Posted
Correlate data in QRadar with intelligence in the form of Indicators in ThreatConnect
ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can occur consistently and in real time, without human intervention.
Ground truth is one of the most important sources informing threat intelligence. A key source of this truth is what’s happening in the SIEM- QRadar in this case. Knowing this, we needed a way to the correlate data in QRadar with intelligence in the form of Indicators in ThreatConnect. This Playbook was created to provide a statistical event count, along with a snapshot of the top 5 events by frequency. Memorializing the results in an attribute on an Indicator.
Why You Want to Use it:
- Because it easily fits into what you’re already doing! The Playbook triggers off a tag, making it very simple to incorporate into an analyst’s regular workflow
- Customization ensures you can make each step relevant to you and your goals. The Playbook itself leverages modular components that make it easy to tweak and modify the underlying queries without affecting the larger Playbook
- You’ll learn what’s important to your individual organization. Correlation of indicators with the ground truth of a SIEM helps highlight how relevant those indicators might be to each specific customer
- You’ll be provided with another set of data that will help with prioritization in the future. The event data can be queried via TQL to be prioritized for further analysis
Let’s walk you through the components of this Playbook in the Platform. For an in depth walkthrough, view the video below, or keep reading for a high level overview.
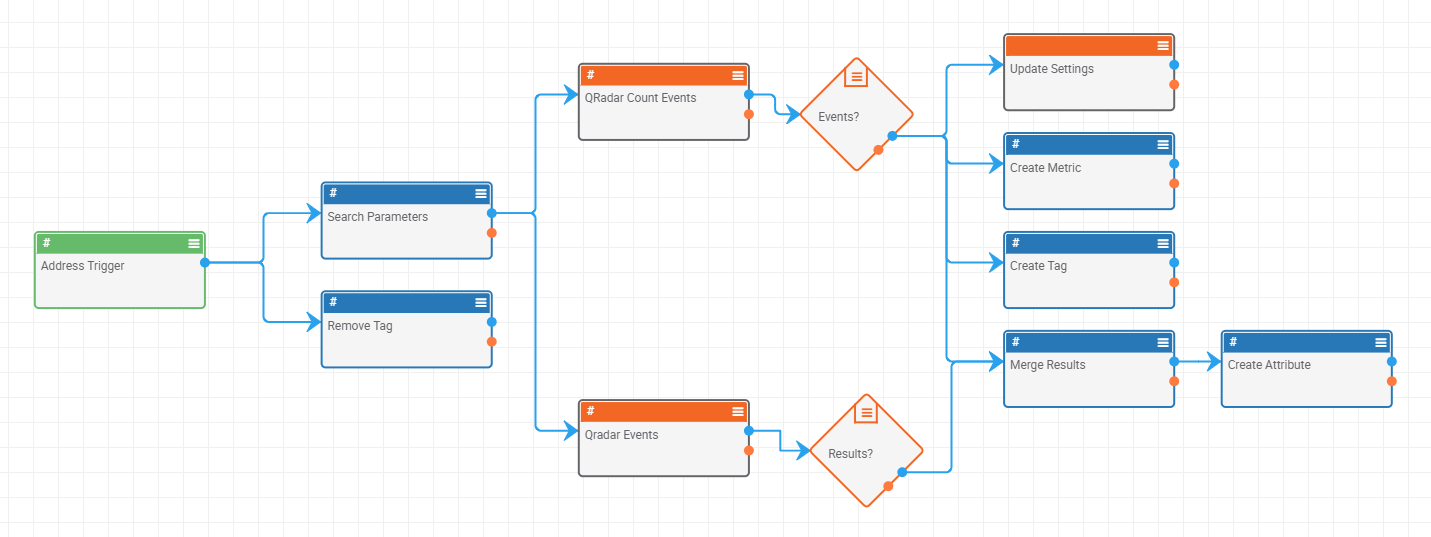
In a nutshell, this Playbook kicks off when a user tags an Indicator with “qSearch.” The Playbook then scans QRadar for Events containing that Indicator, and adds an attribute in ThreatConnect that records the total number of events as well as the top 5 events by frequency. This attribute can then be viewed by a human for analysis or searched on for future use.
