Posted
Part one of this blog series begins with a simple step-by-step walkthrough of how to craft and save a ThreatConnect Query Language (TQL) query without writing out, or even fully understanding, all of the TQL options. Before we jump into the steps, let’s talk a little about TQL. What is it? Why would I want to use it? How does TQL help?
One of the key tools in an analyst or researcher’s toolbelt is the ability to do a highly targeted search. I’ve personally seen many new analysts succeed or fail based in part on whether they could draft a Google query that brought them the results they needed. In ThreatConnect, TQL is somewhat like a hyper-focused Google query. By combining different terms and data types into a TQL query, you can filter the data in ThreatConnect down to very granular levels so you can weed out the noise and focus on the pieces of information that are relevant to your investigation. TQL is available today in Playbooks as well as on the Platform’s Browse screen. In this blog, we’re going to be focusing on using TQL in the Browse screen. (For additional background and information about TQL, please see this knowledge base article.)
Step 1 – Go to the Browse Screen
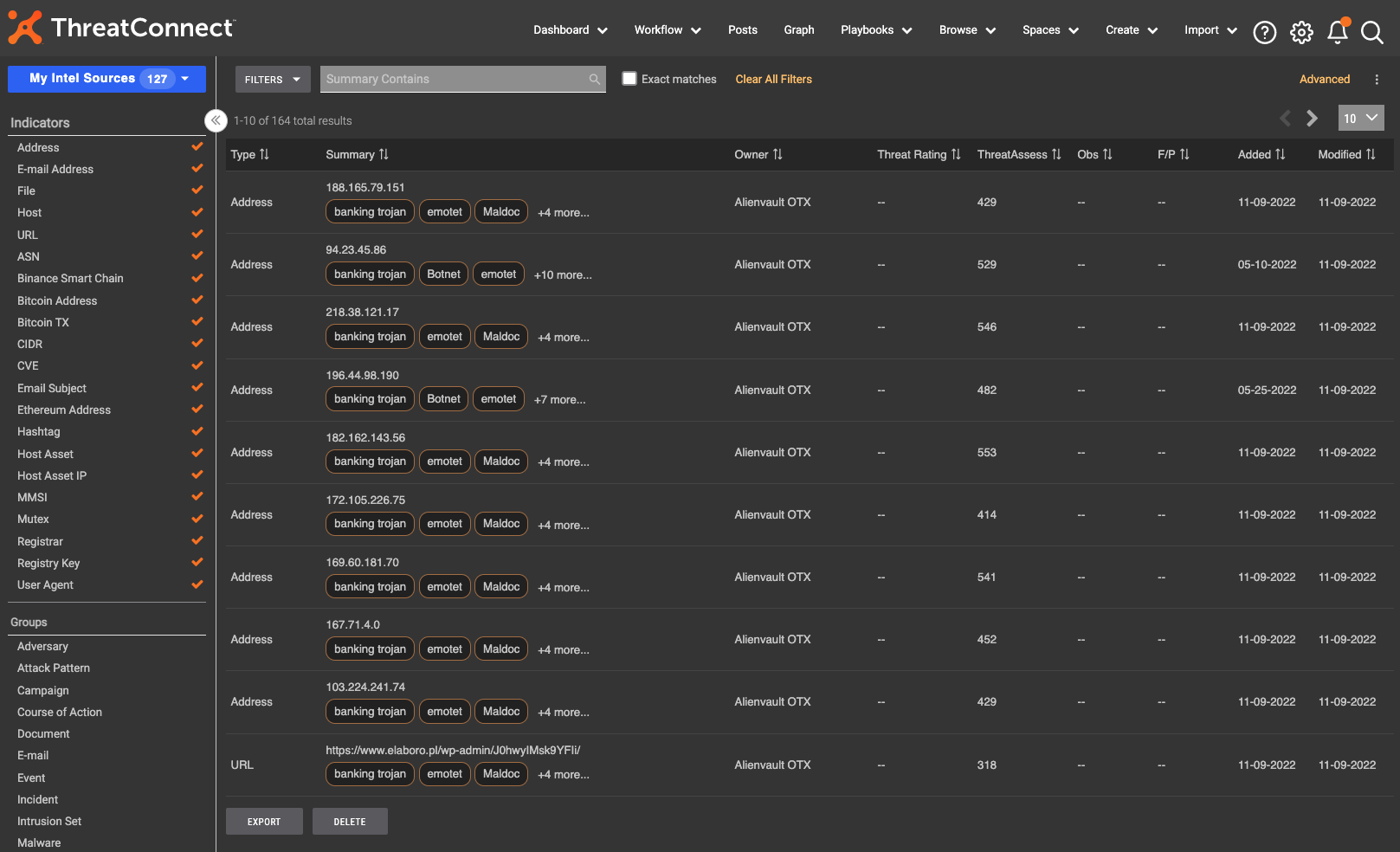
Why the Browse Screen? Well, the Browse screen provides filtering functionality that isn’t available in the traditional Search feature in ThreatConnect. It also has a couple of handy buttons that you can use to get ThreatConnect to do some of the work for you.

