Posted
We are excited to announce that Bayse Intelligence and ThreatConnect have a new strategic partnership, starting with the integration of Bayse Early Alert – Bayse’s phishing intelligence feed.
Phishing-style attacks are not going away
Like many of the most challenging problems in cybersecurity, phishing is a constantly evolving challenge for enterprises of every size. According to CISA, in early 2023, 8 out of 10 organizations assessed had at least one employee fall victim to a phishing attack.
And that’s just within the organization’s control! As we’ve seen most recently in the Okta breach, the compromise of a user’s personal account can impact the organization as well as downstream 3rd parties.
Phishing is truly “borderless” and cross-device. SMS attacks have become a growing attack vector, which is especially challenging for organizations with brands whose reputations are negatively impacted, for example, when customers receive a steady stream of phishing messages.
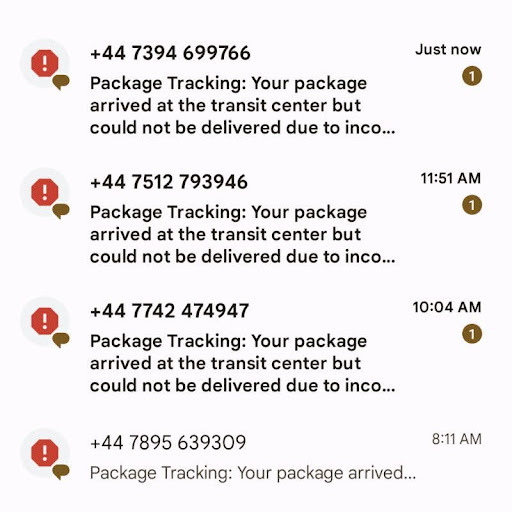
A Recent High-Volume SMS Phishing Attack
The industry reports and statistics reinforce the prevalence and expansion of phishing-style attacks, and because of the increasingly digitally connected ecosystems enterprises rely on these days, it is increasingly important to understand 3rd party and supply chain risks as well.
Last but not least, with phishing-as-a-service options available to threat actors and the availability of generative AI tools, phishing is going to:
- Continue to move downstream to less sophisticated operators
- Increase in volume (both email and SMS attacks)
- Affect more organizations that may have previously been too small and not worth the effort
The Value of Bayse Intelligence Integrated with the ThreatConnect TI Ops Platform
Bayse was built from the ground up by security practitioners who understand the challenges organizations of every size face from a constantly changing threat landscape.
There are several critical differentiators that Bayse provides:
Site Fingerprints Automatically Discover Campaigns
The large majority of phishing attacks leverage templates. Whether those templates are privately owned and developed by one individual/group or sold for use by others (as is the case in common phishing kits), they leave distinct identifiers. Bayse has built a proprietary approach that automatically creates Site Fingerprints for the millions of sites it analyzes monthly. This means that every time a similar site is seen, Bayse automatically associates it with every other site with the same Site Fingerprint (think of it as JA4 for websites). This is especially powerful within ThreatConnect, as it automatically automates indicator grouping for better and faster analysis.
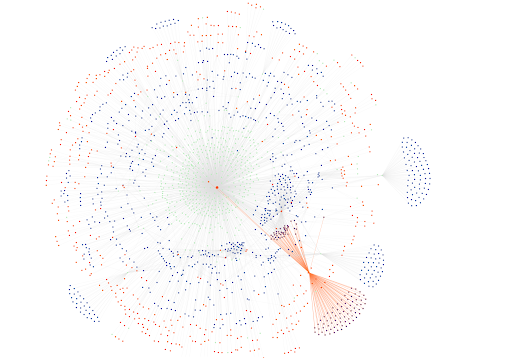
An example of Bayse Intelligence Grouped Indicators Targeting Microsoft Credentials
And since every intelligence feed item is automatically clustered and explained, the tactical value within ThreatConnect is extended even further:
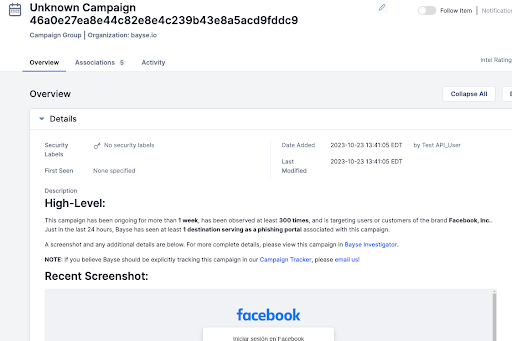
ThreatConnect Detail Page with Bayse Intelligence showing Grouped Campaign Targeting Facebook Users
Automated Credential Collection Extraction
Is there a direct business impact if a user clicks on a phishing link but doesn’t enter information? Perhaps not. However, if they enter information, there could be a large-scale business impact that requires a response (e.g., triage and analyze the end user’s actions).
Whenever possible, Bayse will automatically extract the “next step” that occurs when information is entered into a phishing portal. Often, that next step is a compromised (but legitimate) website that, were an analyst to see it in their logs, would look innocuous.
