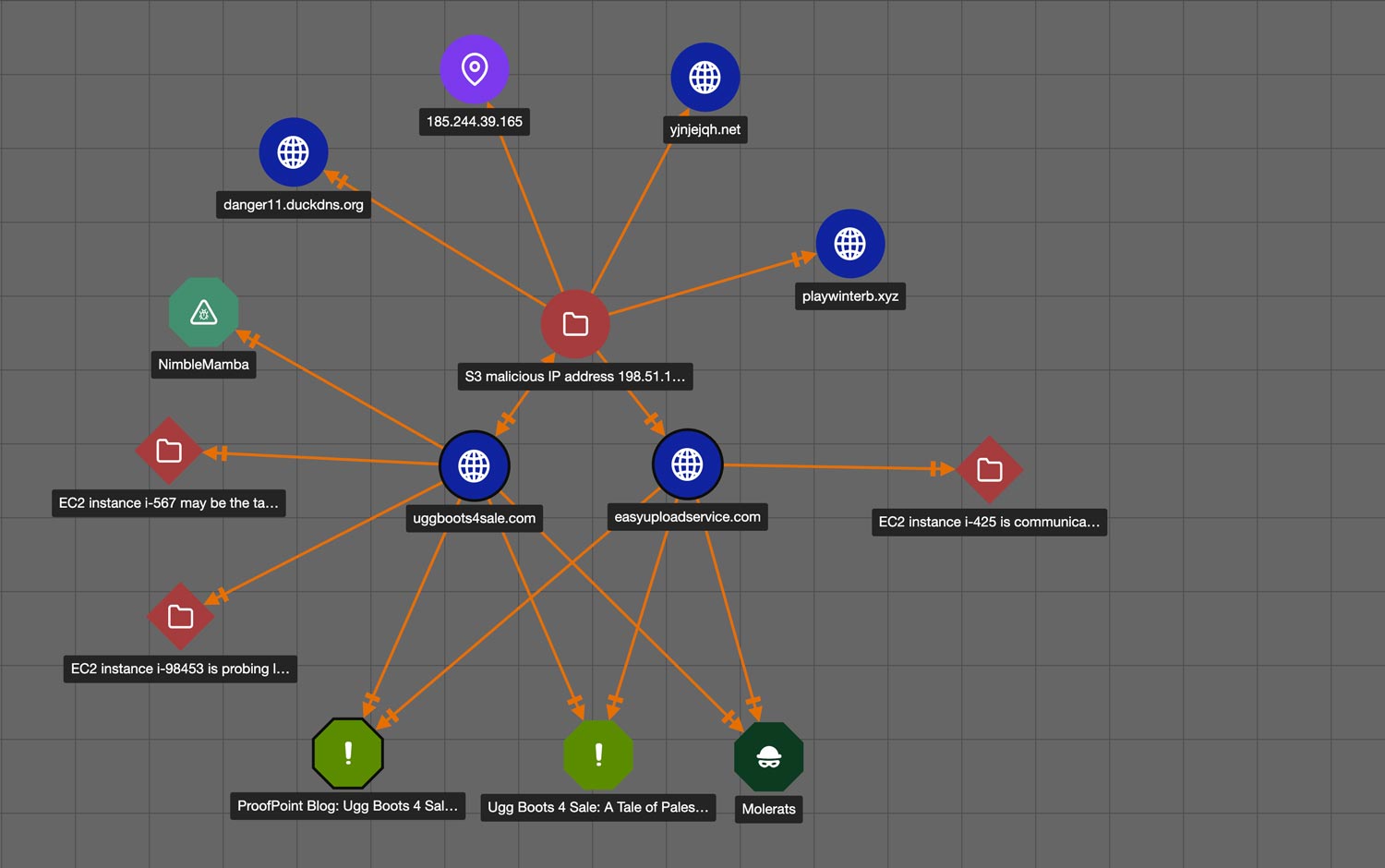
Intelligence-Powered Security Operations
Staying on top of emerging cyber threats means putting threat intelligence at the core of your security function. Whether you’re modernizing your SOC or creating or operating a cyber fusion center, you’ll need to leverage an automated system to synthesize and operationalize your incoming threat intelligence.
The ThreatConnect Platform enables intelligence-powered security operations by turning threat intelligence into actionable insights, capturing and applying analyst knowledge and tradecraft, and integrating, automating, and orchestrating activities across all your tools using machine power. Your teams will be more effective, more confident, and more collaborative.

Use Cases for Your Evolving Challenges
Explore Key Platform Features
CAL™
Natively enrich intelligence with real-time insights into threats and indicators. CAL leverages ground-truth insights from the ThreatConnect user community around the globe.
