What Is Federated Searching?
Federated search is simultaneously retrieving information across multiple websites, online databases, and repositories using a single search tool. This strategy makes large amounts of data easily searchable compared to using several sets of indexes. Federated searching can reduce data duplication, but it also requires secure integrations and access controls to keep users and systems protected.
In threat intelligence, federated search allows users to search several security systems from one location. It makes it more convenient for organizations to gather data and information without performing a manual search.
Federated vs. Enterprise Search
Federated searching utilizes APIs or other connectors to simultaneously connect to and query multiple data sources. This capability is ideal in cybersecurity, where new threat intelligence is constantly emerging from a wide array of tools and feeds.
Enterprise search relies on a single, centralized index of an organization’s internal data. It can be effective for static datasets, such as a company intranet or a knowledge base. However, the process of collecting and indexing all that data can be slow and resource-intensive. For a security team, the information they need might be hours or even days old, a critical gap when dealing with an active threat.
| Metrics | Enterprise Search | Federated Search |
| Data Sources | Indexes internal documents, CRMs, and other business-related data | Connects to threat intelligence feeds, SIEMs, malware analysis tools, vulnerability scanners, and more |
| Data Freshness | Relies on indexing schedules, creating a time lag between when data is created and when it’s searchable | Provides near-real-time access to the latest information by querying data sources live, depending on source latency and availability |
