Posted
Read a Google Alerts RSS feed and create indicators from the links
ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can occur consistently and in real time, without human intervention.
Once in a while, there is a Google search that turns up a lot of malicious or compromised domains. When this happens, it is helpful to use Google Alerts to create a RSS feed of websites matching the search. This Playbook will then read from the RSS feed on a regular interval and create all of the urls as indicators in ThreatConnect. This is extremely useful for automating the threat hunting process especially when there is an outbreak of compromised hosts that can be easily discovered using a Google search.
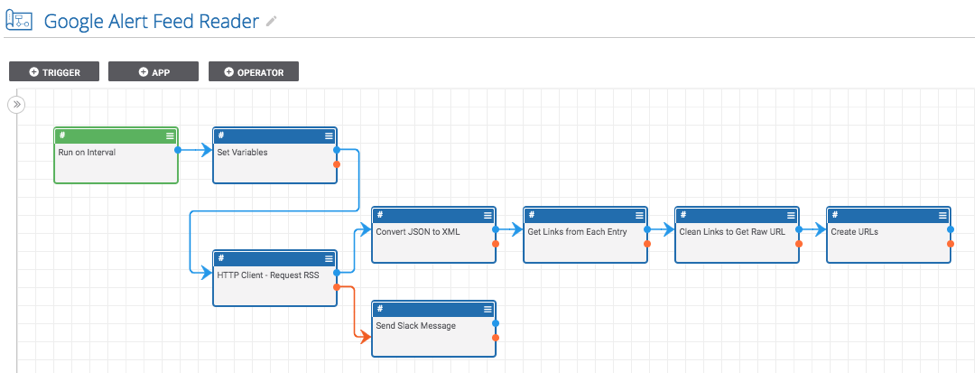
ThreatConnect developed this Playbook to read a Google Alerts RSS feed and create indicators from the links.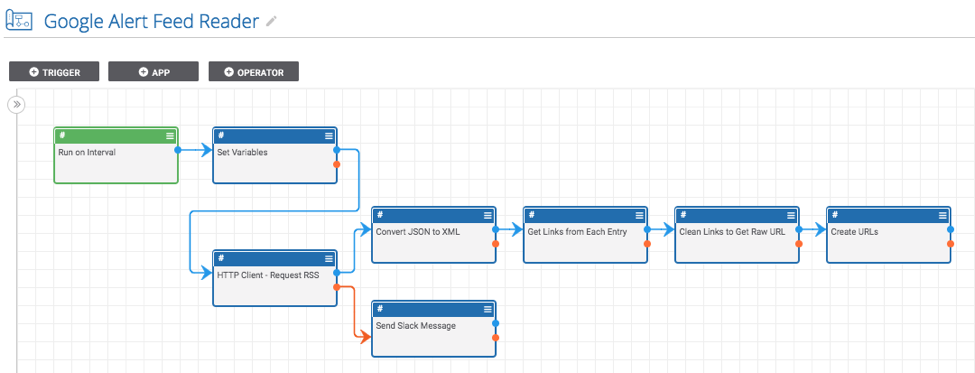
Getting Started
