No Results Match Your Search
Please try again or contact marketing@threatconnect.com for more information on our resources.
The SOC is a Machine – And Lessons Learned from Lockdown
In this webinar, experts discuss how the global pandemic forced businesses and the cyber security industry to adapt. Meanwhile, the SOC was forced to maintain security for the company and help provide the employees the ability to maintain business operations.
The Connection – Using Phishing Emails to Demonstrate ThreatConnect’s SOAR capabilities
In this webinar, experts offer insight about ThreatConnect’s three aspects of SOAR: our TIP capabilities, Playbooks, and Case Management using phishing emails as the main use case for the overview.
Building and Managing the Next-Generation Security Operations Center (SOC)
In this webinar, experts offer insight and recommendations on how to build a next-generation SOC, and what tools and skills you may need to outfit that SOC to respond to today’s most current threats and online exploits.
Using MITRE ATT&CK and Threat Intelligence to Stop Attacks
The ThreatConnect Platform was specifically designed to help users understand adversaries, automate workflows, and mitigate threats faster using threat intelligence. When integrated with Flashpoint, users can seamlessly access finished intelligence and targeted data from illicit online communities. By mapping these insights to the MITRE ATT&CK framework, users can gain even greater visibility into emerging threats, […]
Shaking Off Security Alert Fatigue: Tips for Taking Control
Adding new security tools to your SOC toolset may help alert you to the newest cyber threats to your business. However, when a zillion unprioritized alerts hit you in a day, you might start treating them like whack-a-mole or the snooze button on your alarm clock. How can you manage security alerts so they are […]
How to Get Promoted: Developing Metrics to Show How Threat Intel Works
Many organizations have operationalized threat intelligence as part of a well-rounded security program, but often struggle to show the return on investment. This webinar focuses on developing measures of effectiveness whether your program is just getting started or is pretty well established, independent of what tools or vendors you use.
Disrupting Adversary Infrastructure
Using the State of New York as an example, this white paper describes how ThreatConnect’s tactics are intended to encourage ISP and government collaboration with a sharp focus on disrupting adversary infrastructure.

Security Operations Maturity Model
ThreatConnect developed a Security Operations Maturity Model to provide a systematic guide to help you understand where your organization resides on the path to fully leveraging the power of a SOAR Platform.
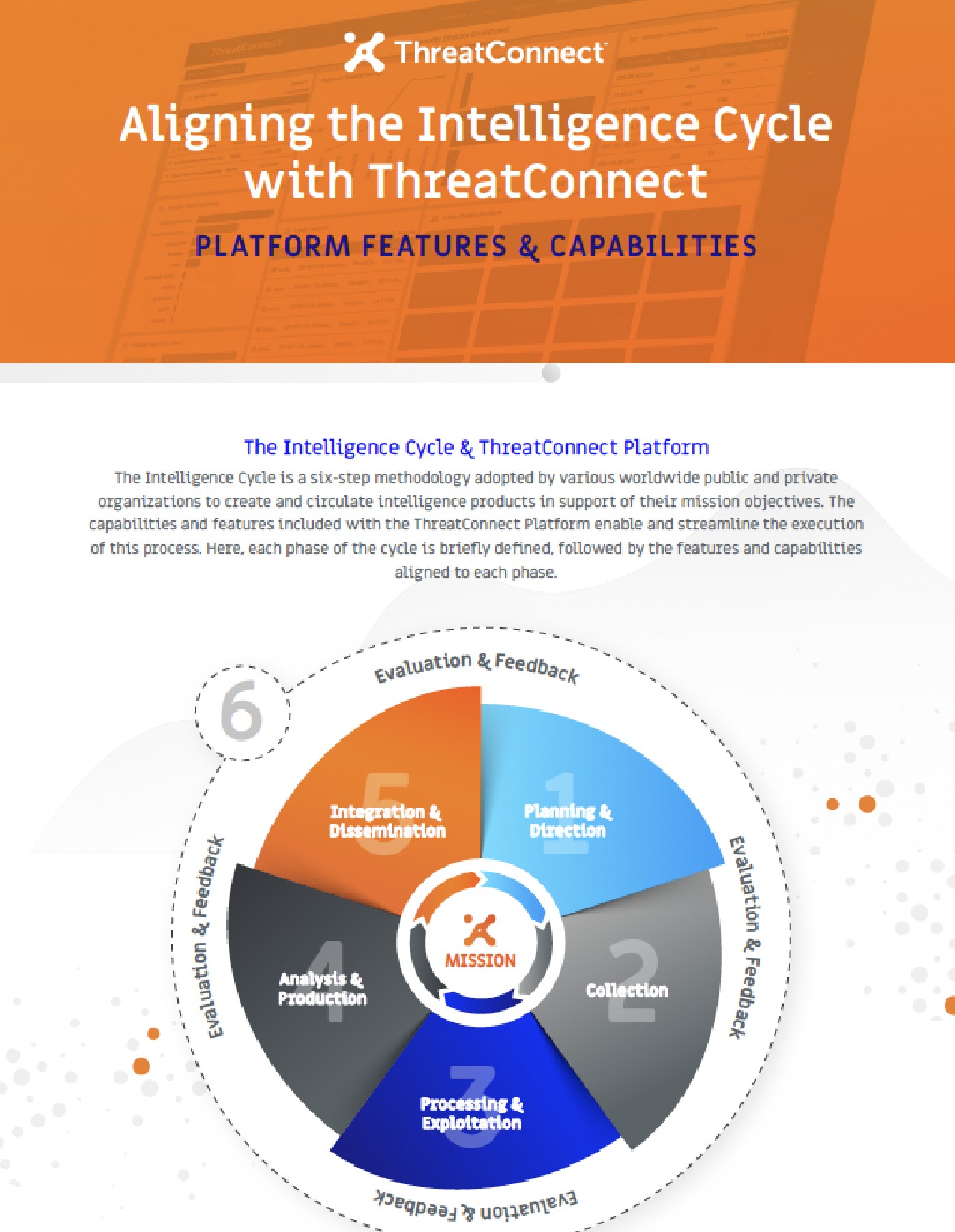
ThreatConnect Intelligence Cycle
The Intelligence Cycle is a foundational six-step framework utilized by organizations worldwide. Explore our infographic to discover how the ThreatConnect Platform seamlessly integrates with and enhances each stage of the cycle.

Customer Success Story: Packaged Goods Leader Takes Automated Cyber Risk Quantification Global
Find out how ThreatConnect’s Risk Quantifier solution: Helped a customer cut out the long, laborious, and manual effort of gathering and tabulating data in Excel spreadsheets and using business intelligence to produce results they could count on. Delivered results for more than 250 applications and 30 separate legal entities in less than 90 days. Established […]

A ThreatConnect Customer Success Story: Establishing a Strong Partnership to Ensure Continued Success
Find out how ThreatConnect: Helped a customer set up and deploy the ThreatConnect TI Ops Platform. Delivered tailored training, ensuring that the customer’s security team felt confident in their ability to use the Platform. Established multiple avenues for ongoing communication with the ThreatConnect Customer Success and Support Teams. Learn more about ThreatConnect’s TI Ops platform […]
Reduce Risk and Improve Security through Infrastructure Automation
Watch this webinar to hear Joe Reese, Product Manager at ThreatConnect and guest speaker Joseph (JB) Blankenship, Principal Analyst at Forrester discuss the effect security automation is having on infrastructure and security processes. They talk about how automation can reduce security “grunt work” and increase the speed and reliability of incident response procedures. Download the […]



