risk quantification could rank vulnerabilities by their potential financial impact to the organization and show clear return on investment for your vulnerability management program. With ThreatConnect RQ, you can focus on remediating the most important unpatched CVEs in the applications and systems that represent the highest financial risk to your organization.
Want to learn more about how threat intelligence and risk quantification can improve your approach to remediation? View this Vulnerability Enrichment webinar.
These are clear examples of how intelligence-powered security operations address some of today’s top cybersecurity challenges, but this is just a taste. Read our white paper: Smarter Security and Maximum Impact from Intelligence-Powered Security Operations for a full exploration of the case for IPSO, how it elevates security operations and puts TI Ops at the core of successful security programs.
