Posted
The Diamond Model of Intrusion Analysis (aka the Diamond Model), written by Sergio Caltagirone, Andy Pendergast (co-founder and EVP of Product at ThreatConnect), and Christopher Betz, is a cornerstone of cyber threat intelligence tradecraft. It was released in 2013 in what I believe was one of the most constructive periods of cybersecurity when other important frameworks and methodologies were also developed like VERIS in 2010, the Cyber Kill Chain in 2011, and MITRE ATT&CK in 2013 (and NIST CSF if we stretch into 2014).
What is the Diamond Model of Intrusion Analysis?
The Diamond Model is a process to document, analyze, and correlate intrusions by threat actors into an organization’s environments (network, digital, physical). It looks pretty simplistic, which makes it easy to understand, but it is extremely powerful. The Diamond Model, when put into practice “… is a mathematical framework allowing the application of game, graph, and classification/clustering theory to improve analysis and decision making.” (p.5) This enables it to be adaptable, flexible, and extensible as needed.
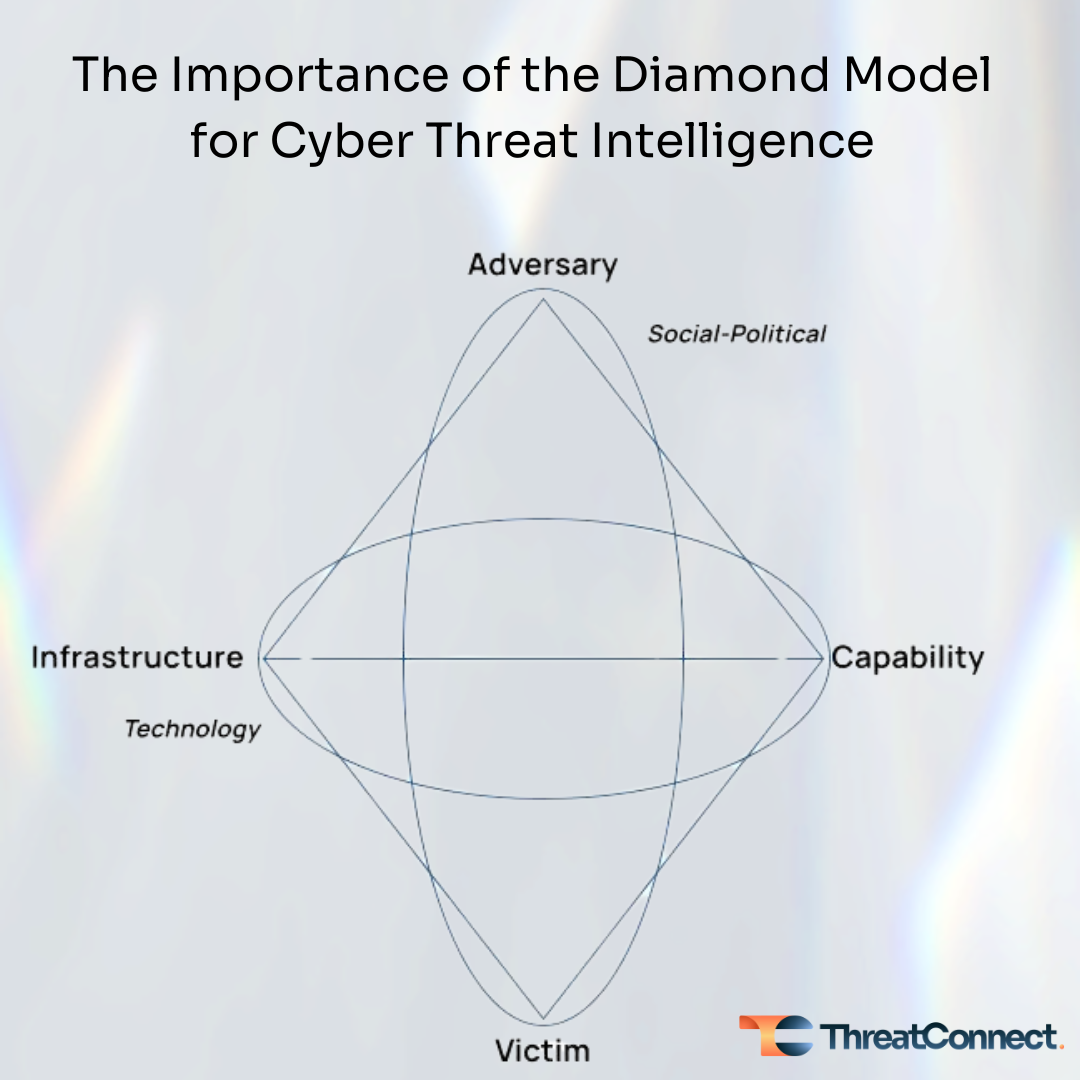
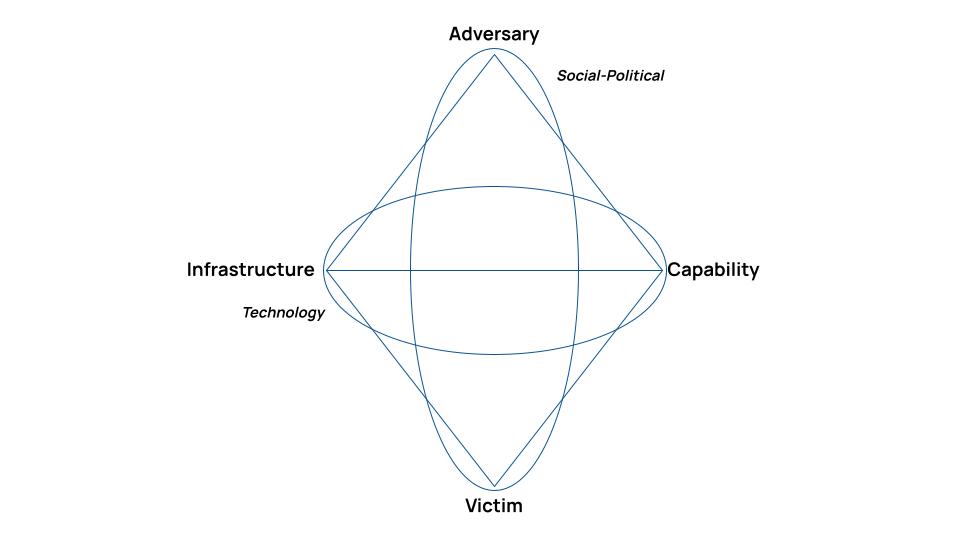
The model defines four “atomic elements” – adversary, infrastructure, capability, and victim. Connecting the edges visually makes a diamond. There are also meta-features (event, thread, and group) that support putting the model into various practices, such as the ability to link events into “activity threads” and threads into “activity groups”.
Applying the Diamond Model to Cyber Threat Intel
The Diamond Model is used to describe threat actor behaviors. The typical behavior is that a threat actor (aka adversary) “…deploys a capability over some infrastructure against a victim.” (p.7) This is what the model refers to as events. A cyber threat intel (CTI) analyst collects and analyzes events, and populates the atomic elements (Adversary, Infrastructure, Capability, and Victim) with those details. Through the analysis of this intelligence, a CTI analyst gains a broader understanding of the threat actor and how they operate.
