
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.
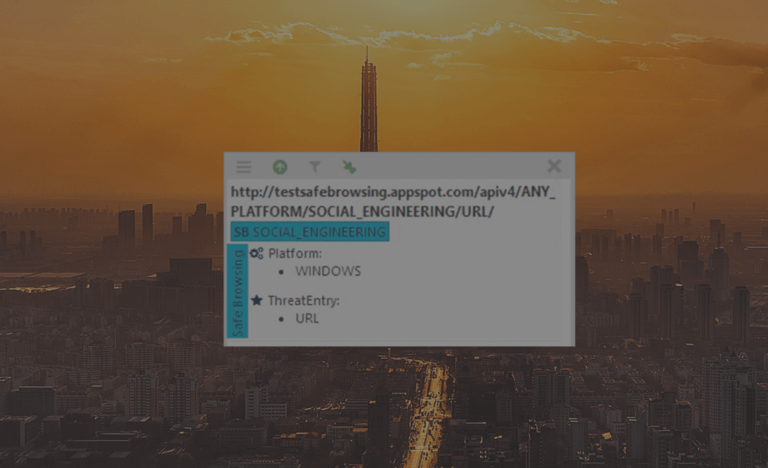
Always know if that URL is Malicious
Did you know that not every website you visit, or link that you might click on is safe? Well I hate to break it to you, but a decent amount of them are not. To mitigate that, Google has released their database of URLs that they consider malicious in some way, called Google Safe-Browsing. This […]
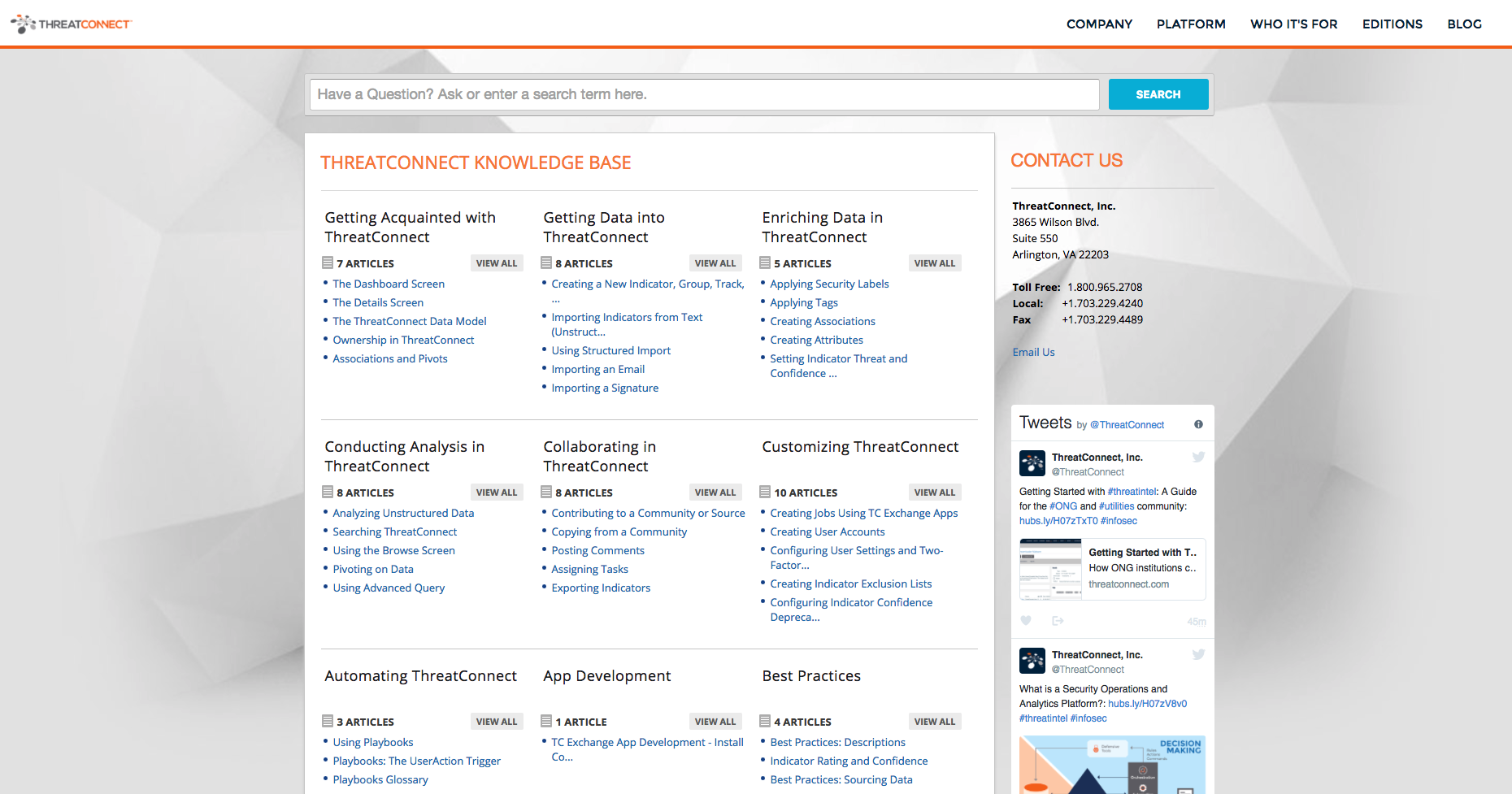
Did You Know We Have A Knowledge Base?
