
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.
ThreatConnect 5.7 Shows Advancements in Playbooks Capabilities
Juggling Priorities and Countless Orchestration Use Cases? We’ve Got Your Back Automation and Orchestration are terms that are thrown around interchangeably and claimed to be supported by just about every product offering out there. The advancements in technology required to truly support scalable workflows should not be understated. Remember those connect-the-dot games we used to […]
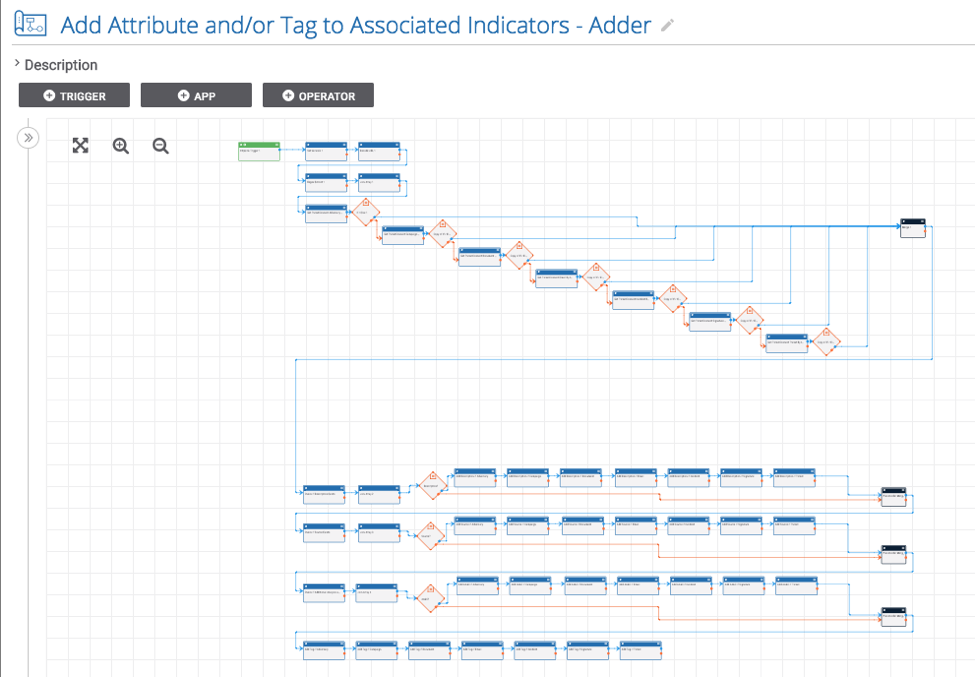
Playbook Fridays: Associated Indicator Metadata Creator
Easily add metadata (in the form of certain attributes and tags) to the all of the Indicators associated with any Group ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can occur […]
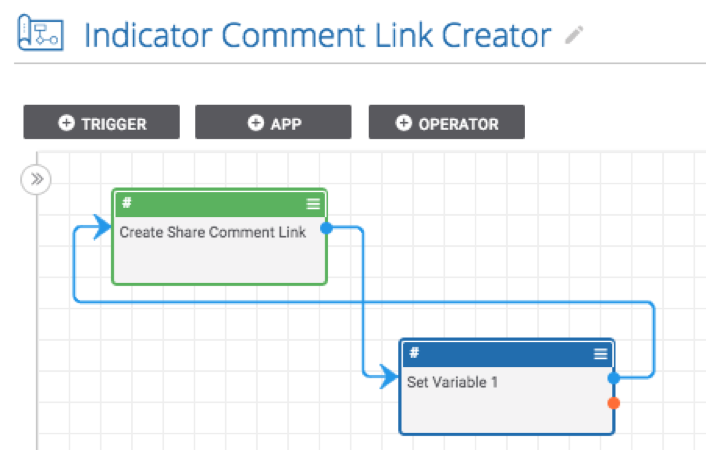
Playbook Fridays: Group and Indicator Comment Link Creators
Create and copy the link to an Indicator or Group in two clicks ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can occur consistently and in real time, without human intervention. […]
Playbook Fridays: Robtex ASN Query and Robtex IP Query
Simplify the process of pivoting through data and expanding an investigation using Robtex ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can occur consistently and in real time, without human intervention. […]