Events can be ordered since threat actors don’t take actions in isolation, but rather they are a series of steps taken to achieve their objectives. Activity threads are constructed as adversary-victim pairs and, when combined with events, provide insights about threat actor behaviors and the most appropriate preventative or reactive response actions. Finally, events can be correlated across activity threads. One utility of this feature of the model, but certainly not the only one, is it can provide further insights about threat actors by exposing larger campaigns and identifying relationships across other events and threats. It can also highlight common or similar activity threads used in campaigns over time or by completely different actors.
The Diamond Model really frames how a CTI analyst performs their job from the intelligence that’s been collected. It goes beyond the function of aggregating, processing, and distributing indicators (you can read more in my blog here). It facilitates the systematic analysis of intel to build an understanding of clusters of specific elements of intrusion activity, which is commonly used to build profiles of threat actor behaviors, and then find the relationships across intel to expand the scope of that knowledge. All this is in service of being appropriately enabled to take action to make it harder for the threat actor to attack an organization, e.g., move up The Pyramid of Pain with your detection and protection capabilities.
Other Diamond Model resources:
- If you like Star Wars, then our blog on applying the Diamond Model to the Battle of Yavin is a great read too!
- Sergio has a class focused just on the Diamond Model here.
How ThreatConnect Leverages the Diamond Model.