Low Code Playbooks
Reduce the manual burden on analysts and save money with extensible drag-and-drop automation designed from the ground up to work with our intel-first data model. Standardize processes and workflows to improve consistency and increase efficiency.
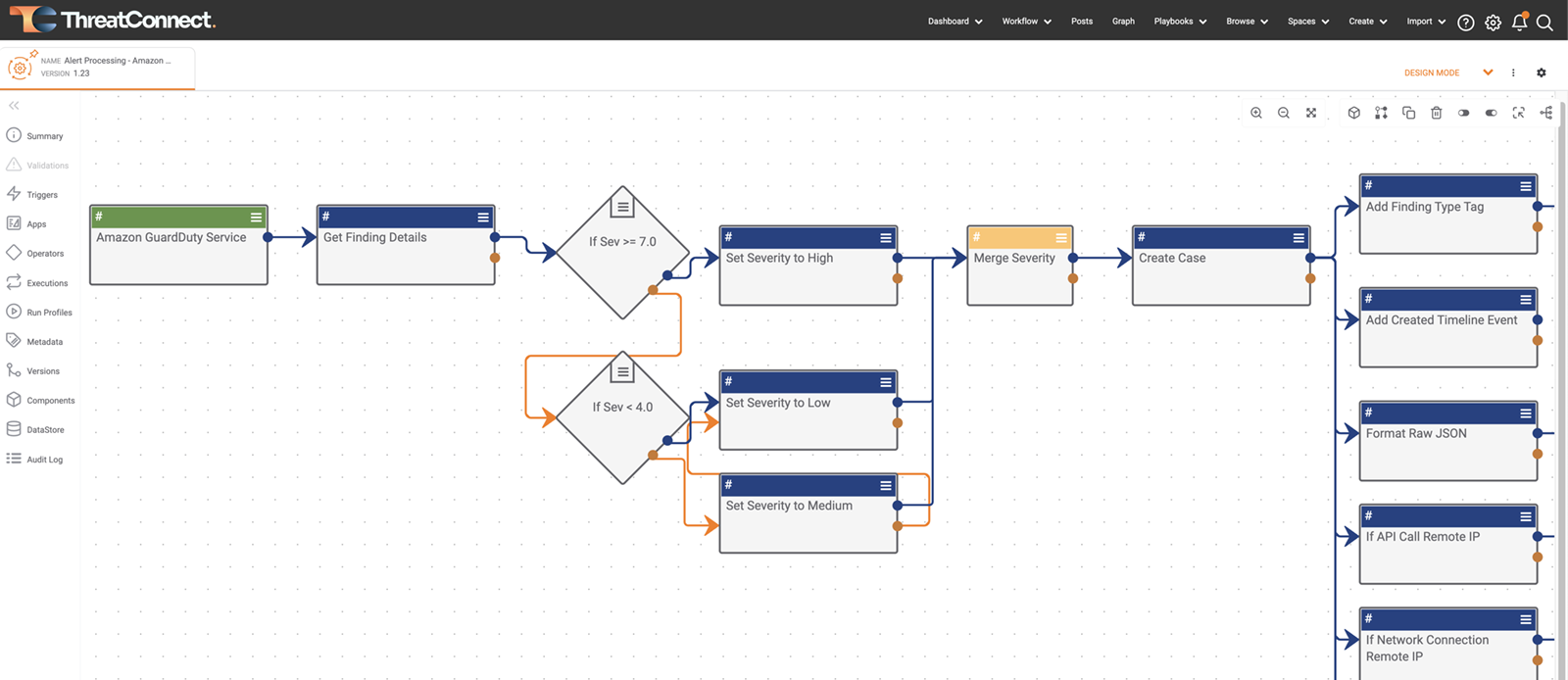
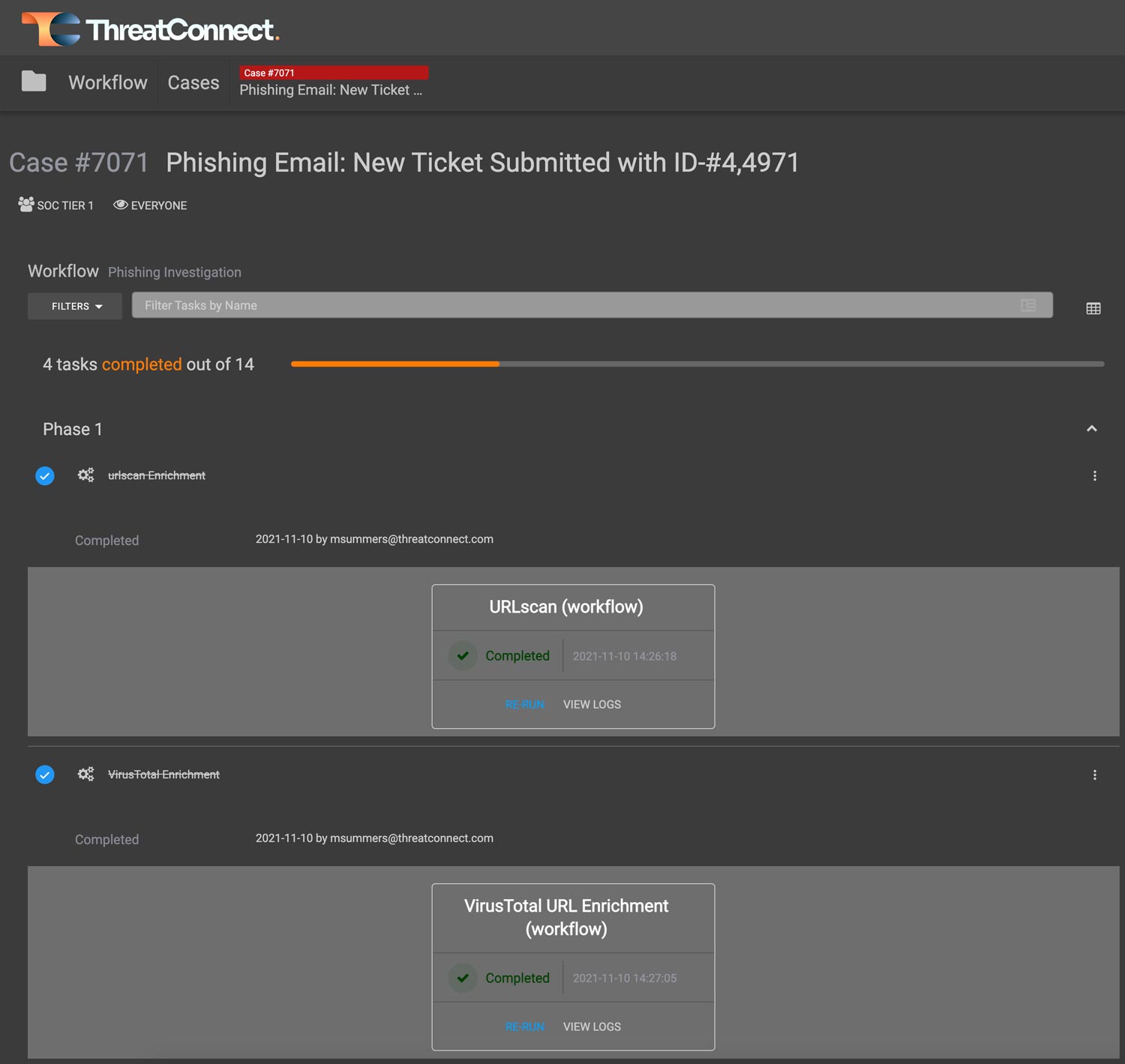
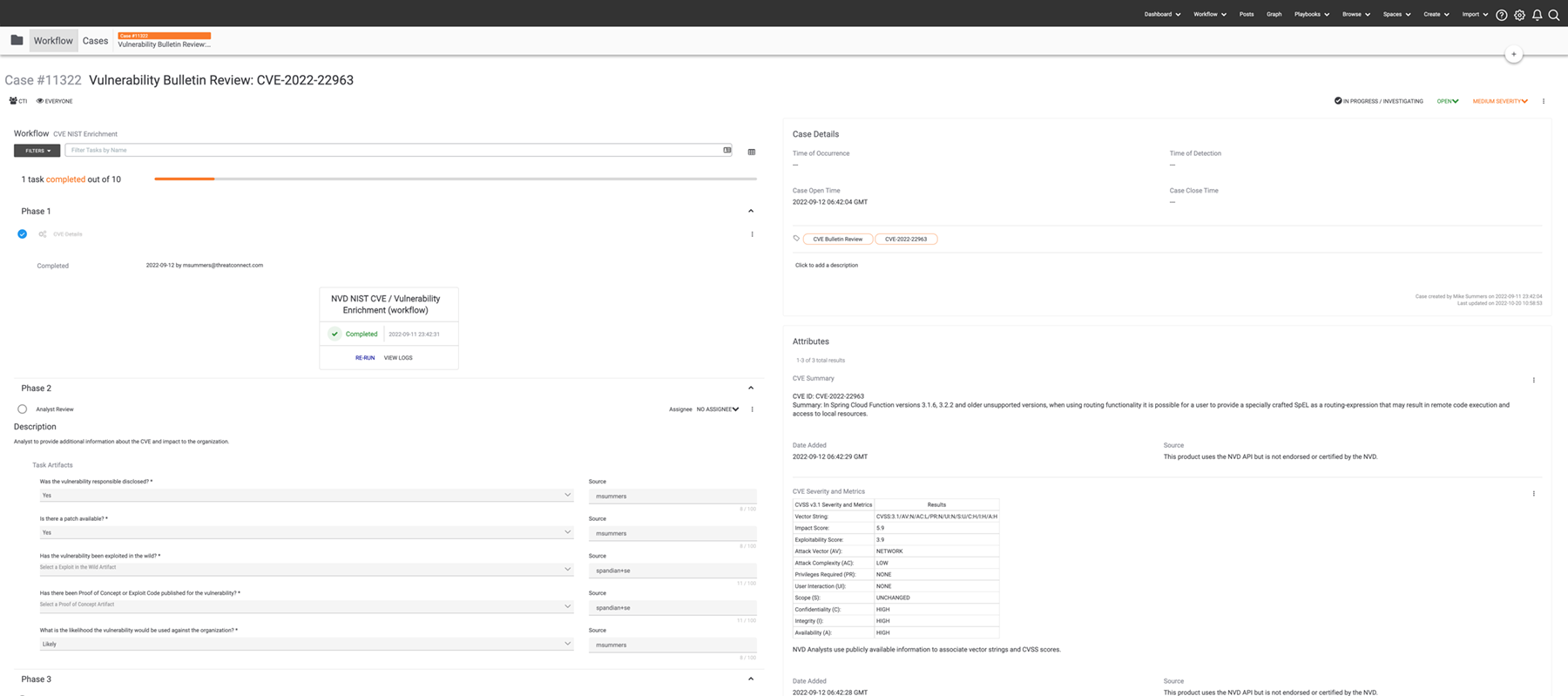
Workflow
