Posted
2023 was a banner year for ThreatConnect’s Threat Intelligence Operations Platform. The innovative, market-leading features introduced last year allow CTI teams to:
- Align to the Evolved Threat Intel Lifecycle
- Operationalize their threat intelligence in a way that benefits the CTI team and their customers
- Clearly demonstrate the value of the CTI program
So, let’s take a look at what the ThreatConnect TI Ops Platform team delivered in 2023.
January 2023
The next major version of the TI Ops Platform, version 7.0 was launched. It brought threat intelligence platforms (TIPs) into the age of Threat Intelligence Operations with new features like:
- Built-in Reporting
- Automated Enrichment (starting with VirusTotal)
- Our new UI design
We also launched the Automated Threat Library (ATL) as part of our regular updates to CAL™, the AI-powered “brain” of the ThreatConnect TI Ops Platform. CAL ATL covers 60+ definitive sources of open source threat intel and uses CAL’s natural language processing (NLP) to automatically extract indicators and tag relevant details, like MITRE ATT&CK tactics and techniques, and threat actor aliases using our “Rosetta Stone” of threat actors.
April 2023
Version 7.1 delivered enhancements to a variety of features in the platform, for example:
- The ability to execute Playbook automations directly within Threat Graph
- Automated enrichment was expanded with coverage for Shodan
July 2023
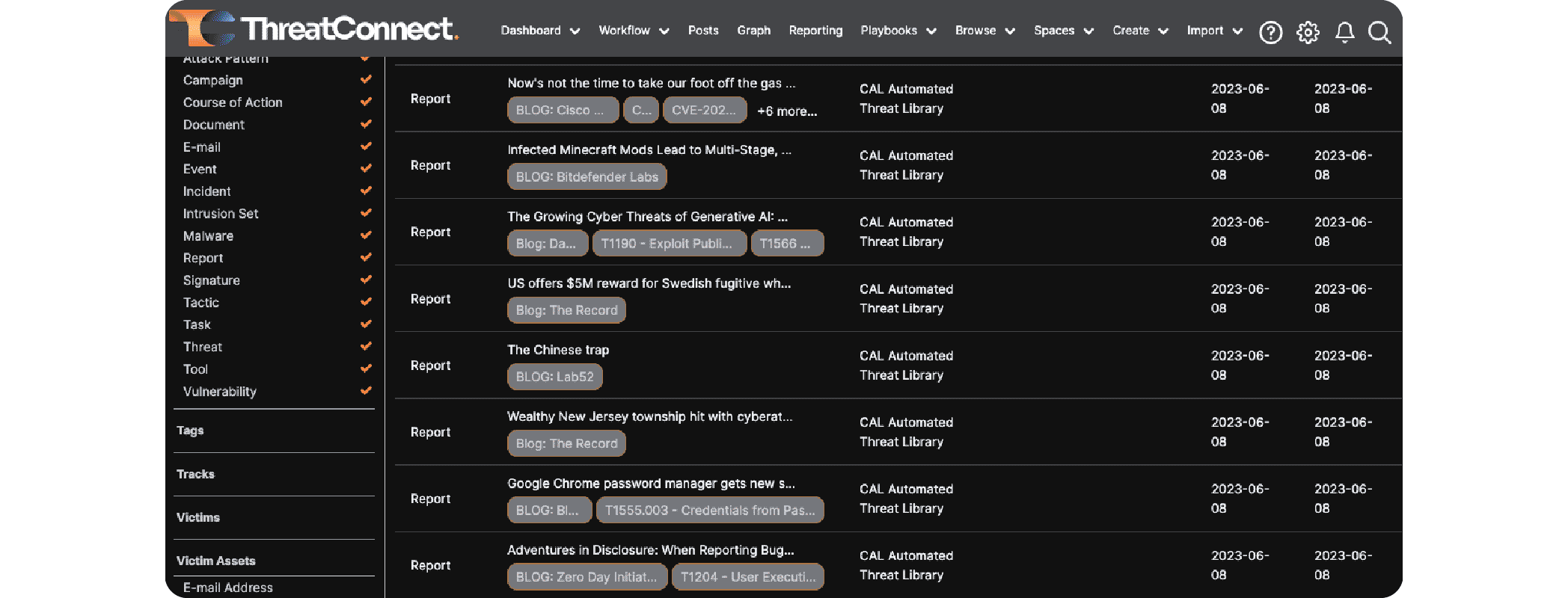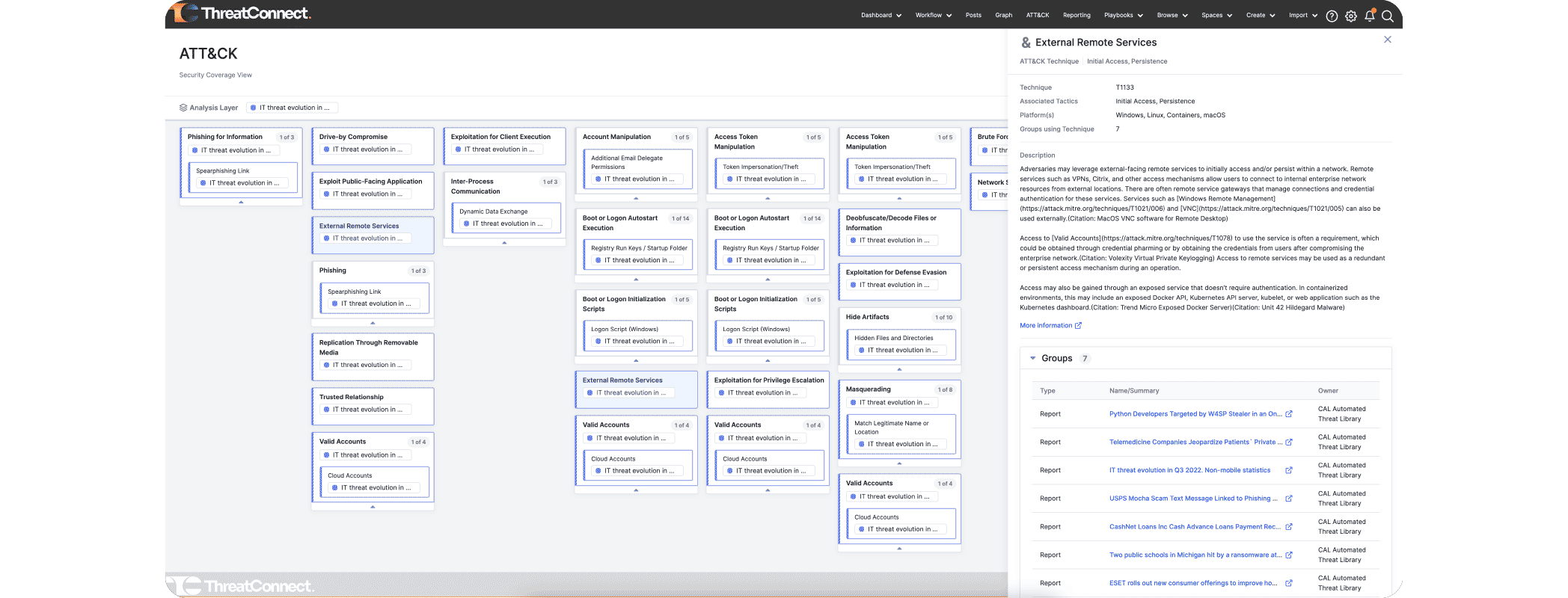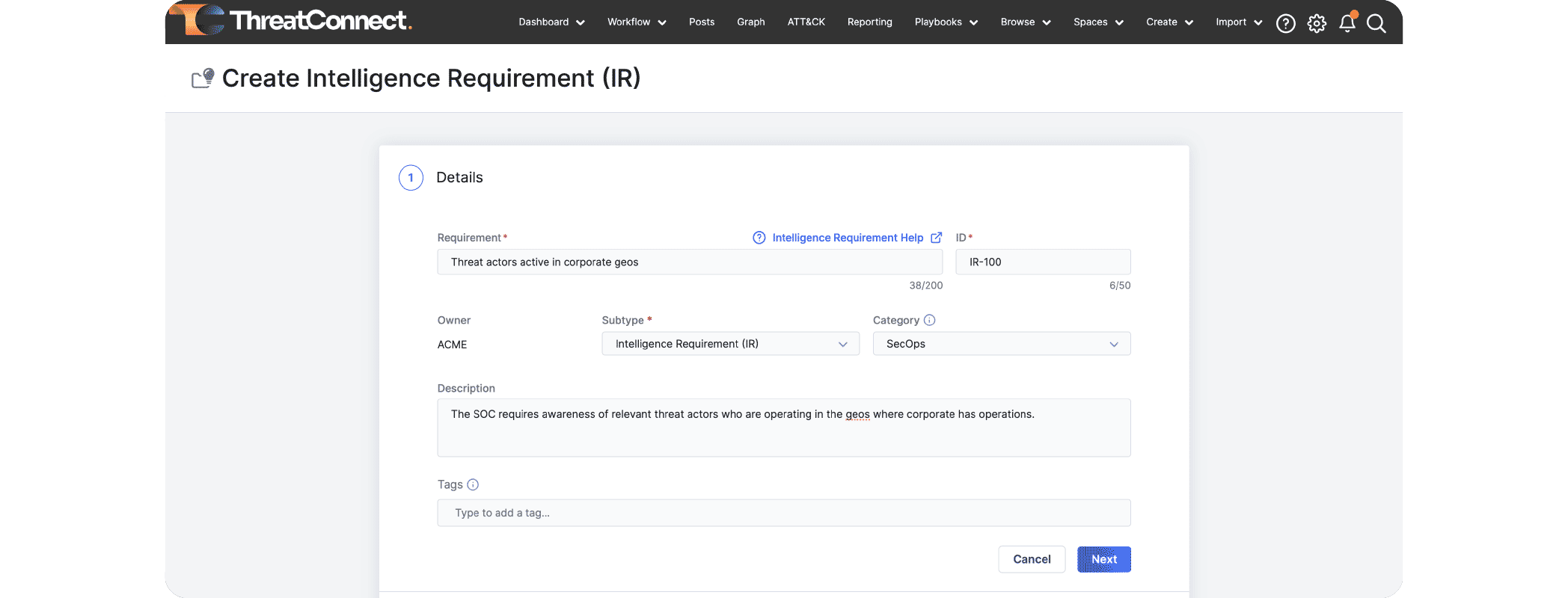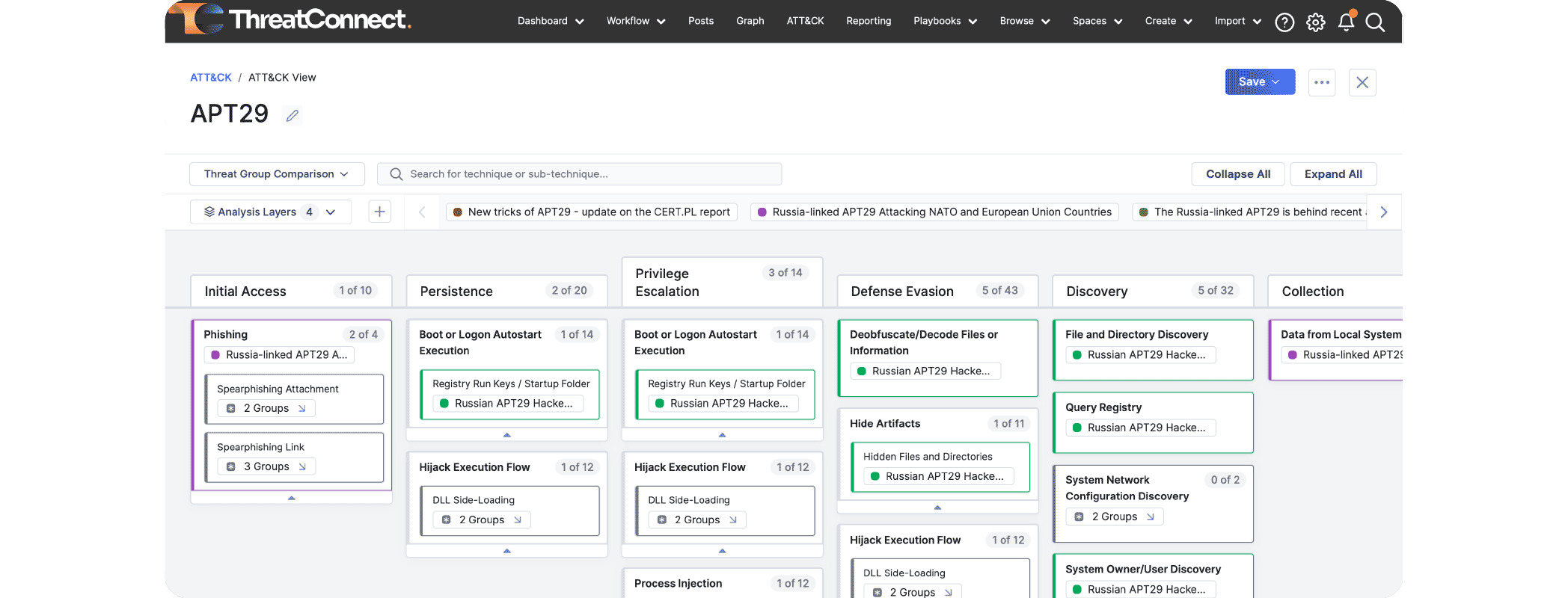
Version 7.2 was a major milestone in the evolution of the TI Ops Platform with the introduction of ATT&CK Visualizer. Visualizer does what it says – it allows organizations to visually analyze their threat intelligence in the MITRE ATT&CK Framework directly in the Platform instead of having to use ATT&CK Navigator or spreadsheets.
We also released features to improve the operationalization of threat intelligence, like
- Tag Normalization and Management to enforce standardization of the tags used by teams
- Built-in Reporting enhancements for report management and easier dissemination
- Automated Enrichment was expanded with coverage for URLScan.io
October 2023
ThreatConnect broke new ground in operationalizing threat intel with the introduction of Intelligence Requirements in version 7.3. This feature was announced at Black Hat USA and received significant press coverage, such as being named by CRN as one of 20 Hottest New Cybersecurity Tools at Black Hat 2023 and one of the top new cybersecurity products by CSO Online.
And beyond launching Intelligence Requirements, we also delivered
- ATT&CK Visualizer enhancements that expanded its capabilities to provide a heatmap of tactics, techniques, and sub-technique coverage across multiple Groups.
- Automated Enrichment was expanded to DomainTools
Looking at 2024
2024 is already off to a bang with the release of version 7.4. I won’t spoil the surprises here, so be sure to check out the blog announcing the release. And don’t forget to take a tour of the ThreatConnect TI Ops or reach out to one of our experts to learn more about how ThreatConnect can help you operationalize your threat intel program.