From guides to training videos and best practices, ThreatConnect’s Knowledge Base has everything you need to use the Platform to its fullest potential. Did you know that ThreatConnect has a knowledge base? What is a knowledge base, you ask? And why is it awesome? Read on… First, let’s define it: a knowledge base is a […]

Remembering Network Ports and Services
When systems communicate on a network they often use one or more of the available 65,536 TCP/IP ports. https://en.wikipedia.org/wiki/List_of_TCP_and_UDP_port_numbers Such service names and port numbers are used to distinguish between different communication purposes and successfully remembering the association can be the key to troubleshooting a network or security issue. Many IT professionals experience moments where they […]
When Dumpster Fires Make You WannaCry
Stepping back and taking stock of WannaCry lessons learned During the afternoon on Friday May 12th, WannaCry ransomware infections broke out at several UK National Health Service (NHS) medical facilities and Spain’s telecommunication company, Telefonica. By the early evening, the attention to WannaCry had reached a fever pitch. While kill switches for the malware were […]
Getting Started with Threat Intelligence: A Guide for the ONG Community
Getting Started with Threat Intelligence: A Guide for the ONG Community How ONG institutions can get started with ThreatConnect to gain context about threats The utilities vertical, specifically oil and gas (ONG) is a complicated one, especially when it comes to information security. Each company has multiple endpoints that they need to protect – and […]