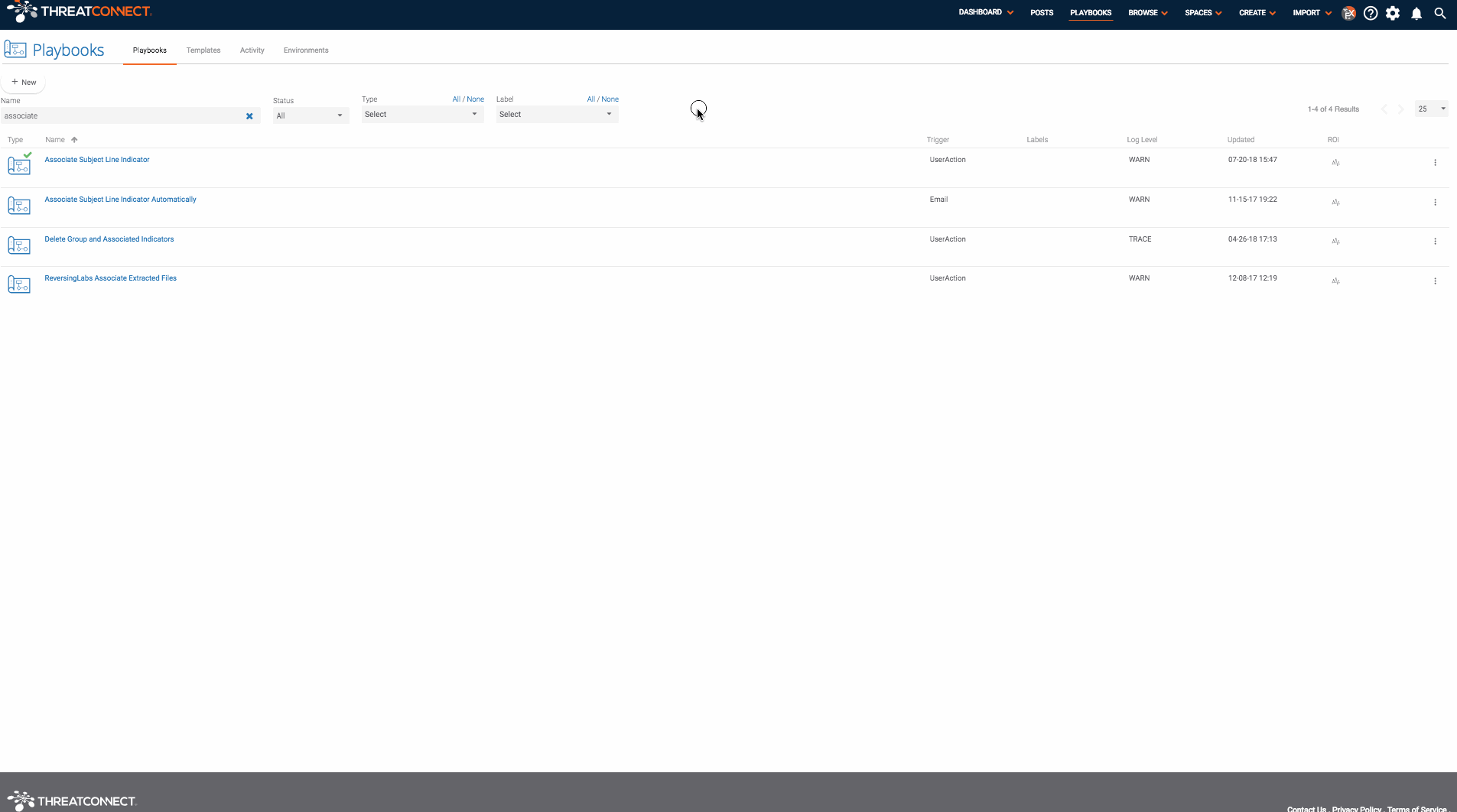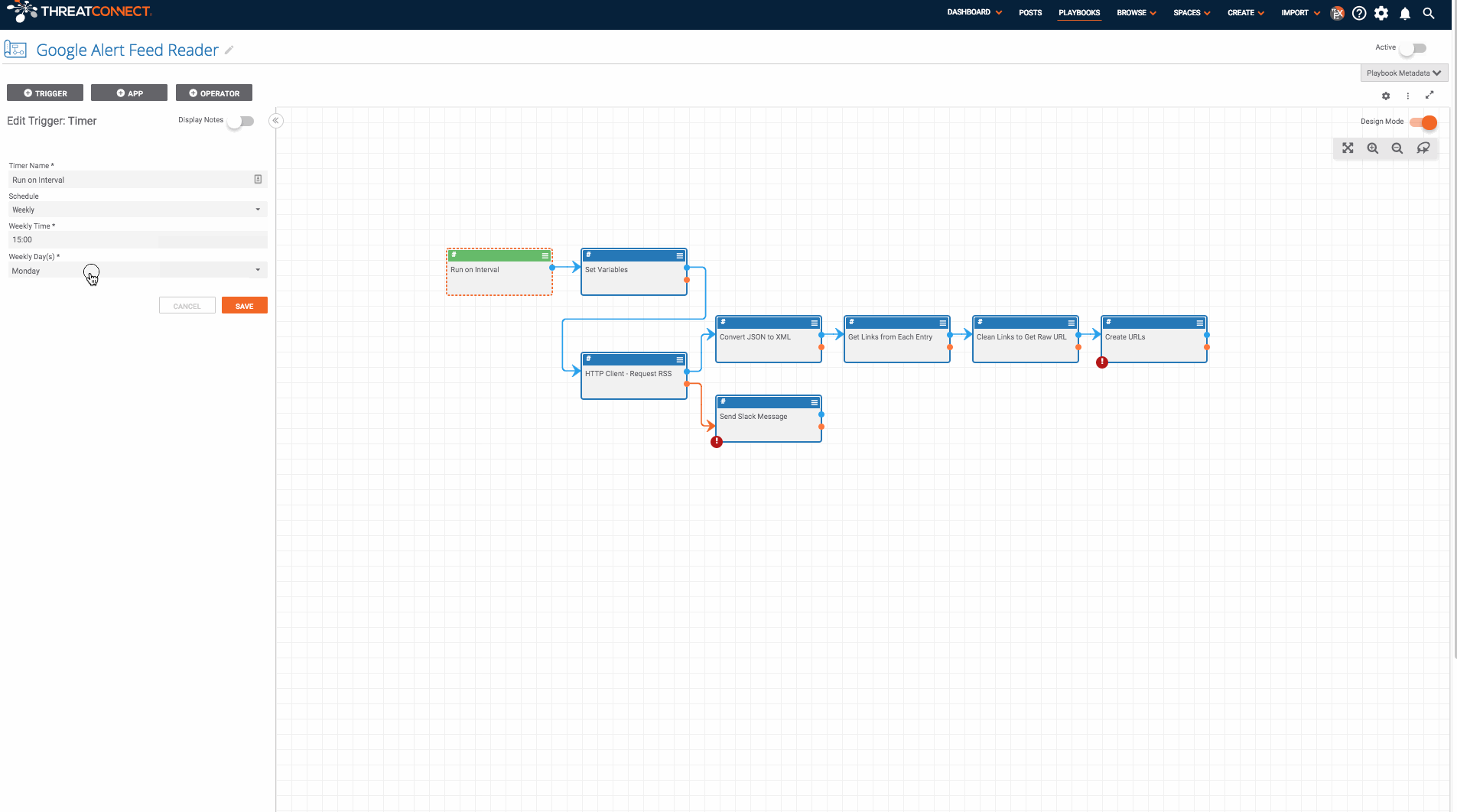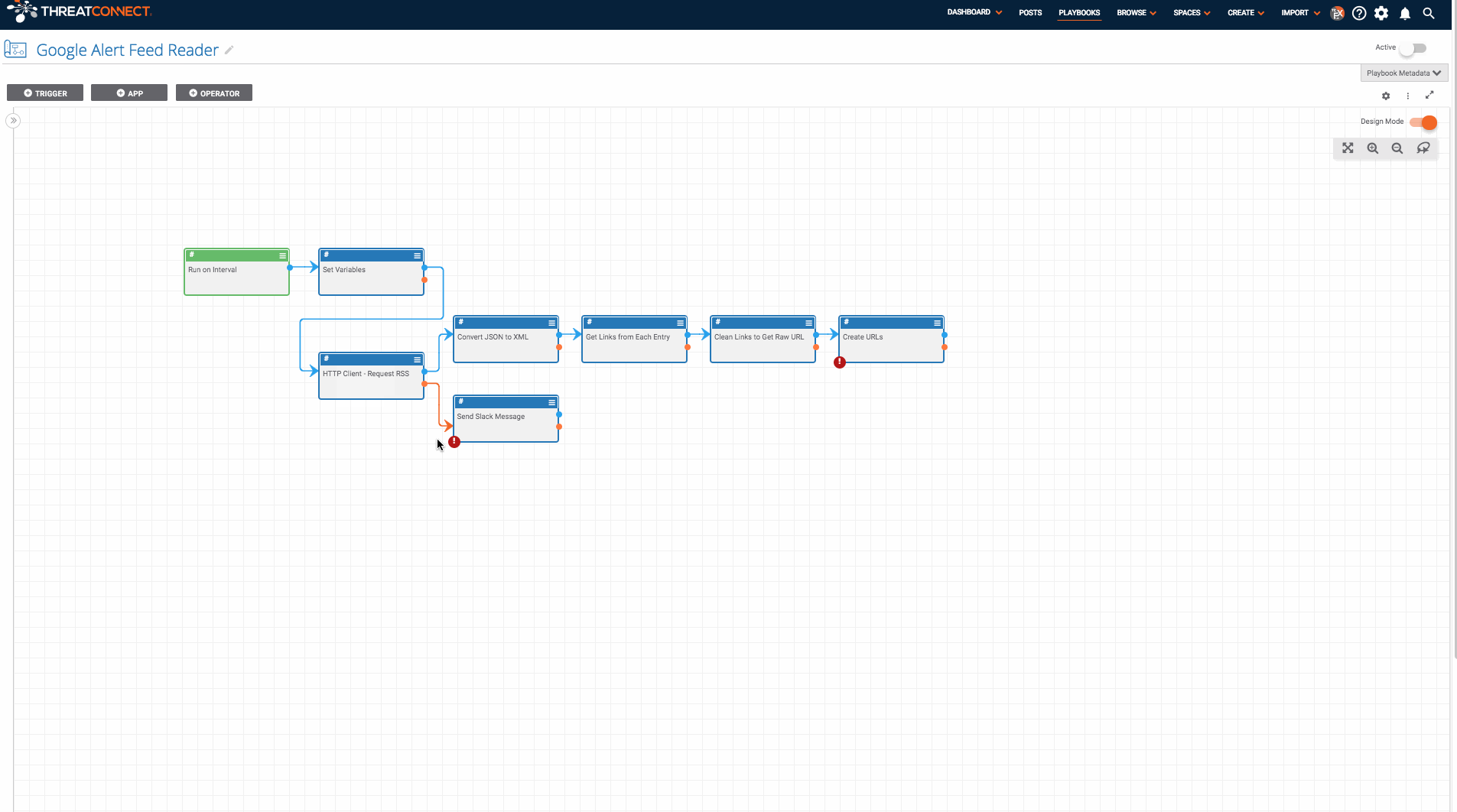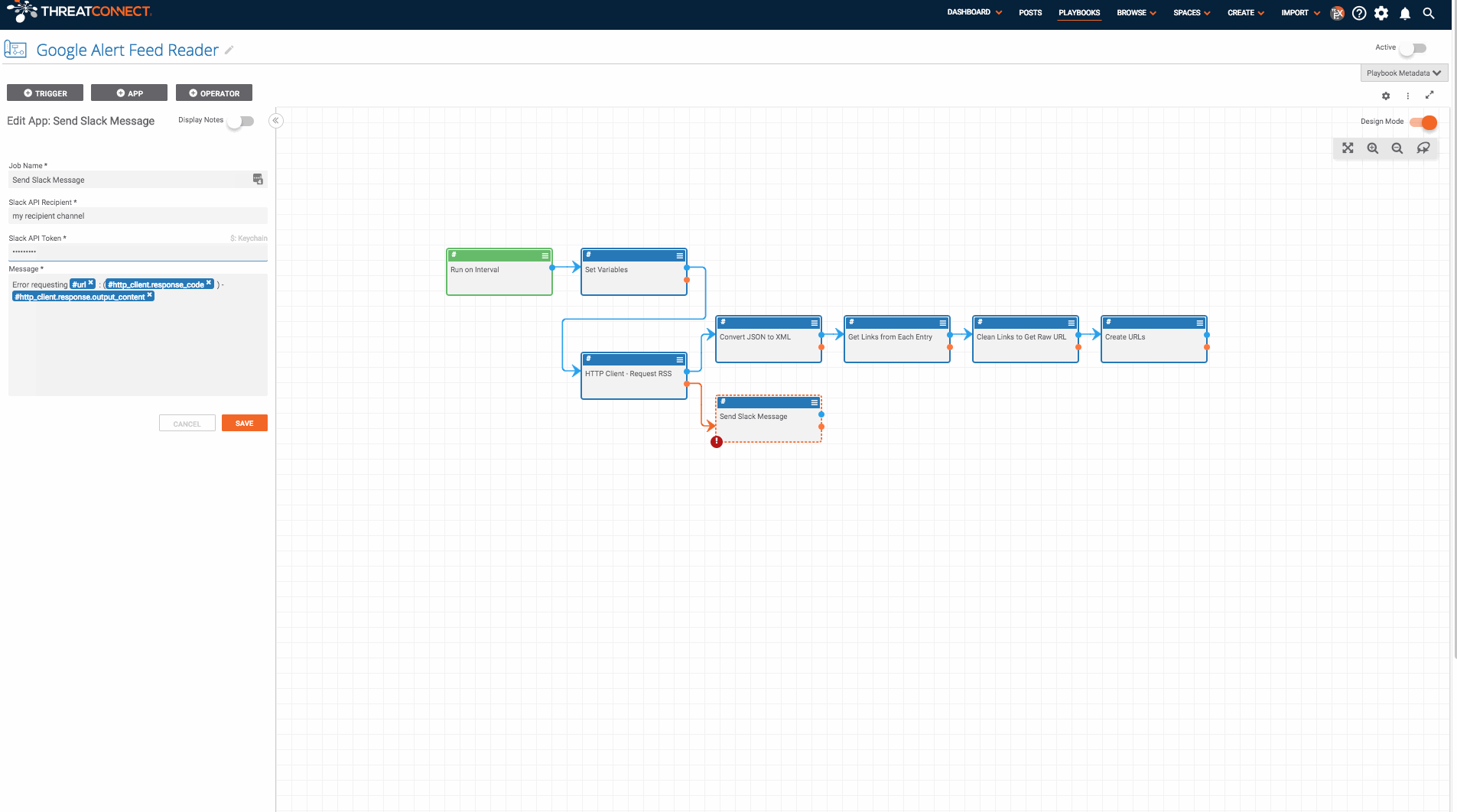
There are two main parts to this system: a Google alert RSS feed and this Playbook.
There are details and instructions for setting up a RSS feed for a Google alert here: https://thenextweb.com/news/google-alerts-regains-rss-delivery-option-it-lost-after-google-readers-demise
Once you have a Google alert RSS feed setup, you can install and use the Playbook. To do this, go to https://github.com/ThreatConnect-Inc/threatconnect-playbooks/tree/master/playbooks/google-alerts-rss-reader and download the “Google Alert Feed Reader.pbx” file. Now, import it into ThreatConnect. Go to the “Playbooks” tab in ThreatConnect and click “New” > “Import” (on ThreatConnect versions before 5.7, you can just click the “Import” button). Then import the Google Alert Feed Reader.pbx file. Next, set up the Playbook.
To do this:
- Double click on the “Run on Interval” app and specify how often and when you would like the app to run.
- Double click the “Set Variables” app and provide the URL to a Google Alerts RSS feed. Also, set the confidence and threat ratings you would like to apply to the created indicators.
- Find all of the apps which have errors and fill in the missing fields (which include parameters like the ThreatConnect owner and slack API token).
- Turn it on and run the Playbook!