
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.

5 Powerful Splunk Queries to Enhance Your Team
Maximizing your Splunk Investment with Polarity In the ever-evolving landscape of cybersecurity threats, organizations need to be prepared to investigate and respond to incidents immediately, and with confidence. Splunk plays a crucial role in this process for many organizations. Many teams need to respond to more attacks than ever before, often with less time and […]

Why Threat Intel is Critical for Supply Chain Security
In today’s interconnected world, organizations rely heavily on a complex network of suppliers and vendors critical to their operations. They supply software used across an enterprise and provide services that may be part of essential business processes. While these partnerships offer numerous benefits, they can also introduce significant cyber risks that can impact the security […]
Applying the Diamond Model for Threat Intelligence to the Star Wars’ Battle of Yavin
Alternate titles: “Diamonds are a Sith’s best friend” “I used to Bullseye Womp Rats in my t-shirt back home.” “That’s no Shamoon…it’s a space station attack! Those of you who know ThreatConnect well are aware that we’re Star Wars fans. A recent example and awesome webinar if you haven’t seen it – The Need for […]
Day in the Life of a TI Analyst Part 2: Dashing Through Dashboards
Welcome back, Class! This is ThreatConnect 101 for CTI analysts featuring me…a former analyst and all-around nerd. If you haven’t seen the first post in this series, I highly recommend checking that out before diving into this one. Check out ThreatConnect Query Language (TQL) for People Who Don’t Code. Part 1 lays the foundation that we’ll […]
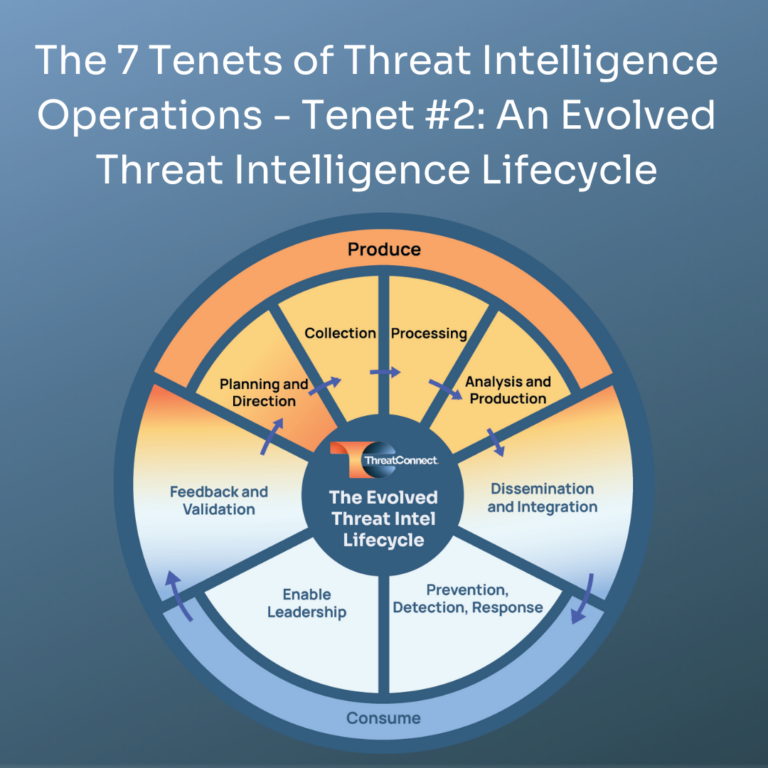
The 7 Tenets of Threat Intelligence Operations – Tenet #2: Requires an Evolved Threat Intelligence Lifecycle
In the first blog of this series, I took a 30,000-foot view of the seven tenets of TI Ops defined in the Dawn of Threat Intelligence Operations paper. In this edition we are going to dig into Tenet #2 – Requires an Evolved Threat Intelligence Lifecycle, one that emphasizes the planning and requirements and the […]

Evolution of the Threat Intelligence Products and Services Market – Our Take on The Latest Gartner® Market Guide
Gartner recently released the latest version of their 2023 Market Guide for Security Threat Intelligence Products and Services. We’re honored to be named a Representative Vendor, but equally excited by the insights and advice offered in the Gartner report. I find the Key Findings and Recommendations to be a great summary of the challenges we […]