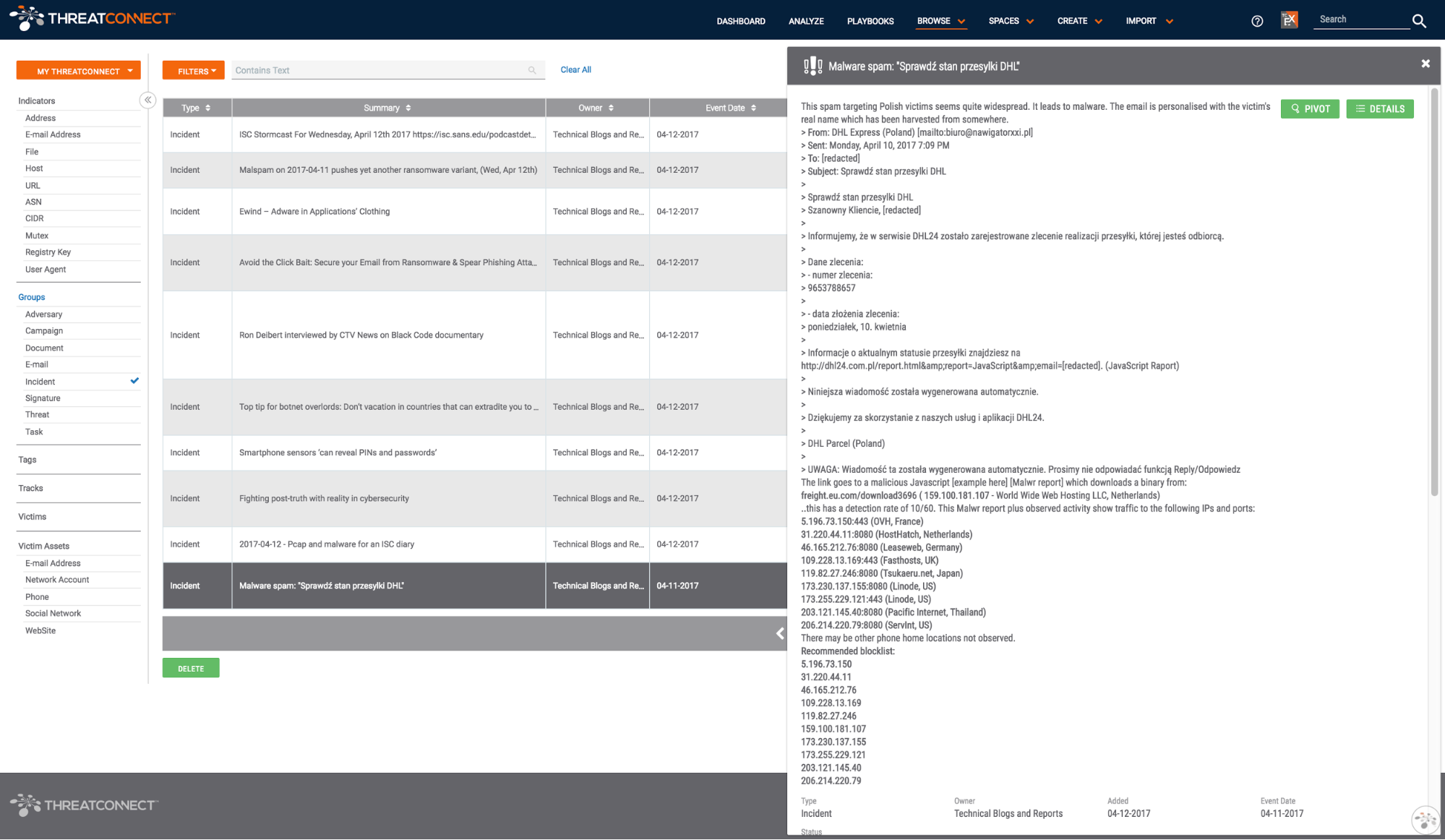
The Technical Blogs and Reports Source
I’ve got 99 problems, but keeping up with the news isn’t one Collecting is the sort of thing that creeps up on you. ~Paul Mellon “Did you see that latest report on [ransomware, ShadowBrokers, insert topic du jour here]?” Keeping up with the latest research in the field is a key task for any […]
Parlez-vous Fancy?
ThreatConnect Reviews Potential Fancy Bear Activity Targeting the French Election Runoff In the run up to the French election runoff between Emmanuel Macron and Marine Le Pen, ThreatConnect reviews intelligence suggesting domains spoofing Macron’s En-Marche.fr website are associated with Russian cyber activity. Pour lire ce blog en français, cliquez ici. In the wake of a […]

Getting Started with Threat Intelligence: A Guide for Retailers
How any size retailer can get started with ThreatConnect to gain context about threats Are you a retailer? Just getting started with threat intelligence? Then you are going to want to read this — our first post in a series directed toward specific business verticals. Retail is a vast ecosystem that connects merchants to suppliers, […]
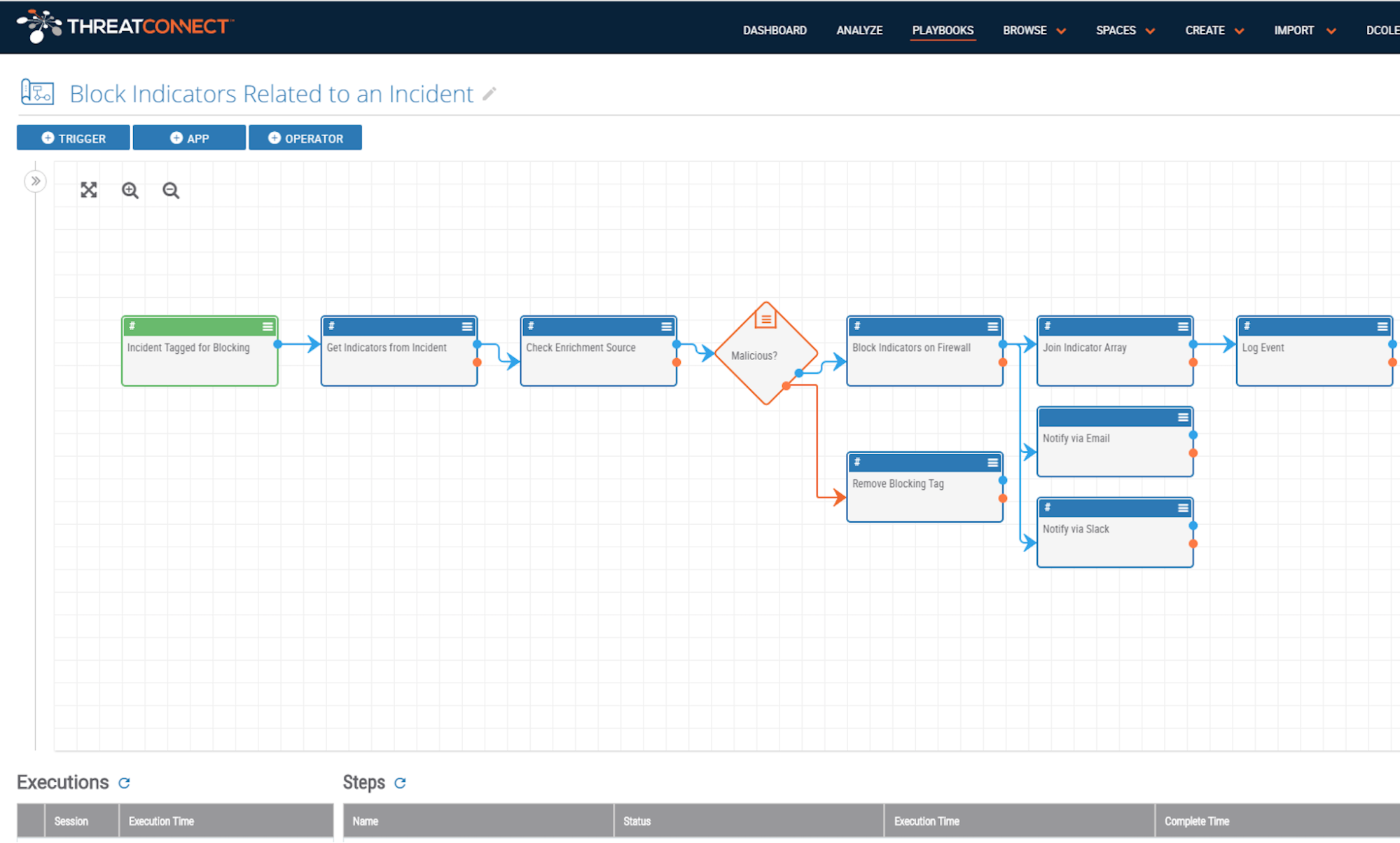
Save Time and Accomplish More with Playbooks
