No Results Match Your Search
Please try again or contact marketing@threatconnect.com for more information on our resources.
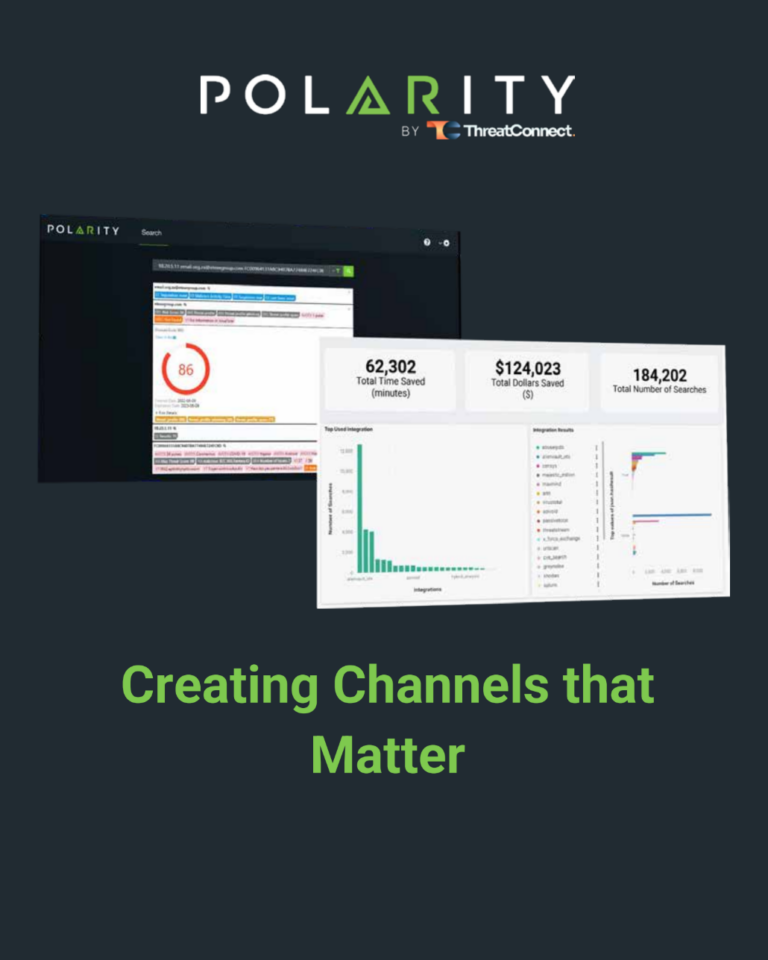
Creating Channels That Matter
Polarity is a cutting-edge platform designed to help IT and cybersecurity professionals manage and utilize intelligence more effectively. By creating a “collective memory,” Polarity delivers real-time insights directly to users, ensuring critical information isn’t missed. Its core feature, Channels, organizes and tailors data into reference or collaborative groups, streamlining workflows and enhancing decision-making. Polarity empowers […]

Smarter Security Series – How Do You Operationalize Cyber Threat Intelligence and Where Do You Start?
Introducing ThreatConnect’s Smarter Security Expert Series! We’re interviewing the brightest minds in the cyber industry and getting their expertise on current trends and tips and tricks for a successful modern security team. For our first guest, we’re joined by Colin Anderson, CISO at Ceridian and ThreatConnect’s newest Board Advisor! Colin sat down with our VP […]

Video: Smarter Security Series – The Importance Of Cyber Threat Intelligence In Today’s Industry
Introducing ThreatConnect’s Smarter Security Expert Series! We’re interviewing the brightest minds in the cyber industry and getting their expertise on current trends and tips and tricks for a successful modern security team. For our first guest, we’re joined by Colin Anderson, CISO at Ceridian and ThreatConnect’s newest Board Advisor! Colin sat down with our VP […]

Smarter Security Series – The Importance of Cyber Threat Intelligence in Today’s Industry
Toby Bussa, Vice President of Product Marketing at ThreatConnect, recently sat down for a discussion about cyber threat intelligence with Colin Anderson. As a seasoned Cybersecurity Executive, Anderson, who has over 25 years of experience, is currently the Senior Vice President and CISO at Ceridian, a Human Resource Management software company. In this conversation, Bussa […]

Dawn of Threat Intelligence Operations White Paper
Threat Intelligence Operations (TI Ops) is the evolution of the cyber threat intelligence function. TI Ops is critical for organizations that want to modernize their security operations to address increasingly hostile adversaries looking to take advantage of growing attack surfaces and increasing exposures. Adopting a TI Ops approach is critical to getting ahead of the […]

Evolved Threat Intel Lifecycle Infographic
The cyber threat intel lifecycle has been around for close to twenty years, and has been the de facto approach to operating a threat intel function. However, as threat intelligence needs to be operationalized, the lifecycle is showing its limits. An Evolved Threat Intel Lifecycle is required that accounts for both the production and consumption […]

How ThreatConnect Enables Cyber Fusion Operations
Download our whitepaper to learn how the Intelligence-Powered Security Operations approach changes the game for cyber fusion operations with increased collaboration and improved efficiency, which lightens the load for everyone on the team and better protects the organization.

Operationalizing Cyber Threat Intelligence Webinar
Cyber threat intelligence is a necessary part of all modern Security Operations teams, but what do you do with it? Data and algorithms are the fuels for insights and driving decisions in a modern digital business, and cyber threat intelligence (CTI) is the fuel for modern security operations. Operationalizing threat intelligence requires the right mix […]
Customer Story: Global Aerospace and Defense Company – Consolidating Threat Intelligence & Automating Processes With Playbooks
Company Type: Aerospace & Defense Technologies Industry: Aerospace & Defense Company Size: Global Fortune 400 Challenge This Global Fortune 400 Aerospace & Defense organization works with multiple separate business units that each have their own set of unique use cases for threat intelligence standard operating procedures (SOPs). This includes specific tags per business unit, […]
Customer Story: Large U.S. Health System – Phishing Automation and Bulk Importing and Enrichment of Indicators
Company Type: Hospital System Industry: Healthcare Company Size: 50 Hospitals across 7 states Challenge This large, multi-state health system’s major challenges involved automating Threat Intelligence collection, IOC enrichment, creating workflow templates, and improving Case Management. The main use cases were around phishing automation and bulk importing and enrichment of indicators (using VirusTotal) and specific […]
Customer Story: National Medical Insurance Provider Quantifies Risk
Company Type: Medical Insurance Provider Industry: Healthcare Company Size: 40 Independent Operating Companies Challenge Healthcare Cyber Risk: The healthcare company was unable to consistently measure cyber risk across its member companies, and had difficulty accurately showing the potential financial impact of a successful attack. They also were challenged by subjective project prioritization that did not […]
Customer Story: Large Enterprise Needed Centralized Threat Intelligence Management
Company Type: Software Provider Industry: Technology Company Size: 130,000+ Employees Challenge This large technology client was looking for a centralized repository of contextualized threat intelligence, from which humans and machines can get a unified view to derive associations, prioritize, and collaborate on observations. The solution needed to be able to collect, normalize, and disseminate data […]