Step 2 – Click to view Filters
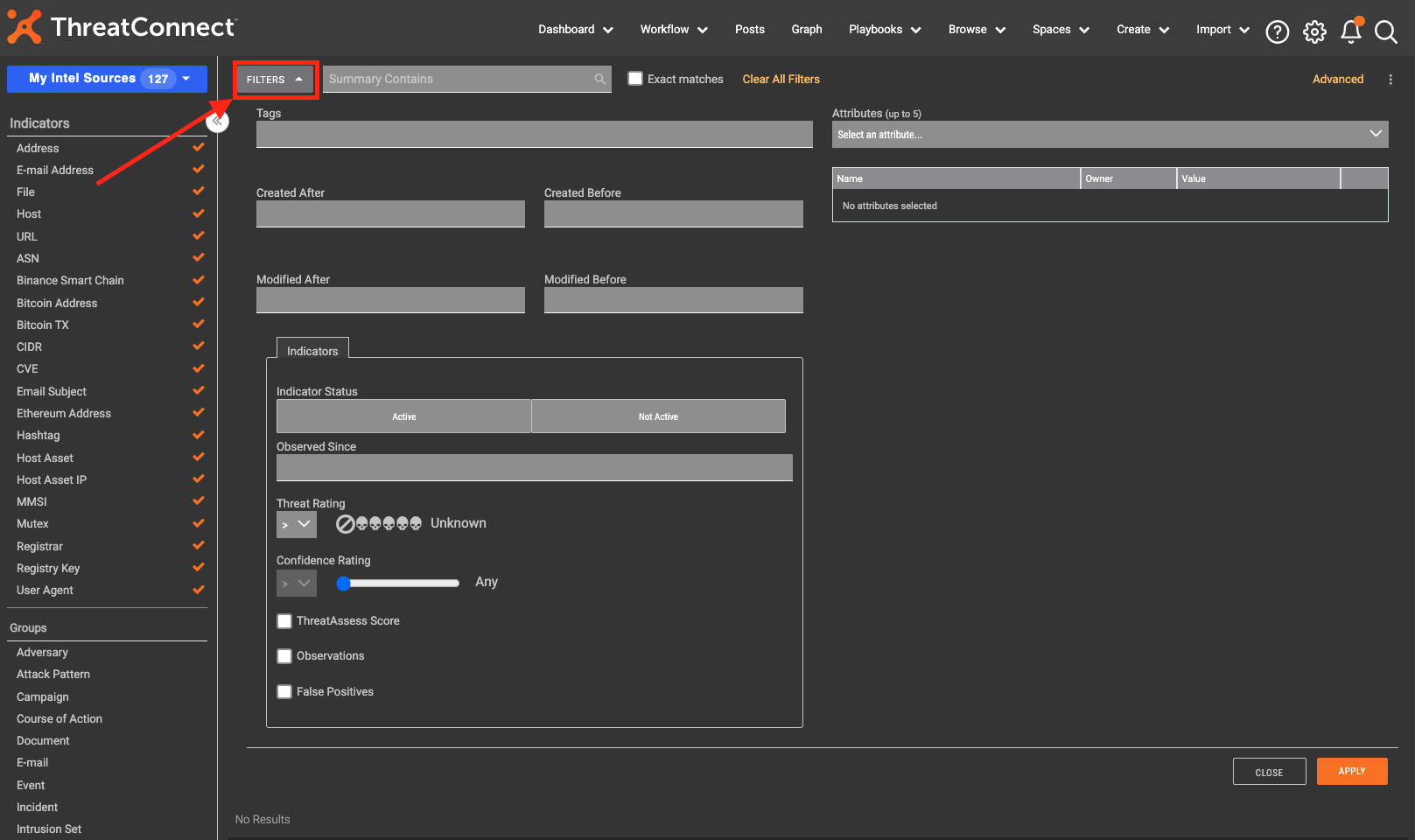 Filters give you the option to start targeting particular pieces of information. For example, you can leverage the filters to query for files that have certain tags or were created at particular times. You can even query while investigating a certain set of activities based on attributes like import hash (imphash).
