Posted
The Latest on ProxyNotShell and How To Respond If You’re Impacted
Word is spreading fast about two of the newest zero-day (0-day) vulnerabilities targeting Microsoft Exchange servers, now referred to as “ProxyNotShell” – and how their initial mitigations fell short of expectations. Given the evidence that these vulnerabilities are already being exploited to mount attacks we wanted to share an overview of the situation, links to resources for more information and how to respond to this threat. We’ll also explain how the ThreatConnect Platform, along with vulnerability threat intelligence, can aid efforts to track CVEs, as well as the details on severity and potential impact on an organization.
What’s ProxyNotShell?
Two 0-day vulnerabilities were identified in Microsoft Exchange Servers 2013, 2016 and 2019 in August 2022 by Vietnamese cybersecurity company GTSC.
- CVE-2022-41040 – a Server-Side Request Forgery (SSRF) vulnerability
- CVE-2022-41082 – which allows for remote code execution (RCE) when PowerShell is accessible to the attacker
Attackers are using these vulnerabilities – either separately or chained together – to gain access to users’ systems. And while authenticated user access is needed to exploit the vulnerabilities, administrator credentials are not necessary.
GTSC worked with the Zero Day Initiative to get the vulnerabilities published and promote them with Microsoft for fast action. However, security researcher Jang has already demonstrated that the mitigations provided by Microsoft can be successfully bypassed, without much effort, to continue to exploit these vulnerabilities.
Who is Impacted by ProxyNotShell?
According to Microsoft, Exchange Online customers do not need to take any action and are protected by detections and mitigations that Microsoft has put in place. However, on-premises and hybrid configurations (i.e. customers running Outlook Web Applications) are at risk. If your organization is affected, and until a patch has been deployed, it’s important to focus on detecting and tracking any attacks against your organization, as well as sharing information with the security community and trusted partners.
What Can You Do If You’re Impacted by ProxyNotShell?
Until your organization has remediated these vulnerabilities, your security team will need to be on the lookout for indications that your environments have been compromised so that they can respond quickly to cut off any lateral movement and take mitigation steps.
How to Detect
- GTSC provided this PowerShell Command so organizations can check if their Exchange Servers have already been compromised: Get-ChildItem -Recurse -Path <Path_IIS_Logs> -Filter “*.log” | Select-String -Pattern ‘powershell.*Autodiscover.json.*@.*200
- Microsoft also offered advice on how to check their own tools in the Detection section of their security blog
How to Mitigate
- Microsoft offers options for Mitigation in their security blog. If you already implemented the initial guidance, please note that it was updated on 10/2 with a recommendation that “Exchange Server customers disable remote PowerShell access for non-admin users in your organization.”
Information Sharing – Spread the word!
As we mentioned above, when attacks are ongoing it’s critical to spread the word throughout the industry as threats are identified. Some key ways to share information are through ISACs you are part of, trusted partners and communities, and if you are a ThreatConnect customer, with the community of global TC users.
How Can ThreatConnect Help?
The ThreatConnect Platform aggregates and normalizes all your intelligence sources into a centralized threat library, enriching it with real-time insights from the global ThreatConnect community, allowing you to analyze, prioritize, and take action against threat actors leveraging 0-day vulnerabilities like ProxyNotShell. The vulnerability enrichment capabilities of the platform can track threat actor groups to understand their infrastructure and tactics, pull in relevant vulnerability data, prioritize by actively exploitable vulnerabilities and share reports with stakeholders. Using Automation Playbooks you can drive fast, automated responses if you detect evidence of an exploit being used or an attacker inside your environment.