The ThreatConnect TI Ops Platform is the easiest path to leveraging the Diamond Model because the Platform’s data and analytics are directly built on the concepts from the Diamond Model. This makes it easy to get up and running, putting the Diamond Model into practice.
Some examples of how the ThreatConnect Platform leverages the Diamond Model include:
- The ThreatConnect data model, which is exposed to users via the Browse screen and Threat Graph, has mappings to the atomic elements in the Diamond Model. Groups (e.g. Adversary, Campaigns, Intrusion Sets, Malware, etc) within ThreatConnect are effectively holders for clustering of indicators, techniques, and other elements related by grouping functions per the Diamond model.
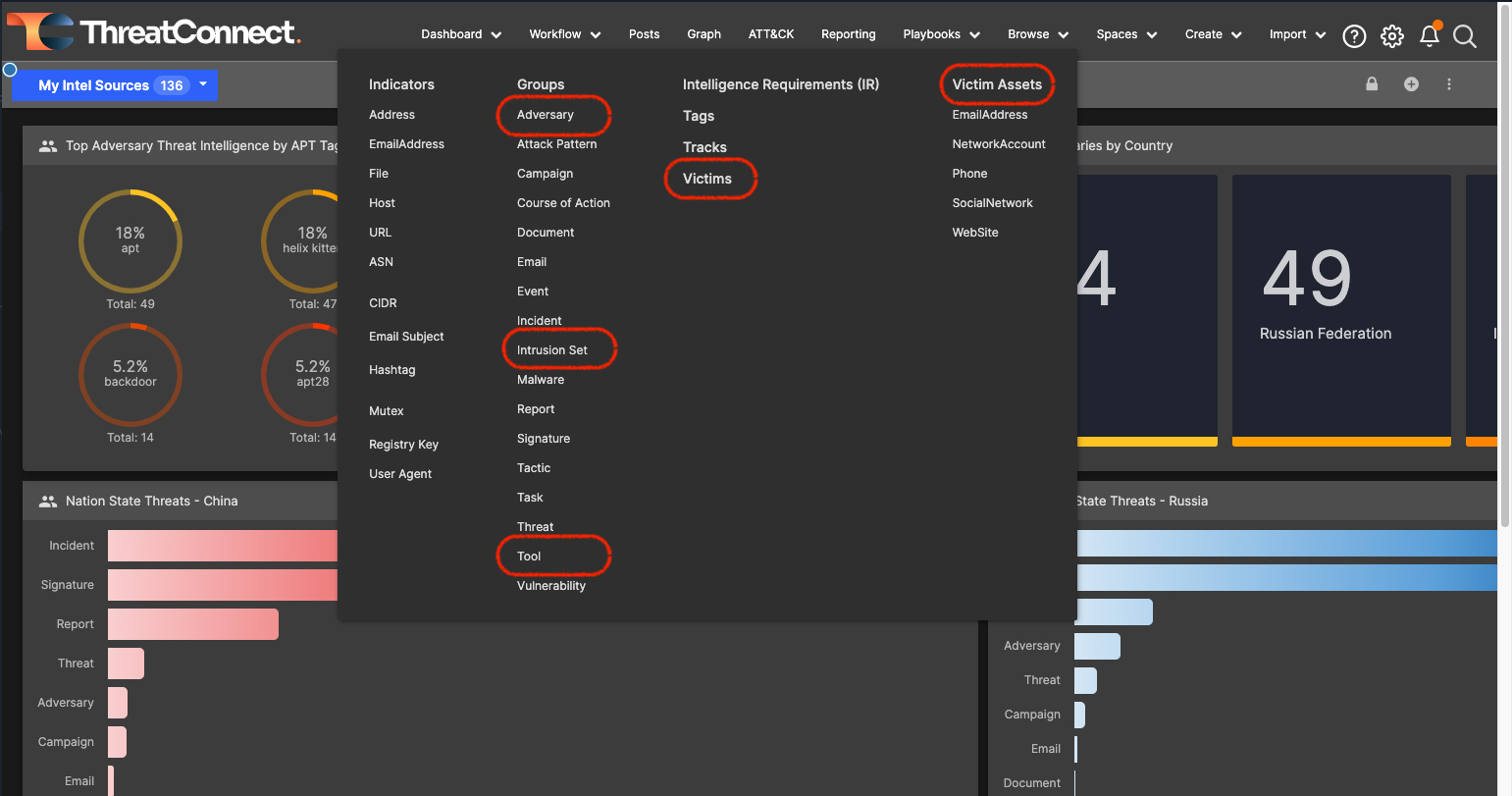
The Browse Screen
- Associations are used to link threat intel data points showing their relationships, which can be done manually by analysts or automatically through the analytics in the Platform.