Workflow gives you access to full Case Management from the same Platform where you’re managing your threat intelligence automation and security processes. Automate case creation, intel production, and data enrichment for smarter, faster, and more-targeted investigations and decision-making.
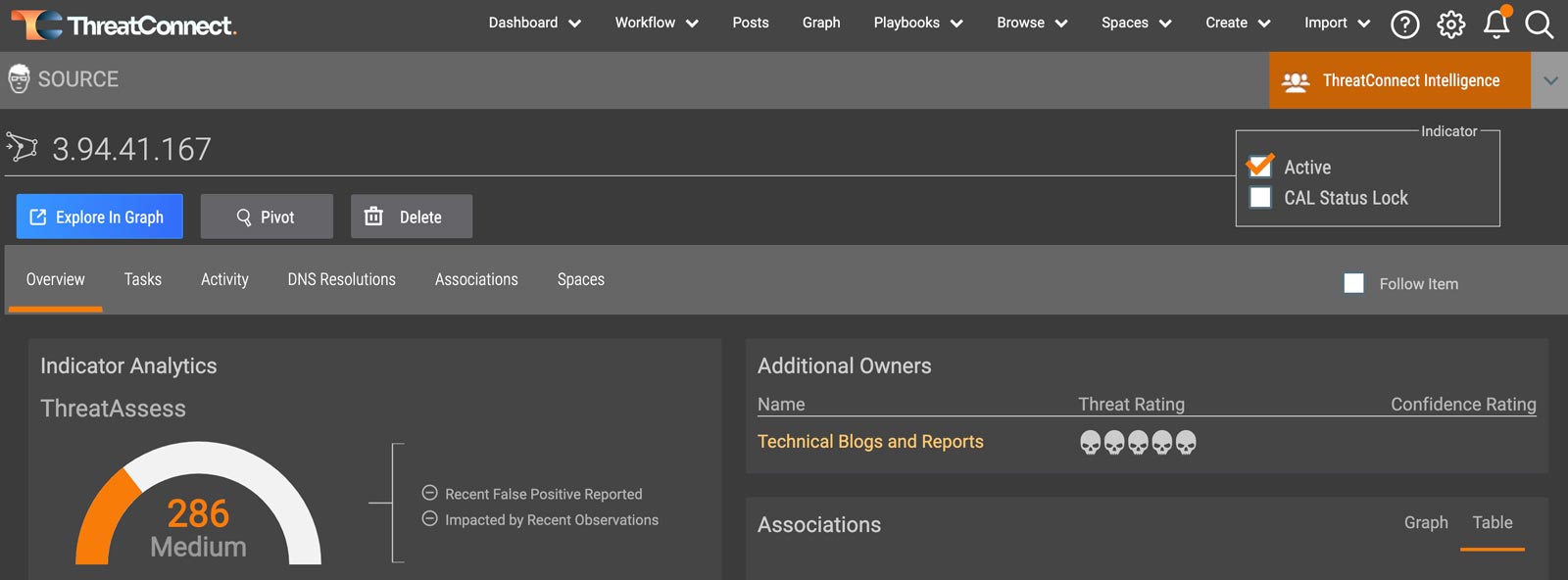
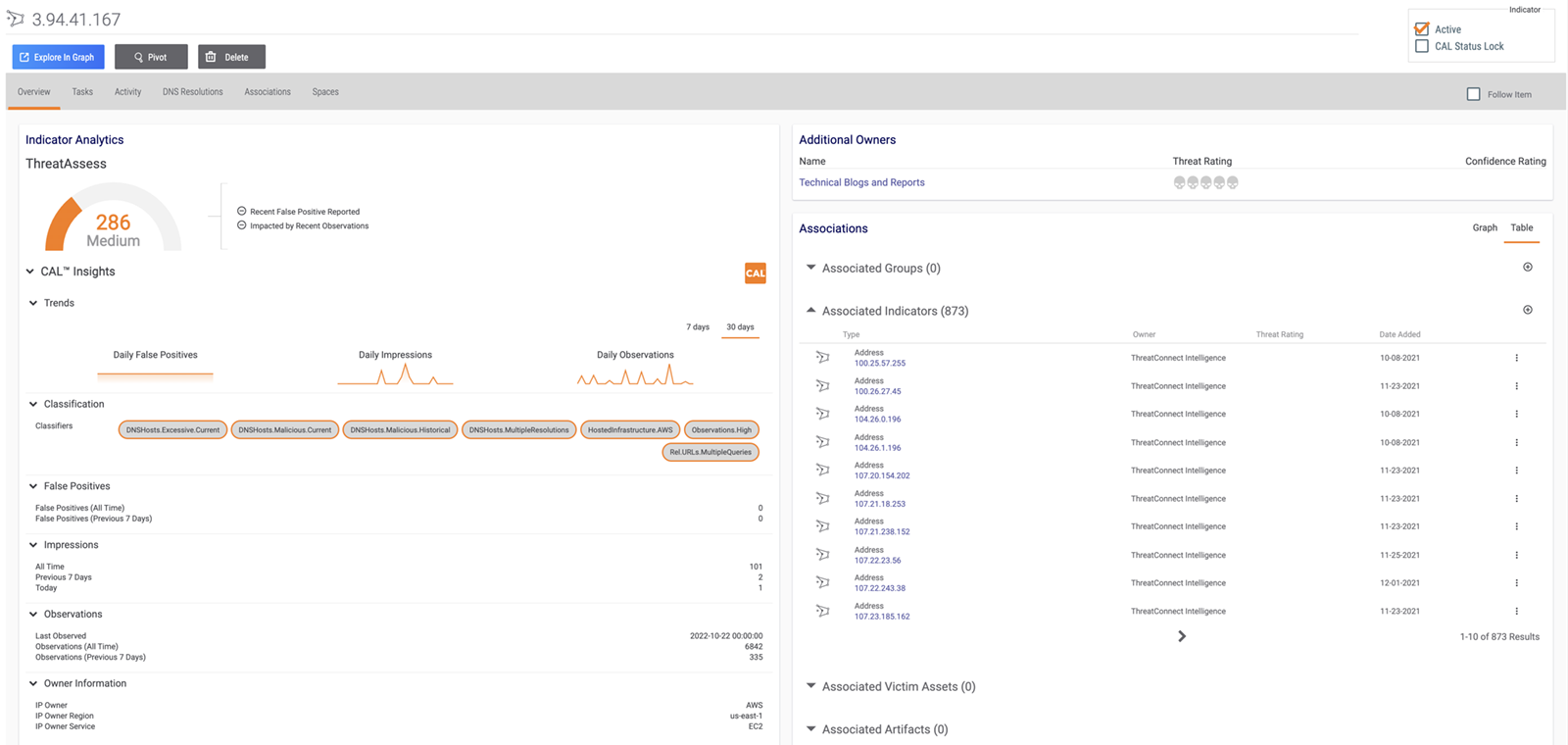
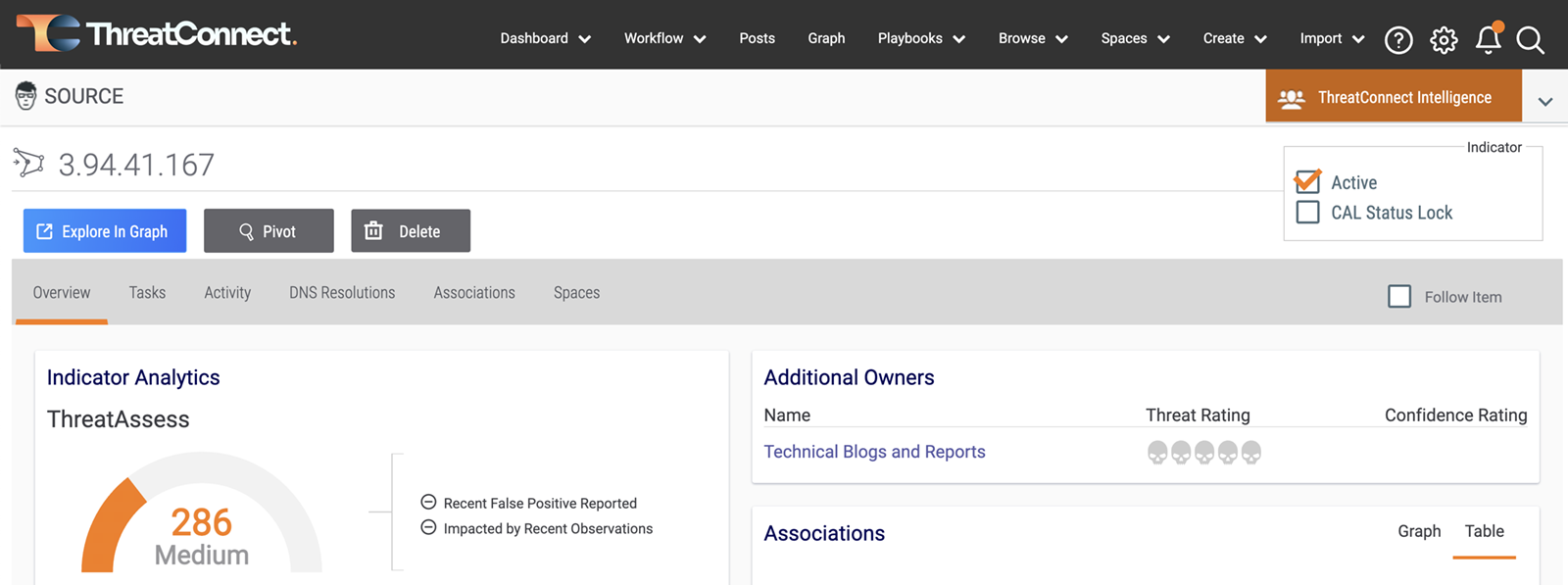