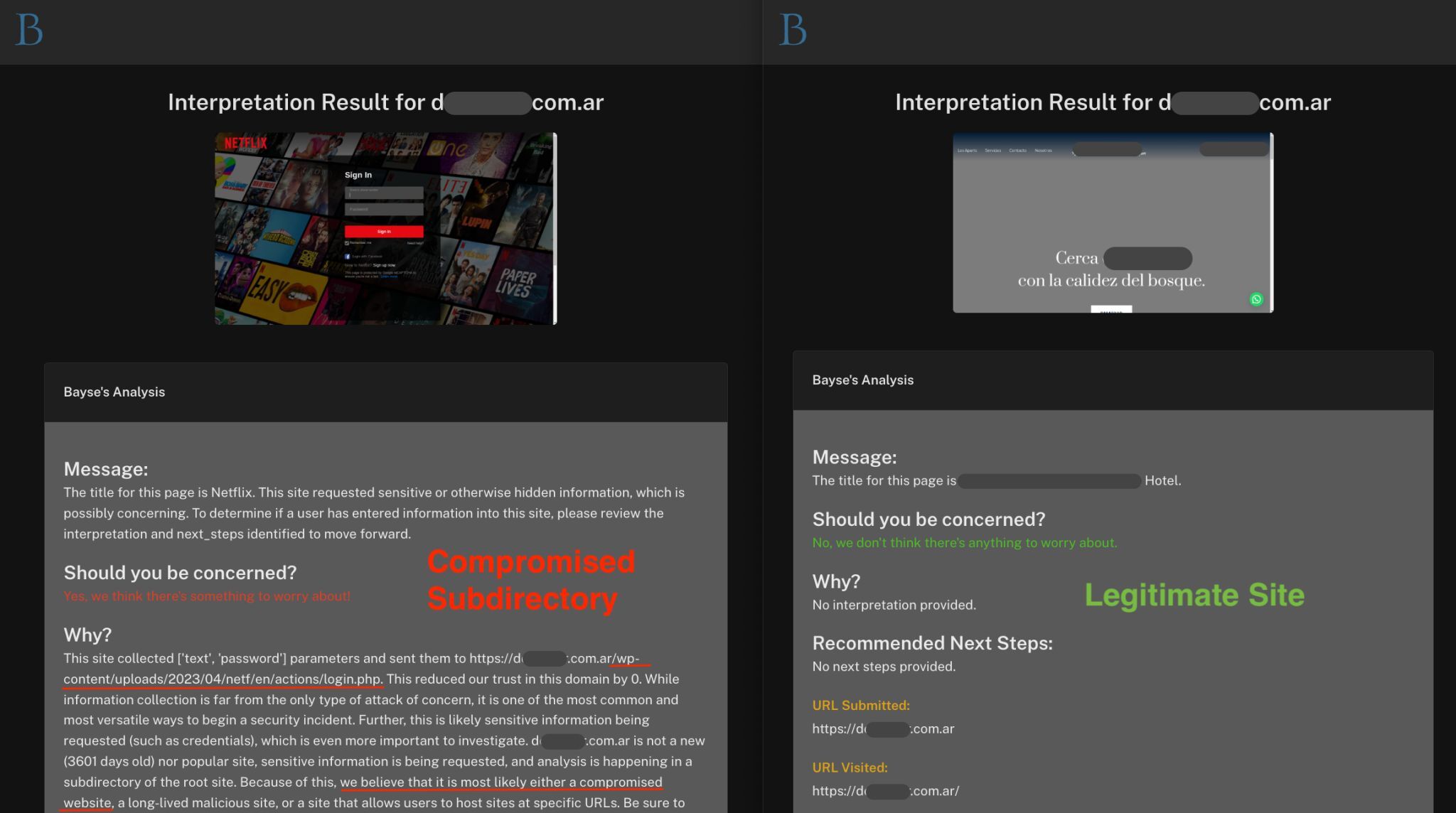
A legitimate, compromised site collecting credentials
This approach saves analysts time and effort when assessing the activities around a phishing attack through:
- activity extraction
- identifying the credential collection activity to connect otherwise distinct-looking attacks
- providing details and context about what may have been stolen by the attacker
- identify sites that don’t appear at scale in any other threat intelligence feed
Highly-Enriched Feed
Every item in the Bayse Early Alert Intelligence feed can contain over a dozen highly enriched pieces of information that will significantly enhance analysts’ ability to automate many investigation and response steps and hunt for missed threats. Some of the most compelling metadata are:
- a full, human-readable description of why a site was identified as phishing (and what to do about it)
- the full URL of where credentials or PII was sent
- screenshot
- domain-to-IP mapping
- TLS certificate information
Easy to Onboard New Brands
Finally, Bayse can start tracking and protecting an organization’s brands in just a few minutes, and as brands change, they can be easily updated.
How to get started
If you’re already a ThreatConnect customer, contact your customer success manager to learn more about Bayse Intelligence or visit the ThreatConnect Marketplace. If you’re not yet a customer, take a tour of the TI Ops Platform or reach out to a ThreatConnect expert to get a customized demo. To learn more about Bayse Intelligence and all of their offerings, please see their products and use cases.
