Posted
In an era where cyber-attacks happen faster and are growing, staying ahead of adversaries is a necessity but very challenging. Quickly assessing suspected malicious files and URLs is vital for reducing the time it takes to detect and respond to cyber threats. Understanding the adversary’s tactics, techniques, and malware infrastructure can significantly improve your organization’s defenses. Organizations must understand how their enemies operate and the type of malware they use and leverage this knowledge to bolster defenses. Yet, the manual process of analyzing files and URLs is cumbersome and inefficient, leaving security analysts overwhelmed.
ThreatConnect and VMRay
Enter ThreatConnect and VMRay. We’re pleased to announce an upgraded integration as well as a brand new integration between ThreatConnect’s Threat Intelligence Operations (TI Ops) Platform and VMRay. The combined solutions enable security operations and cyber threat intelligence (CTI) teams to scale their file and URL analyses, converting raw data into actionable intelligence, and help them better understand adversaries and take proactive actions to fortify defenses.
By combining ThreatConnect’s robust TI Ops platform with VMRay’s advanced malware sandboxing and URL analysis, security teams can scale their analysis efforts dramatically and produce custom intelligence tailored to threats targeting their organization. This means stronger, more proactive defenses that adapt as quickly as adversaries do.
The Power of Integrated Solutions
Automation is at the heart of this integration. Playbook automation in ThreatConnect streamlines file and URL analysis processes, ensuring that your security team can handle large volumes of data without being bogged down by manual tasks. The latest version of the VMRay Platform App for ThreatConnect automates the submission of files and URLs for analysis and processes the results, saving analysts hours of effort. The data—whether it’s file hashes, IP addresses, domains, or URLs—is seamlessly integrated into the ThreatConnect Platform, providing enriched context for better decision-making.
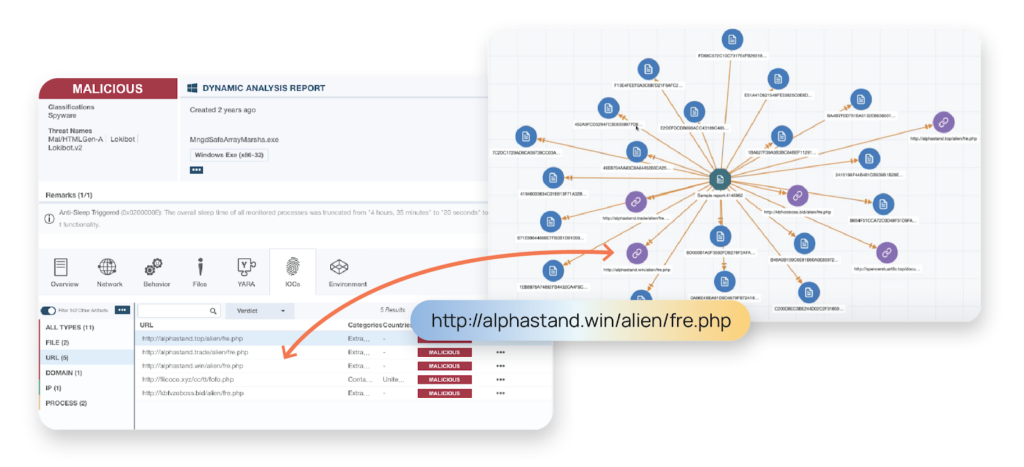
Utilize new intel from VMRay analyses to enhance your detection and prevention tools. By incorporating this data into ThreatConnect, you can optimize tools like SIEMs, endpoint protection, and network and cloud security. How? The new VMRay Threat Intelligence Job App automates the ingestion of threat intelligence from files and URLs analyzed by the VMRay Platform into ThreatConnect TI Ops. This ensures that analysts always have the latest insights from ongoing attacks, allowing them to leverage this intel for enhanced threat detection, prevention, and response.
But wait, there are even more benefits!
Enriching context is crucial for understanding the bigger picture. With these integrations, analysts get detailed insights into malware families, indicators of compromise (IOCs), phishing emails, and threat actors, all within one platform. The automated enrichment of intel adds context, improving its fidelity. This is particularly useful in phishing attack analysis, where understanding the context can make the difference between an overlooked threat and a crucial insight.
Leveraging context from ThreatConnect and VMRay to triage, prioritize, and respond to alerts more effectively. This ensures that security defense tools—like SIEM, XDR, EDR, and NDR—are operating at their full potential.
With new intel from VMRay analyses, threat hunting becomes far more effective. This integration enables your team to actively search for malware within your environment, improving overall security posture.
Take your cyber defense to the next level
To learn more about the latest integrations between ThreatConnect and VMRay, visit the ThreatConnect Marketplace. If you’d like to learn more about ThreatConnect’s TI Ops Platform, check out our interactive tour or reach out to one of our experts. To learn more about VMRay’s Advanced Malware Sandbox and URL Analysis Platform, reach out to a VMRay expert today.