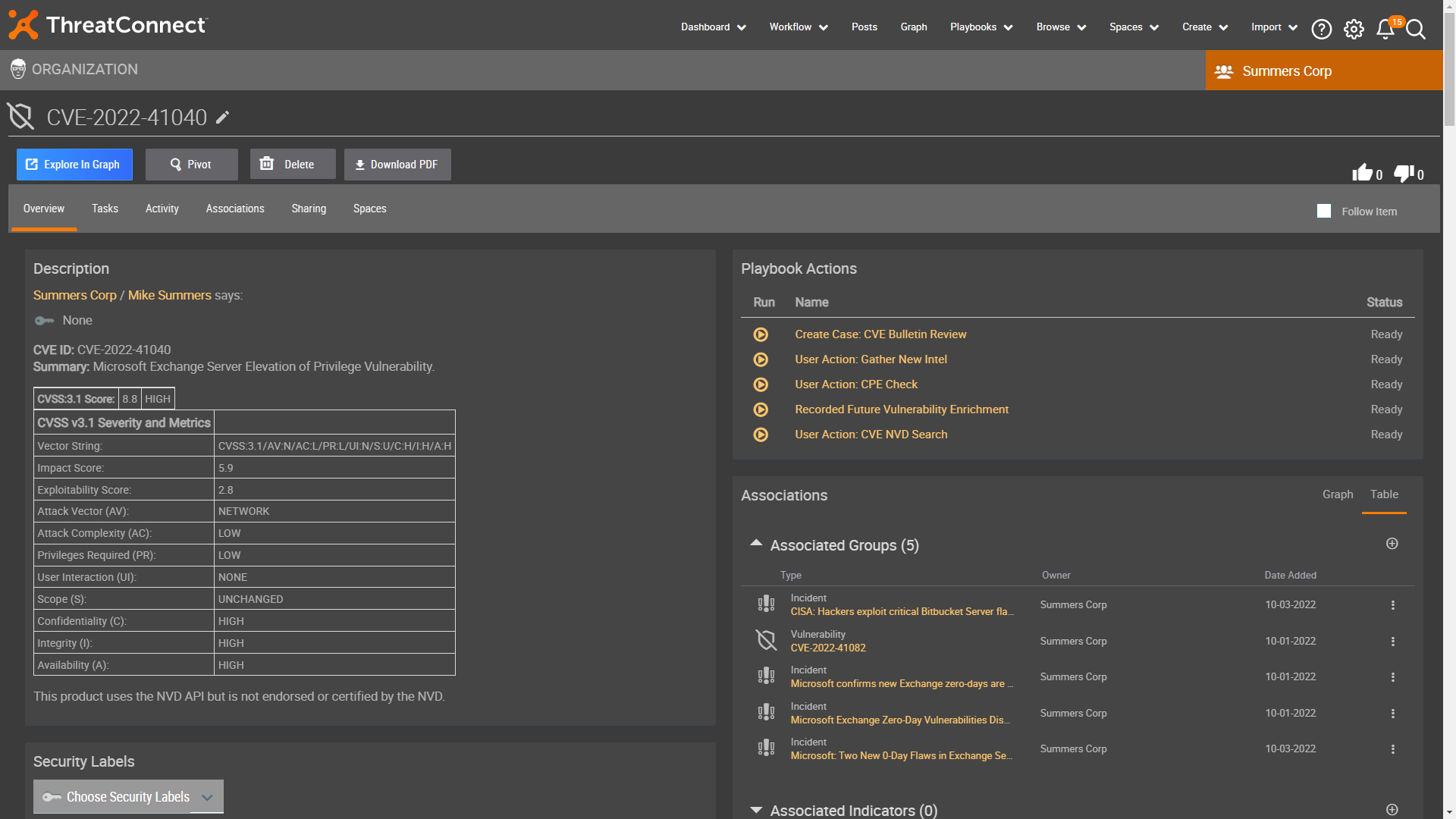
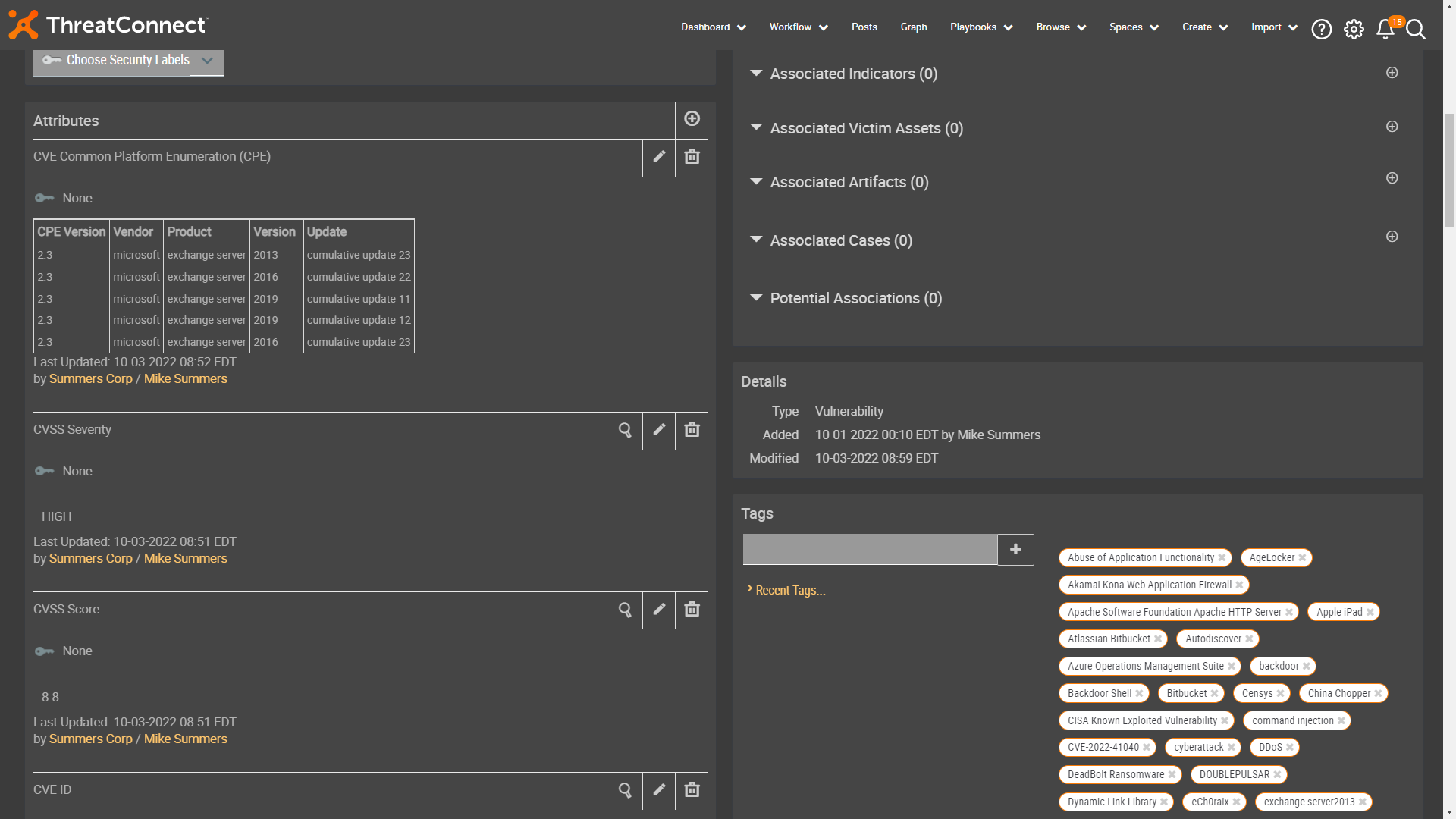
With a CVE details view (see examples below) you can quickly review the information about Criticality, Severity, Score and the Metrics matrix. The Matrix helps you understand the overall severity and impact a vulnerability may have on your organization from references that have been associated with the CVE pulled in from the National Vulnerability Database. You will also clearly see information in the Attributes section on the Impacted Products and Latest Updates.