Filters give you the option to start targeting particular pieces of information. For example, you can leverage the filters to query for files that have certain tags or were created at particular times. You can even query while investigating a certain set of activities based on attributes like import hash (imphash).
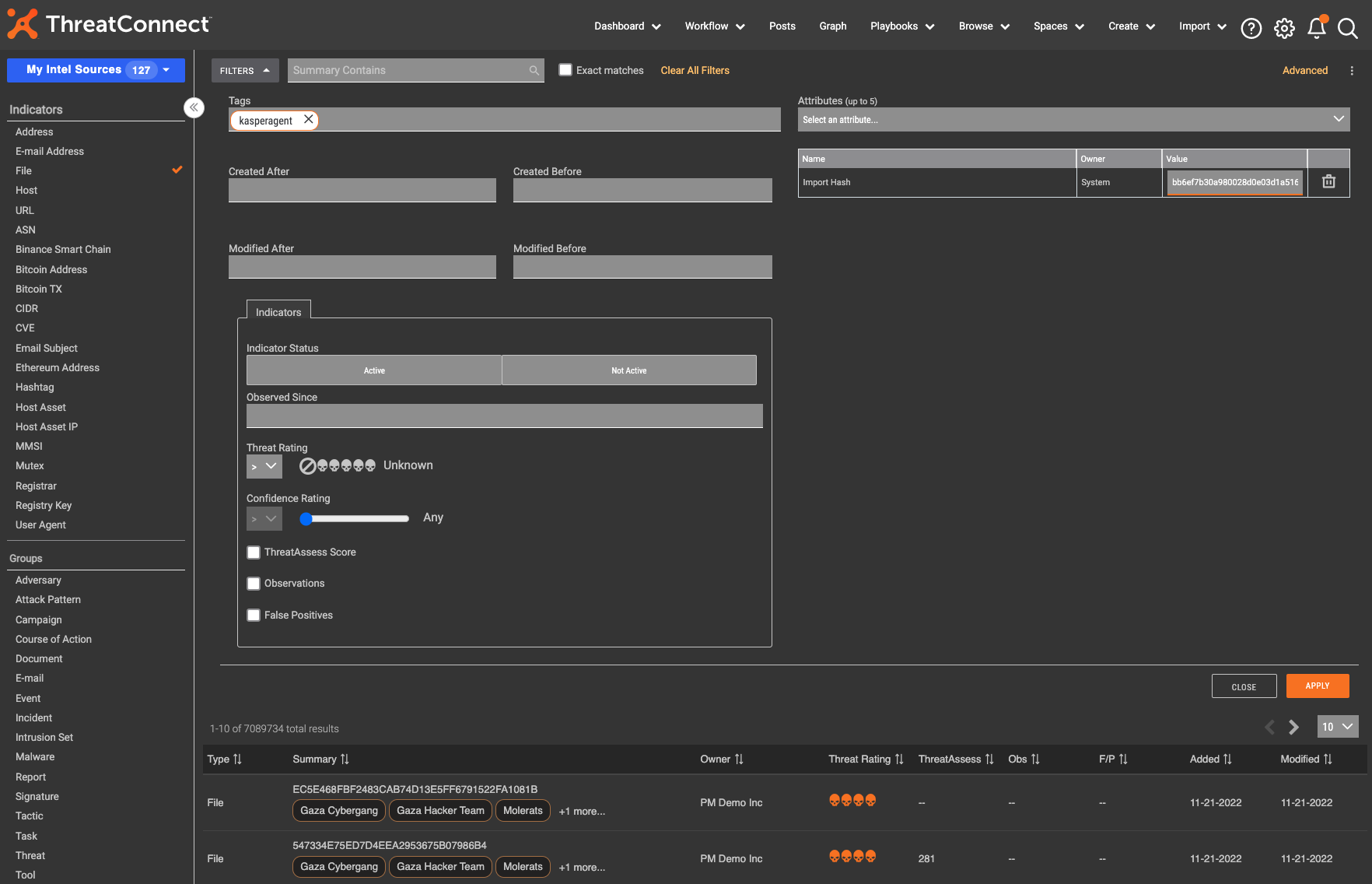
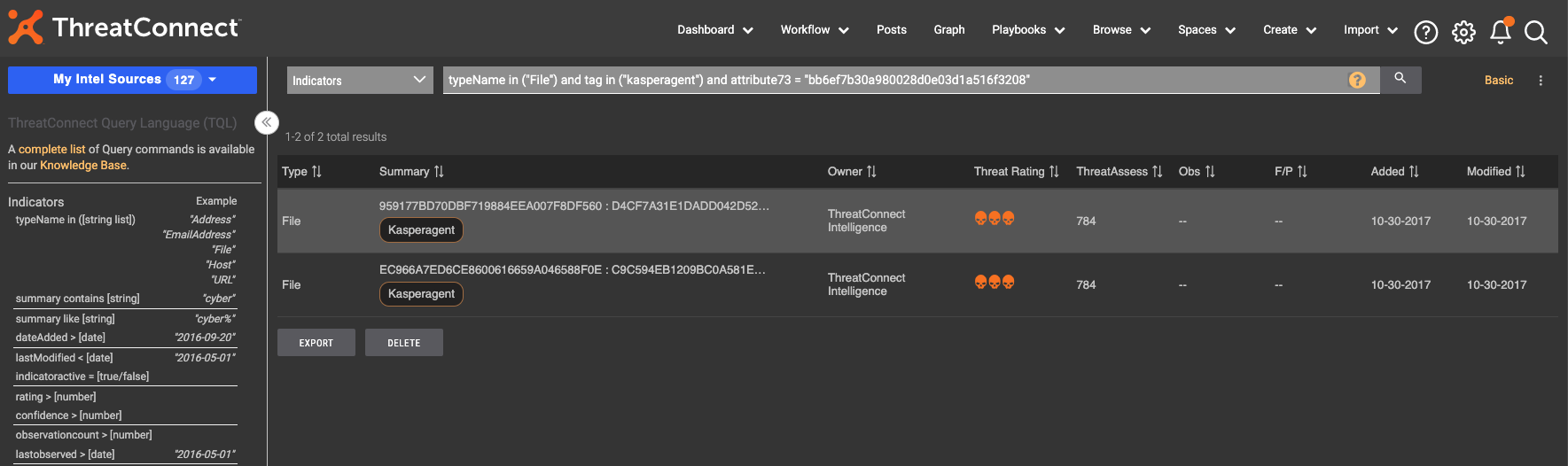
Enter any filters you want. This may be a combination of tags and attributes or a series of tags with specific threat ratings and confidence levels. In the example above, you’ll see on the left, only the File indicator type is selected. Additionally, the user filters by the tag “kasperagent” and the imphash attribute with a value of “bb6ef7b30a980028d0e03d1a516f3208”. These filters search for file indicators with the identified tag and the imphash attribute value and help analysts zero in on the information that they need rather than having to wade through the massive amounts of data available to them.
Note: Make sure you hit “Apply” in the bottom right corner before moving on to the next step.
This next part is kind of like magic.

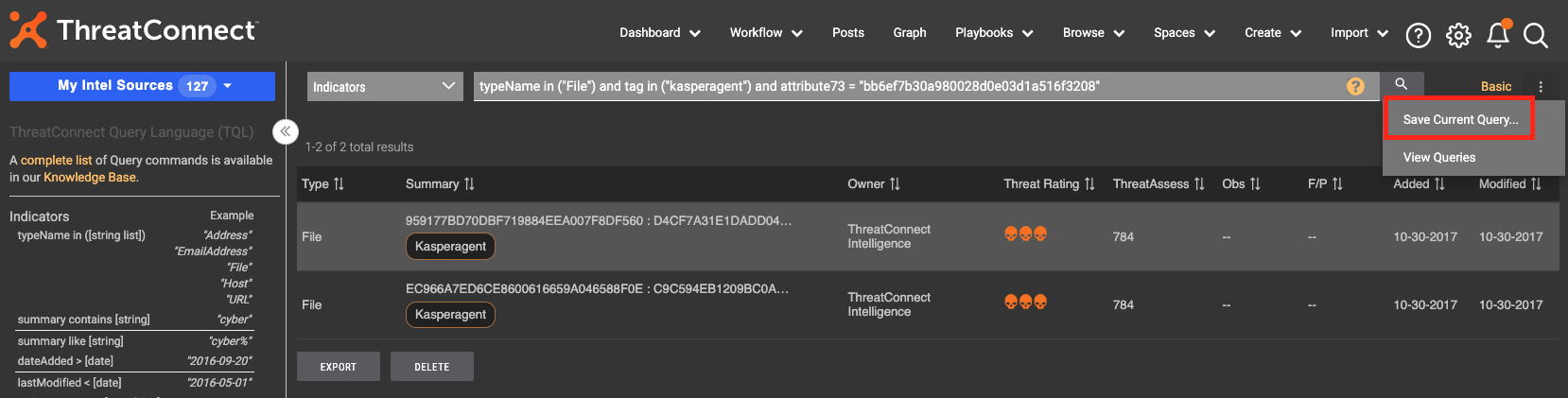