| Implementation | Often requires a large-scale data ingestion and indexing project, which can be time-consuming and expensive | Can be implemented quickly with fewer resources using APIs to connect to existing tools |
Why Modern Security Teams Rely on Federated Search
Federated search empowers analysts to query all relevant security and threat intelligence sources concurrently. This visibility accelerates investigations, shortens incident response cycles, and reduces the manual work required to pivot between different security tools. Federated search capabilities enable security professionals to break down data silos, gain instant insights, and better protect the organization from threats.
Who Uses Federated Search Tools?
A variety of organizations and professionals use federated search tools. Some of the most common users include:
- Threat hunters: Threat hunters use federated search to comb through numerous security data to search for malware, monitor patterns for suspicious activity, and enhance an organization’s security system.
- Incident response teams: Incident response and cybersecurity teams use federated search to identify potential threats and vulnerabilities in their systems.
- Security operations center (SOC): SOCs use federated search tools to monitor the health of their security system and maintain compliance and security across different platforms and services.
- Red teams and Pentesters: Red teaming and penetration testing experts use federated search to identify possible security flaws and help enhance an enterprise’s response time to cyberthreats.
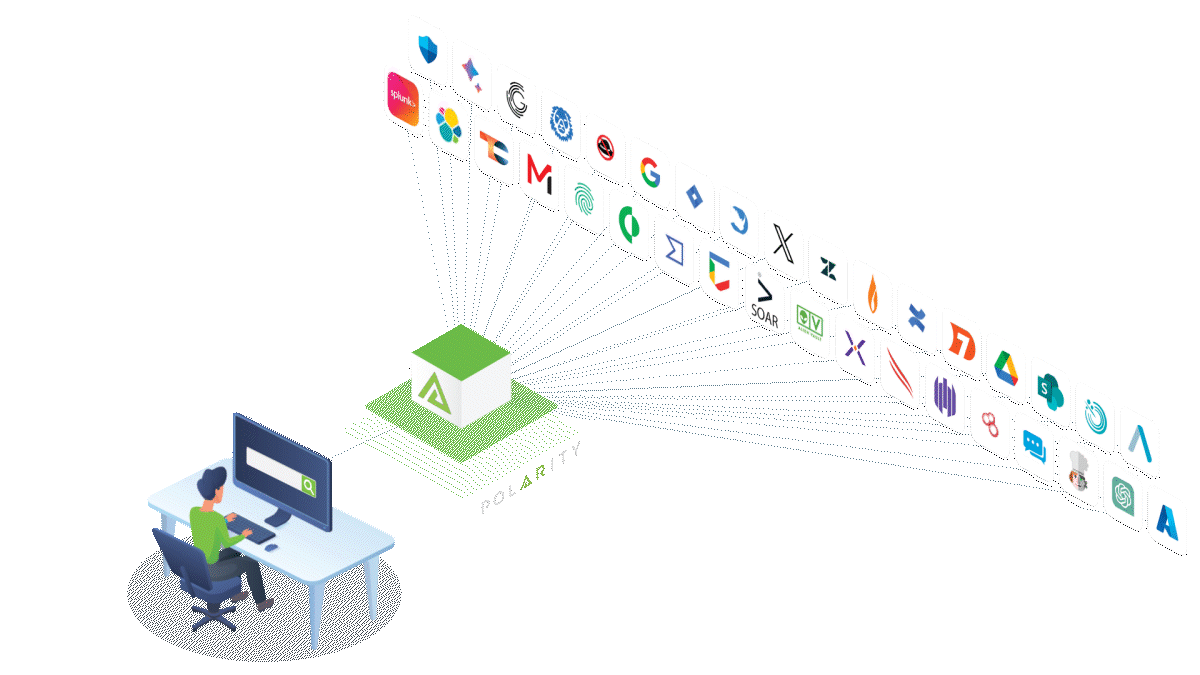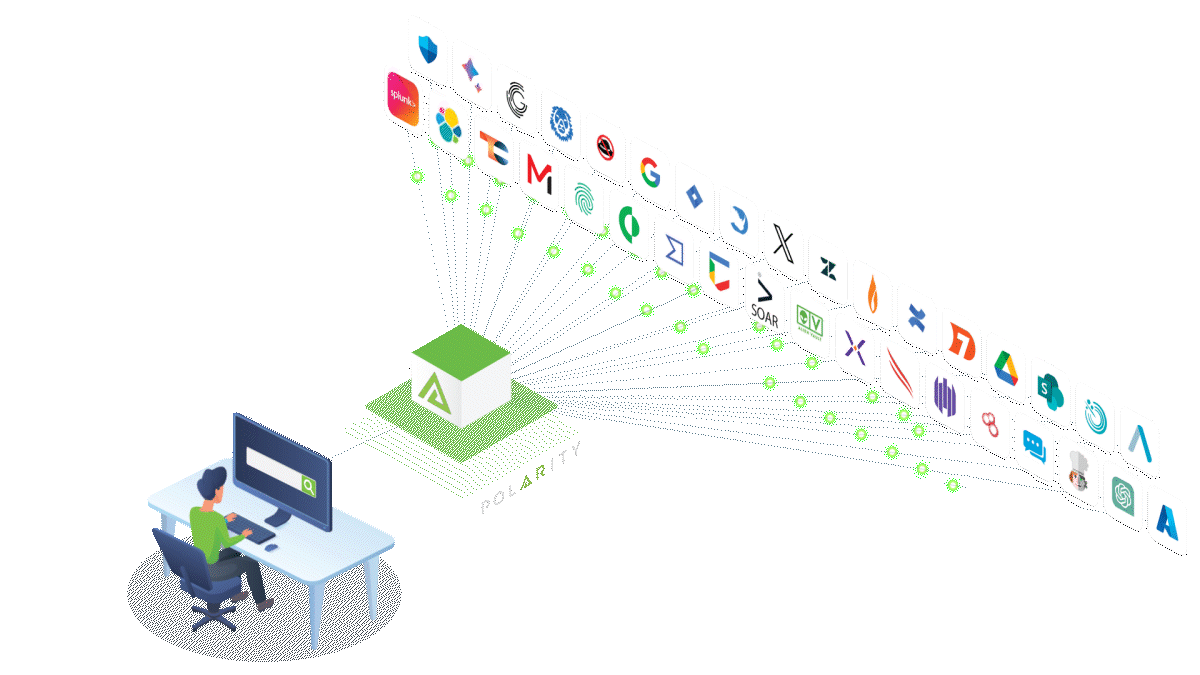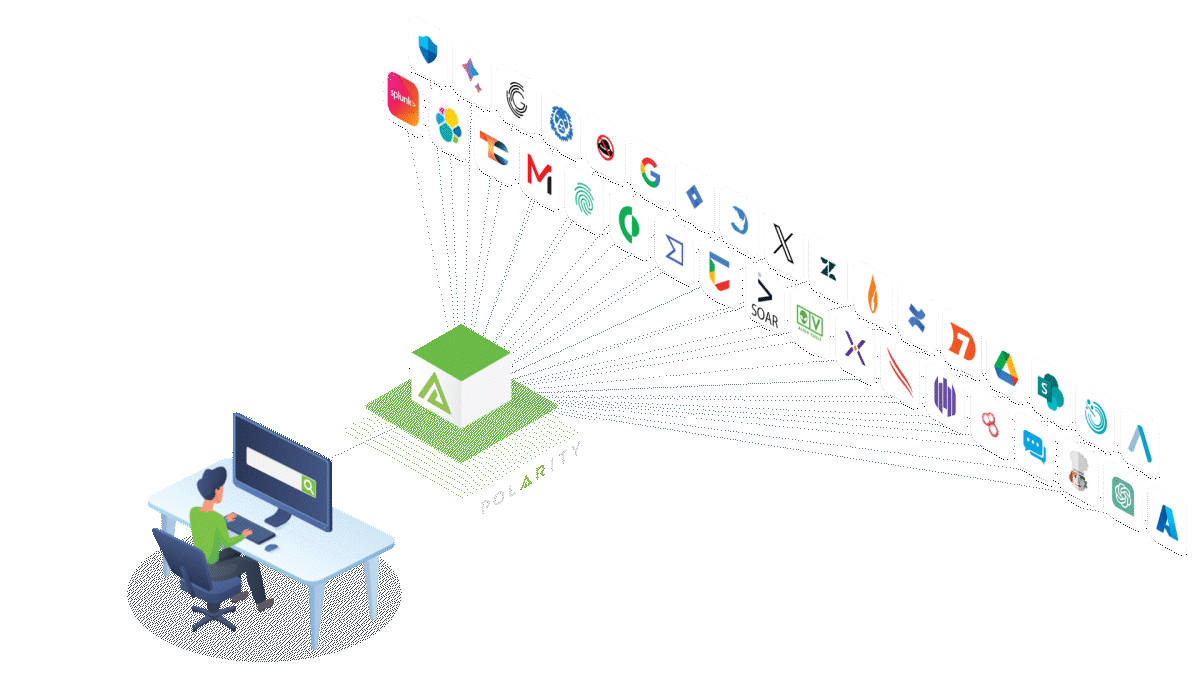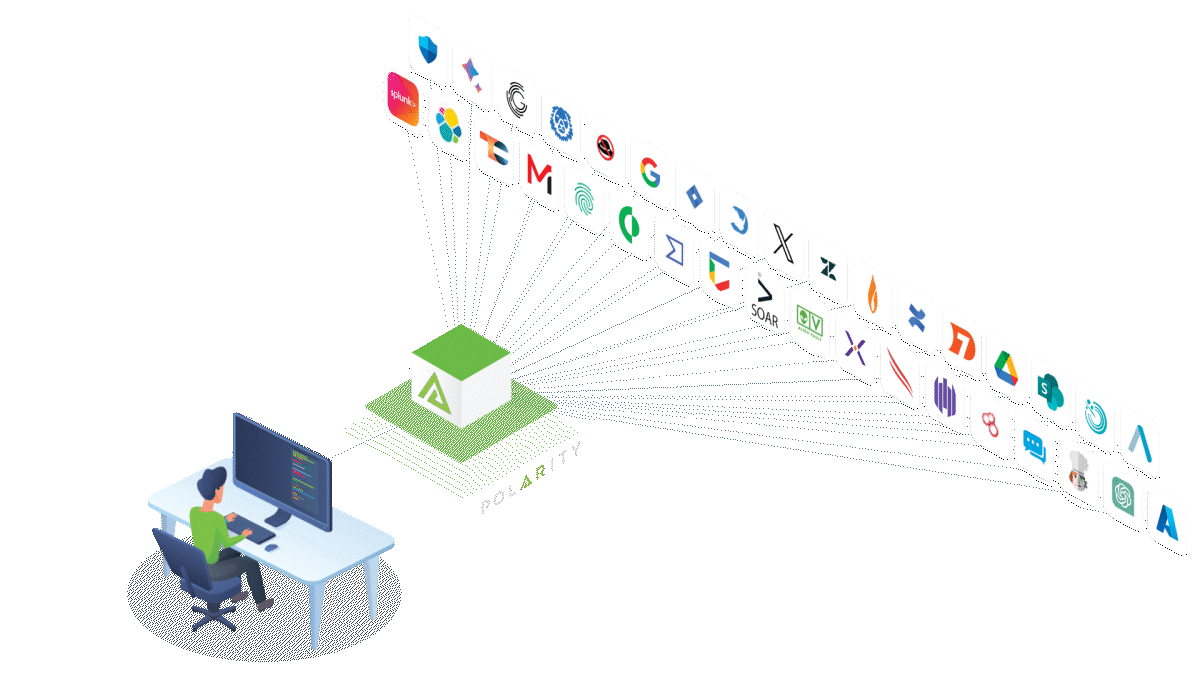
Why Use Polarity by ThreatConnect for Federated Search?
Polarity by ThreatConnect offers solutions to make federated search more convenient and secure for every organization. Some of its benefits include:
- Efficiency: Polarity can retrieve information from over 200 sources of threat intelligence and data and present it in an aggregated display for easy access and review. The aggregation of search results includes weighting for relevance and importance and contextualizing alerts, which helps with triaging.
- Convenience: This tool uses a unified interface, allowing analysts to conduct speedy threat analysis and reducing detection and response times. Features like optical character recognition (OCR) and computer vision initiate searches directly from alerts.
- Scalability and flexibility: Polarity enables users to integrate the tool within their existing platform, giving all team members access to updated information. It also allows users to include more data sources without impacting search and threat response time.
How to Use Federated Search Tools
Federated search tools may vary based on their capability, but using them is as simple as inputting a search query using specific keywords, phrases, and advanced search parameters.
From there, the tool will broadcast the query across several databases and merge the aggregated results before sorting and presenting relevant findings.
Why Trust Us?
ThreatConnect offers a smart approach to cybersecurity through threat intelligence operations, federated search, and cyber risk quantification. Our industry expertise provides customers with reliable solutions that allow them to take decisive action against cyberattack threats. Backed by over 25 industry awards, we are the preferred threat intelligence partner of 30 of the world’s largest financial institutions.
Please read about our customer stories to learn how our clients use ThreatConnect’s solutions to mitigate cybersecurity risks while maintaining operational efficiency.
Boost Your Threat Intelligence With the Experts
Leverage Polarity by ThreatConnect to address cybersecurity threats to your organization securely and efficiently. Request a demo to learn how ThreatConnect can help your organization.
