Posted
Today, we’re launching version 7.3 of the ThreatConnect TI Ops Platform. This marks an exciting occasion as we roll out this update, delivering substantial enhancements to our customers through a range of new capabilities and improvements.
Our latest updates include our new Intelligence Requirements capability, ATT&CK Visualizer v2, the latest update to ThreatConnect’s native ATT&CK navigator, and DomainTools Built-In Enrichment.
Announcing the new ThreatConnect Intelligence Requirements capability:
- Elevates insights relevant to your organization
- Directly implements requirements into the platform
- Increases your team’s efficiency
Updates in ATT&CK Visualizer v2 will enable CTI analysts to:
- Compare more than one threat Group to identify common Techniques and Sub Techniques
- Filter options to show a heat map of Prevalent Techniques
- Save navigator view and export in more formats
These updates will make the workflow for analysts much more efficient so you can find time to focus on more impactful work.
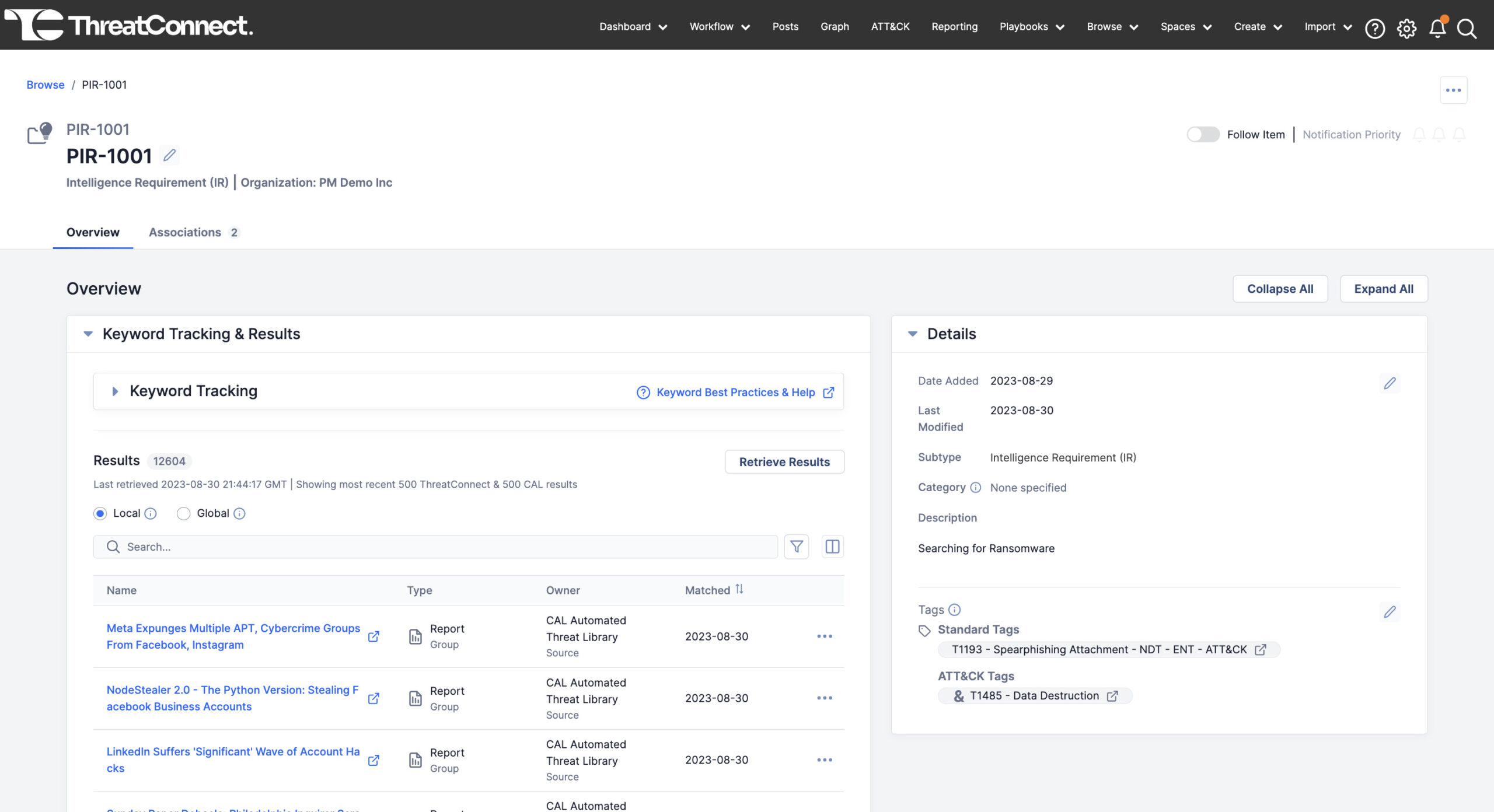
Intelligence Requirements
ThreatConnect is also proud to announce our new Intelligence Requirements capability, a new and unique capability within ThreatConnect’s TI Ops platform.