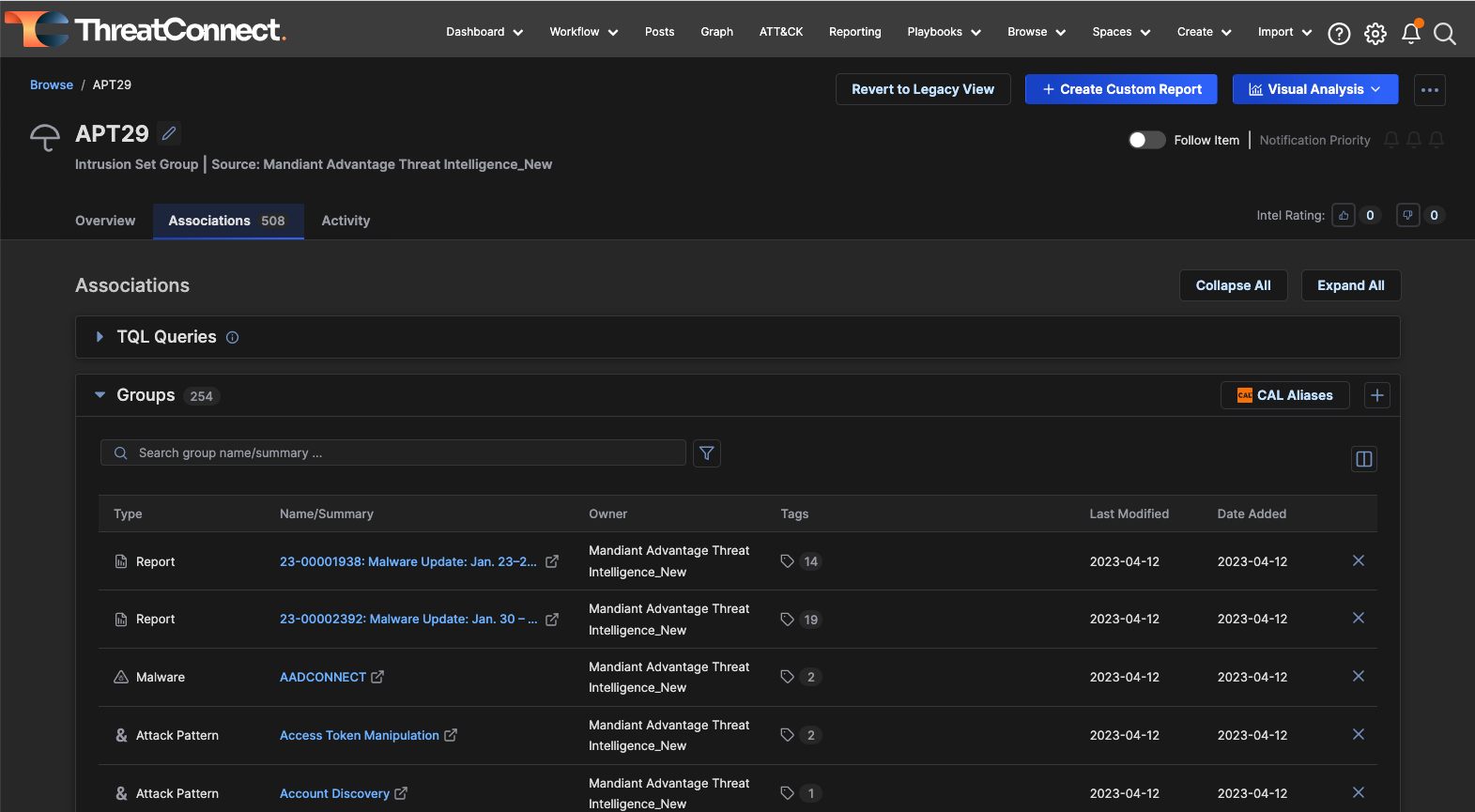
An Associations Tab
- Pivoting on data allows users to explore other threat intel data points to explore other related intel data points, find further relationships, and build out their knowledge of a threat actor or adversary. This can also be done visually and interactively via the Threat Graph feature, or programmatically with our API.