Step 3: Click “Advanced”
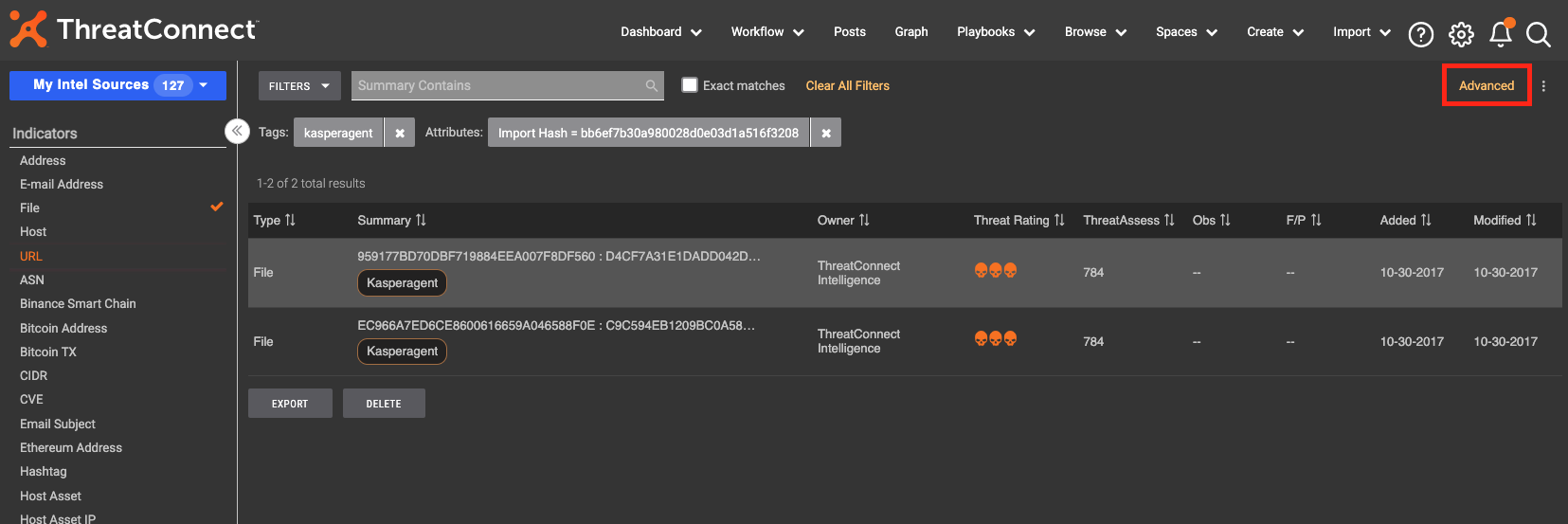
The Advanced button on the Browse screen automatically converts the filters into a TQL query that can be used in other areas of the Platform.
From there, you can click the kabob menu on the right to save the query for use in Dashboard cards. (Soon available for use in Reporting and other areas of ThreatConnect.)
By leveraging the Advanced button, you are able to have ThreatConnect build a TQL query for you. You can then add additional parameters as needed to filter your search further. This lets you drill down into the data available in ThreatConnect and bring items of interest to the surface faster. Then, with the Save functionality mentioned above, you can capture that query for later use so that you can use it again and again without having to go through the process of writing a new query each time you want to look at a given set of information. All in all, by leveraging these steps to capture a TQL query, users can identify relevant information faster so they spend more time doing analysis and less time searching through data points.
Next Up:
In our next post in this series, we’ll be diving into building a dashboard leveraging some of the TQL queries you can build in the Browse screen and highlighting how Dashboards can help bring relevant information to the surface so you spend more time doing analysis and less time poking about looking for something to research. Read the Day in the Life of a TI Analyst Part 2: Dashing Through Dashboards.
Who am I:
Hi, I’m Marika. I’m currently the Senior Strategic Product Manager for Threat Intelligence at ThreatConnect, but before moving into that position (and completely changing careers), I spent 10 years in threat intelligence analyst and threat researcher roles. I am a complete nerd at heart and love nothing more than digging into seemingly disparate incidents and finding similarities leading to new understandings of the threats facing an organization. That said, I am not a technical analyst. I do not write code, and I only made it halfway through my Python book. This series is for people like me. People who are more strategic threat intelligence analysts who look at behaviors and trends in activity and make technical concepts easier to understand for non-technical people.