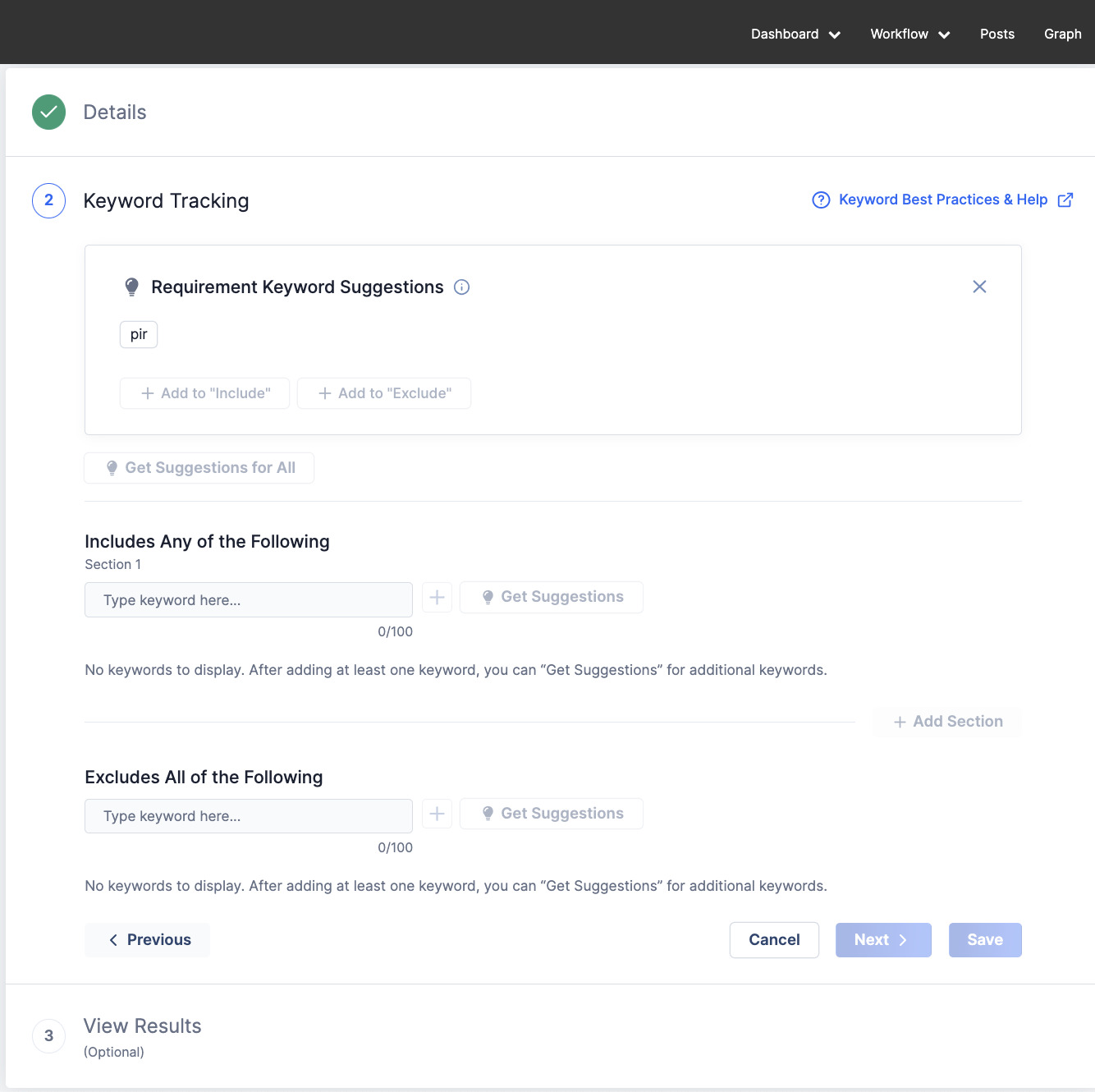
Intelligence Requirements allow CTI analysts and their customers, such as SOC and vulnerability management teams, to gain insights into the threat landscape and adversaries relevant to their organization. Intelligence Requirements helps identify, prioritize, and proactively take action against the most impactful threats, making the management and operationalization of threat intelligence easier, faster, consistent, and effective.