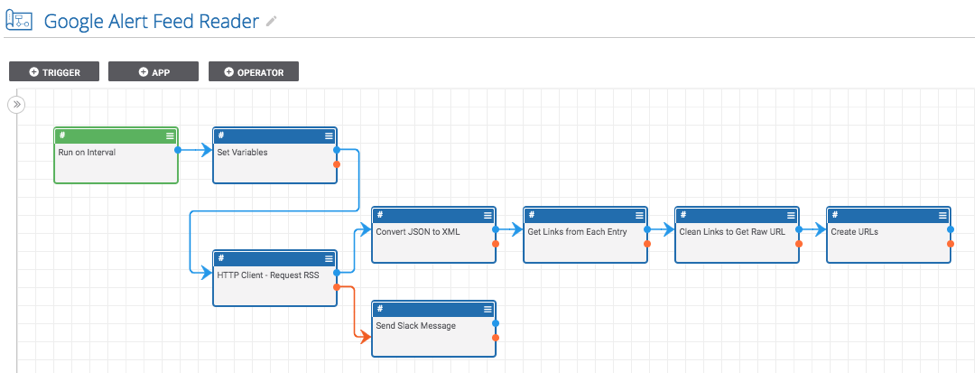
Playbook Fridays: Google Alerts RSS Reader
Read a Google Alerts RSS feed and create indicators from the links ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can occur consistently and in real time, without human intervention. Once […]
Top 5 ThreatConnect Resources for Malware Analysis
Malware Analysis. Some may say it’s the most exciting part of the job, right? You have something you know is bad. What’s it do? How’s it run? Where’d it come from? These are questions we all want to know the answers to. And because technology is a beautiful thing, we have the ability to find […]
Playbook Fridays: QRadar Tag Search in ThreatConnect
Correlate data in QRadar with intelligence in the form of Indicators in ThreatConnect ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can occur consistently and in real time, without human intervention. […]
ThreatConnect Introduces Version 5.6
More Results, More Analysis, More ROI Earlier this quarter we announced the release of ThreatConnect version 5.6. It’s centered around making our platform even more effective for user collaboration and analysis. Having what you need exactly when you need it is critical across security operations, but especially when dealing with threat intelligence. So much so, […]

ThreatConnect achieves ISO 27001:2013 certification
Continuing our commitment to protect our customers’ data What is ISO 27001? ISO 27001 is an internationally recognized standard defining requirements for a systematic approach to managing sensitive information, also known as an information security management system (ISMS). But what’s an ISMS? Think of an ISMS as the blueprint for how we identify, assess, and […]

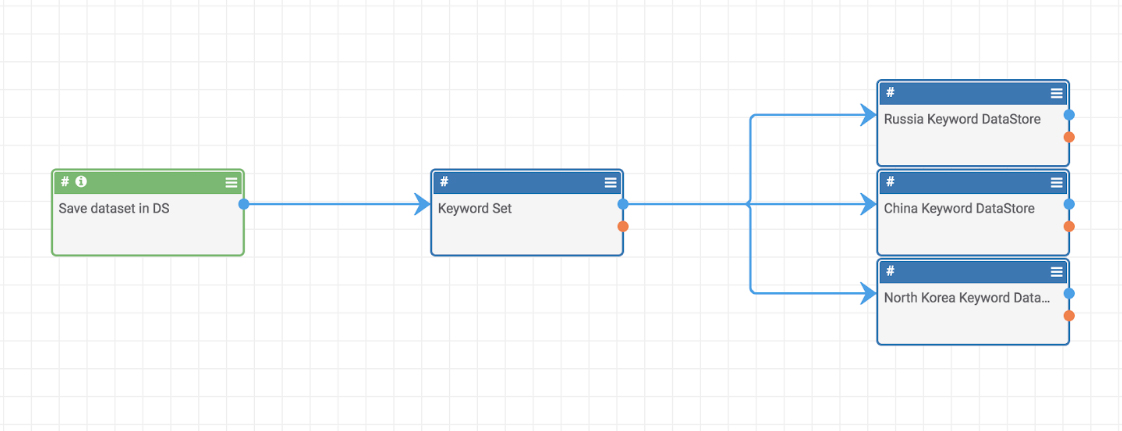
Playbook Fridays: Document Parsing and Keyword Scanning/Tagging
Automatically tag the documents with keywords and focused areas of interest without human intervention ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can occur consistently and in real time, without human […]
How to Choose the Right Threat Intelligence Platform for You
Understand it’s “job” and what you and your team need The first step to choosing the right threat intelligence platform (TIP) for you is to figure out what you actually want the TIP to do. One pitfall that security teams often fall into is that they approach the selection with a checklist of criteria, without […]

We’ve built an actual HUD, not a dashboard.
The time has come for the official release of the HUD. As of today, the feature users have been asking for is officially out of beta. In this post, we share the reasons users wanted the HUD to be real-time, what problems it solves, and how it works. Why Since data awareness and improving decisions […]
