Posted
Chief Information Security Officers (CISOs) serve a critical role in protecting their business from internal and external threats. They need to design and implement the right resources to mitigate growing digital security risks and maintain regulatory compliance. This requires an understanding of the current and future security risks to business operations that could hinder the organization from reaching corporate objectives.
Traditionally, these risks were assessed with Red-Amber-Green heat maps but with the growing impact of cyber attacks and the forces of adversaries, CISOs need more information to stay ahead. Many are looking to quantify cyber risks in order to proactively make decisions but whilst there are many drivers accelerating CRQ and the benefits are now widely accepted – some CISOs have not started using this approach just yet.
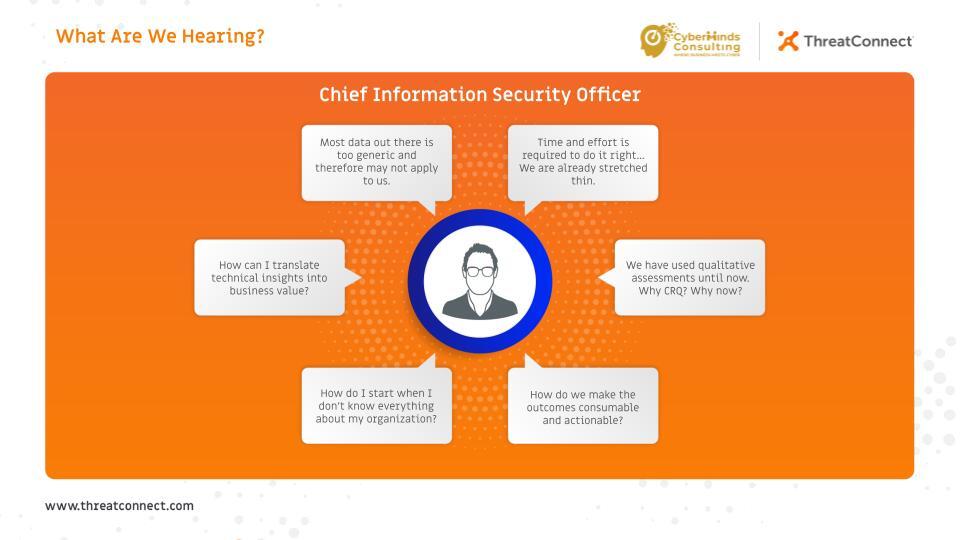
In this blog, we will explore some of the concerns holding CISOs back and also provide recommendations to overcome these barriers. Here’s what we are hearing:
“We have used qualitative assessments until now. Why CRQ? Why now?”
Times are changing. CISOs have many different priorities to juggle which makes prioritization a challenge. Traditional qualitative assessments don’t give you the ability to determine priorities, analyze cost/benefit outcomes or calculate ROI. You need to use a scientific data-driven approach that CRQ provides, in order to make those informed objective decisions.
Shocking as it may sound, when it comes to qualitative versus quantitative risk, it’s not a battle. You don’t go from qualitative to quantitative – the two work together. Qualitative has its own benefits so we encourage you to take a hybrid approach. Qualitative assessments give you an overarching picture, then the quantitative assessments add further detail, depth and context. Take baby steps to transition towards quantitative assessments by starting with your key risks, and demonstrating the value in the process.
“How can I translate technical insights into business value?”
There’s usually some kind of pushback, either due to a lack of understanding or because leaders (especially more technically focused ones) are not always comfortable talking in the language of business. And without a clear understanding of the business, how can we expect those leaders to talk in business terms – especially if they have not reported in that way before?
In a factory, if your staff is making pies and one drops on the floor, chances are it won’t be the reason your business crumbles. If there is a glitch on the production line and it hinders the volume you can produce – it’s easy to calculate loss because you can picture it. Cyber security is at the stage where we are starting to gain a better idea (though still a little subjective) of loss.
In the cyber world, CRQ helps us understand the impact of events and incidents. It supports these challenging conversations in an objective way – one which we can all understand. And if we know what the outcome of a ransomware attack would be or a successful phishing exercise, we can put measures in place to reduce the likelihood of that occurring.
“We follow internationally recognized control frameworks so we already know which controls we need and why. What difference can CRQ make?”
When you look at cyber risks, you can’t look at them in a linear way. Having a control in place doesn’t make you secure because they’re not static. You have to look at it from an attack path perspective and look at controls through different stages. You might have a great control that mitigates a certain kind of tactic early on in an attack phase, but it may be terrible later on. Therefore you have to look at controls against the tactics that are available to the attacker in the totality of the attack chain, otherwise, you’re just getting a really narrow view which may give you false overconfidence.
But also, you don’t just look at controls in isolation. To gain maximum aggregated risk reduction, you must look at the impact of the controls across multiple business processes or applications. You may even find that a control mitigates multiple threats (though they may not have equal impacts) or multiple controls mitigate the same threat. That’s how you would prioritize.
“How do I start when I don’t know everything about my organization?”
Truth is, you don’t have to know everything about the business to be able to start the journey. It’s imperative for our business for the conversation to start now. You can start very small, focusing on your crown jewels – the application that matters most to the business. The information may be imperfect or incomplete initially but you can always add to it to build it out further. The important thing is to start the conversations (and start them early)!
“Most data out there is too generic and therefore may not apply to us.”
Risk quantification is about probability, not certainty. We use it to predict a range for expected loss based on likelihood and impact based on real data (and experience).
One CISO from a manufacturing firm in Germany told me, he would rather provide management with a traditional heat map than estimate cyber risks in financial terms and be way off. I get it – expectation setting is important but these calculations shouldn’t be about guessing numbers. There are a ton of data sources you can leverage to improve the accuracy of your predictions such as regulatory data, insurance claims, financial data, breach reports as well as a wealth of security and threat intelligence. The more we build on our knowledge of cyber attacks, the more we can improve the accuracy and fine-tune our strategies.
“Time and effort are required to do it right… We are already stretched thin.”
There seems to be a perception in the industry that CRQ is very complex. The quantitative risk models, even the ones promoted by The FAIR Institute, may look highly complicated on paper. No doubt, this may scare people off. This is one of the main inhibitors to the adoption of CRQ, in spite of the known benefits. But this tells us that there is a lack of understanding and expertise in how to make things work.
All good things take time. Initially, it may be a little labor-intensive. You can do it this way if you have the resources to do so, or you could automate the process either through your own home-grown tool or using advanced technology.
In fact, with this objection – the clue is in the title. You have limited time and resources – great, that’s even more reason to use them wisely. CRQ can help you put your attention where it needs to be.
“How do we make the outcomes consumable and actionable?”
You can take the outcomes of CRQ and use them to create short-term and long-term control implementation plans that align with your business priorities. It will help you make more informed and more objective decisions around the value of each option.
For example, you may need to implement controls A and B but only have the budget to implement one of them; CRQ will allow you to determine and compare both options. Control A may be a policy for handling redundancies. Control B may contribute to the current business objectives of you wanting to move all your legacy or modernize your legacy applications into the cloud which will improve customer experience. You may very well wish to do both but if you had to choose one first, Control B is more important in this case.
These are just some of the concerns and objections we’ve been hearing. If you are a CISO and there’s something holding you back from CRQ – let us know. We’d love to hear from you.
To learn more, watch our recent webinar on-demand to hear more about this topic in greater detail, and look out for our next blog which will delve into CRQ challenges we are hearing from CIOs. Follow us on LinkedIn and Twitter for the latest content.