With Intelligence Requirements, organizations can capture their requirements in one place, automatically gather information likely related to those requirements, and enable collaboration at the planning stage of the Threat Intelligence Lifecycle. This capability sets ThreatConnect apart from its competitors, makes threat intelligence more accessible and actionable for businesses, and helps analysts be more efficient and effective.
Upcoming features will include full v3 API support, industry-related keyword suggestions, automated notifications, plus the ability to assign a requirement to an individual or group and add “Watchers” to a requirement.
Explore Intelligence Requirements with our interactive demo
Enhance Your Cybersecurity with Intelligent Requirements
Understanding and implementing robust intelligence requirements is crucial to enhancing your organization’s cybersecurity. Download our “Operationalizing Intelligence Requirements: A Comprehensive Guide,” today and learn how to operationalize intelligence requirements to enhance your cybersecurity.
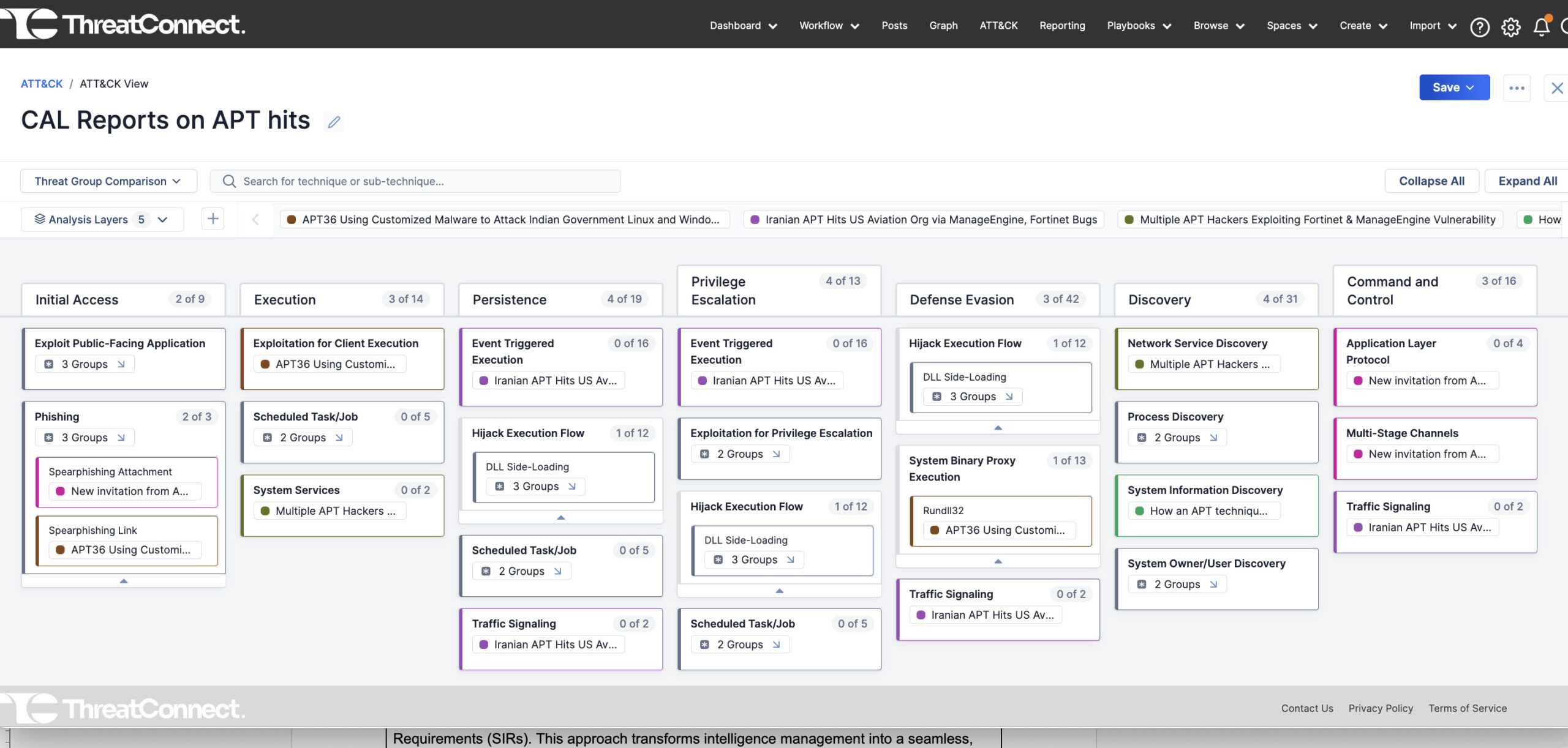
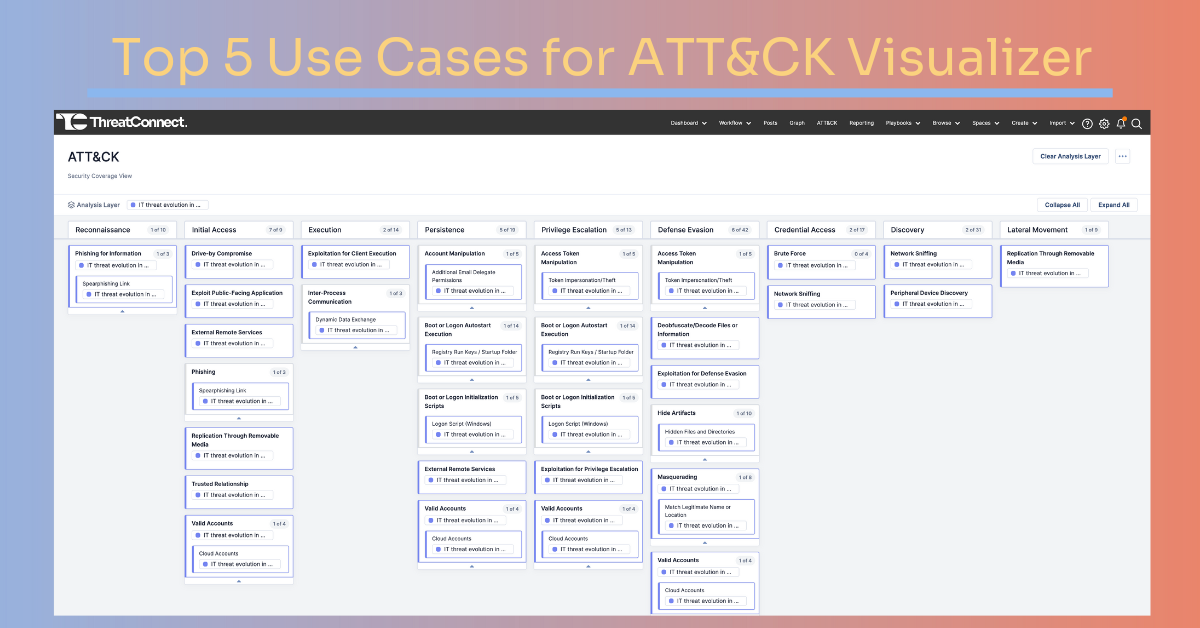
ATT&CK Visualizer v2
In July, ThreatConnect launched ATT&CK Visualizer, our native version of the MITRE ATT&CK framework. ATT&CK Visualizer enables threat intelligence analysts to visualize existing attacker tactics, techniques, and sub-techniques in order to identify adversarial behaviors for planning and organizing defenses.
In this latest release, we’re introducing noteworthy new features. Updates enable users to visually compare multiple threat groups, helping them identify shared techniques and sub-techniques. This enhances the understanding of prevalent tactics and techniques used by these groups.
Furthermore, this release includes advanced layers that allow users to generate a heat map showcasing prevalent techniques to ensure targeted defense strategies. The “Save navigator view” feature allows users to store and retrieve ATT&CK views, while updated export capabilities can be used for further analysis and better collaboration.