How To Prepare For A Threat Intel Ops Platform Project
We asked some of the Senior Leaders at ThreatConnect, whose teams’ spend a lot of time with enterprises, to give their insights on how an organization can prepare for a TI Ops Platform project. We think these insights will give some ‘hacks’ to be successful in selecting, gaining support (e.g., budget and resources), and delivering […]

Maturing Cyber Processes: Enhancing SOP Reliability
Current State of SOPs: Do as we say, not as we do If we look around our corporate environment, many employees within the enterprise can be classified as “knowledge workers.” Those employees are trusted to think, analyze, and apply scrutiny to information such that the best decions can be made, increasing the probability of a […]

Introducing Polarity’s Chrome Extension
We’re thrilled to announce our new Polarity Chrome Extension, available for anyone with access to Polarity using a Chrome based browser. Now, get the power of searching in Polarity as you work in Chrome. To get started: 1. Search for “Polarity” in the Chrome Extension Store, or visit the direct link here. 2. Click “Add […]
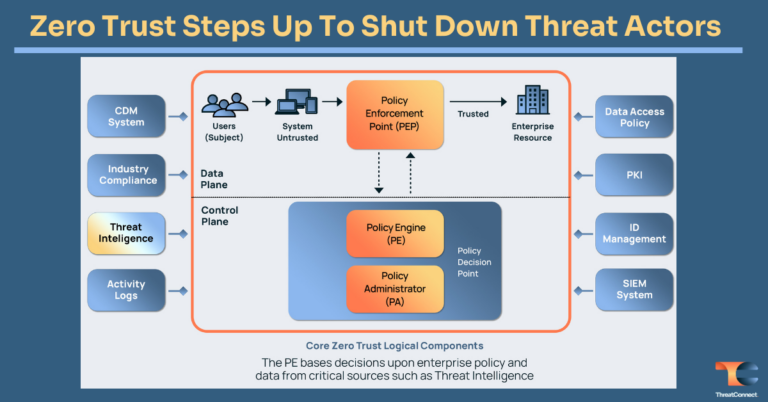
Zero Trust Steps Up To Shut Down Threat Actors
Over a decade ago, Forrester Research introduced the concept of zero trust. Today, zero trust is considered one of the leading frameworks to guide information and security architects in the design of robust and resilient information security architectures. This is a very important aspect of zero trust – it’s a framework that influences security architectures […]

Announcing the Polarity Community Contributor of the Quarter, April 2023
We here at Polarity are excited to bring back our Contributor of the Quarter award for 2023 by announcing this quarter’s contributor, John Winchester of Secrutiny! John and team over at Secrutiny have been doing some fantastic things, and not just with Polarity. If you aren’t familiar with Secrutiny, they are an MSSP that believes cybersecurity doesn’t have […]
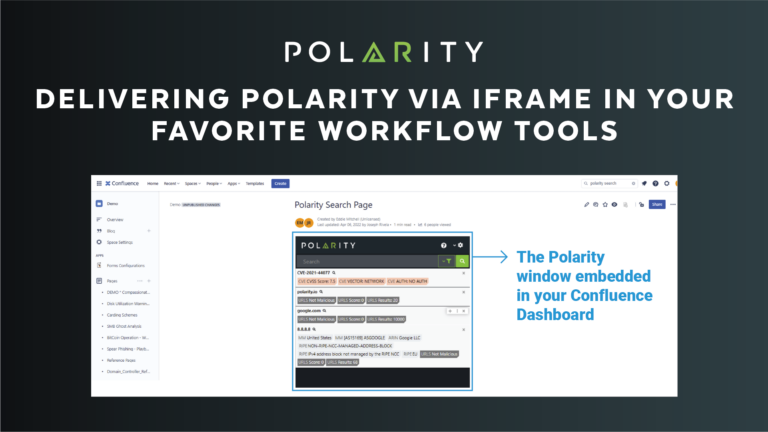
Delivering Polarity via iFrame in your Favorite Workflow Tools
In March of 2023 Polarity officially released one of our new features – Polarity Web Search. While we are still pushing the boundaries of human driven analysis – and consolidating enterprise knowledge (stuff you know) and data (stuff you have) into one unified view by way of our Polarity Desktop Client – we sought to deliver […]