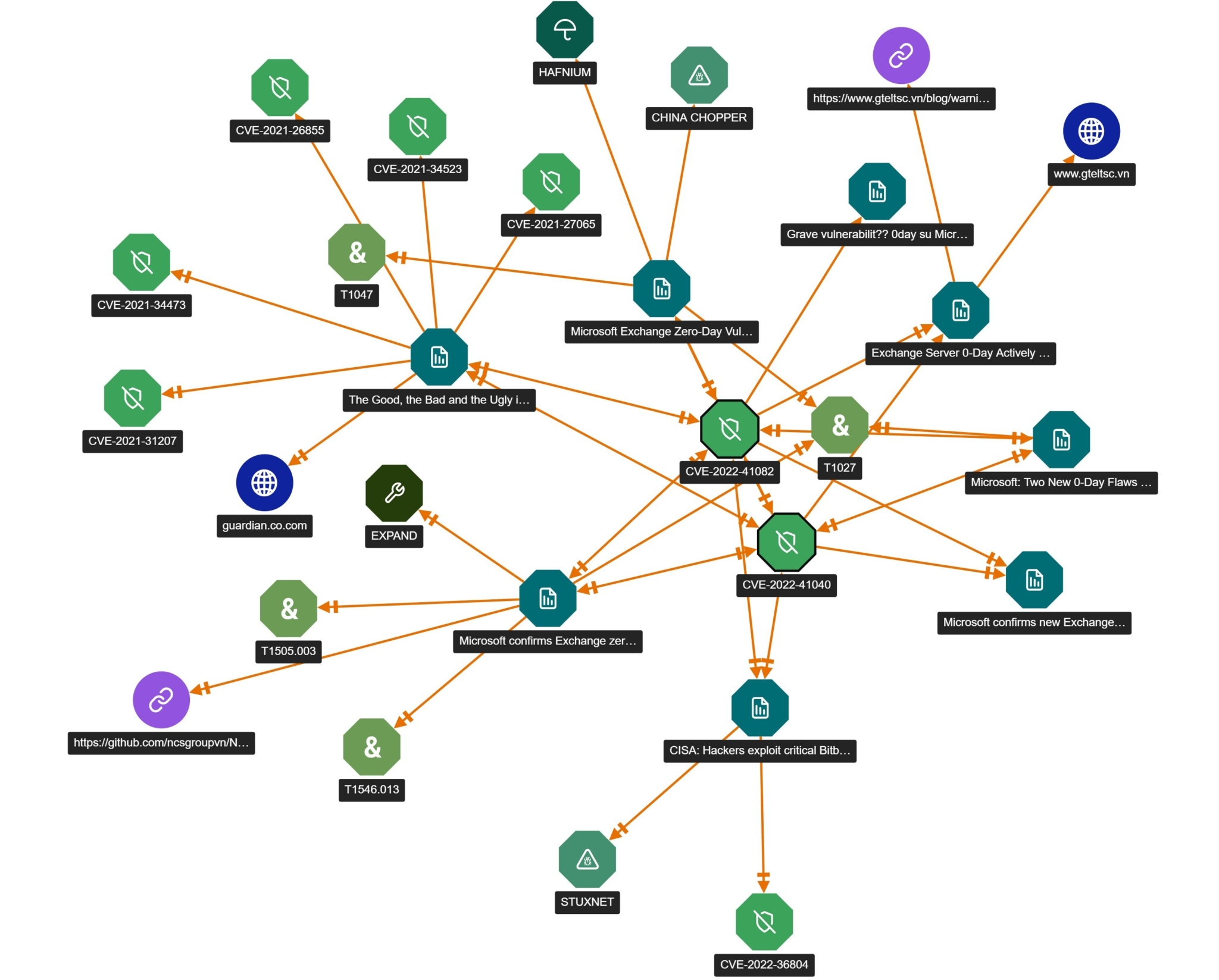
Also within the vulnerability record, there is an opportunity to view all associated intelligence which can include related vulnerabilities, reports, signatures, indicators and Tactics, Techniques, and Procedures (TTPs). This helps provide critical information and context without leaving the platform and enables an analyst to easily find additional intelligence. This can also be displayed visually in Threat Graph (see below).
Learn More
See a demonstration of the ThreatConnect CVE Enrichment capability in this webinar.
If you are a current ThreatConnect customer who’d like to know more about how we can help you optimize your instance around vulnerability enrichment, reach out to your customer success manager.
If you are not a current customer, reach out to us at sales@threatconnect.com to see how we can help you use ThreatConnect to track, prioritize and get the detail you need on the most actively exploitable vulnerabilities.
Thanks to Mike Summers, Sales Engineer, who contributed content for this post.