Splunk
Splunk Inc. (NASDAQ: SPLK) provides the leading software platform for real-time Operational Intelligence. Splunk® software and cloud services enable organizations to search, monitor, analyze and visualize machine-generated big data coming from websites, applications, servers, networks, sensors and mobile devices. More than 8,400 enterprises, government agencies, universities and service providers in more than 100 countries use Splunk software to deepen business and customer understanding, mitigate cybersecurity risk, prevent fraud, improve service performance and reduce cost. Splunk products include Splunk® Enterprise, Splunk Cloud™, Hunk®, Splunk MINT Express™ and premium Splunk Apps.
Integrations
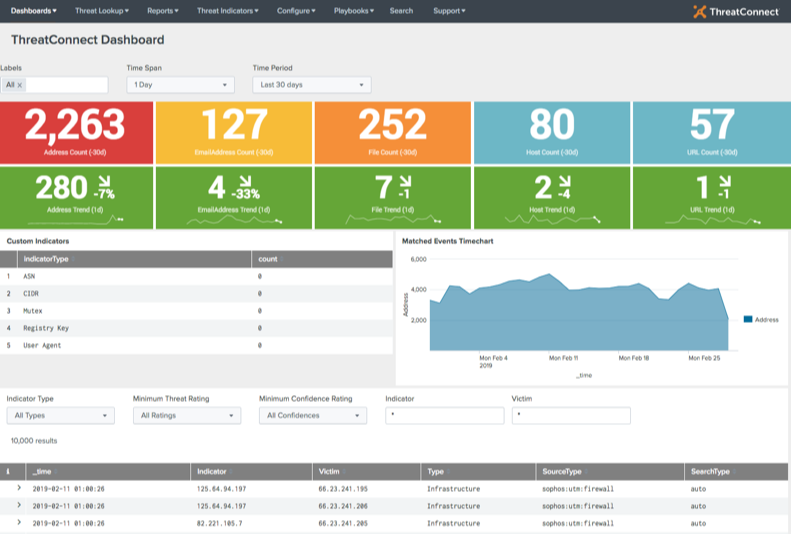
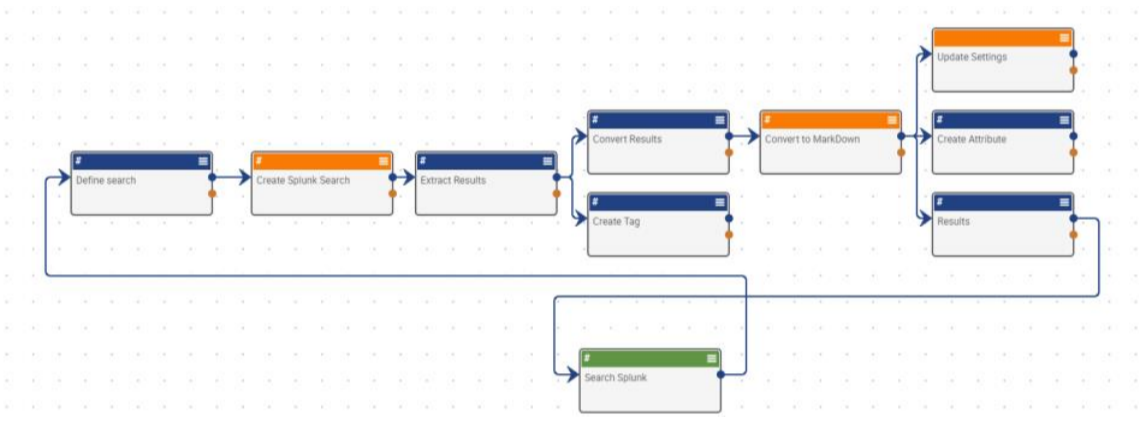
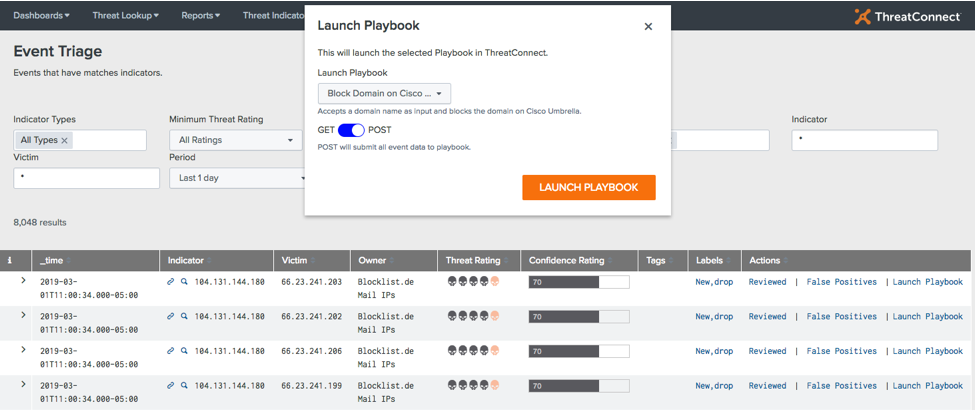
How Splunk Enterprise Integrates With ThreatConnect's Threat Intelligence Platform
Keep ReadingRelated Resources
Built By ThreatConnect
Related Resources
Built By Polarity
TruSTAR with Polarity
Keep ReadingSplunk with Polarity
Keep ReadingRelated Resources
Built By Polarity
Splunk SOAR with Polarity
Keep ReadingRelated Resources
Built By Polarity

 Polarity
Polarity