Unified Threat Library
Reduce complexity, eliminate false positives, and enable more effective detection and response. Easily aggregate, harmonize, and de-duplicate all your threat intel sources: commercial, open source, community, and internally generated.
A single source of truth
Don’t waste time collecting and processing threat intelligence. Automate the collection, normalization, and enrichment of your disparate intelligence data sources in a unified repository and scale to meet your intelligence big data challenges.
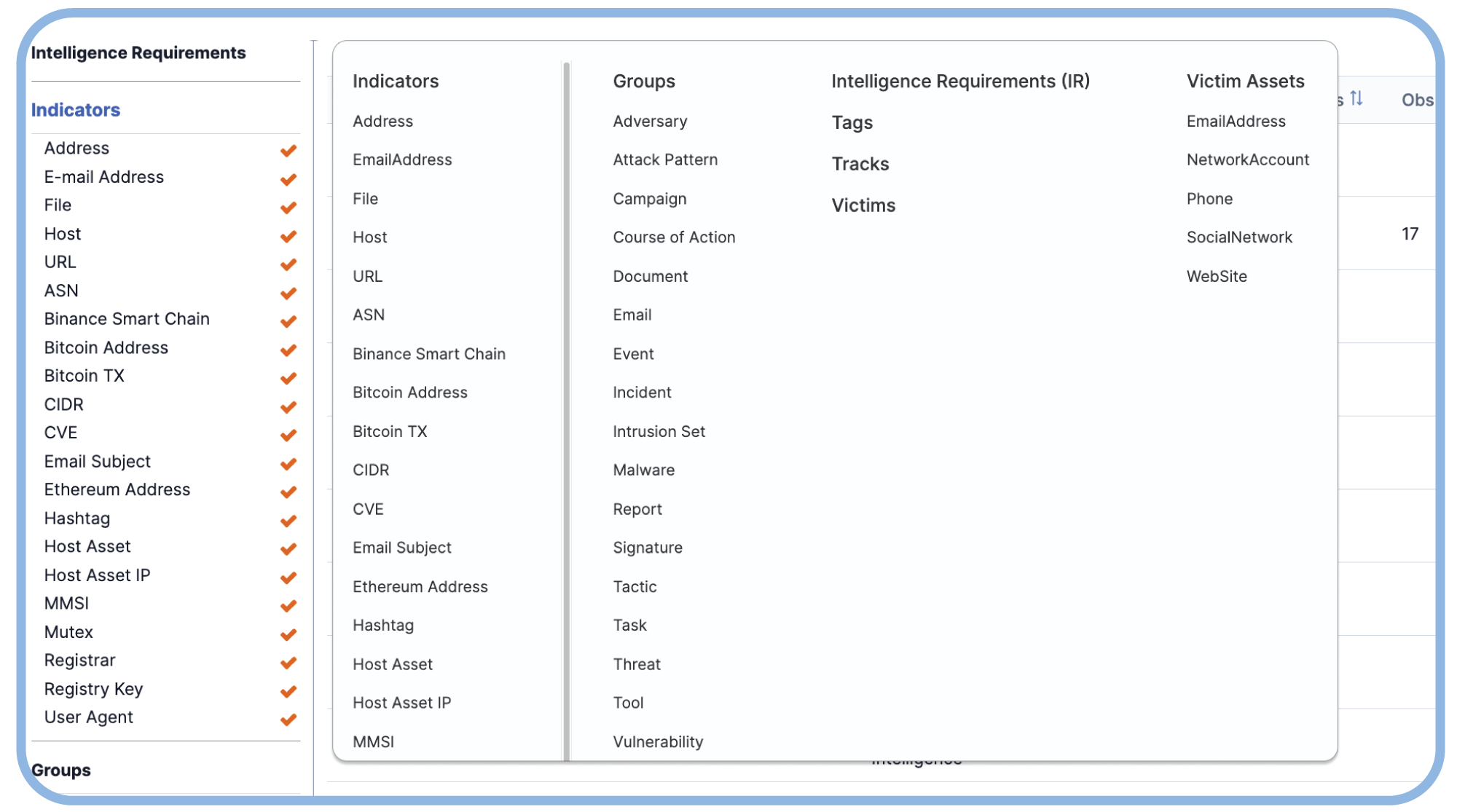
Quickly integrate all of your of intel sources
Leverage pre-built apps for popular intel sources, native support for STIX and TAXII, and a robust API for custom integrations.