ThreatAssess
Prioritize decision-making with reputational analysis that scores the criticality of an indicator of compromise (IOC) on a single numeric scale.
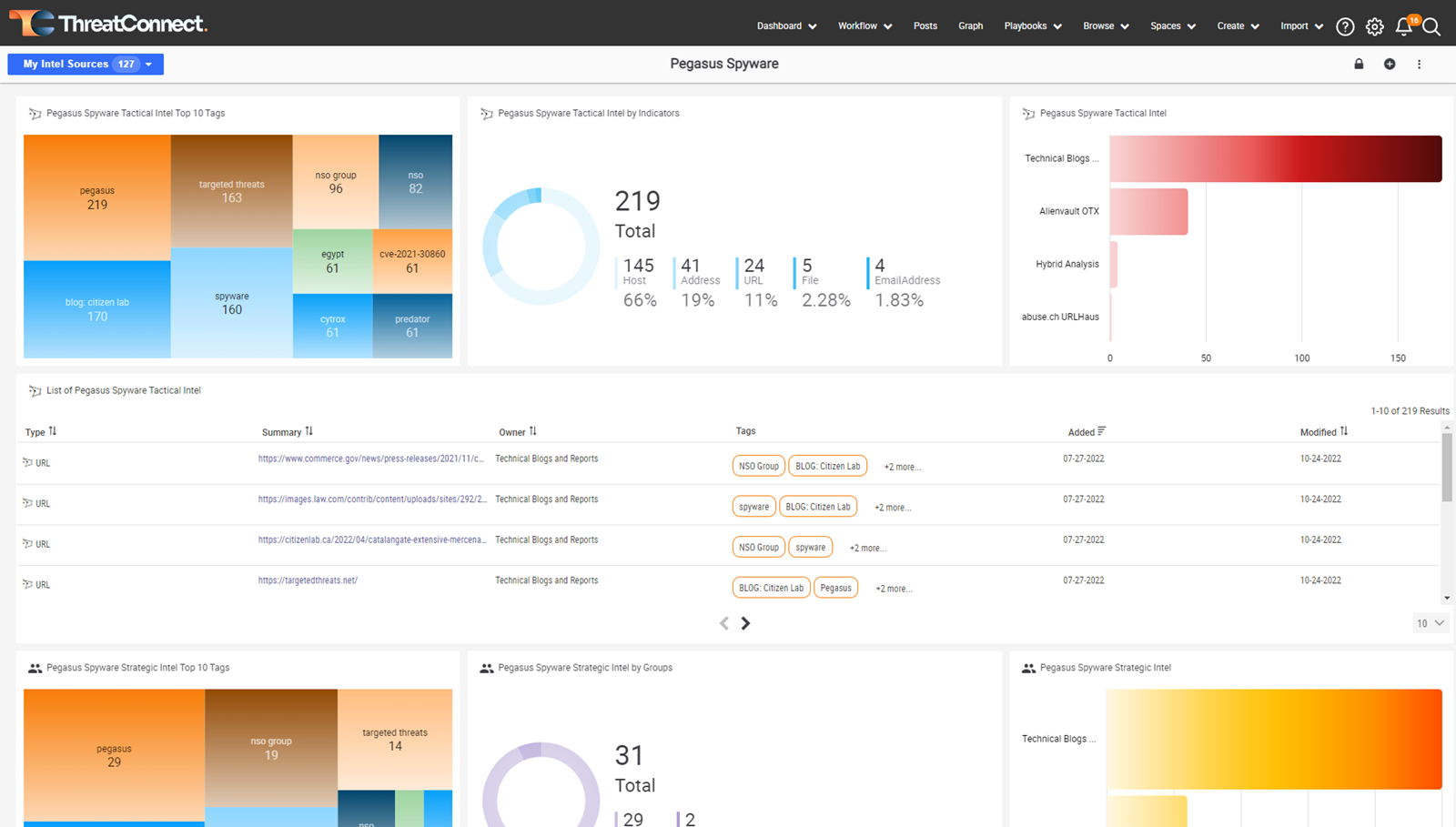