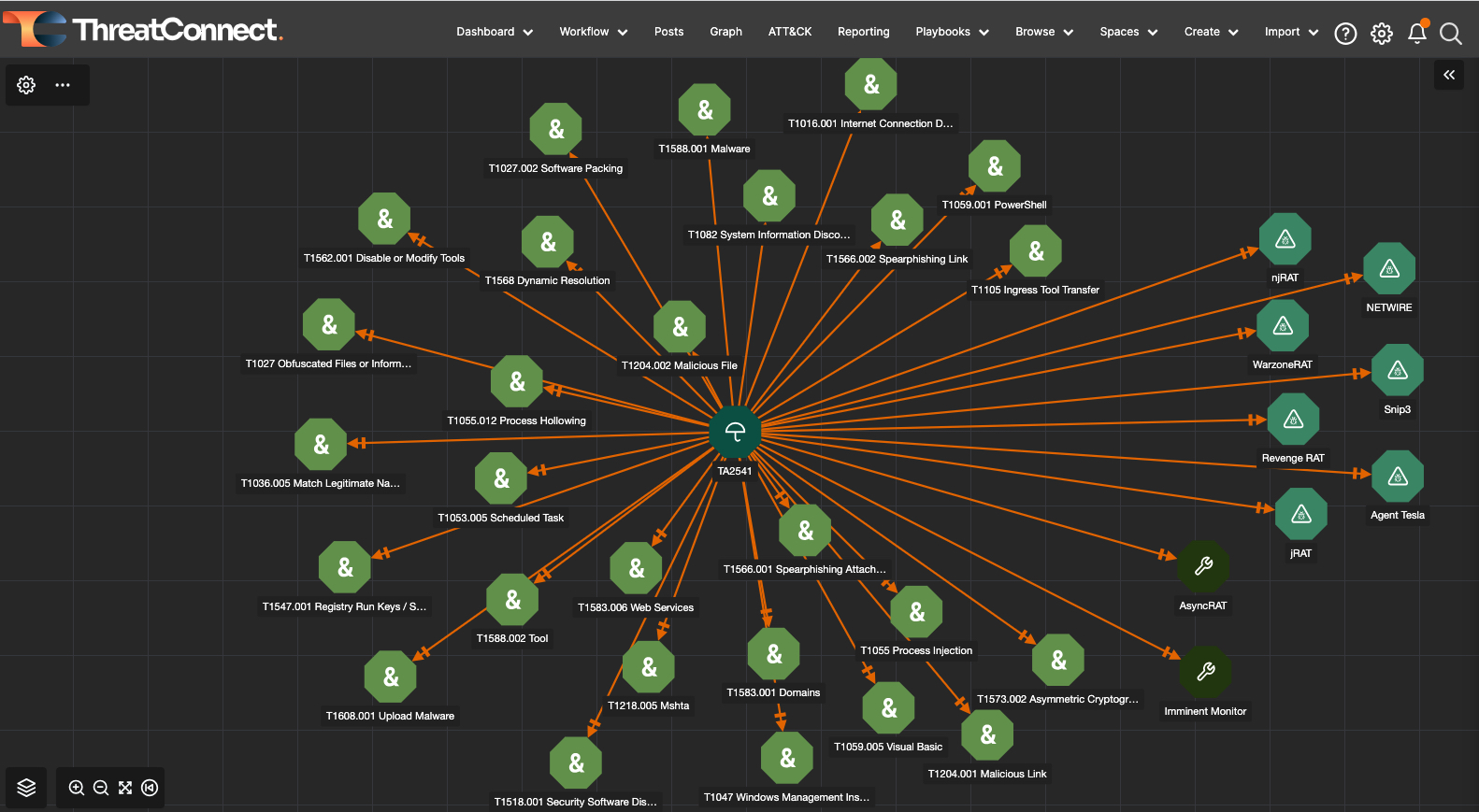
A Threat Graph
More specifics on how the ThreatConnect TI Ops Platform enables application of the Diamond Model can be found in our knowledge base.
Take the next step
If you want your CTI team to put the Diamond Model into practice, check out our interactive tour, or reach out to our experts to learn more and get a customized demo of the ThreatConnect TI Ops Platform.