Optimize Your Intel Investments
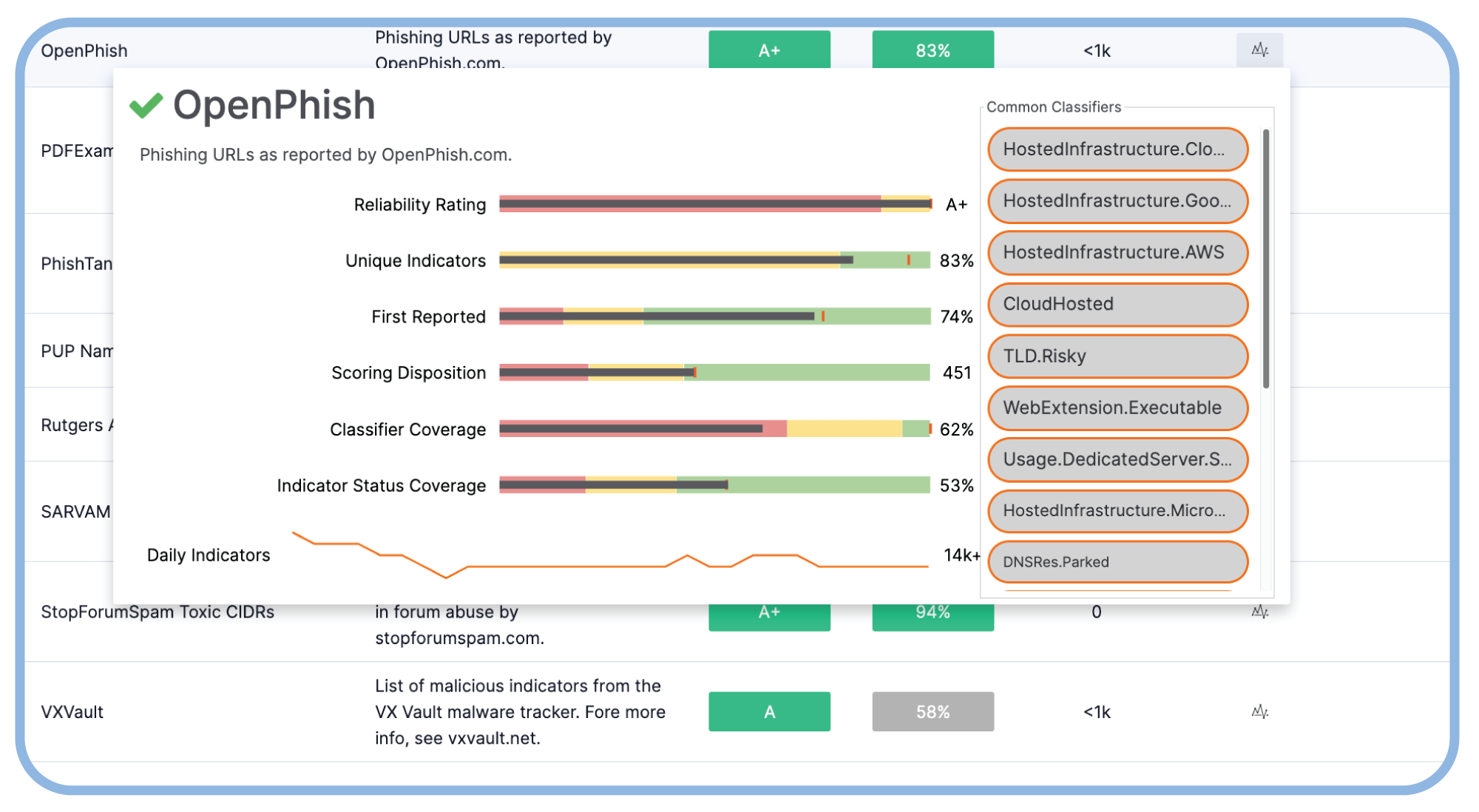
Use feed performance and Report Cards to make defensible decisions on where to invest your threat intel budget.