ThreatConnect Playbook Actions: Be More Efficient and Gain Control with Automated Actions ThreatConnect’s Playbooks feature automates almost any cybersecurity task using an easy drag-and-drop interface – no coding needed. ThreatConnect uses Triggers (e.g., a new IP address Indicator, a phishing email sent to an inbox) to pass data to apps, which perform a variety of […]

Share The Love: Using ThreatConnect as a Threat Intelligence Sharing Platform for ISACs, ISAOs, and their Members
How ISACs, ISAOs, and their members use ThreatConnect’s threat intelligence sharing platform effectively to share threat Information For those who read “share the love” and hoped this was a post about reggae music, and its rhythmic message of peace, love, and unity, my apologies. This post is actually about the smooth sound and power of […]

The FORCE of STIX & TAXII: Why STIX & TAXII are so Important to Financial Services Companies & EMEA
The Force of STIX & TAXII Use the force, Luke. If your cybersecurity team were given a common threat intelligence language and transport method that surrounded, penetrated, and bound you in an impressive-galactic-sort-of-way to other fighters of cybercrime, would you take it? The free, open-source tools, STIX and TAXII are doing just that. With the […]
Measuring the Detection and Response Gap
Measuring the Detection and Response Gap Despite efforts to stockpile the best technology and assemble an army of defenders, today’s security organizations struggle with inefficiencies. Threat actors are getting more efficient at compromising networks, taking only minutes or less to compromise systems. Organizations, meanwhile, are taking weeks (or longer) to discover breaches – and oftentimes […]