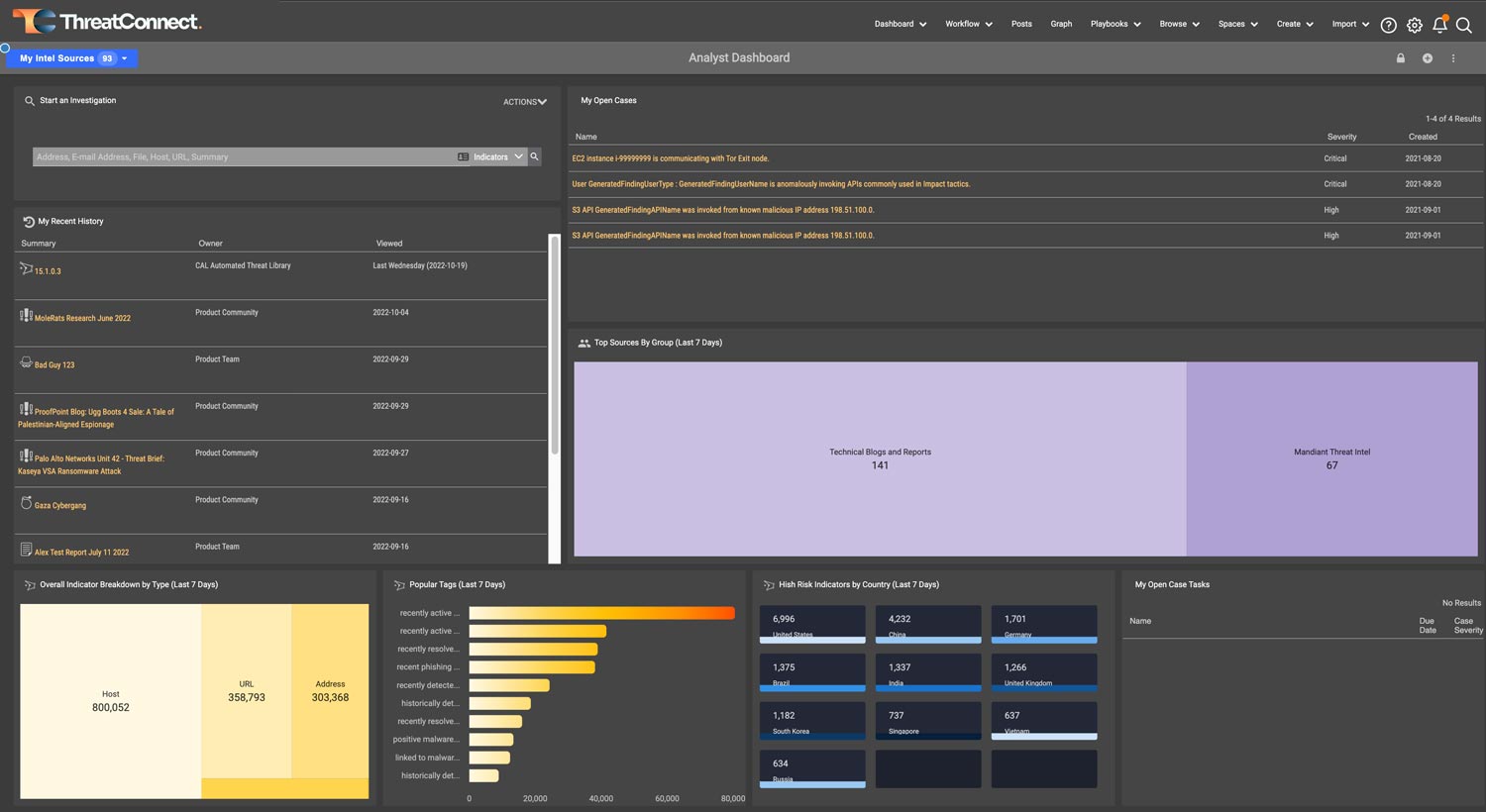
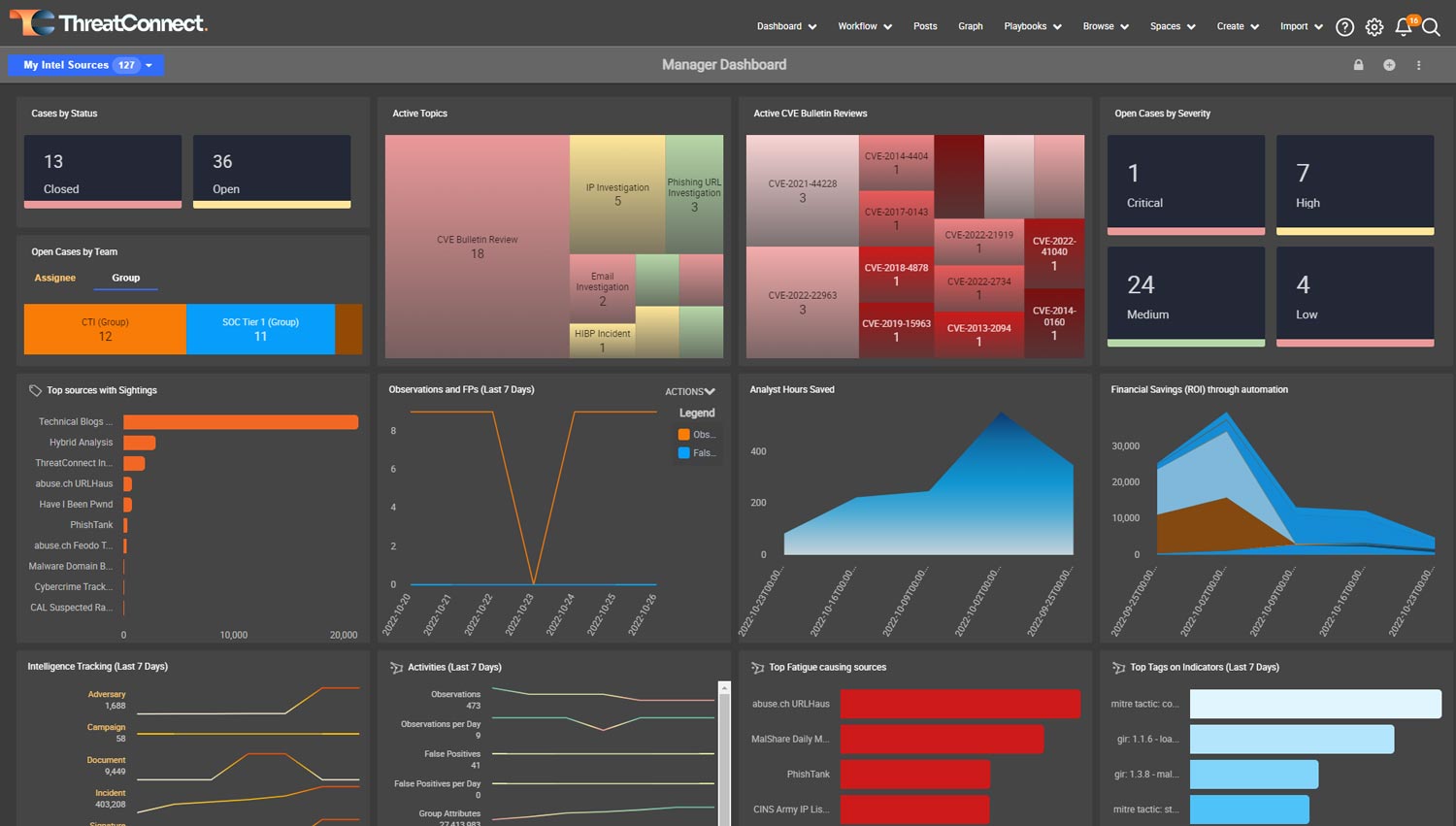
Dashboards and Reporting
ThreatConnect features dashboards that let you visualize data. You’ll see the impact of your security efforts and better understand the threats your organization faces. Customize your dashboards in the platform to align your teams and deliver insights to meet each analyst’s specific needs.