This playbook is comprised of the following:
Components
- QRadar Count Events
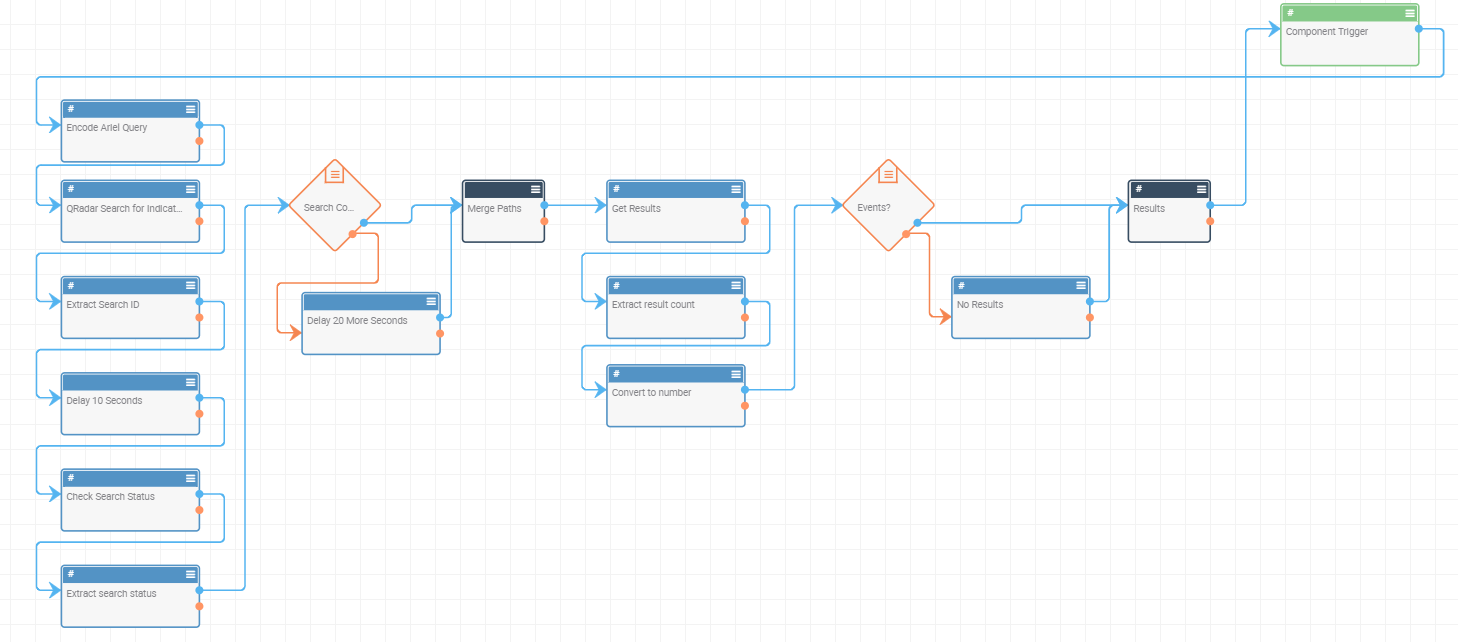
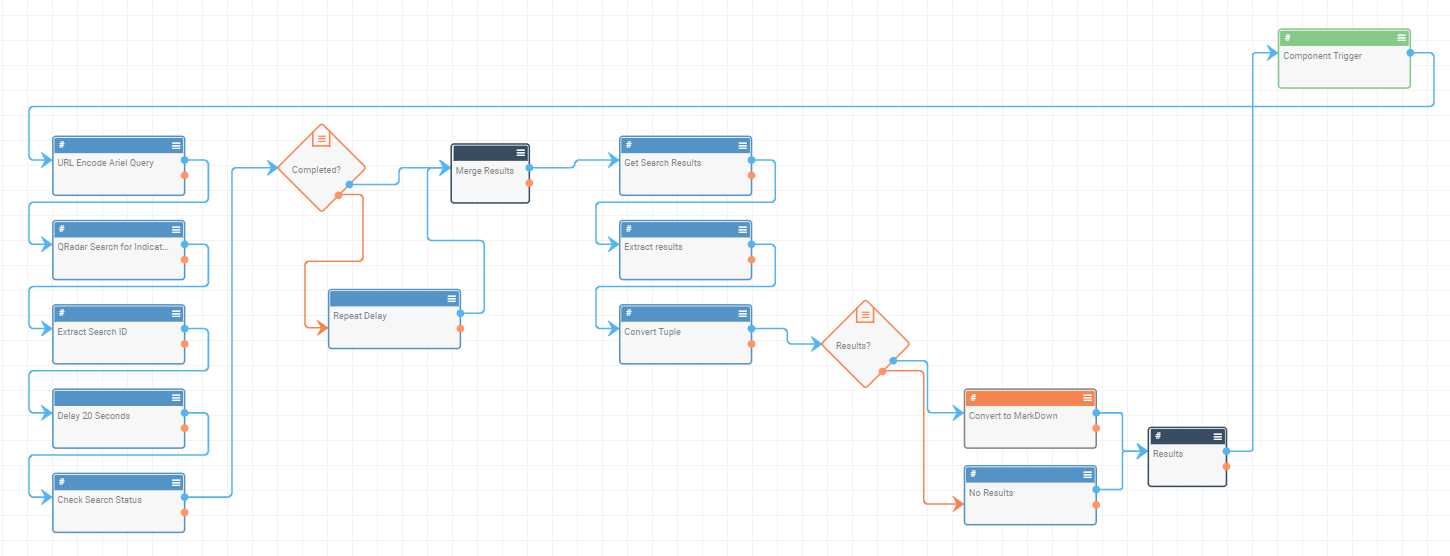
- QRadar Events
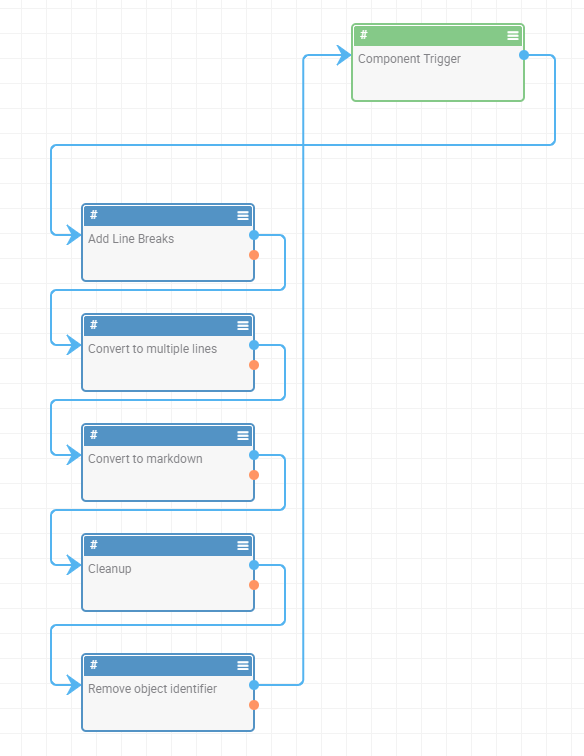
- Convert to MarkDown
Playbook
- Tag Search QRadar:
Again, check out this short recording to see this Playbook in action. Watch the Video on YouTube here.