Create a dynamic threat intelligence loop
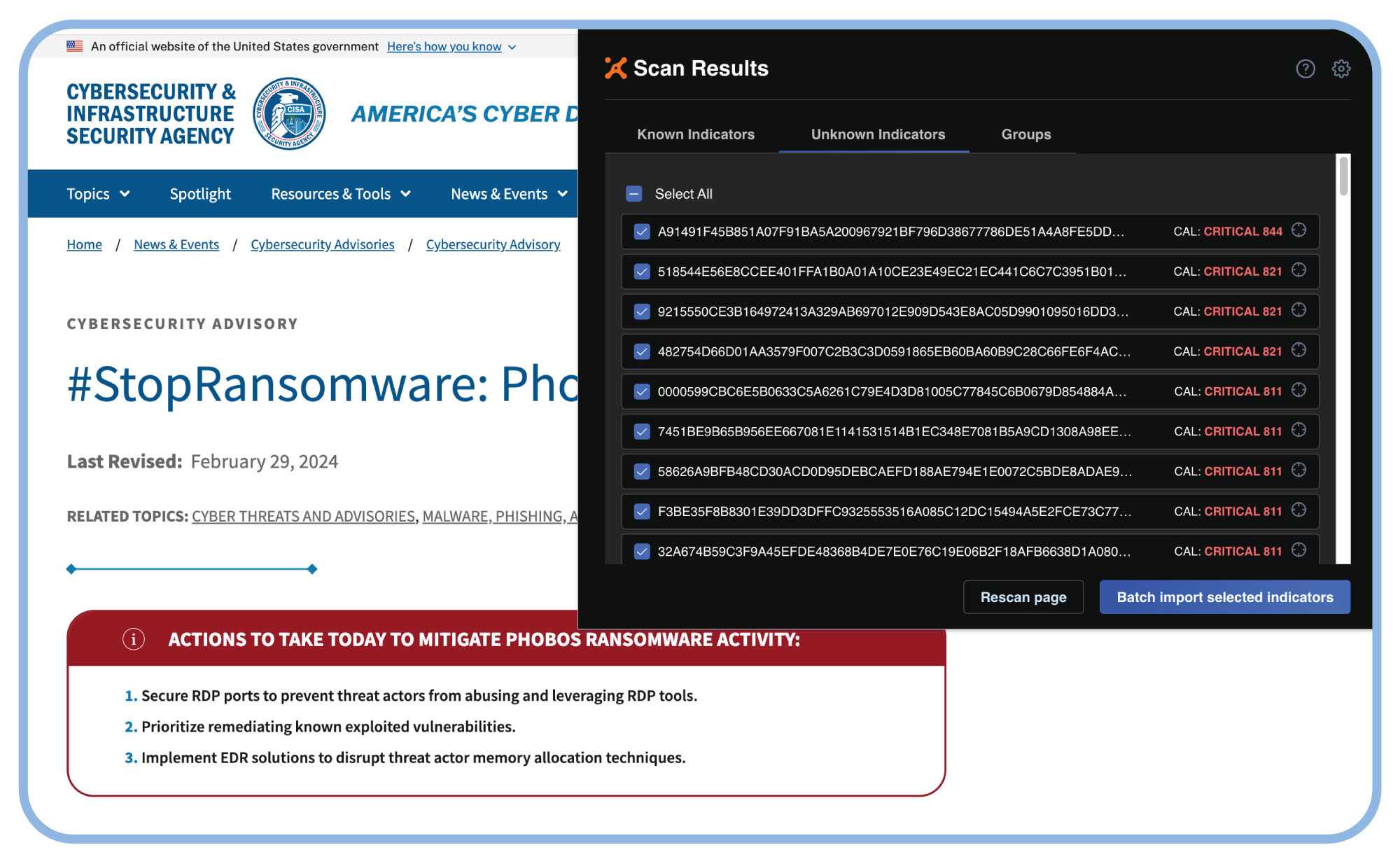
Intelligence Anywhere makes it easy to capture and memorialize internally created intel back into your threat library.
Enhance effectiveness, efficiency, and resilience with a unified threat library
Put Threat Intelligence at the Core of your Cybersecurity
Threat intelligence is vital to helping you defend your organization. Learn more about Threat Intelligence-Powered Security.
Bolster Your Defenses with a Unified Threat Library
Understand how a large energy and utilities organization transformed their cyber threat intel program.
Buyer’s Guide for Threat Intelligence Operations
Learn why ThreatConnect is the modern threat intel platform to transform your CTI program.