Upcoming features include identification of groups using similar sets of Techniques and Tactics and the ability to overlay security coverage to identify security gaps.
Not only does ATT&CK Visualizer provide organizations with a common language when referring to adversarial behaviors, but now it offers increasingly enhanced visualization. With custom saved views, users can seamlessly continue their analysis, ensuring a streamlined and consistent approach to threat evaluation and defensive strategy formulation. Security teams can quickly gather the right evidence for detecting future attacks and take necessary actions to prevent threat progression.
Explore ATT&CK Visualizer with our interactive demo
Additional Enhancements
But wait, there’s more! Beyond the enhancements and updates mentioned above, we have also included an array of enhancements, empowering analysts to conquer their tasks with unparalleled speed and effortless efficiency.
Built-in Enrichment – DomainTools
We continue to improve the experience of our customers by providing consolidated views for DomainTools enrichment. With the 7.3 release, some of the new benefits are:
- Easy configuration of DomainTools lookup
- Out-of-the-Box quick overview Intel for Host; Overall Risk Score, Domain status, Related IP address, etc
- IP Address, IP Address Country/City, ASN, etc
- Overall Risk Score, Domain status (Active/Inactive), Registrant Org, Registrar,
- Comprehensive analysis of other associated indicators
- Visualize and Import enriched threat data from DomainTools in Graph view
For more information on these new capabilities and how ThreatConnect can help your organization operationalize threat intelligence, please reach out to sales@threatconnect.com or request a demo.
Other Resources: